Virtual Private Network
虚拟专用网是一种业务,可以在共享的公共网络上提供安全可靠的连接通道.
按层次分的VPN:
二层VPN : ATM/Frame Relay/DDN/ISDN
三层VPN : IPSEC/GRE/L2TP
应用层VPN : Web VPN/SSL VPN
<安全的含义>
保证来源性 <===对源进行认证
保证完整性 <===在传输过程中,不允许对数据包进行修改
保证私密性 <===对数据包进行加密,又称为:数据的机密性.
不可否认性 <===不允许发送方抵赖,说自己没有传过
IPSEC VPN----IP security VPN:

1. Site-to-Site(又称为:Lan-to-Lan , 或者又称为:gateway-to-gateway)
在公网上使用IPSEC VPN连接两个物理上不相连的局域网
2. Remote-access
技术特点:
适用于远程用户通过cisco VPN client 软件客户端拨号到中心站点的情况
根据中心站点设备的不同分为Router remote VPN 和 PIX remote VPN
关键技术点是1.5阶段的Xauth;VPN group;cisco VPN client
加密算法:
1.对称加密
产生一条密钥(加密或解密都使用同一条密钥).
加密速度快,加密后的文件紧凑(加密前后的文件大小差不多),适用于大量数据的加密.
算法:DES/3DES/AES
2.非对称加密
产生一对密钥(加密使用一条密钥(公钥),解密使用另一条密钥(私钥))
加密速度慢,加密后的文件不紧凑(加密后的文件比加密前的文件大很多),适用于加密证书或KEY的管理.
算法:RSA
DH Key Exchange ------- Diffie-Hellman 密钥交换(第一种公共密钥加密系统)
Data Integrity ------ 数据完整性
HASH的算法: 1. MD5 128bit
2. SHA-1 160bit
HASH的特点: 1. 任意不同长度的输入,得到相同长度的输出.
2. 只有完全相同的输入,才有完全相同的输出
3. 雪崩效应(只要有一点更改,就会有非常大的改变)
HMAC ----- HASH Message Authentication Code (利用HASH检验数据完整性)
"MAC" 是一个与Hash密切相关的名词,即信息鉴权码(Message Authority Code)。它是与密钥相关的Hash值,必须拥有该密钥才能检验该Hash值,只有密钥的拥有者可以计算出新的散列值。
Digital Signatures (数字签名)----- 先用私钥加密,然后用公私解密.用于认证源.
Peer Authentication ----- 只要是验证,就要对比HASH
Peer authentication methods:
1. Pre-shared keys ------ 由双方预先设置好
2. RSA signatures
3. RSA encrypted nonces ----- 不需要CA
三种封装的协议:
1. AH-----Authentication Header(认证报头)
验证头部,一种安全协议,只是用来验证头部和防重发.不对实际用户数据部分加密.可配合ESP使用.AH使用IP协议51进行通信.AH是为IP数据报提供无连接的完整性和数据来源验证,并提供重放(replay)攻击保护.
使用AH时,永远不能穿越PAT设备(穿越PAT时,源IP地址会变);做HASH验证时:不计算TTL值;
Authentication Data(认证字段)包含在AH Header字段中.
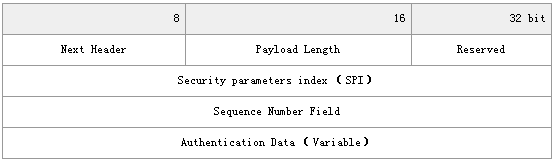
AH头部各字段含义如下:
?下一头(8比特):标识紧跟验证头的下一个头的类型。在传输模式下,将是处于保护的上层协议的值,如UDP或TCP的协议值。在通道模式下,将是值4,表示IP-in-IP(IPv4)封装或IPv6封装的41这个值。
?载荷长度(8比特):以32位字为单位的验证头的长度,再减去2。例如,缺省的验证数据字段的长度是96比特(3个32位字),加上3个字长的固定头,头部共6个字长,因此该字段的值为4。
?保留(16比特):为将来使用。
?安全参数索引(32比特):用于与外部IP头的目的地址一起标识一个安全关联。
?序号(8比特):单增的计数器值,用于提供抗重播功能。
?验证数据(可变):该字段的长度可变(但应为32位字的整数倍),包含的数据有数据包的ICV(完整性校验值)或MAC。
RFC2402对AH头的格式、位置、验证的范围及进入和外出处理规则进行了描述。
2. ESP----Encapsulating Security Payload(封装安全有效载荷)
封装安全有效负载,一种提供数据加密的协议,同时支持验证和防重发功能,它完整封装用户数据,可独自使用或与AH配合使用.ESP使用IP协议50进行通信.
Authentication Data(认证字段)不包含在ESP Header字段中.

