我的sysmon采集全量数据配置:
<!-- FILTERING: Filter conditions available for use are: is,is not,contains,contains any,is any,contains all,excludes,excludes any,excludes all,begin with,not begin with,end with,not end with,less than,more than,image COMPOUND RULE SAMPLE: <Rule groupRelation="and" name=""> <SampleField1 condition="contains">SampleValue</SampleField1> <SampleField2 condition="contains">SampleValue</SampleField2> </Rule> --> <Sysmon schemaversion="4.82"> <HashAlgorithms>*</HashAlgorithms> <DnsLookup>False</DnsLookup> <CheckRevocation>False</CheckRevocation> <EventFiltering> <!--SYSMON EVENT ID 1 : Process Create [ProcessCreate]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, FileVersion, Description, Product, Company, OriginalFileName, CommandLine, CurrentDirectory, User, LogonGuid, LogonId, TerminalSessionId, IntegrityLevel, Hashes, ParentProcessGuid, ParentProcessId, ParentImage, ParentCommandLine, ParentUser--> <RuleGroup name="" groupRelation="or"> <ProcessCreate onmatch="exclude"> </ProcessCreate> </RuleGroup> <!--SYSMON EVENT ID 2 : File creation time changed [FileCreateTime]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, TargetFilename, CreationUtcTime, PreviousCreationUtcTime, User--> <RuleGroup name="" groupRelation="or"> <FileCreateTime onmatch="exclude"> </FileCreateTime> </RuleGroup> <!--SYSMON EVENT ID 3 : Network connection detected [NetworkConnect]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, User, Protocol, Initiated, SourceIsIpv6, SourceIp, SourceHostname, SourcePort, SourcePortName, DestinationIsIpv6, DestinationIp, DestinationHostname, DestinationPort, DestinationPortName--> <RuleGroup name="" groupRelation="or"> <NetworkConnect onmatch="exclude"> </NetworkConnect> </RuleGroup> <!--SYSMON EVENT ID 5 : Process terminated [ProcessTerminate]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, User--> <RuleGroup name="" groupRelation="or"> <ProcessTerminate onmatch="exclude"> </ProcessTerminate> </RuleGroup> <!--SYSMON EVENT ID 6 : Driver loaded [DriverLoad]--> <!--DATA: RuleName, UtcTime, ImageLoaded, Hashes, Signed, Signature, SignatureStatus--> <RuleGroup name="" groupRelation="or"> <DriverLoad onmatch="exclude"> </DriverLoad> </RuleGroup> <!--SYSMON EVENT ID 7 : Image loaded [ImageLoad]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, ImageLoaded, FileVersion, Description, Product, Company, OriginalFileName, Hashes, Signed, Signature, SignatureStatus, User--> <RuleGroup name="" groupRelation="or"> <ImageLoad onmatch="exclude"> </ImageLoad> </RuleGroup> <!--SYSMON EVENT ID 8 : CreateRemoteThread detected [CreateRemoteThread]--> <!--DATA: RuleName, UtcTime, SourceProcessGuid, SourceProcessId, SourceImage, TargetProcessGuid, TargetProcessId, TargetImage, NewThreadId, StartAddress, StartModule, StartFunction, SourceUser, TargetUser--> <RuleGroup name="" groupRelation="or"> <CreateRemoteThread onmatch="exclude"> </CreateRemoteThread> </RuleGroup> <!--SYSMON EVENT ID 9 : RawAccessRead detected [RawAccessRead]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, Device, User--> <RuleGroup name="" groupRelation="or"> <RawAccessRead onmatch="exclude"> </RawAccessRead> </RuleGroup> <!--SYSMON EVENT ID 10 : Process accessed [ProcessAccess]--> <!--DATA: RuleName, UtcTime, SourceProcessGUID, SourceProcessId, SourceThreadId, SourceImage, TargetProcessGUID, TargetProcessId, TargetImage, GrantedAccess, CallTrace, SourceUser, TargetUser--> <RuleGroup name="" groupRelation="or"> <ProcessAccess onmatch="exclude"> </ProcessAccess> </RuleGroup> <!