-
编译得到s文件
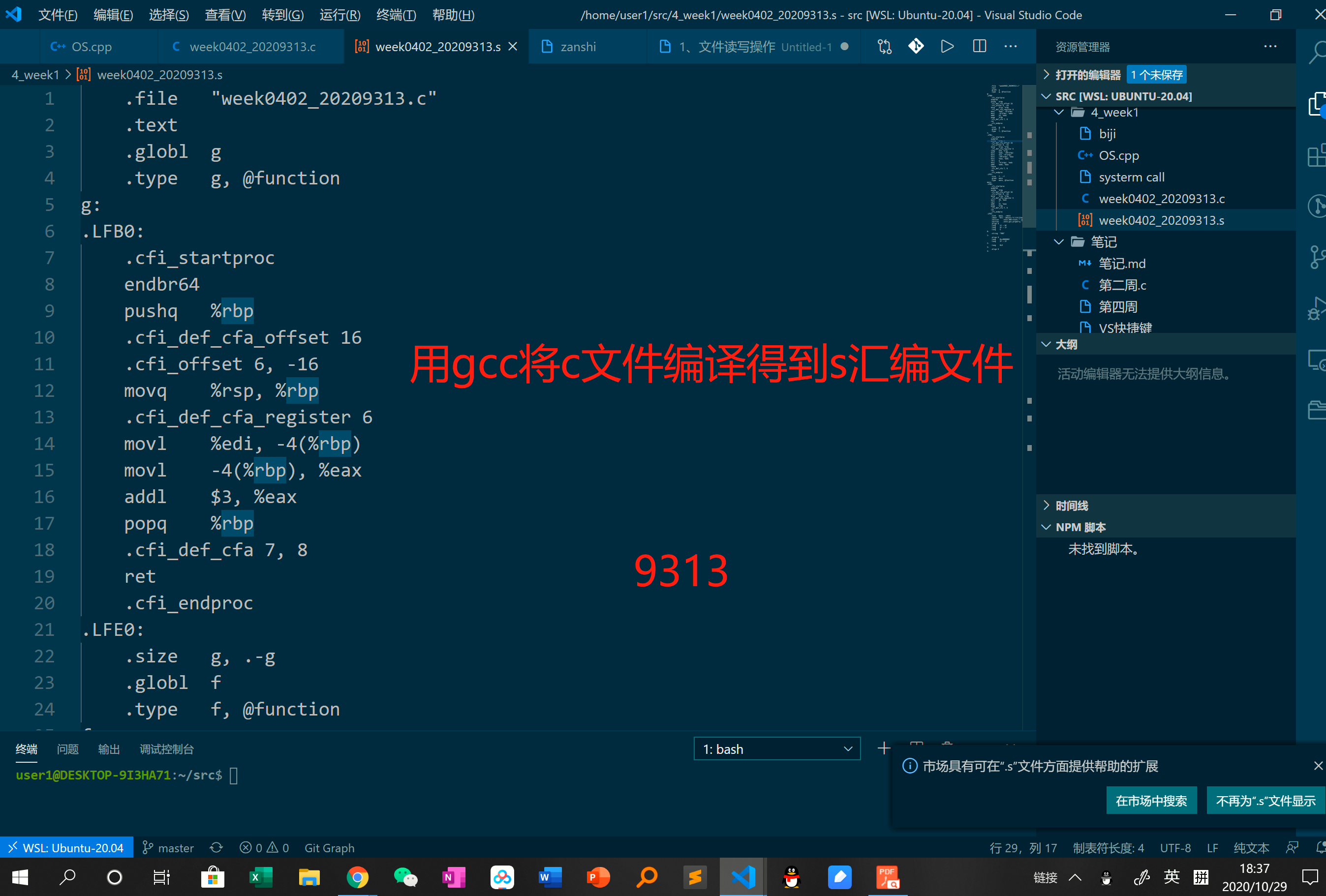
-
清理.开头的信息,简化分析

-
装m32的依赖库
sudo apt-get install libc6-dev-i386
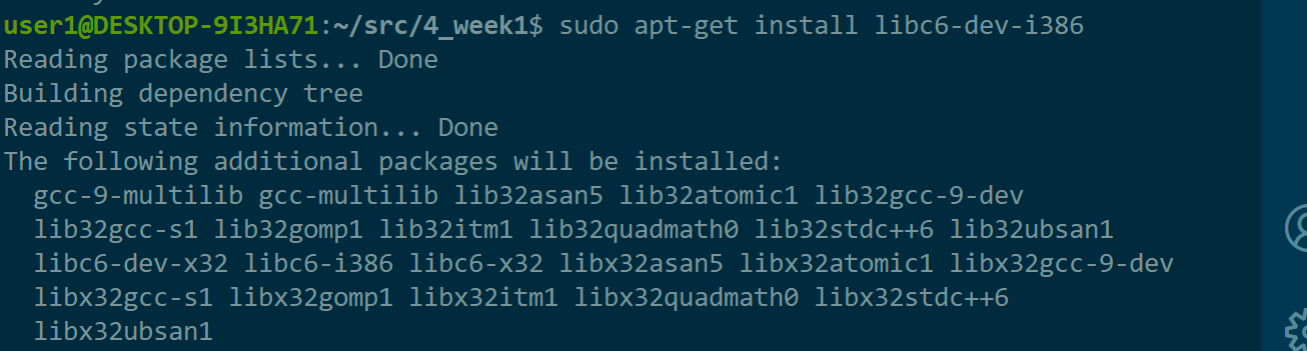
否则报错:
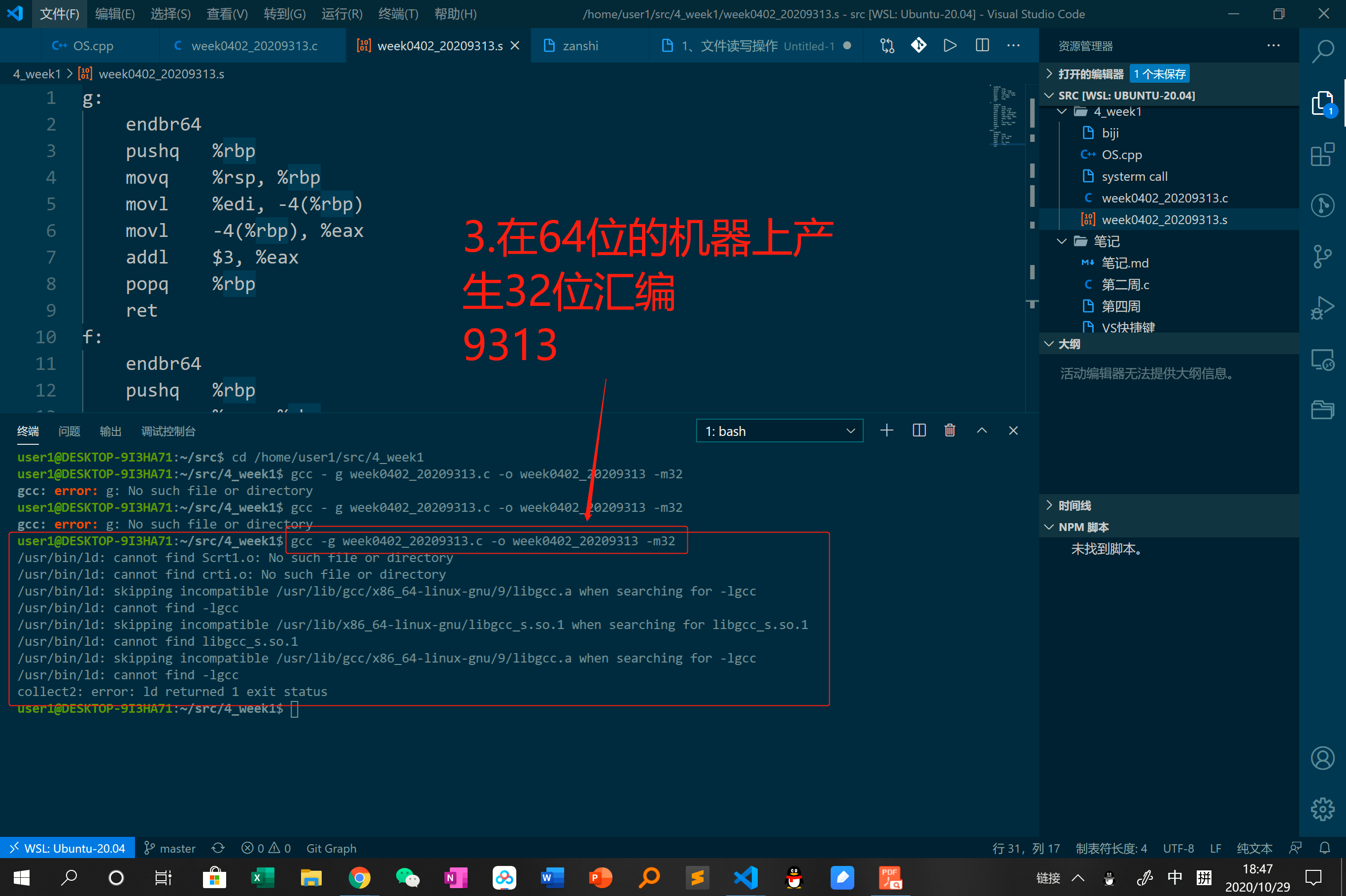
-
使用gcc - g example.c -o example -m32指令在64位的机器上产生32位汇编,然后使用gdb example指令进入gdb调试器:
gcc - g week0402_20209313.c -o week0402_20209313 -m32
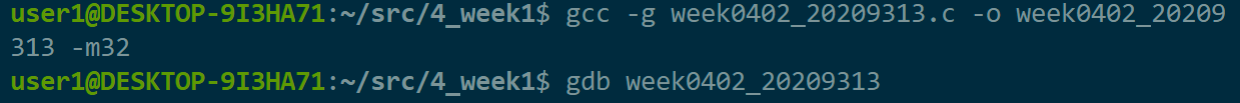
-
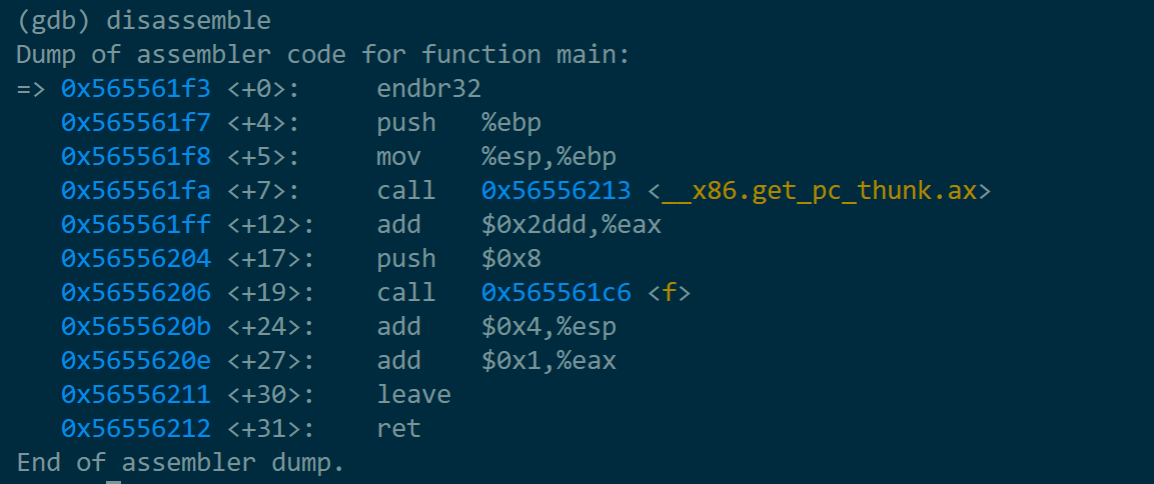
进入之后先在main函数处设置一个断点,再run一下,使用disassemble指令获取汇编代码,
break main
r
disassemble
- 用i(info) r(registers)指令查看各寄存器的值:
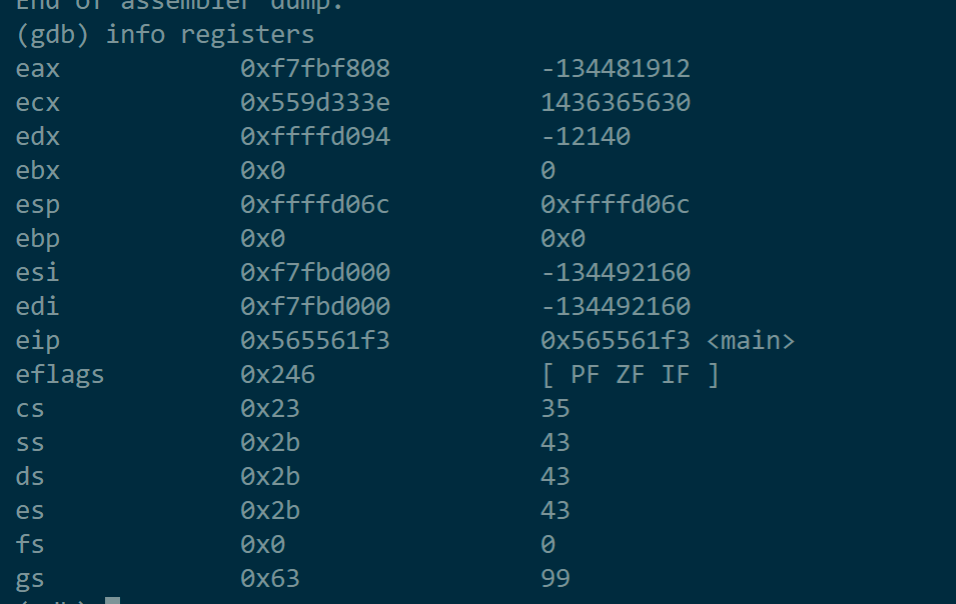
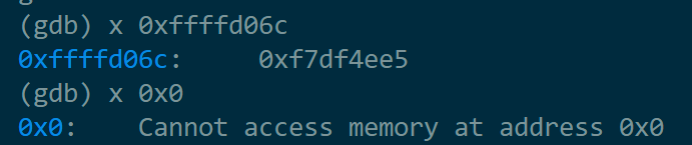
可见此时主函数的栈基址为0xffffd06c,用x(examine)指令查看内存地址中的值,但目前%esp所指堆栈内容为0,%ebp所指内容也为0
gdb中使用“x”命令来打印内存的值,格式为“x/nfu addr”。含义为以f格式打印从addr开始的n个长度单元为u的内存值。参数具体含义如下:
a)n:输出单元的个数。
b)f:是输出格式。比如x是以16进制形式输出,o是以8进制形式输出,等等。
c)u:标明一个单元的长度。b是一个byte,h是两个byte(halfword),w是四个byte(word),g是八个byte(giant word)。
- si到f函数
8.f

return f(8)+1;
call 0x565561c6
eax 0x56558fdc 1448447964
esp 0xffffd064 0xffffd064
ebp 0xffffd068 0xffffd068
eip 0x56556206 0x56556206 <main+19>
(gdb) x/2a 0xffffd064
0xffffd064: 0x8 0x0
=> 0x565561c6