ESP头部各字段含义如下:
?SPI字段(Security Parameter Index(SPI)):确定安全关联的安全参数索引,用于和IP头之前的目标地址以及协议一起标识一个安全关联。[32比特]
?序列号字段(Sequence Number:):用来提供反重放保护,跟验证报头中描述的一样。[32比特]
?有效载荷数据(Payload Data):传输层数据段(传输模式)或IP包(隧道模式),通过加密受到保护。也可在保护数据字段中包含一个加密算法可能需要用到的初始化向量(IV)。以强制实施的算法(DES-CBC)来说,IV是“受保护数据”字段中的第一个8位组。[可变]
?填充字段(Padding: Extra bytes):加密算法需要的任何填充字节。[0~9/10字节]
?填充长度(Pad length):包含填充长度字段的字节数[64 bit/块]
?下一报头(Next Header):通过标识载荷中的第一个头(如IPv6中的扩展头,或诸如TCP之类的上层协议头),决定载荷数据字段中数据的类型。
next header 取值: 1 for ICMP / 4 for IP-in-IP encapsulation / 6 for TCP / 17 for UDP
?有效载荷数据(Authentication Data):长度可变的字段(应为32位字的整数倍),用于填入ICV。ICV的计算范围为ESP包中除掉验证数据字段的部分。
ESP加密部分:Payload Data/Padding/Pad length/Next Header
RFC2406对ESP头的格式、位置、验证的范围及进入和外出处理规则进行了描述。
3. Encapsulating Security Payload + Authentication Header
包结构==> | Destination Source | AH HDR| ESP HDR| DATA|
Five steps of IPSec
1. Interesting Traffic --- The VPN devices recognize the traffic to protect
感兴趣流:用于VPN设备识别需要被保护的流量

如上图,IPSEC Tunnel 还没有建立起来:
(1) 当满足了感兴趣流定义的流量,那么将会丢弃.
(2) 没有满足感兴趣流定义的流量,对IPSEC Tunnel的建立与否不受到任何影响.
2. IKE Phase 1 --- The VPN devices negotiate an IKE security policy and establish a secure channel
--- Authenticate the peers
--- Negotiate a bidirectional SA
--- Main mode or aggressive mode
对认证双方PEER和为了加密一部分Main mode 和所有quick mode交换包,而协商一些参数.但是aggressive mode的包都没有加密.
1. 认证双方PEER
2. 产生KEY材料,这个用于产生为了实际加密数据,而用到的KEY
3. 在协商过程中: IKE使用用户数据报协议(UDP)端口500(通常用于源和目的双方)进行通信
所有的主模式和主动模式协商的信息都存在IKE或ISAKMP安全关联(SA)里.每两个PEER之间有一个安全关联.
Main mode (6 Messages) : Site-to-Site
aggressive mode (3 Messages) : Remote VPN 基于 Pre-share Key

上图中,只对第五步和第六步加密了(即Verify the peer identity),认证对方时使用"SKEYID_a".
3. IKE Phase 2 --- The VPN devices negotiate an IPSec security policy used to protect IPSec data
--- IPSec SAs/SPIs
--- Quick mode
在快速模式中,双方PEER协商IPSEC安全关联的属性值.用于加密(例如:ESP)两个主机之间的通信数据.如果启用PFS,将重新进行一次DH交换,在产生IPSEC数据加密KEY之前,交换新的KEY材料.
4. Data transfer --- The VPN devices apply security services to traffic and then transmit the traffic
5. Tunnel terminated --- The tunnel is torn down
SA----security association(安全关联)
SA只是向它所承载的流量提供安全服务的一个连接.SA包含了有关要加密哪种数据流量、如何加密它、是否以及如何认证它、加密密钥及其多长时间刷新的信息.SA是单向的,故欲进行双向通信需建立两个SA(各为一个方向).这些SA通过ISAKMP协商或可人工定义.
SA包括以下两个数据库:
1. Security Policy Database
(1) Encryption Algorithm
(2) Authentication Algorithm
(3) Mode
(4) Key lifetime
2. SA Database
(1) Destination IP address <===用于新的IP包头和目的地址
(2) SPI(安全参数索引) <===用于标识IPSEC通道
(3) Protocol(ESP or AH)
IKE-----Internet Key Exchange(Internet密钥交换协议)
负责各种IPSEC选项的协商、认证通信的每一端(应用时包括公钥交换),以及管理IPSEC隧道的会话密钥.IKE使用用户数据报协议(UDP)端口500(通常用于源和目的双方)进行通信.
一种在Internet Security Association and Key Management Protocol (ISAKMP) 框架中使用Oakley和SKEME协议组的混合协议.IKE通常用来确定一个共享的安全策略和对需要KEY 的KEY服务的验证,在IPSEC流量能通过之前,先要对router/firewall/host 这些对等体进行身份验证.可以在双边手工输入预共享(pre-share)key或者通过CA获得KEY,通过双边协商双边获得统一IKE的SA,建立初步的安全通道,为接下来的IPSEC作准备.