--SYSMON EVENT ID 11 : File created [FileCreate]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, TargetFilename, CreationUtcTime, User--> <RuleGroup name="" groupRelation="or"> <FileCreate onmatch="exclude"> </FileCreate> </RuleGroup> <!--SYSMON EVENT ID 12 : Registry object added or deleted [RegistryEvent]--> <!--DATA: RuleName, EventType, UtcTime, ProcessGuid, ProcessId, Image, TargetObject, User--> <!--SYSMON EVENT ID 13 : Registry value set [RegistryEvent]--> <!--DATA: RuleName, EventType, UtcTime, ProcessGuid, ProcessId, Image, TargetObject, Details, User--> <!--SYSMON EVENT ID 14 : Registry object renamed [RegistryEvent]--> <!--DATA: RuleName, EventType, UtcTime, ProcessGuid, ProcessId, Image, TargetObject, NewName, User--> <RuleGroup name="" groupRelation="or"> <RegistryEvent onmatch="exclude"> </RegistryEvent> </RuleGroup> <!--SYSMON EVENT ID 15 : File stream created [FileCreateStreamHash]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, TargetFilename, CreationUtcTime, Hash, Contents, User--> <RuleGroup name="" groupRelation="or"> <FileCreateStreamHash onmatch="exclude"> </FileCreateStreamHash> </RuleGroup> <!--SYSMON EVENT ID 17 : Pipe Created [PipeEvent]--> <!--DATA: RuleName, EventType, UtcTime, ProcessGuid, ProcessId, PipeName, Image, User--> <!--SYSMON EVENT ID 18 : Pipe Connected [PipeEvent]--> <!--DATA: RuleName, EventType, UtcTime, ProcessGuid, ProcessId, PipeName, Image, User--> <RuleGroup name="" groupRelation="or"> <PipeEvent onmatch="exclude"> </PipeEvent> </RuleGroup> <!--SYSMON EVENT ID 19 : WmiEventFilter activity detected [WmiEvent]--> <!--DATA: RuleName, EventType, UtcTime, Operation, User, EventNamespace, Name, Query--> <!--SYSMON EVENT ID 20 : WmiEventConsumer activity detected [WmiEvent]--> <!--DATA: RuleName, EventType, UtcTime, Operation, User, Name, Type, Destination--> <!--SYSMON EVENT ID 21 : WmiEventConsumerToFilter activity detected [WmiEvent]--> <!--DATA: RuleName, EventType, UtcTime, Operation, User, Consumer, Filter--> <RuleGroup name="" groupRelation="or"> <WmiEvent onmatch="exclude"> </WmiEvent> </RuleGroup> <!--SYSMON EVENT ID 22 : Dns query [DnsQuery]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, QueryName, QueryStatus, QueryResults, Image, User--> <RuleGroup name="" groupRelation="or"> <DnsQuery onmatch="exclude"> </DnsQuery> </RuleGroup> <!--SYSMON EVENT ID 23 : File Delete archived [FileDelete]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, User, Image, TargetFilename, Hashes, IsExecutable, Archived--> <RuleGroup name="" groupRelation="or"> <FileDelete onmatch="exclude"> </FileDelete> </RuleGroup> <!--SYSMON EVENT ID 24 : Clipboard changed [ClipboardChange]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, Session, ClientInfo, Hashes, Archived, User--> <RuleGroup name="" groupRelation="or"> <ClipboardChange onmatch="exclude"> </ClipboardChange> </RuleGroup> <!--SYSMON EVENT ID 25 : Process Tampering [ProcessTampering]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, Image, Type, User--> <RuleGroup name="" groupRelation="or"> <ProcessTampering onmatch="exclude"> </ProcessTampering> </RuleGroup> <!--SYSMON EVENT ID 26 : File Delete logged [FileDeleteDetected]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, User, Image, TargetFilename, Hashes, IsExecutable--> <RuleGroup name="" groupRelation="or"> <FileDeleteDetected onmatch="exclude"> </FileDeleteDetected> </RuleGroup> <!--SYSMON EVENT ID 27 : File Block Executable [FileBlockExecutable]--> <!--DATA: RuleName, UtcTime, ProcessGuid, ProcessId, User, Image, TargetFilename, Hashes--> <RuleGroup name="" groupRelation="or"> <FileBlockExecutable onmatch="exclude"> </FileBlockExecutable> </RuleGroup> </EventFiltering> </Sysmon>
看看采集效果:



sysmon采集事件的含义说明:
Events
On Vista and higher, events are stored in Applications and Services Logs/Microsoft/Windows/Sysmon/Operational, and on older systems events are written to the System event log. Event timestamps are in UTC standard time.
The following are examples of each event type that Sysmon generates.
Event ID 1: Process creation
The process creation event provides extended information about a newly created process. The full command line provides context on the process execution. The ProcessGUID field is a unique value for this process across a domain to make event correlation easier. The hash is a full hash of the file with the algorithms in the HashType field.
Event ID 2: A process changed a file creation time
The change file creation time event is registered when a file creation time is explicitly modified by a process. This event helps tracking the real creation time of a file. Attackers may change the file creation time of a backdoor to make it look like it was installed with the operating system. Note that many processes legitimately change the creation time of a file; it does not necessarily indicate malicious activity.
Event ID 3: Network connection
The network connection event logs TCP/UDP connections on the machine. It is disabled by default. Each connection is linked to a process through the ProcessId and ProcessGUID fields. The event also contains the source and destination host names IP addresses, port numbers and IPv6 status.
Event ID 4: Sysmon service state changed
The service state change event reports the state of the Sysmon service (started or stopped).
Event ID 5: Process terminated
The process terminate event reports when a process terminates. It provides the UtcTime, ProcessGuid and ProcessId of the process.
Event ID 6: Driver loaded
The driver loaded events provides information about a driver being loaded on the system. The configured hashes are provided as well as signature information. The signature is created asynchronously for performance reasons and indicates if the file was removed after loading.
Event ID 7: Image loaded
The image loaded event logs when a module is loaded in a specific process. This event is disabled by default and needs to be configured with the –l option. It indicates the process in which the module is loaded, hashes and signature information. The signature is created asynchronously for performance reasons and indicates if the file was removed after loading. This event should be configured carefully, as monitoring all image load events will generate a large number of events.
Event ID 8: CreateRemoteThread
The CreateRemoteThread event detects when a process creates a thread in another process. This technique is used by malware to inject code and hide in other processes. The event indicates the source and target process. It gives information on the code that will be run in the new thread: StartAddress, StartModule and StartFunction. Note that StartModule and StartFunction fields are inferred, they might be empty if the starting address is outside loaded modules or known exported functions.
Event ID 9: RawAccessRead
The RawAccessRead event detects when a process conducts reading operations from the drive using the \\.\ denotation. This technique is often used by malware for data exfiltration of files that are locked for reading, as well as to avoid file access auditing tools. The event indicates the source process and target device.
Event ID 10: ProcessAccess
The process accessed event reports when a process opens another process, an operation that’s often followed by information queries or reading and writing the address space of the target process. This enables detection of hacking tools that read the memory contents of processes like Local Security Authority (Lsass.exe) in order to steal credentials for use in Pass-the-Hash attacks. Enabling it can generate significant amounts of logging if there are diagnostic utilities active that repeatedly open processes to query their state, so it generally should only be done so with filters that remove expected accesses.
Event ID 11: FileCreate
File create operations are logged when a file is created or overwritten. This event is useful for monitoring autostart locations, like the Startup folder, as well as temporary and download directories, which are common places malware drops during initial infection.
Event ID 12: RegistryEvent (Object create and delete)
Registry key and value create and delete operations map to this event type, which can be useful for monitoring for changes to Registry autostart locations, or specific malware registry modifications.
Sysmon uses abbreviated versions of Registry root key names, with the following mappings:
| Key name | Abbreviation |
|---|---|
HKEY_LOCAL_MACHINE |
HKLM |
HKEY_USERS |
HKU |
HKEY_LOCAL_MACHINE\System\ControlSet00x |
HKLM\System\CurrentControlSet |
HKEY_LOCAL_MACHINE\Classes |
HKCR |
Event ID 13: RegistryEvent (Value Set)
This Registry event type identifies Registry value modifications. The event records the value written for Registry values of type DWORD and QWORD.
Event ID 14: RegistryEvent (Key and Value Rename)
Registry key and value rename operations map to this event type, recording the new name of the key or value that was renamed.
Event ID 15: FileCreateStreamHash
This event logs when a named file stream is created, and it generates events that log the hash of the contents of the file to which the stream is assigned (the unnamed stream), as well as the contents of the named stream. There are malware variants that drop their executables or configuration settings via browser downloads, and this event is aimed at capturing that based on the browser attaching a Zone.Identifier "mark of the web" stream.
Event ID 16: ServiceConfigurationChange
This event logs changes in the Sysmon configuration - for example when the filtering rules are updated.
Event ID 17: PipeEvent (Pipe Created)
This event generates when a named pipe is created. Malware often uses named pipes for interprocess communication.
Event ID 18: PipeEvent (Pipe Connected)
This event logs when a named pipe connection is made between a client and a server.
Event ID 19: WmiEvent (WmiEventFilter activity detected)
When a WMI event filter is registered, which is a method used by malware to execute, this event logs the WMI namespace, filter name and filter expression.
Event ID 20: WmiEvent (WmiEventConsumer activity detected)
This event logs the registration of WMI consumers, recording the consumer name, log, and destination.
Event ID 21: WmiEvent (WmiEventConsumerToFilter activity detected)
When a consumer binds to a filter, this event logs the consumer name and filter path.
Event ID 22: DNSEvent (DNS query)
This event is generated when a process executes a DNS query, whether the result is successful or fails, cached or not. The telemetry for this event was added for Windows 8.1 so it is not available on Windows 7 and earlier.
Event ID 23: FileDelete (File Delete archived)
A file was deleted. Additionally to logging the event, the deleted file is also saved in the ArchiveDirectory (which is C:\Sysmon by default). Under normal operating conditions this directory might grow to an unreasonable size - see event ID 26: FileDeleteDetected for similar behavior but without saving the deleted files.
Event ID 24: ClipboardChange (New content in the clipboard)
This event is generated when the system clipboard contents change.
Event ID 25: ProcessTampering (Process image change)
This event is generated when process hiding techniques such as "hollow" or "herpaderp" are being detected.
Event ID 26: FileDeleteDetected (File Delete logged)
A file was deleted.
Event ID 255: Error
This event is generated when an error occurred within Sysmon. They can happen if the system is under heavy load and certain tasked could not be performed or a bug exists in the Sysmon service. You can report any bugs on the Sysinternals forum or over Twitter (@markrussinovich).
Configuration files
Configuration files can be specified after the -i (installation) or -c (installation) configuration switches. They make it easier to deploy a preset configuration and to filter captured events.
A simple configuration xml file looks like this:
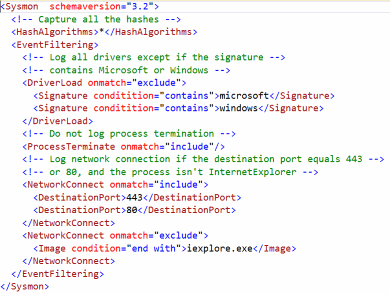
The configuration file contains a schemaversion attribute on the Sysmon tag. This version is independent from the Sysmon binary version and allows the parsing of older configuration files. You can get the current schema version by using the “-? config” command line. Configuration entries are directly under the Sysmon tag and filters are under the EventFiltering tag.
真正的LPC攻击复现:todo,下午实践下
https://malwarenailed.blogspot.com/2017/10/hunting-mimikatz-using-sysmon-elk-part.html
我在受害者端点上利用 EternalBlue。 建立反向 https (8443) 时请注意端口 (49228)