eax 0x56558fdc 1448447964
esp 0xffffd060 0xffffd060
ebp 0xffffd068 0xffffd068
eip 0x565561c6 0x565561c6
(gdb) x/2a 0xffffd060
0xffffd060: 0x5655620b <main+24> 0x8
=> 0x565561ca <f+4>: push %ebp
(gdb) i r
eax 0x56558fdc 1448447964
esp 0xffffd060 0xffffd060
ebp 0xffffd068 0xffffd068
eip 0x565561ca 0x565561ca <f+4>
(gdb) x/3a 0xffffd060
0xffffd060: 0x5655620b <main+24> 0x8 0x0
=> 0x565561cb <f+5>: mov %esp,%ebp
(gdb) i r
eax 0x56558fdc 1448447964
esp 0xffffd05c 0xffffd05c
ebp 0xffffd068 0xffffd068
eip 0x565561cb 0x565561cb <f+5>
(gdb) x/4a 0xffffd05c
0xffffd05c: 0xffffd068 0x5655620b <main+24> 0x8 0x0
=> 0x565561cd <f+7>: sub $0x10,%esp
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd05c 0xffffd05c
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561cd 0x565561cd <f+7>
eflags 0x212 [ AF IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd05c
0xffffd05c: 0xffffd068 0x5655620b <main+24> 0x8 0x0
=> 0x565561d0 <f+10>: call 0x56556213 <__x86.get_pc_thunk.ax>
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd04c 0xffffd04c
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561d0 0x565561d0 <f+10>
