JenKins使用Kubernetes
最近我们构建和部署服务的方式与原来相比简直就是突飞猛进,像那种笨拙的、单一的、用于构建单体式应用程序的方式已经是过去式了。现在的应用为了提供更好的拓展性和可维护性,都会去拆解成各种相互依赖小、解耦性强的微服务,这些服务有各自的依赖和进度。这跟我们的Kubernetes不谋而合。
JenKins链接K8S
使用Jenkins链接K8S需要创建一些秘钥。
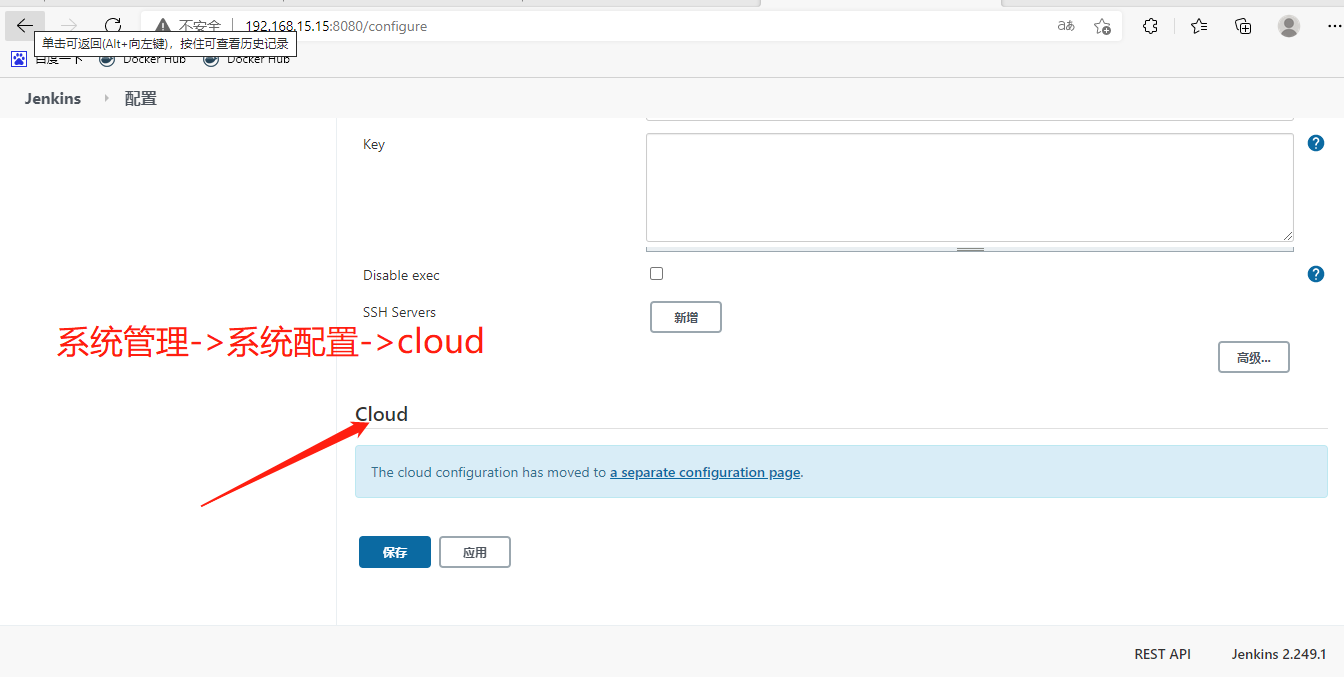
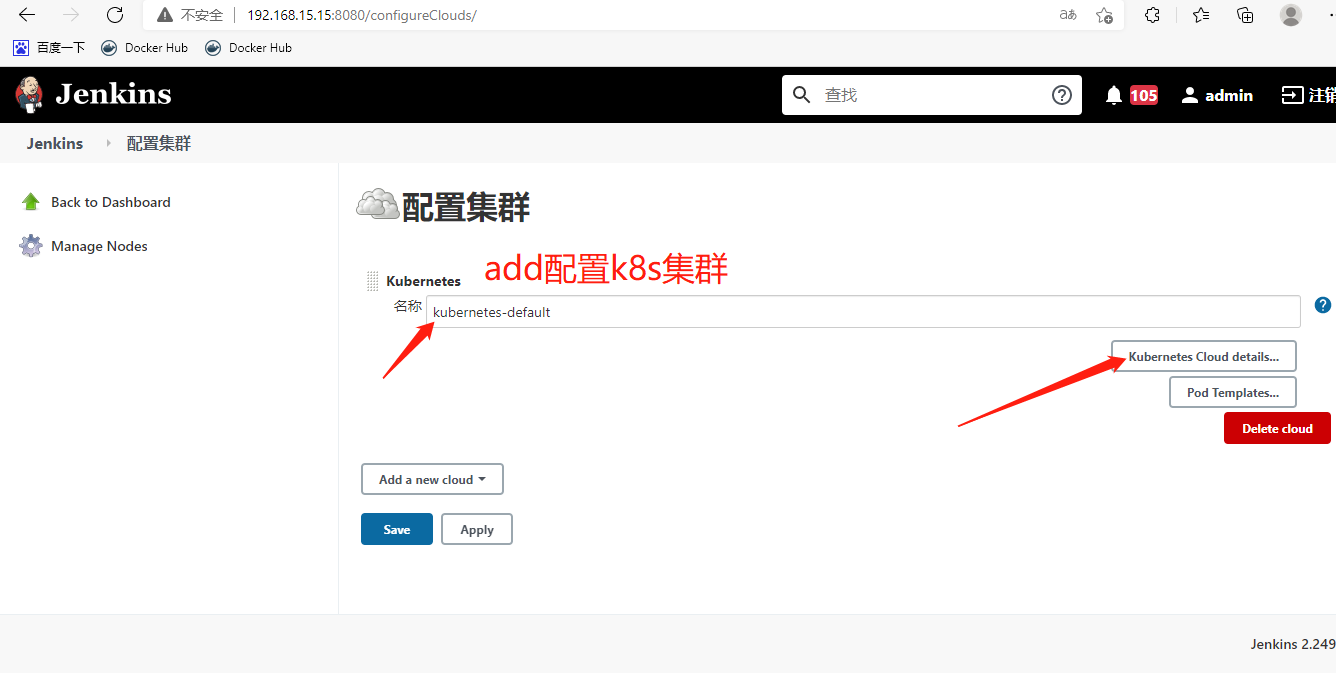
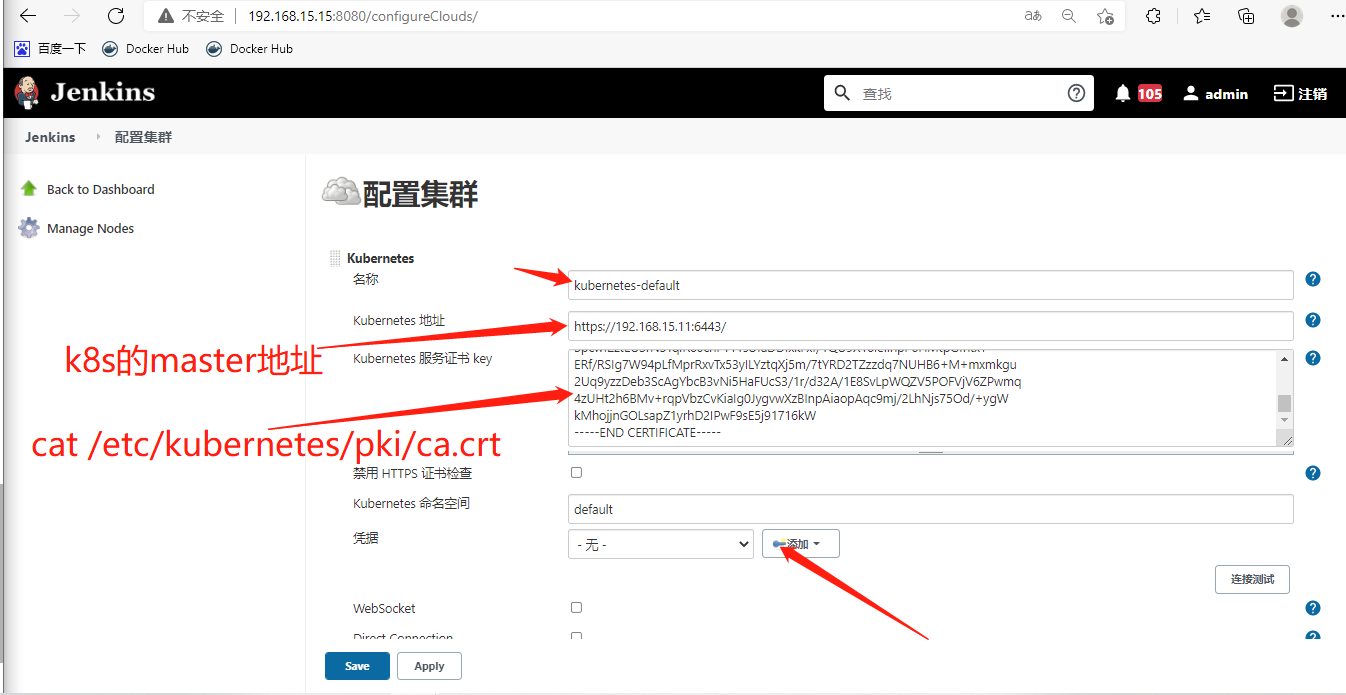
第1步:将证书私钥填写至Jenkins
cat /etc/kubernetes/pki/ca.crt
第2步:创建admin-csr.json
cat > admin-csr.json << EOF
{
"CN":"admin",
"key":{
"algo":"rsa",