IKE的功能:
1. Negotiating protocol parameters 协商协议参数
2. Exchanging public keys 交换公钥
3. Authenticating both sides 认证PEER
4. Managing keys after the exchange 管理交换完成的KEY
IKE是一个"元"(meta)协议: "ISAKMP" = "Oakley" + "SKEME"
1. ISAKMP----Internet Security Association and Key Management Potocol
(Internet安全连接和密钥管理协议)
作用:定义了一个信息交换的体系架构,包括包的格式和分组在两个Peer之间的传送方式和状态.
2. Oakley ------ 一种KEY交换协议,它的一个基本机制就是Diffie-Hellman KEY交换算法
作用:提供了为在2个IPSec Peer 之间达成一种相同的加密密钥,而需要的一种基于模式的机制.用户从会话中得到加密密钥.
3. SKEME-----Security Key Exchange Mechanism(安全密钥交换机制)
作用:提供了以认证为目的而使用公钥加密的机制,用于认证 IKE SA 的两端.
IKE:Other Functions
DPD ------ Dead peer detection
用于探测对端的Peer是否还存在.
NAT traversal
Encapsulates IPSEC packet in UDP packet
因为IPSEC包为三层包是没有端口信息,所以要将IPSEC的包封装进UDP包的4500号端口里面
IPSEC的包分两种: AH (不支持 NAT Traversal)
ESP (支持 NAT Traversal)
所有主机的数据在没有穿越PAT设备时,源端口和目标端口都是4500号端口;当第一台主机数据穿越PAT设备时,源端口或目标端口号不发生改变,但当第二台主机数据穿越PAT设备时,源端口会随机更改.
SKEYID是从秘密材料中衍生出的字符串,只有某次交换中的活跃双方才知道。
SKEYID_a是ISAKMP SA用来验证消息所使用的密钥材料。 <====HASH时,使用
SKEYID_e是ISAKMP SA用来保护消息的机密性的密钥材料。 <====第一阶段时,使用
SKEYID_d是非ISAKMP安全联盟用来衍生出密钥所使用的密钥材料。 <===衍生出ESP的密钥材料{即:也会根据前面的"SKEYID_d"衍生出新的 "SKEYID_a"(已经没用了) / "SKEYID_e"(已经没用了) / "SKEYID_d"(衍生出ESP的密钥材料) }
Crypto Map
1. 静态的Crypto Map ----- 两端都使用静态的IP地址,例:Lan-to-Lan
2. 动态的Crypto Map ----- 其中一端使用动态的IP地址,例:Remote VPN
MAP的处理----对进来的数据包
是否感兴趣流 是否加密 有无MAP action
N/A 是 有 解密
是 不 有 drop
是 不 没有 forward
N/A 是 没有 解密
实验1:Lan-to-Lan
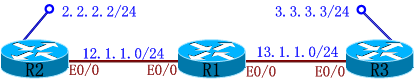
IKE Phase I Policy:
协商策略(策略可以建立多个,发起方会将自己的所有策略发给对方,对方会按收到的序号最小的开始匹配;双方完全匹配的策略会由对方发回到发起方,表示确认,并使用此策略):
R2(config)#crypto isakmp policy 2 <===策略号只是本地有效(建议两端相同)
R2(config-isakmp)#authentication pre-share <====认证方法(Pre-share/rsa-encr/rsa-sig)
R2(config-isakmp)#hash md5 <====对协商包进行认证
R2(config-isakmp)#encryption 3des <===对协商的数据进行"3des"加密(两端一定要相同)
R2(config-isakmp)#group 2 <===两端组号一定要相同(不同的组:加密的位数也不相同)
R2(config-isakmp)#lifetime 60 <===多少秒后,重新协商(默认为:86400 second )
R2(config)#crypto isakmp key 0 wolf address 13.1.1.3 <===使用"Pre-share"认证方式,才要输入此命令
"0":密钥将以明文方式发向"13.1.1.3"
"wolf":密码(两端一定要一样)
---------------------------------------------
R3(config)#crypto isakmp policy 3
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#hash md5
R3(config-isakmp)#encryption 3des
R3(config-isakmp)#group 2
R3(config)#crypto isakmp key 0 wolf address 12.1.1.2
IKE Phase II Policy:
定义转换集(本地所有的转换集要发往对方,让对方匹配自己的转换集,然后返回确认;可设置多个):
R2(config)#crypto ipsec transform-set cisco esp-des esp-sha-hmac
"cisco":transform-set的名字
"esp-des esp-sha-hmac":transform-set的加密和认证方式(选择"esp-null":不对数据加密)
R2(cfg-crypto-trans)#mode tunnel <===可选择 transport/tunnel(但Lan-to-Lan只能选择:tunnel模式)
定义感兴趣流:
R2(config)#access-list 101 permit ip 2.2.2.0 0.0.0.255 3.3.3.0 0.0.0.255
或者: R2(config)#ip access-list extended VPN
R2(config-ext-nacl)#permit ip 2.2.2.0 0.0.0.255 3.3.3.0 0.0.0.255
定义MAP:
R2(config)#crypto map huawei 10 ipsec-isakmp
"huawei":定义MAP的名字
"10":序号
"ipsec-isakmp":可选择 ipsec-isakmp(自动)/ ipsec-manual(手动)
R2(config-crypto-map)#set peer 13.1.1.3 <===当满足了感兴趣流之后,和"13.1.1.3"建立peer
R2(config-crypto-map)#set transform-set cisco <===调用名字为"cisco"的transform-set
或者: R2(config-crypto-map)#set transform-set cisco cisco2 <===后面可写多个"transform-set"
R2(config-crypto-map)#set pfs <===可选择(group1/group2/group5),默认为"group1"
R2(config-crypto-map)#match address 101 <===匹配"101"(或者是"VPN")的感兴趣流
