ICMP协议字段解释

ICMP协议
- ICMP类型:

ICMP报文类型
- 代码:不同的ICMP类型,可能还需要代码做进一步的区分,比如
type=3(终点不可达),就区分网络不可达(0),主机不可达(1),协议不可达(2),端口不可达(3)等
[root@bogon ~]# ping 8.8.8.8 PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data. 64 bytes from 8.8.8.8: icmp_seq=1 ttl=101 time=43.3 ms 64 bytes from 8.8.8.8: icmp_seq=2 ttl=101 time=42.8 ms 64 bytes from 8.8.8.8: icmp_seq=3 ttl=101 time=42.8 ms 64 bytes from 8.8.8.8: icmp_seq=4 ttl=101 time=42.7 ms ^C --- 8.8.8.8 ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3005ms rtt min/avg/max/mdev = 42.785/42.959/43.389/0.355 ms [root@bogon ~]#
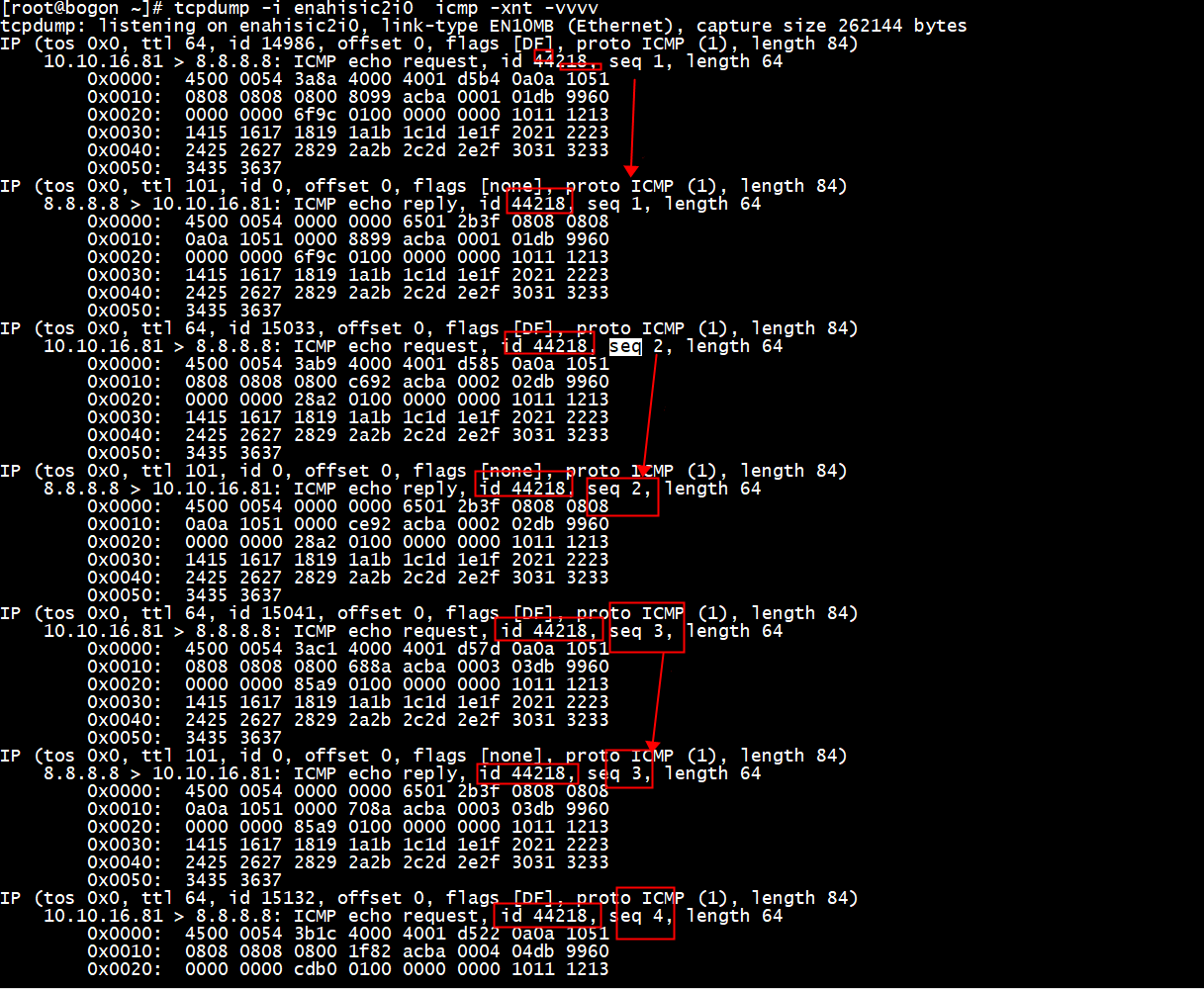
所有ICMP echo request 和ICMP echo reply的id 都一样 id 44218,没有变化
seq 单调递增,一个ICMP echo request 和他的ICMP echo reply的seq一样
[root@bogon ~]# tcpdump -i enahisic2i0 icmp -xnt -vvvv tcpdump: listening on enahisic2i0, link-type EN10MB (Ethernet), capture size 262144 bytes IP (tos 0x0, ttl 64, id 14986, offset 0, flags [DF], proto ICMP (1), length 84) 10.10.16.81 > 8.8.8.8: ICMP echo request, id 44218, seq 1, length 64 0x0000: 4500 0054 3a8a 4000 4001 d5b4 0a0a 1051 0x0010: 0808 0808 0800 8099 acba 0001 01db 9960 0x0020: 0000 0000 6f9c 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637 IP (tos 0x0, ttl 101, id 0, offset 0, flags [none], proto ICMP (1), length 84) 8.8.8.8 > 10.10.16.81: ICMP echo reply, id 44218, seq 1, length 64 0x0000: 4500 0054 0000 0000 6501 2b3f 0808 0808 0x0010: 0a0a 1051 0000 8899 acba 0001 01db 9960 0x0020: 0000 0000 6f9c 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637 IP (tos 0x0, ttl 64, id 15033, offset 0, flags [DF], proto ICMP (1), length 84) 10.10.16.81 > 8.8.8.8: ICMP echo request, id 44218, seq 2, length 64 0x0000: 4500 0054 3ab9 4000 4001 d585 0a0a 1051 0x0010: 0808 0808 0800 c692 acba 0002 02db 9960 0x0020: 0000 0000 28a2 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637 IP (tos 0x0, ttl 101, id 0, offset 0, flags [none], proto