"size":2048
},
"names":[
{
"C":"CN",
"L":"BeiJing",
"ST":"BeiJing",
"O":"system:masters",
"OU":"System"
}
]
}
EOF
第3步:创建证书和私钥
#先下载cfssl
[root@k8s-m-01 ~]# wget https://github.com/cloudflare/cfssl/releases/download/v1.6.0/cfssl_1.6.0_linux_amd64
[root@k8s-m-01 ~]# wget https://github.com/cloudflare/cfssl/releases/download/v1.6.0/cfssljson_1.6.0_linux_amd64
[root@k8s-m-01 ~]# chmod +x cfssl_1.6.0_linux_amd64
[root@k8s-m-01 ~]# chmod +x cfssljson_1.6.0_linux_amd64
[root@k8s-m-01 ~]# mv cfssl_1.6.0_linux_amd64 /usr/local/bin/cfssl
[root@k8s-m-01 ~]# mv cfssljson_1.6.0_linux_amd64 /usr/local/bin/cfssljson
cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key --profile=kubernetes admin-csr.json | cfssljson -bare admin
第4步:配置证书
openssl pkcs12 -export -out ./jenkins-admin.pfx -inkey ./admin-key.pem -in ./admin.pem -passout pass:123456
[root@k8s-m-01 ~]# ll
total 75764
-rw-r--r-- 1 root root 1009 Aug 23 15:58 admin.csr