eflags 0x282 [ SF IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd04c
0xffffd04c: 0x56556241 <__libc_csu_init+33> 0xf7fe22d0 0x0 0x0
(gdb) si
0x56556213 in __x86.get_pc_thunk.ax ()
1: x/i $pc
=> 0x56556213 <__x86.get_pc_thunk.ax>: mov (%esp),%eax
(gdb) i r
eax 0x56558fdc 1448447964
esp 0xffffd048 0xffffd048
ebp 0xffffd05c 0xffffd05c
eip 0x56556213 0x56556213
(gdb) x/4a 0xffffd048
0xffffd048: 0x565561d5 <f+15> 0x56556241 <__libc_csu_init+33> 0xf7fe22d0 0x0
=> 0x56556216 <__x86.get_pc_thunk.ax+3>: ret
(gdb) i r
eax 0x565561d5 1448436181
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd048 0xffffd048
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x56556216 0x56556216 <__x86.get_pc_thunk.ax+3>
eflags 0x282 [ SF IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd048
0xffffd048: 0x565561d5 <f+15> 0x56556241 <__libc_csu_init+33> 0xf7fe22d0 0x0
=> 0x565561d5 <f+15>: add $0x2e07,%eax
(gdb) i r
eax 0x565561d5 1448436181
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd04c 0xffffd04c
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561d5 0x565561d5 <f+15>