---------------------------------------------------
R3(config)#crypto ipsec transform-set cisco esp-des esp-sha-hmac
R3(cfg-crypto-trans)#mode tunnel
R3(config)#access-list 101 permit ip 3.3.3.0 0.0.0.255 2.2.2.0 0.0.0.255
R3(config)#crypto map huawei 10 ipsec-isakmp
R3(config-crypto-map)#set peer 12.1.1.2
R3(config-crypto-map)#set transform-set cisco
R3(config-crypto-map)#set pfs
R3(config-crypto-map)#match address 101
Apply VPN Configuration:
在接口上调用名字为"huawei"的MAP:
R2(config)#interface e0/0
R2(config-if)#crypto map huawei
------------------------------------
R3(config)#interface e0/0
R3(config-if)#crypto map huawei
调试:
R2#debug crypto isakmp <===查看第一阶段的IKE
R2#debug crypto ipsec <===查看第二阶段的IKE
IPSEC中Lan-to-Lan的建立过程:
R2#ping 3.3.3.3 source 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 2.2.2.2
*Mar 1 00:55:40.767: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 12.1.1.2, remote= 13.1.1.3, <==由于ping包的触发,开始建立IPSEC通道
local_proxy= 2.2.2.0/255.255.255.0/0/0 (type=4),
remote_proxy= 3.3.3.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x5E39E570(1580852592), conn_id= 0, keysize= 0, flags= 0x400B
*Mar 1 00:55:40.767: ISAKMP: received ke message (1/1) <===IKE的第一阶段
*Mar 1 00:55:40.771: ISAKMP (0:0): SA request profile is (NULL)
*Mar 1 00:55:40.771: ISAKMP: local port 500, remote port 500
*Mar 1 00:55:40.771: ISAKMP: set new node 0 to QM_IDLE
*Mar 1 00:55:40.771: ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 628E53B8
*Mar 1 00:55:40.771: ISAKMP (0:2): Can not start Aggressive mode, trying Main mode.
*Mar 1 00:55:40.775: ISAKMP: Looking for a matching key for 13.1.1.3 in default : success
*Mar 1 00:55:40.775: ISAKMP (0:2): found peer pre-shared key matching 13.1.1.3
*Mar 1 00:55:40.775: ISAKMP (0:2): constructed NAT-T vendor-07 ID
*Mar 1 00:55:40.775: ISAKMP (0:2): constructed NAT-T vendor-03 ID
*Mar 1 00:55:40.775: ISAKMP (0:2): constructed NAT-T vendor-02 ID
*Mar 1 00:55:40.775: ISAKMP (0:2): Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 1 00:55:40.775: ISAKMP (0:2): Old State = IKE_READY New State = IKE_I_MM1
IKE第一阶段的第一个包的交换
*Mar 1 00:55:40.775: ISAKMP (0:2): beginning Main Mode exchange <==开始使用Main mode
*Mar 1 00:55:40.775: ISAKMP (0:2): sending packet to 13.1.1.3 my_port 500 peer_port 500 (I) MM_NO_STATE 发协包到对方PEER"13.1.1.3" 源端口:500 目标端口:500
*Mar 1 00:55:40.963: ISAKMP (0:2): received packet from 13.1.1.3 dport 500 sport 500 Global (I) MM_NO_STATE
*Mar 1 00:55:40.967: ISAKMP (0:2): Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 00:55:40.967: ISAKMP (0:2): Old State = IKE_I_MM1 New State = IKE_I_MM2
IKE第一阶段的第二个包的交换
*Mar 1 00:55:40.967: ISAKMP (0:2): processing SA payload. message ID = 0
*Mar 1 00:55:40.967: ISAKMP (0:2): processing vendor id payload
*M.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 12/12/12 ms
R2#ar 1 00:55:40.971: ISAKMP (0:2): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 00:55:40.971: ISAKMP (0:2): vendor ID is NAT-T v7
*Mar 1 00:55:40.971: ISAKMP: Looking for a matching key for 13.1.1.3 in default : success
*Mar 1 00:55:40.971: ISAKMP (0:2): found peer pre-shared key matching 13.1.1.3
*Mar 1 00:55:40.971: ISAKMP (0:2) local preshared key found
*Mar 1 00:55:40.971: ISAKMP : Scanning profiles for xauth ...