-rw-r--r-- 1 root root 260 Aug 23 15:46 admin-csr.json
-rw------- 1 root root 1675 Aug 23 15:58 admin-key.pem
-rw-r--r-- 1 root root 1294 Aug 23 15:58 admin.pem
-rw-r--r-- 1 root root 2517 Aug 23 15:59 jenkins-admin.pfx
[root@k8s-m-01 ~]# sz jenkins-admin.pfx #传到桌面
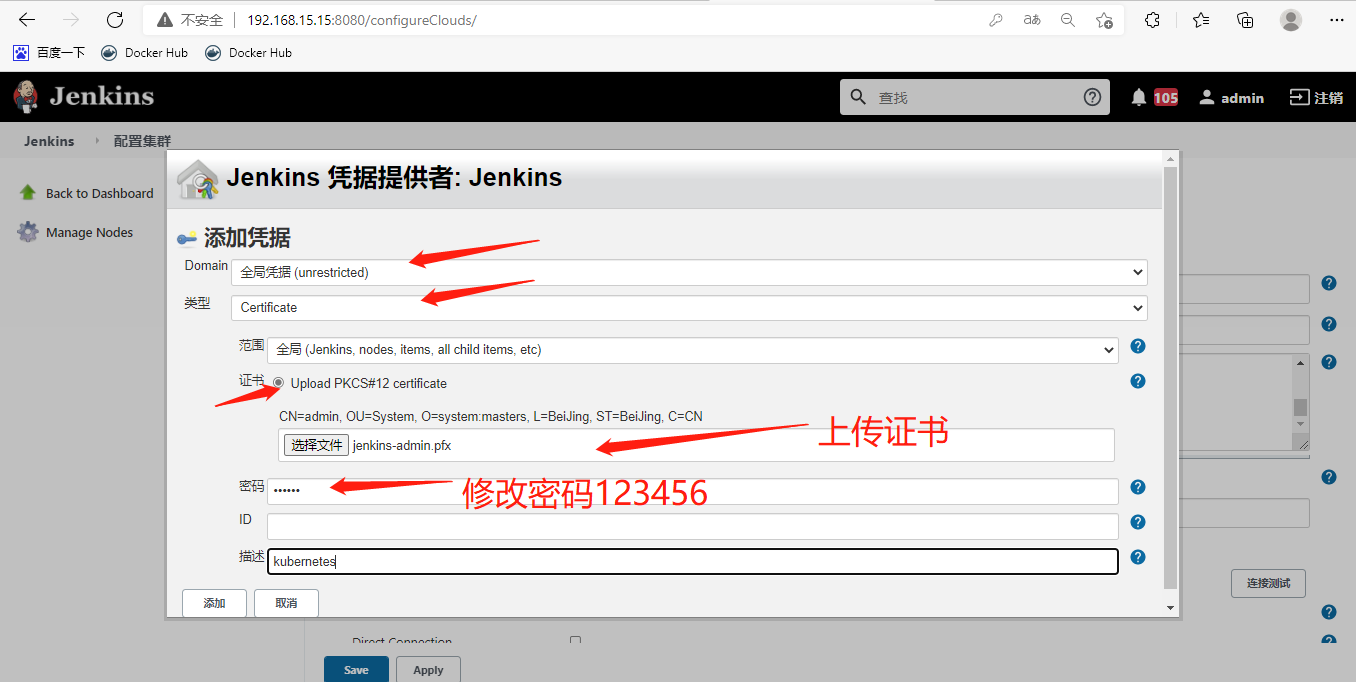
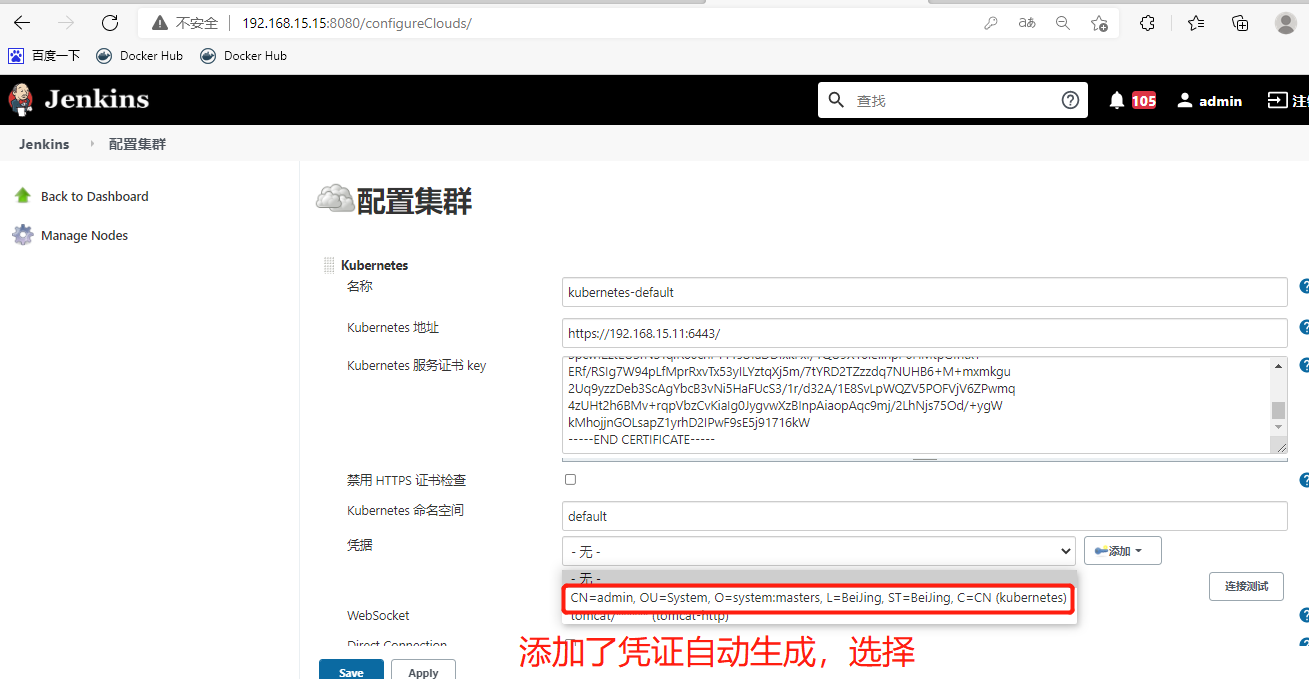
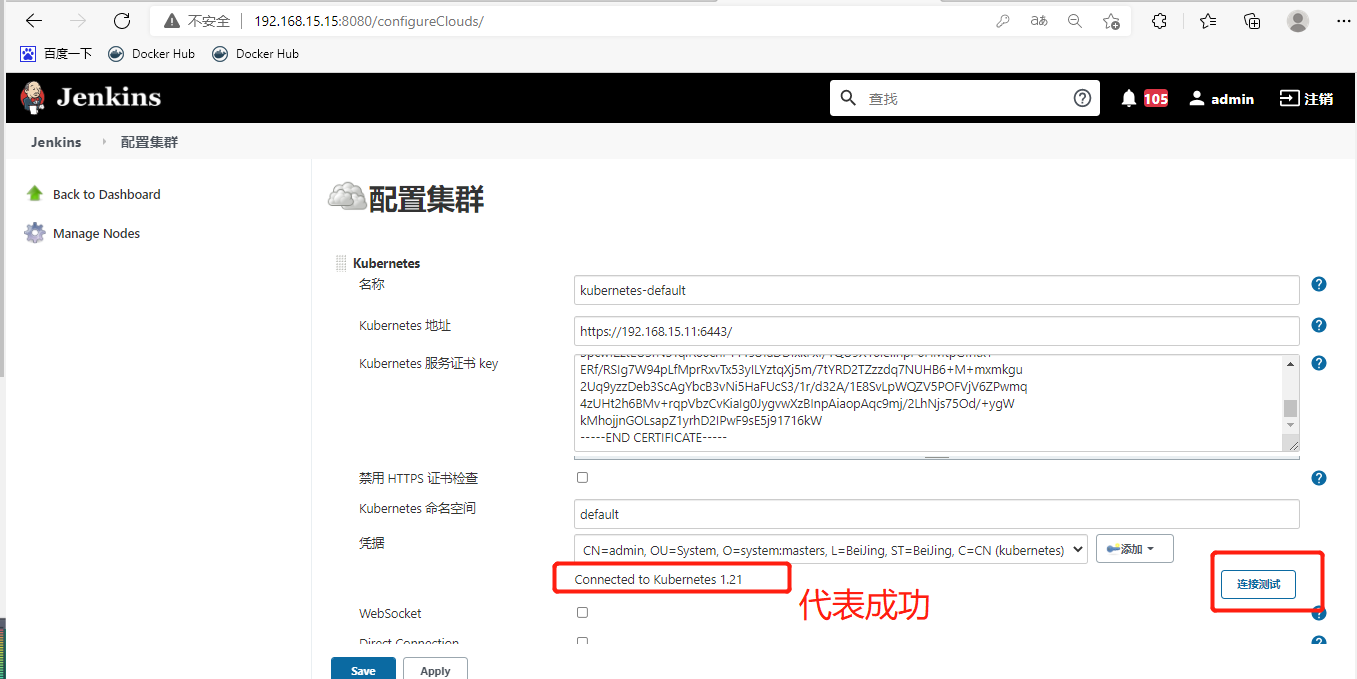
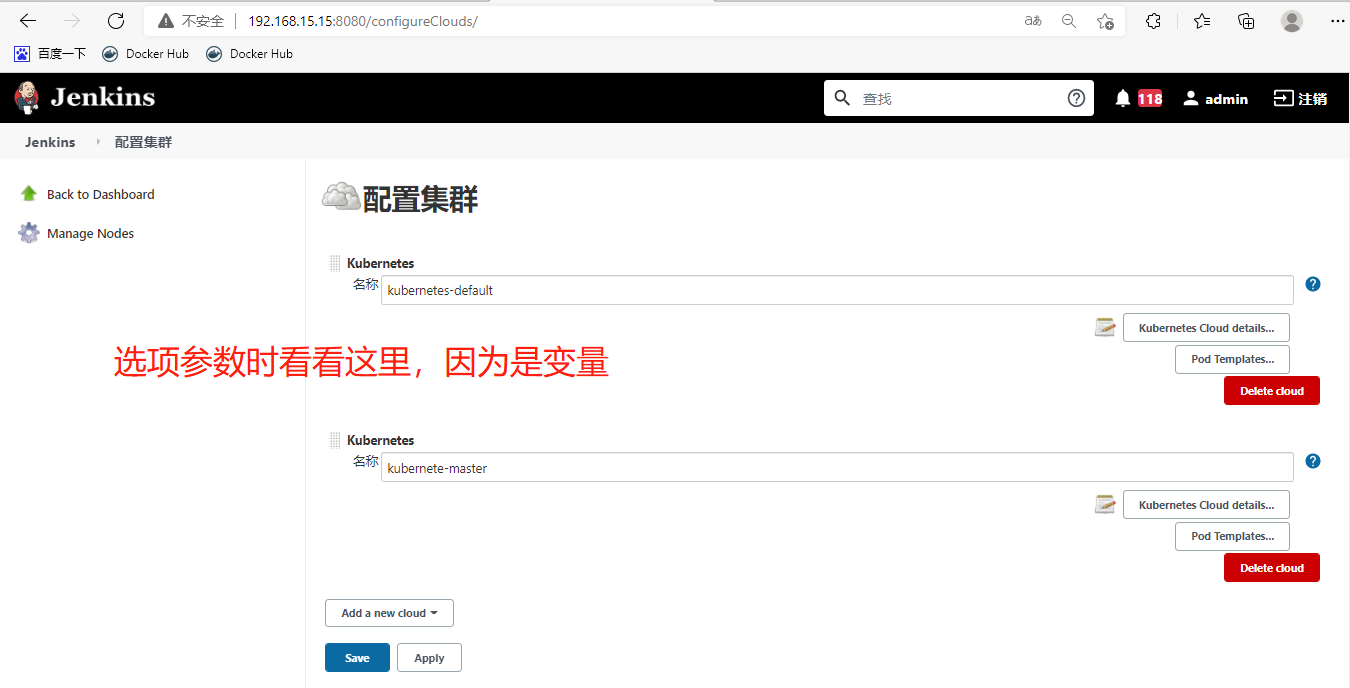
保存!还可以用这种方法配置多个集群
