系统 : Windows xp
程序 : crackme4
程序下载地址 :http://pan.baidu.com/s/1nu452xN
要求 : 注册机编写
使用工具 : OD & IDA
可在“PEDIY CrackMe 2007”中查找关于此程序的破文,标题为“一个简单CrackMe的破解”。
老规矩,先用IDA载入程序,查看字串表得到关键字串“You cracked the CFF CrackMe #4 ! Please send your solution to aci”。定位字串调用位置并向上翻找到关键算法:
00457BCA |. 8D55 FC lea edx, dword ptr [ebp-4] ; 取变量地址给edx
00457BCD |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457BD3 |. E8 08C3FCFF call 00423EE0 ; 取用户名字符数给eax
00457BD8 |. 837D FC 00 cmp dword ptr [ebp-4], 0
00457BDC |. 75 18 jnz short 00457BF6
00457BDE |. 6A 00 push 0
00457BE0 |. B9 987E4500 mov ecx, 00457E98 ; ASCII "Enter your Name !"
00457BE5 |. BA AC7E4500 mov edx, 00457EAC ; ASCII "You must enter your Name !"
00457BEA |. A1 98A54500 mov eax, dword ptr [45A598]
00457BEF |. 8B00 mov eax, dword ptr [eax]
00457BF1 |. E8 3A85FEFF call 00440130
00457BF6 |> 8D55 FC lea edx, dword ptr [ebp-4] ; 取用户名字串地址给edx
00457BF9 |. 8B83 DC020000 mov eax, dword ptr [ebx+2DC]
00457BFF |. E8 DCC2FCFF call 00423EE0
00457C04 |. 837D FC 00 cmp dword ptr [ebp-4], 0 ; 序列号是否为空?
00457C08 |. 75 18 jnz short 00457C22
00457C0A |. 6A 00 push 0
00457C0C |. B9 C87E4500 mov ecx, 00457EC8 ; ASCII "Enter a Serial !"
00457C11 |. BA DC7E4500 mov edx, 00457EDC ; ASCII "You must enter a Serial !"
00457C16 |. A1 98A54500 mov eax, dword ptr [45A598]
00457C1B |. 8B00 mov eax, dword ptr [eax]
00457C1D |. E8 0E85FEFF call 00440130
00457C22 |> 33C0 xor eax, eax
00457C24 |. A3 40B84500 mov dword ptr [45B840], eax
00457C29 |. 8D55 FC lea edx, dword ptr [ebp-4] ; 取序列号
00457C2C |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457C32 |. E8 A9C2FCFF call 00423EE0
00457C37 |. 8B45 FC mov eax, dword ptr [ebp-4] ; 取用户名
00457C3A |. E8 F9BFFAFF call 00403C38
00457C3F |. A3 44B84500 mov dword ptr [45B844], eax
00457C44 |. A1 44B84500 mov eax, dword ptr [45B844]
00457C49 |. E8 82FDFAFF call 004079D0
00457C4E |. 83F8 06 cmp eax, 6 ; 用户名大于等于6?
00457C51 |. 73 1D jnb short 00457C70
00457C53 |. 6A 00 push 0
00457C55 |. B9 F87E4500 mov ecx, 00457EF8 ; ASCII "Name too short !"
00457C5A |. BA 0C7F4500 mov edx, 00457F0C ; ASCII "Your Name must be at least 6 Chars long !"
00457C5F |. A1 98A54500 mov eax, dword ptr [45A598]
00457C64 |. 8B00 mov eax, dword ptr [eax]
00457C66 |. E8 C584FEFF call 00440130
00457C6B |. E9 59010000 jmp 00457DC9
00457C70 |> 8D55 FC lea edx, dword ptr [ebp-4] ; 取用户名
00457C73 |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457C79 |. E8 62C2FCFF call 00423EE0
00457C7E |. 8B45 FC mov eax, dword ptr [ebp-4] ; 取用户名
00457C81 |. BA 01000000 mov edx, 1
00457C86 |. 4A dec edx ; dex = 0
00457C87 |. 3B50 FC cmp edx, dword ptr [eax-4] ; 用户名长度大于0?
00457C8A |. 72 05 jb short 00457C91
00457C8C |. E8 F3AEFAFF call 00402B84
00457C91 |> 42 inc edx ; dex = 1
00457C92 |. 0FB64410 FF movzx eax, byte ptr [eax+edx-1] ; 取第一个字符
00457C97 |. 6BF0 02 imul esi, eax, 2 ; esi = eax * 2
00457C9A |. 71 05 jno short 00457CA1 ; 无溢出则跳转
00457C9C |. E8 EBAEFAFF call 00402B8C
00457CA1 |> 8D55 F8 lea edx, dword ptr [ebp-8] ; 取内存地址
00457CA4 |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457CAA |. E8 31C2FCFF call 00423EE0
00457CAF |. 8B45 F8 mov eax, dword ptr [ebp-8] ; 取用户名字串
00457CB2 |. BA 02000000 mov edx, 2
00457CB7 |. 4A dec edx ; edx = 1
00457CB8 |. 3B50 FC cmp edx, dword ptr [eax-4] ; 用户名长度是否大于1?