*Mar 1 00:55:40.971: ISAKMP (0:2): Checking ISAKMP transform 1 against priority 2 policy
*Mar 1 00:55:40.971: ISAKMP: encryption 3DES-CBC
*Mar 1 00:55:40.971: ISAKMP: hash MD5
*Mar 1 00:55:40.971: ISAKMP: default group 2
*Mar 1 00:55:40.971: ISAKMP: auth pre-share
*Mar 1 00:55:40.971: ISAKMP: life type in seconds
*Mar 1 00:55:40.975: ISAKMP: life duration (basic) of 60
*Mar 1 00:55:40.975: ISAKMP (0:2): atts are acceptable. Next payload is 0 <===表示策略匹配协商完成
*Mar 1 00:55:41.143: ISAKMP (0:2): processing vendor id payload
*Mar 1 00:55:41.143: ISAKMP (0:2): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 00:55:41.143: ISAKMP (0:2): vendor ID is NAT-T v7
*Mar 1 00:55:41.143: ISAKMP (0:2): Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 00:55:41.143: ISAKMP (0:2): Old State = IKE_I_MM2 New State = IKE_I_MM2
*Mar 1 00:55:41.147: ISAKMP (0:2): sending packet to 13.1.1.3 my_port 500 peer_port 500 (I) MM_SA_SETUP
*Mar 1 00:55:41.151: ISAKMP (0:2): Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 00:55:41.151: ISAKMP (0:2): Old State = IKE_I_MM2 New State = IKE_I_MM3
IKE第一阶段的第三个包的交换
*Mar 1 00:55:41.371: ISAKMP (0:1): purging node -1572961127
*Mar 1 00:55:41.383: ISAKMP (0:2): received packet from 13.1.1.3 dport 500 sport 500 Global (I) MM_SA_SETUP
*Mar 1 00:55:41.387: ISAKMP (0:2): Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 00:55:41.387: ISAKMP (0:2): Old State = IKE_I_MM3 New State = IKE_I_MM4
IKE第一阶段的第四个包的交换
*Mar 1 00:55:41.387: ISAKMP (0:2): processing KE payload. message ID = 0
*Mar 1 00:55:41.603: ISAKMP (0:2): processing NONCE payload. message ID = 0
*Mar 1 00:55:41.607: ISAKMP: Looking for a matching key for 13.1.1.3 in default : success
*Mar 1 00:55:41.607: ISAKMP (0:2): found peer pre-shared key matching 13.1.1.3
*Mar 1 00:55:41.607: ISAKMP (0:2): SKEYID state generated <===当第三、四个包完成后,就会产生SKEYID
*Mar 1 00:55:41.607: ISAKMP (0:2): processing vendor id payload
*Mar 1 00:55:41.607: ISAKMP (0:2): vendor ID is Unity
*Mar 1 00:55:41.611: ISAKMP (0:2): processing vendor id payload
*Mar 1 00:55:41.611: ISAKMP (0:2): vendor ID is DPD
*Mar 1 00:55:41.611: ISAKMP (0:2): processing vendor id payload
*Mar 1 00:55:41.611: ISAKMP (0:2): speaking to another IOS box!
*Mar 1 00:55:41.611: ISAKMP (0:2): Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 00:55:41.611: ISAKMP (0:2): Old State = IKE_I_MM4 New State = IKE_I_MM4
*Mar 1 00:55:41.615: ISAKMP (0:2): Send initial contact
*Mar 1 00:55:41.615: ISAKMP (0:2): SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Mar 1 00:55:41.615: ISAKMP (0:2): ID payload
next-payload : 8
type : 1
address : 12.1.1.2
protocol : 17
port : 500
length : 12
*Mar 1 00:55:41.619: ISAKMP (2): Total payload length: 12
*Mar 1 00:55:41.619: ISAKMP (0:2): sending packet to 13.1.1.3 my_port 500 peer_port 500 (I) MM_KEY_EXCH
*Mar 1 00:55:41.623: ISAKMP (0:2): Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 00:55:41.623: ISAKMP (0:2): Old State = IKE_I_MM4 New State = IKE_I_MM5
IKE第一阶段的第五个包的交换
*Mar 1 00:55:41.643: ISAKMP (0:2): received packet from 13.1.1.3 dport 500 sport 500 Global (I) MM_KEY_EXCH