(gdb) x/4a 0xffffd04c
0xffffd04c: 0x56556241 <__libc_csu_init+33> 0xf7fe22d0 0x0 0x0
5 int i = 13;
1: x/i $pc
=> 0x565561da <f+20>: movl $0xd,-0x4(%ebp)
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd04c 0xffffd04c
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561da 0x565561da <f+20>
--Type
eflags 0x202 [ IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd04c
0xffffd04c: 0x56556241 <__libc_csu_init+33> 0xf7fe22d0 0x0 0x0
6 return g(x)+i;
1: x/i $pc
=> 0x565561e1 <f+27>: pushl 0x8(%ebp)
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd04c 0xffffd04c
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561e1 0x565561e1 <f+27>
eflags 0x202 [ IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd04c
0xffffd04c: 0x56556241 <__libc_csu_init+33> 0xf7fe22d0 0x0 0xd
0x565561e4 6 return g(x)+i;
1: x/i $pc
=> 0x565561e4 <f+30>: call 0x565561ad
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd048 0xffffd048
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561e4 0x565561e4 <f+30>
eflags 0x202 [ IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd048
0xffffd048: 0x8 0x56556241 <__libc_csu_init+33> 0xf7fe22d0 0x0
=> 0x565561ad
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd044 0xffffd044
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561ad 0x565561ad
eflags 0x202 [ IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd044
0xffffd044: 0x565561e9 <f+35> 0x8 0x56556241 <__libc_csu_init+33> 0xf7fe22d0
=> 0x565561b1 <g+4>: push %ebp
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd044 0xffffd044
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561b1 0x565561b1 <g+4>
eflags 0x202 [ IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd044
0xffffd044: 0x565561e9 <f+35> 0x8 0x56556241 <__libc_csu_init+33> 0xf7fe22d0
=> 0x565561b2 <g+5>: mov %esp,%ebp
(gdb) i r
eax 0x56558fdc 1448447964
ecx 0x142fb45d 338670685
edx 0xffffd094 -12140
ebx 0x0 0
esp 0xffffd040 0xffffd040
ebp 0xffffd05c 0xffffd05c
esi 0xf7fbd000 -134492160
edi 0xf7fbd000 -134492160
eip 0x565561b2 0x565561b2 <g+5>
eflags 0x202 [ IF ]
cs 0x23 35
ss 0x2b 43
ds 0x2b 43
es 0x2b 43
fs 0x0 0
gs 0x63 99
(gdb) x/4a 0xffffd040
0xffffd040: 0xffffd05c 0x565561e9 <f+35> 0x8 0x56556241 <__libc_csu_init+33>