我寻找 lsass.exe 进程,以便将恶意代码从 spoolsvc.exe 迁移到 lsass.exe ==》提权?


我运行meterpreter的本机hashdump,然后加载mimkatz并运行它的命令





我再次查看事件以查找相关日志:

我们可以看到 lsass.exe 连接到管道 \wkssvc

恶意进程还连接到 \wkssvc 管道以进行基于 LPC 的通信



注意服务的命令行(ImagePath)值



服务开始值设置为手动








最后我们看到了 CreateRemotethread 事件(事件 8),其中 TargetImage 是 lsass.exe。 这是一个高保真事件,几乎总是表示恶意:



wsmprovhost.exe 是 WinRM 远程 Powershell 会话

我们可以看到这个进程连接到管道 \lsass


wsmprovhost.exe 创建了一些临时的 powershell 脚本和模块
见原文吧!
这里我们看到目标端口 5985,用于使用 winrm 进行 powershell 远程处理
接下来我们看到 wsmprovhost.exe 访问 lsass.exe 进程。 GrantedAccess 值为 0x143a 。 当 mimikatz 从meterpreter ( 0x1400 OR 0x1410 OR 0x147a) 又 mimikatz 二进制文件时,这又是不同的。
让我们也看看一些检测 Mimikatz 相关 PS ScriptBlock Logs 的方法:
注入内存的去混淆 PS 代码如下所示(事件 ID 4104)。 注意 VirtualAlloc 和 memset
还可以看到其他 PS 日志(如事件 ID 800)调用 System.Reflection 函数以在运行时在内存中创建程序集。 请参阅我 过去的博客文章 ,了解如何扭转这一点。