*Mar 1 00:55:41.647: ISAKMP (0:2): processing ID payload. message ID = 0
*Mar 1 00:55:41.647: ISAKMP (0:2): ID payload
next-payload : 8
type : 1
address : 13.1.1.3
protocol : 17
port : 500
length : 12
*Mar 1 00:55:41.647: ISAKMP (0:2): processing HASH payload. message ID = 0
*Mar 1 00:55:41.651: ISAKMP (0:2): SA authentication status:
authenticated
*Mar 1 00:55:41.651: ISAKMP (0:2): SA has been authenticated with 13.1.1.3
*Mar 1 00:55:41.651: ISAKMP (0:2): peer matches *none* of the profiles
*Mar 1 00:55:41.651: ISAKMP (0:2): Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 00:55:41.651: ISAKMP (0:2): Old State = IKE_I_MM5 New State = IKE_I_MM6
IKE第一阶段的第六个包的交换
*Mar 1 00:55:41.655: ISAKMP (0:2): Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 00:55:41.655: ISAKMP (0:2): Old State = IKE_I_MM6 New State = IKE_I_MM6
*Mar 1 00:55:41.659: ISAKMP (0:2): Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 00:55:41.659: ISAKMP (0:2): Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
*Mar 1 00:55:41.659: ISAKMP (0:2): received packet from 13.1.1.3 dport 500 sport 500 Global (I) MM_KEY_EXCH
*Mar 1 00:55:41.663: ISAKMP: set new node -1323939639 to QM_IDLE
*Mar 1 00:55:41.663: ISAKMP (0:2): processing HASH payload. message ID = -1323939639
*Mar 1 00:55:41.667: ISAKMP (0:2): processing DELETE payload. message ID = -1323939639
*Mar 1 00:55:41.667: ISAKMP (0:2): peer does not do paranoid keepalives.
*Mar 1 00:55:41.667: ISAKMP (0:2): deleting node -1323939639 error FALSE reason "informational (in) state 1"
*Mar 1 00:55:41.667: ISAKMP (0:2): beginning Quick Mode exchange, M-ID of -426260398
IKE的第二阶段的快速模式的开始
*Mar 1 00:55:41.775: IPSEC(key_engine): got a queue event...
*Mar 1 00:55:41.775: IPSEC(key_engine_delete_sas): rec'd delete notify from ISAKMP
*Mar 1 00:55:41.779: ISAKMP (0:2): sending packet to 13.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Mar 1 00:55:41.779: ISAKMP (0:2): Node -426260398, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Mar 1 00:55:41.779: ISAKMP (0:2): Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Mar 1 00:55:41.779: ISAKMP (0:2): Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
*Mar 1 00:55:41.783: ISAKMP (0:2): Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Mar 1 00:55:42.287: ISAKMP (0:2): received packet from 13.1.1.3 dport 500 sport 500 Global (I) QM_IDLE
*Mar 1 00:55:42.295: ISAKMP (0:2): processing HASH payload. message ID = -426260398
*Mar 1 00:55:42.295: ISAKMP (0:2): processing SA payload. message ID = -426260398
*Mar 1 00:55:42.295: ISAKMP (0:2): Checking IPSec proposal 1
*Mar 1 00:55:42.295: ISAKMP: transform 1, ESP_DES
*Mar 1 00:55:42.295: ISAKMP: attributes in transform:
*Mar 1 00:55:42.295: ISAKMP: encaps is 1 (Tunnel)
*Mar 1 00:55:42.295: ISAKMP: SA life type in seconds
*Mar 1 00:55:42.295: ISAKMP: SA life duration (basic) of 3600
*Mar 1 00:55:42.295: ISAKMP: SA life type in kilobytes
*Mar 1 00:55:42.295: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
*Mar 1 00:55:42.295: ISAKMP: authenticator is HMAC-SHA
*Mar 1 00:55:42.295: ISAKMP: group is 1
*Mar 1 00:55:42.299: ISAKMP (0:2): atts are acceptable.