ICMP (1), length 84) 8.8.8.8 > 10.10.16.81: ICMP echo reply, id 44218, seq 2, length 64 0x0000: 4500 0054 0000 0000 6501 2b3f 0808 0808 0x0010: 0a0a 1051 0000 ce92 acba 0002 02db 9960 0x0020: 0000 0000 28a2 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637 IP (tos 0x0, ttl 64, id 15041, offset 0, flags [DF], proto ICMP (1), length 84) 10.10.16.81 > 8.8.8.8: ICMP echo request, id 44218, seq 3, length 64 0x0000: 4500 0054 3ac1 4000 4001 d57d 0a0a 1051 0x0010: 0808 0808 0800 688a acba 0003 03db 9960 0x0020: 0000 0000 85a9 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637 IP (tos 0x0, ttl 101, id 0, offset 0, flags [none], proto ICMP (1), length 84) 8.8.8.8 > 10.10.16.81: ICMP echo reply, id 44218, seq 3, length 64 0x0000: 4500 0054 0000 0000 6501 2b3f 0808 0808 0x0010: 0a0a 1051 0000 708a acba 0003 03db 9960 0x0020: 0000 0000 85a9 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637 IP (tos 0x0, ttl 64, id 15132, offset 0, flags [DF], proto ICMP (1), length 84) 10.10.16.81 > 8.8.8.8: ICMP echo request, id 44218, seq 4, length 64 0x0000: 4500 0054 3b1c 4000 4001 d522 0a0a 1051 0x0010: 0808 0808 0800 1f82 acba 0004 04db 9960 0x0020: 0000 0000 cdb0 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637 IP (tos 0x0, ttl 101, id 0, offset 0, flags [none], proto ICMP (1), length 84) 8.8.8.8 > 10.10.16.81: ICMP echo reply, id 44218, seq 4, length 64 0x0000: 4500 0054 0000 0000 6501 2b3f 0808 0808 0x0010: 0a0a 1051 0000 2782 acba 0004 04db 9960 0x0020: 0000 0000 cdb0 0100 0000 0000 1011 1213 0x0030: 1415 1617 1819 1a1b 1c1d 1e1f 2021 2223 0x0040: 2425 2627 2829 2a2b 2c2d 2e2f 3031 3233 0x0050: 3435 3637
|
字段 |
协议 |
内容 |
对应的tcpdump文字描述 |
|---|---|---|---|
|
0x04 |
ICMP消息类型 |
回送请求 |
ICMP echo request |
|
0x00 |
ICMP代码 |
||
|
0xcbae |
16位校验和 |
||
|
0x472e |
ICMP数据标志 |
ICMP的ID |
length 84 |
|
0x1f4c |
16位的标识 |
数据报标识 |
id 18222 |
|
0x0001 |
ICMP序号 |
ICMP序号 |
seq 1 |