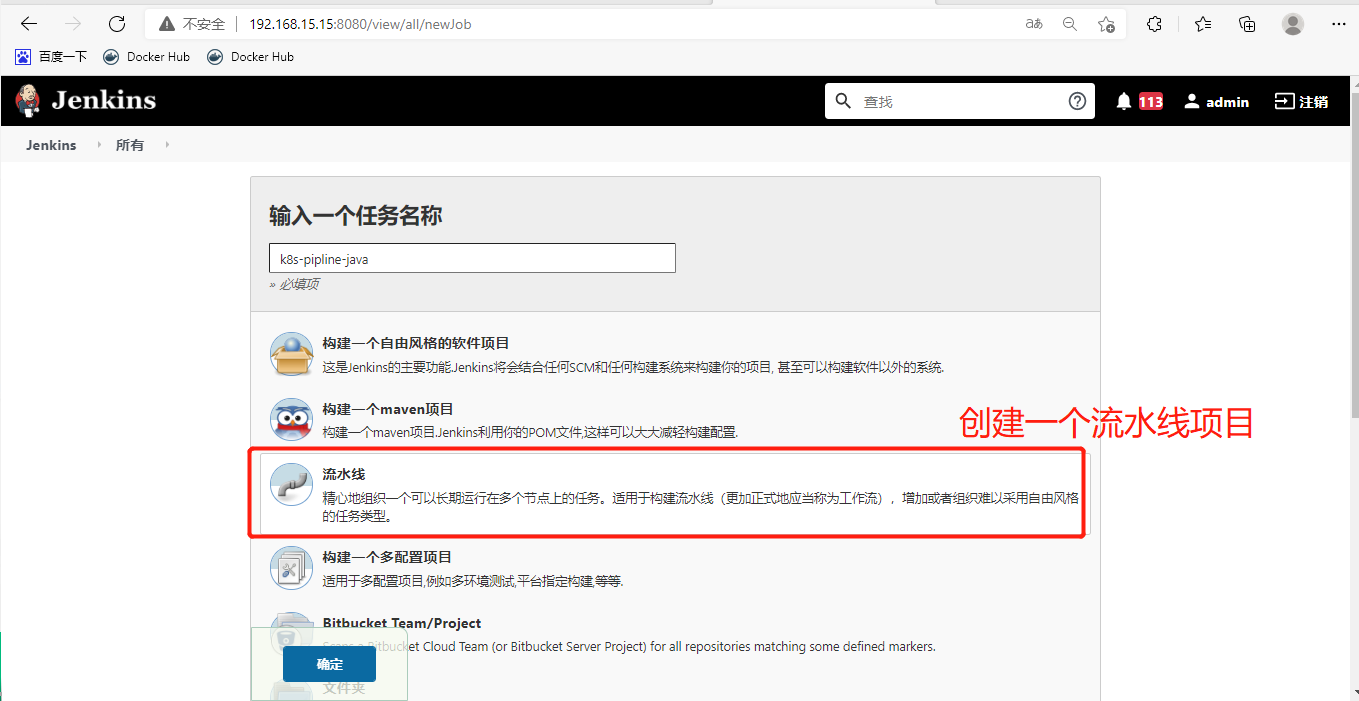
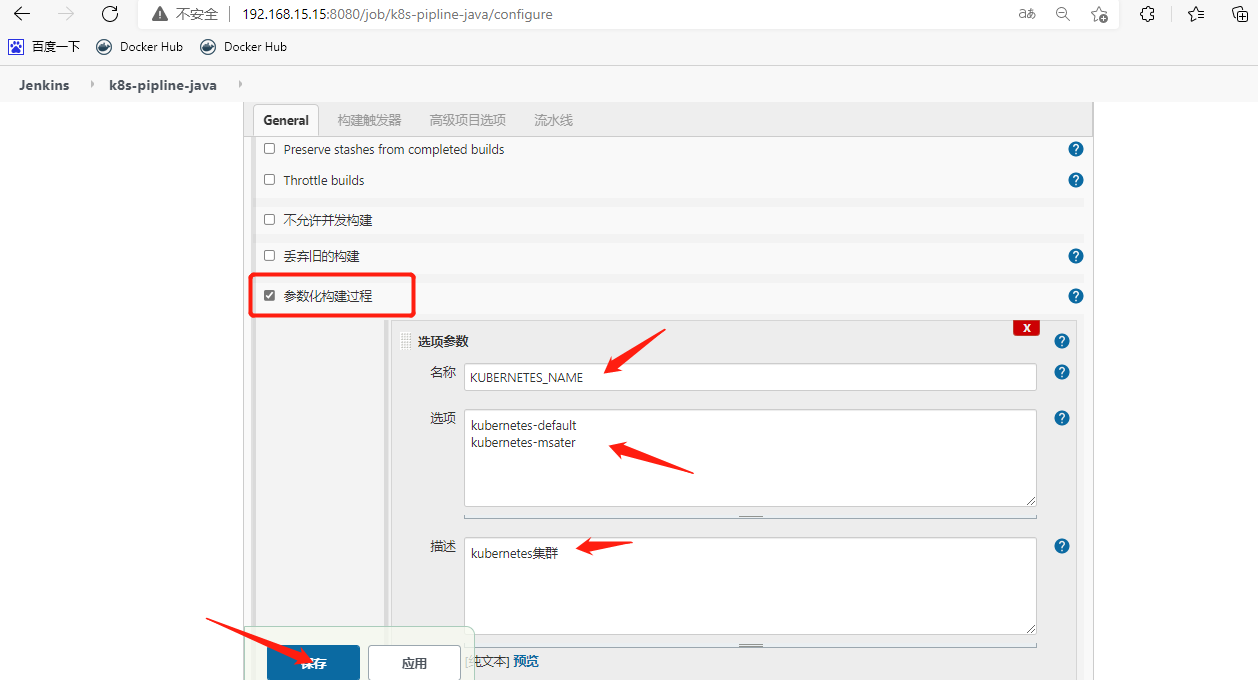
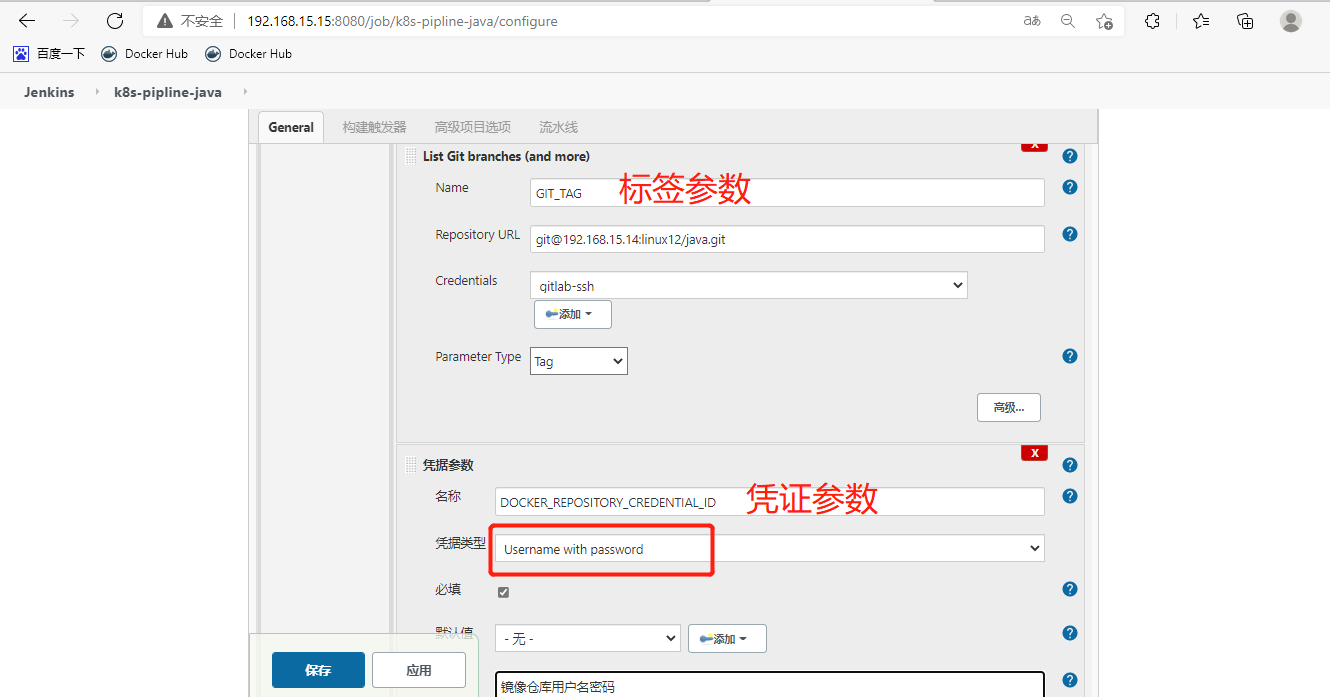
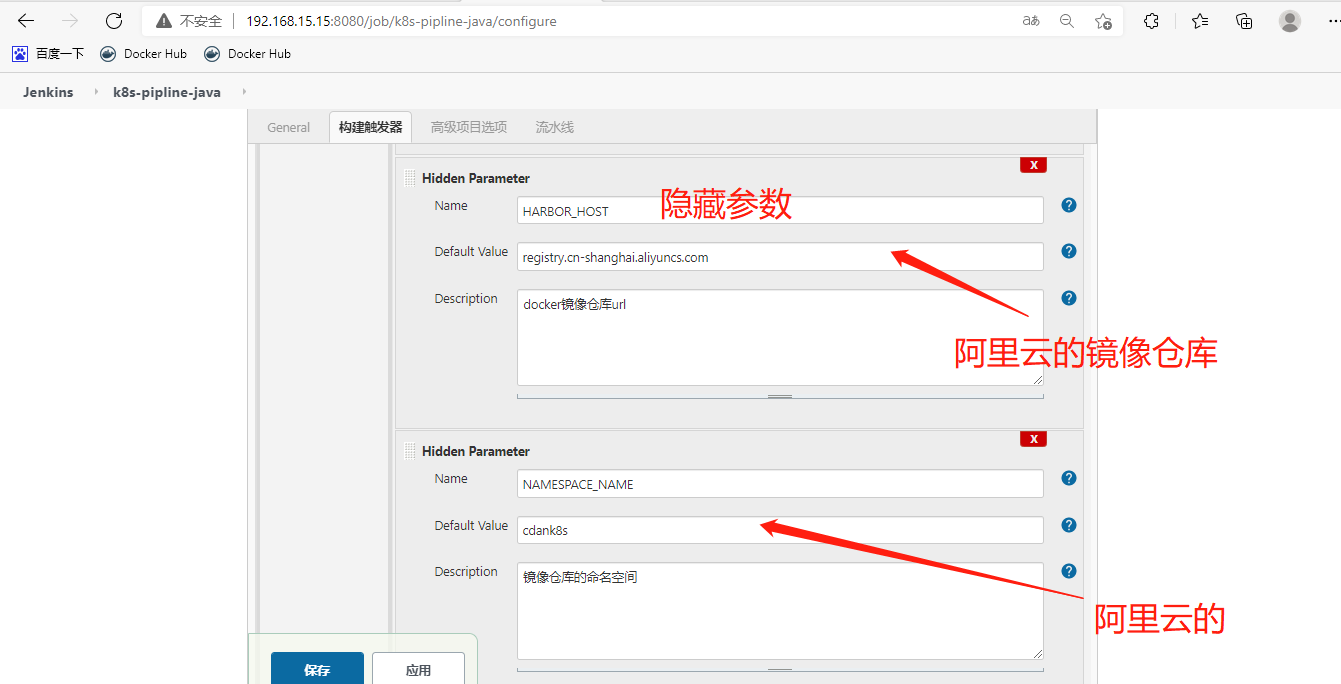
创建流水线项目
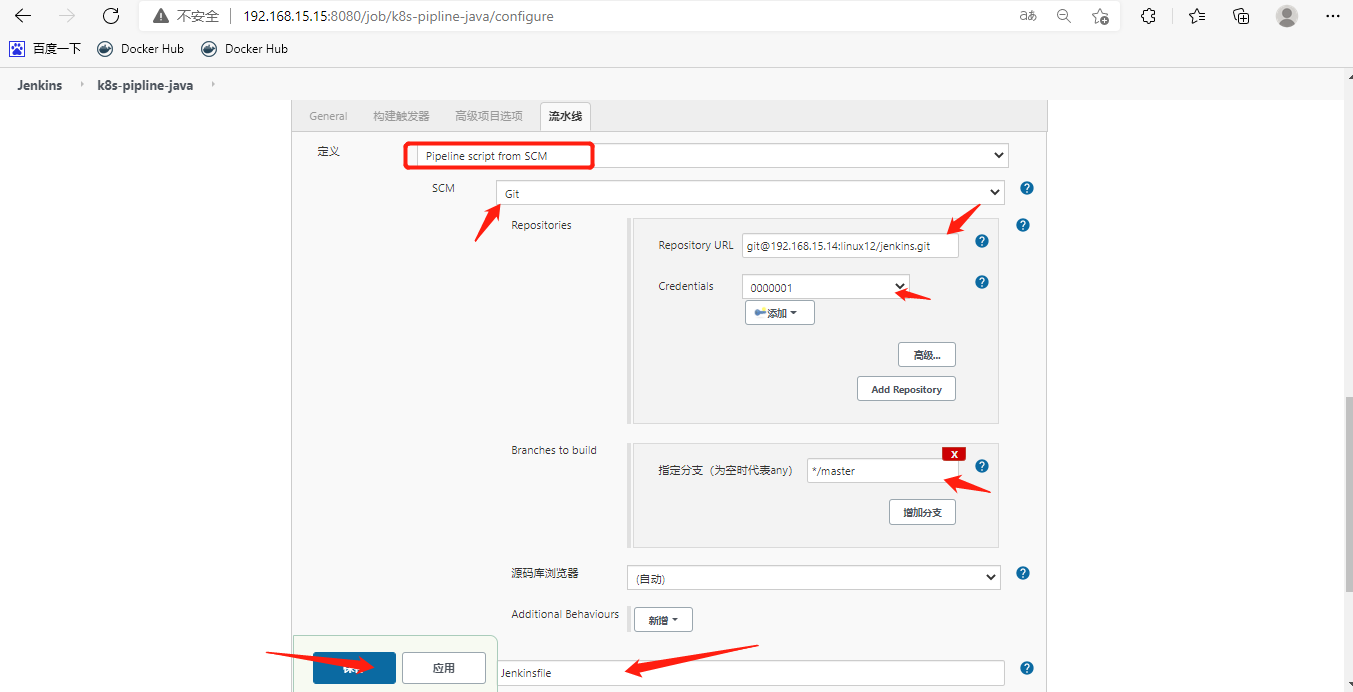

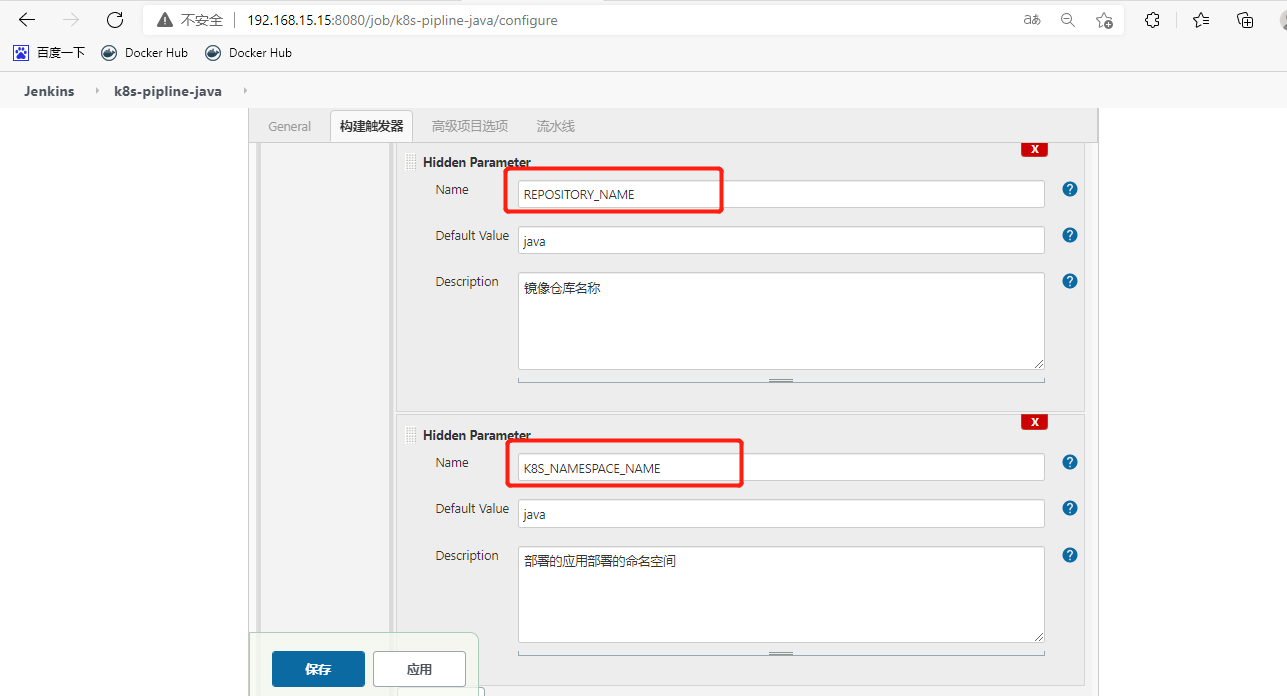
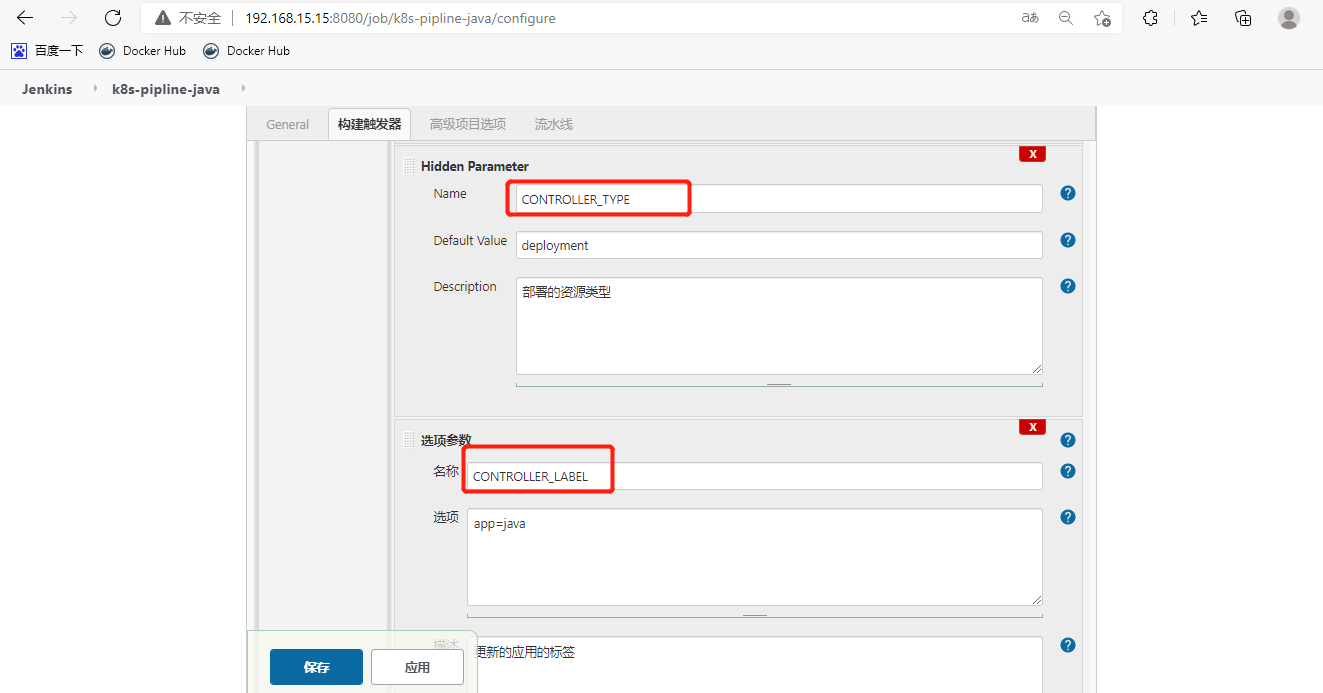
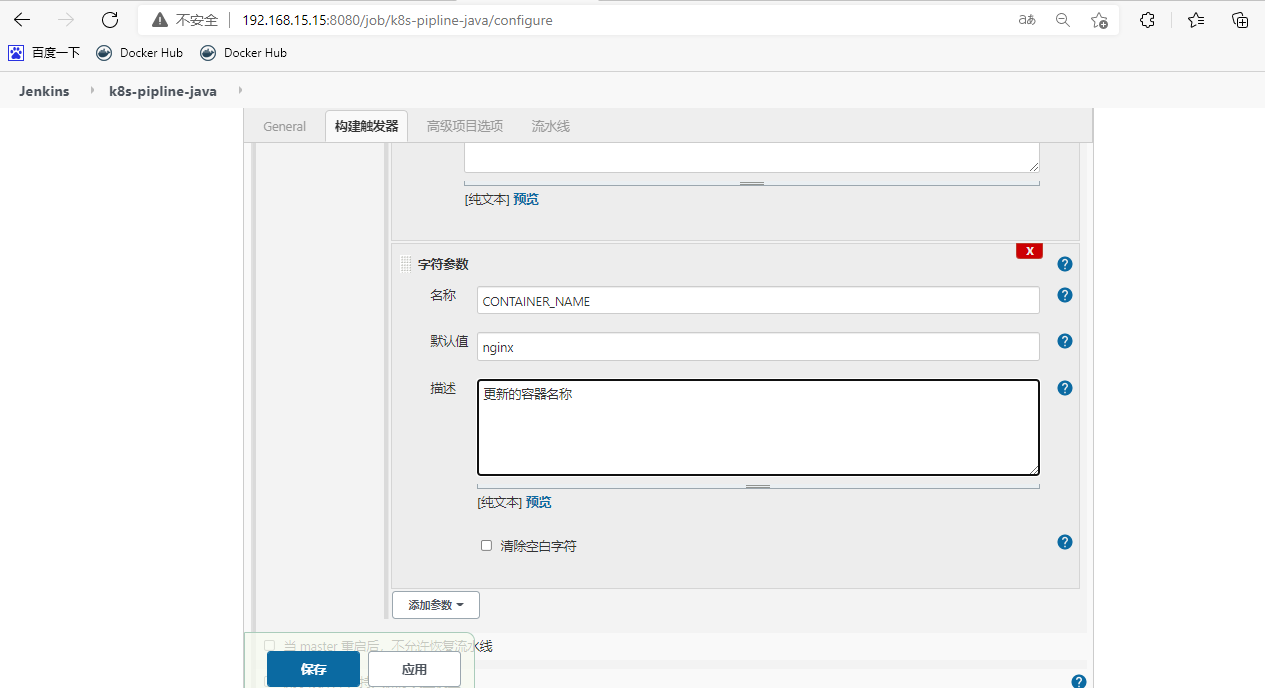
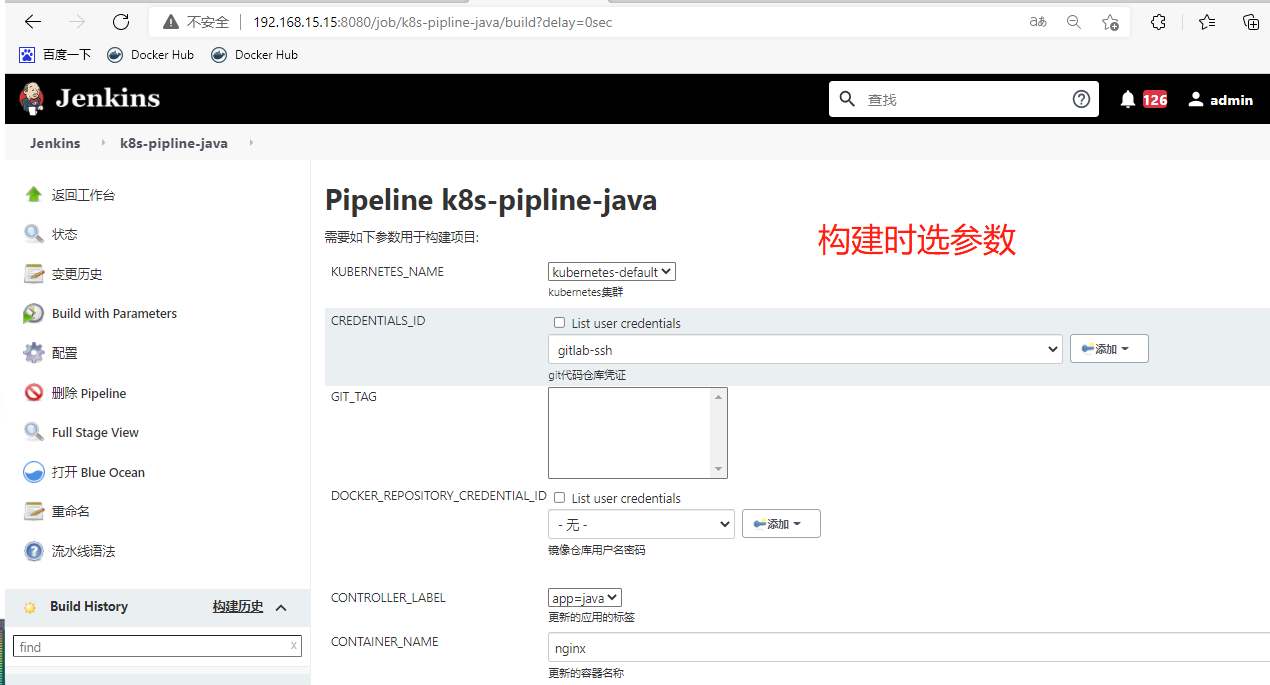
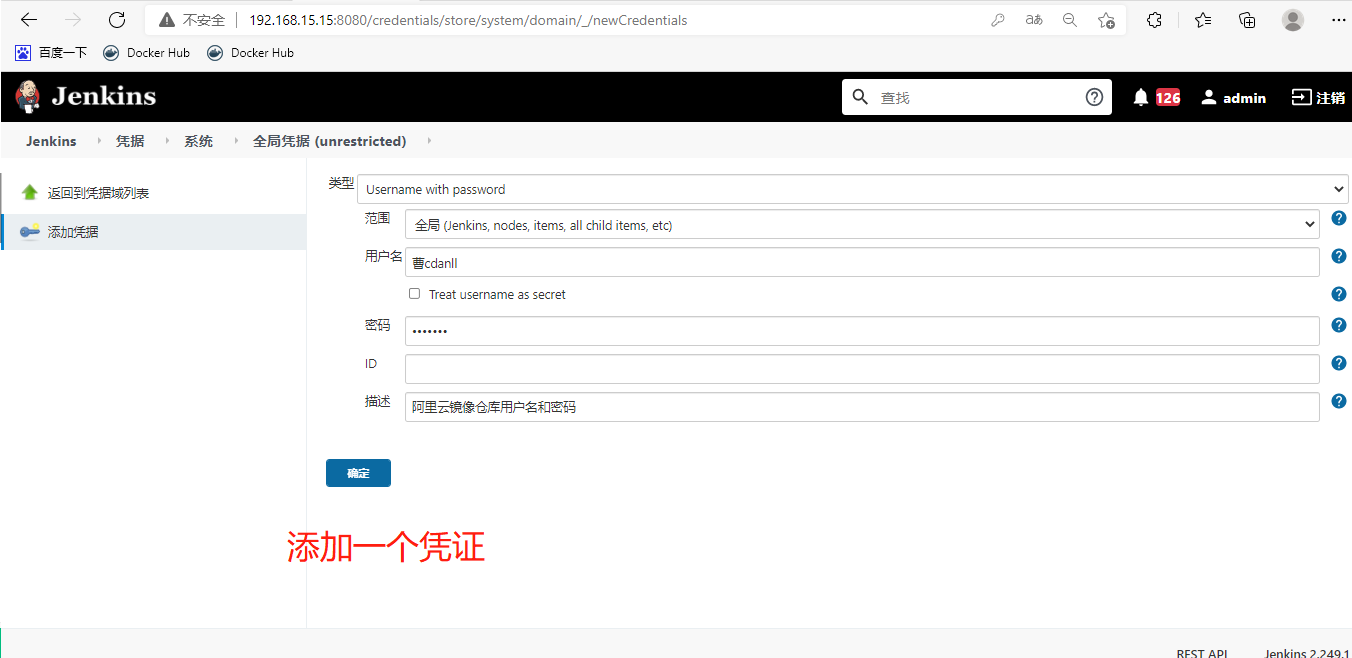
[root@k8s-m-01 ~]# vim java.yaml
kind: Namespace