*Mar 1 00:55:42.299: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 12.1.1.2, remote= 13.1.1.3,
local_proxy= 2.2.2.0/255.255.255.0/0/0 (type=4),
remote_proxy= 3.3.3.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-sha-hmac (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x12
*Mar 1 00:55:42.299: IPSEC(kei_proxy): head = huawei, map->ivrf = , kei->ivrf =
*Mar 1 00:55:42.303: ISAKMP (0:2): processing NONCE payload. message ID = -426260398
*Mar 1 00:55:42.303: ISAKMP (0:2): processing KE payload. message ID = -426260398
*Mar 1 00:55:42.431: ISAKMP (0:2): processing ID payload. message ID = -426260398
*Mar 1 00:55:42.431: ISAKMP (0:2): processing ID payload. message ID = -426260398
*Mar 1 00:55:42.443: ISAKMP (0:2): Creating IPSec SAs
*Mar 1 00:55:42.443: inbound SA from 13.1.1.3 to 12.1.1.2 (f/i) 0/ 0
(proxy 3.3.3.0 to 2.2.2.0)
*Mar 1 00:55:42.443: has spi 0x5E39E570 and conn_id 2000 and flags 13
*Mar 1 00:55:42.443: lifetime of 3600 seconds
*Mar 1 00:55:42.443: lifetime of 4608000 kilobytes
*Mar 1 00:55:42.443: has client flags 0x0
*Mar 1 00:55:42.443: outbound SA from 12.1.1.2 to 13.1.1.3 (f/i) 0/ 0 (proxy 2.2.2.0 to 3.3.3.0 )
*Mar 1 00:55:42.443: has spi 235339588 and conn_id 2001 and flags 1B
*Mar 1 00:55:42.443: lifetime of 3600 seconds
*Mar 1 00:55:42.443: lifetime of 4608000 kilobytes
*Mar 1 00:55:42.443: has client flags 0x0
*Mar 1 00:55:42.447: ISAKMP (0:2): sending packet to 13.1.1.3 my_port 500 peer_port 500 (I) QM_IDLE
*Mar 1 00:55:42.447: ISAKMP (0:2): deleting node -426260398 error FALSE reason ""
*Mar 1 00:55:42.447: ISAKMP (0:2): Node -426260398, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Mar 1 00:55:42.447: ISAKMP (0:2): Old State = IKE_QM_I_QM1 New State = IKE_QM_PHASE2_COMPLETE
*Mar 1 00:55:42.451: IPSEC(key_engine): got a queue event... 第二阶段完成后,就会建立SA
*Mar 1 00:55:42.451: IPSEC(initialize_sas): ,
(key eng. msg.) INBOUND local= 12.1.1.2, remote= 13.1.1.3,
local_proxy= 2.2.2.0/255.255.255.0/0/0 (type=4),
remote_proxy= 3.3.3.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x5E39E570(1580852592), conn_id= 2000, keysize= 0, flags= 0x13 <===证明SA已经建立完成
*Mar 1 00:55:42.451: IPSEC(initialize_sas): ,
(key eng. msg.) OUTBOUND local= 12.1.1.2, remote= 13.1.1.3,
local_proxy= 2.2.2.0/255.255.255.0/0/0 (type=4),
remote_proxy= 3.3.3.0/255.255.255.0/0/0 (type=4),
protocol= ESP, transform= esp-des esp-sha-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0xE06FF44(235339588), conn_id= 2001, keysize= 0, flags= 0x1B
*Mar 1 00:55:42.455: IPSEC(kei_proxy): head = huawei, map->ivrf = , kei->ivrf =
*Mar 1 00:55:42.455: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and 13.1.1.3
*Mar 1 00:55:42.455: IPSEC(add mtree): src 2.2.2.0, dest 3.3.3.0, dest_port 0
*Mar 1 00:55:42.455: IPSEC(create_sa): sa created,
(sa) sa_dest= 12.1.1.2, sa_prot= 50,
sa_spi= 0x5E39E570(1580852592),
sa_trans= esp-des esp-sha-hmac , sa_conn_id= 2000
*Mar 1 00:55:42.455: IPSEC(create_sa): sa created,
(sa) sa_dest= 13.1.1.3, sa_prot= 50,
sa_spi= 0xE06FF44(235339588),
sa_trans= esp-des esp-sha-hmac , sa_conn_id= 2001
*Mar 1 00:55:51.371: ISAKMP (0:1): purging SA., sa=62E3C24C, delme=62E3C24C
清除IPSEC中Lan-to-Lan的连接:
R2#clear crypto isakmp <===清除第一阶段的IKE
R2#clear crypto sa
R2#show crypto isakmp sa
R2#show crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: huawei, local addr 12.1.1.2 <===本端的地址
protected vrf: (none)
local ident (addr/mask/prot/port): (2.2.2.0/255.255.255.0/0/0) <====本端的感兴趣流
remote ident (addr/mask/prot/port): (3.3.3.0/255.255.255.0/0/0) <====远端的感兴趣流
current_peer 13.1.1.3 port 500 <====远端的地址和端口号
PERMIT, flags={origin_is_acl,}
#pkts encaps: 3, #pkts encrypt: 3, #pkts digest: 3
#pkts decaps: 3, #pkts decrypt: 3, #pkts verify: 3
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 12.1.1.2, remote crypto endpt.: 13.1.1.3
path mtu 1500, ip mtu 1500
current outbound spi: 0x5C587C54(1549302868)
inbound esp sas:
spi: 0xECCDDAEC(3972913900)
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: 1, crypto map: huawei
sa timing: remaining key lifetime (k/sec): (4449567/3167)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x5C587C54(1549302868) <===本地"outbound"的"spi" ,就是对方"inbound"的"spi"
transform: esp-des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: 2, crypto map: huawei
sa timing: remaining key lifetime (k/sec): (4449567/3165)
SA Lifetime: Data-based/Time-based
假设两端时间不相同:由时间小的一端发起PING包是可通的,但由时间大的一端发起PING包是不通的.
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R2#show crypto map
Crypto Map "huawei" 10 ipsec-isakmp
Peer = 13.1.1.3
Extended IP access list VPN
access-list VPN permit ip 2.2.2.0 0.0.0.255 3.3.3.0 0.0.0.255
Current peer: 13.1.1.3
Security association lifetime: 4608000 kilobytes/3600 seconds <===两端协商时间,使用小的时间("Security association lifetime"中的"seconds")
PFS (Y/N): Y <===重新做一次Diffie-Hellman交换
只有一端配置了PFS:
(1) 由配置了PFS的一端发起连接是可以成功的(但会显示"Attributes Not Supported",然后继续协商)
(2) 由没有配置了PFS的一端发起连接是不成功的
DH group: group1
Transform sets={
cisco,
}
Interfaces using crypto map huawei:
Ethernet0/0
更改Security association lifetime:
R2(config)#crypto ipsec security-association lifetime seconds 600
R2(config)#crypto ipsec security-association lifetime kilobytes 10240
R2#show crypto engine connections active
ID Interface IP-Address State Algorithm Encrypt Decrypt
1 Ethernet0/0 12.1.1.2 set HMAC_MD5+3DES_56_C 0 0
2001 Ethernet0/0 12.1.1.2 set DES+SHA 0 99
2002 Ethernet0/0 12.1.1.2 set DES+SHA 99 0
实验2:Router Remote VPN ----- 只能是动态IP的一方发起连接(即,下例:"remote"方发起连接)
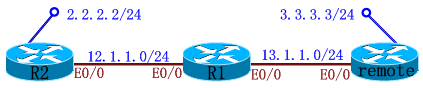
IKE Phase I Policy:
R2(config)#crypto isakmp policy 2
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#hash md5
R2(config-isakmp)#encryption 3des
R2(config-isakmp)#group 2
R2(config)#crypto isakmp key 0 wolf address 0.0.0.0 0.0.0.0 <====由于是动态VPN,对端的地址不固定,所以写0.0.0.0
---------------------------------------------------------
remote(config)#crypto isakmp policy 2
remote(config-isakmp)#authentication pre-share
remote(config-isakmp)#hash md5
remote(config-isakmp)#encryption 3des
remote(config-isakmp)#group 2
remote(config)#crypto isakmp key 0 wolf address 12.1.1.2
IKE Phase II Policy:
R2(config)#crypto ipsec transform-set cisco esp-des esp-sha-hmac
R2(cfg-crypto-trans)#mode tunnel
R2(config)#access-list 101 permit ip 2.2.2.0 0.0.0.255 3.3.3.0 0.0.0.255
Static Crypto Map:
R2(config)#crypto map huawei 10 ipsec-isakmp
R2(config-crypto-map)#set peer 13.1.1.3
R2(config-crypto-map)#set transform-set cisco
R2(config-crypto-map)#set pfs
R2(config-crypto-map)#match address 101
----------------------------------------------------------------------
remote(config)#crypto ipsec transform-set cisco esp-des esp-sha-hmac
remote(cfg-crypto-trans)#mode tunnel
Dynamic Crypto Map:
remote(config)#crypto dynamic-map dynamap 10
remote(config-crypto-map)#set transform-set cisco
remote(config-crypto-map)#set pfs
remote(config)#crypto map QQ 10 ipsec-isakmp dynamic dynamap
Apply VPN Configuration:
R2(config)#interface e0/0
R2(config-if)#crypto map huawei
------------------------------------
remote(config)#interface e0/0
remote(config-if)#crypto map QQ
实验3:Lan-to-Lan (新命令)
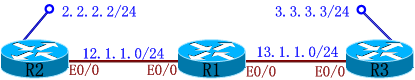
IKE Phase I Policy:
R2(config)#crypto isakmp policy 2
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#hash md5
R2(config-isakmp)#encryption 3des
R2(config-isakmp)#group 2
R2(config)#crypto keyring L2LKEY
R2(conf-keyring)#pre-shared-key address 13.1.1.3 key wolf
R2(config)#crypto isakmp profile L2L
R2(conf-isa-prof)#match identity address 13.1.1.3
R2(conf-isa-prof)#keyring L2LKEY
IPSec Phase II Policy:
R2(config)#crypto ipsec transform-set cisco esp-des esp-sha-hmac
R2(cfg-crypto-trans)#mode tunnel
R2(config)#access-list 101 permit ip 2.2.2.0 0.0.0.255 3.3.3.0 0.0.0.255
R2(config)#crypto map huawei 10 ipsec-isakmp
R2(config-crypto-map)#set peer 13.1.1.3
R2(config-crypto-map)#set transform-set cisco
R2(config-crypto-map)#set pfs
R2(config-crypto-map)#match address 101
R2(config-crypto-map)#set isakmp-profile L2L
R2(config-crypto-map)#reverse-route <===选其一:反向路由注入/静态(即:写了反向路由注入,可以不用写静态)
Apply VPN Configuration
R2(config)#interface ethernet 0/0
R2(config-if)#crypto map huawei