apiVersion: v1
metadata:
name: java
---
kind: Deployment
apiVersion: apps/v1
metadata:
name: java
namespace: java
labels:
app: java
spec:
selector:
matchLabels:
app: java
template:
metadata:
labels:
app: java
spec:
imagePullSecrets:
- name: aliyun-registry-key
containers:
- name: java
image: tomcat
imagePullPolicy: IfNotPresent
---
kind: Service
apiVersion: v1
metadata:
name: java-svc
namespace: java
spec:
ports:
- port: 8080
targetPort: 8080
name: java
selector:
app: java
---
kind: Ingress
apiVersion: networking.k8s.io/v1
metadata:
name: java-svc-ingress
namespace: java
spec:
rules:
- host: "java.test.com"
http:
paths:
- path: "/"
pathType: Prefix
backend:
service:
name: java-svc
port:
number: 8080
[root@k8s-m-01 ~]# kubectl apply -f java.yaml
namespace/java created
deployment.apps/java created
service/java-svc created
ingress.networking.k8s.io/java-svc-ingress created
[root@k8s-m-01 ~]# cd .kube
[root@k8s-m-01 .kube]# kubectl create secret generic kubeconfig --from-file=config
secret/kubeconfig created
[root@jenkins ~]# kubectl create secret generic aliyun-registry-key
secret/aliyun-registry-key created
[root@jenkins ~]# cd /var/lib/jenkins/
[root@jenkins jenkins]# vim config.xml
...
<slaveAgentPort>-1</slaveAgentPort> #端口会冲突,-1改成8081或者别的
...
[root@jenkins jenkins]# systemctl restart jenkins
#解析域名
192.168.15.11 java.test.com

**构建后,会和k8s进行连接。拉取镜像,创建pod **