00457CBB |. 72 05 jb short 00457CC2
00457CBD |. E8 C2AEFAFF call 00402B84
00457CC2 |> 42 inc edx ; edx=2
00457CC3 |. 0FB64410 FF movzx eax, byte ptr [eax+edx-1] ; 取第二个字符
00457CC8 |. 6BC0 02 imul eax, eax, 2 ; eax = eax * 2
00457CCB |. 71 05 jno short 00457CD2 ; 无溢出则跳转
00457CCD |. E8 BAAEFAFF call 00402B8C
00457CD2 |> 03F0 add esi, eax ; 运算结果累加存入esi
00457CD4 |. 71 05 jno short 00457CDB ; 无溢出则跳转
00457CD6 |. E8 B1AEFAFF call 00402B8C
00457CDB |> 8D55 F4 lea edx, dword ptr [ebp-C] ; 取内存地址
00457CDE |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457CE4 |. E8 F7C1FCFF call 00423EE0
00457CE9 |. 8B45 F4 mov eax, dword ptr [ebp-C] ; 取用户名
00457CEC |. BA 03000000 mov edx, 3
00457CF1 |. 4A dec edx
00457CF2 |. 3B50 FC cmp edx, dword ptr [eax-4] ; 用户名长度是否大于2?
00457CF5 |. 72 05 jb short 00457CFC
00457CF7 |. E8 88AEFAFF call 00402B84
00457CFC |> 42 inc edx
00457CFD |. 0FB64410 FF movzx eax, byte ptr [eax+edx-1] ; 取第三个字符
00457D02 |. 6BC0 02 imul eax, eax, 2 ; eax = eax * 2
00457D05 |. 71 05 jno short 00457D0C ; 无溢出则跳转
00457D07 |. E8 80AEFAFF call 00402B8C
00457D0C |> 03F0 add esi, eax ; 运算结果累加存入esi
00457D0E |. 71 05 jno short 00457D15 ; 无溢出则跳转
00457D10 |. E8 77AEFAFF call 00402B8C
00457D15 |> 8D55 F0 lea edx, dword ptr [ebp-10] ; 取内存地址
00457D18 |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457D1E |. E8 BDC1FCFF call 00423EE0
00457D23 |. 8B45 F0 mov eax, dword ptr [ebp-10] ; 取用户名
00457D26 |. BA 04000000 mov edx, 4
00457D2B |. 4A dec edx
00457D2C |. 3B50 FC cmp edx, dword ptr [eax-4] ; 用户名长度是否大于3?
00457D2F |. 72 05 jb short 00457D36
00457D31 |. E8 4EAEFAFF call 00402B84
00457D36 |> 42 inc edx
00457D37 |. 0FB64410 FF movzx eax, byte ptr [eax+edx-1] ; 取第四个字符
00457D3C |. 6BC0 02 imul eax, eax, 2 ; eax = eax * 2
00457D3F |. 71 05 jno short 00457D46 ; 无溢出则跳转
00457D41 |. E8 46AEFAFF call 00402B8C
00457D46 |> 03F0 add esi, eax ; 运算结果累加存入esi
00457D48 |. 71 05 jno short 00457D4F ; 无溢出则跳转
00457D4A |. E8 3DAEFAFF call 00402B8C
00457D4F |> 8D55 EC lea edx, dword ptr [ebp-14] ; 取内存地址
00457D52 |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457D58 |. E8 83C1FCFF call 00423EE0
00457D5D |. 8B45 EC mov eax, dword ptr [ebp-14] ; 取用户名
00457D60 |. BA 05000000 mov edx, 5
00457D65 |. 4A dec edx
00457D66 |. 3B50 FC cmp edx, dword ptr [eax-4] ; 用户名长度是否大于4?
00457D69 |. 72 05 jb short 00457D70
00457D6B |. E8 14AEFAFF call 00402B84
00457D70 |> 42 inc edx
00457D71 |. 0FB64410 FF movzx eax, byte ptr [eax+edx-1] ; 取第五个字符
00457D76 |. 6BC0 02 imul eax, eax, 2 ; eax = eax * 2
00457D79 |. 71 05 jno short 00457D80 ; 无溢出则跳转
00457D7B |. E8 0CAEFAFF call 00402B8C
00457D80 |> 03F0 add esi, eax ; 运算结果累加存入esi
00457D82 |. 71 05 jno short 00457D89 ; 无溢出则跳转
00457D84 |. E8 03AEFAFF call 00402B8C
00457D89 |> 8D55 E8 lea edx, dword ptr [ebp-18] ; 取内存地址
00457D8C |. 8B83 D8020000 mov eax, dword ptr [ebx+2D8]
00457D92 |. E8 49C1FCFF call 00423EE0
00457D97 |. 8B45 E8 mov eax, dword ptr [ebp-18] ; 取用户名
00457D9A |. BA 06000000 mov edx, 6
00457D9F |. 4A dec edx
00457DA0 |. 3B50 FC cmp edx, dword ptr [eax-4] ; 用户名长度是否大于5?
00457DA3 |. 72 05 jb short 00457DAA
00457DA5 |. E8 DAADFAFF call 00402B84
00457DAA |> 42 inc edx
00457DAB |. 0FB64410 FF movzx eax, byte ptr [eax+edx-1] ; 取第六个字符
00457DB0 |. 6BC0 02 imul eax, eax, 2 ; eax = eax * 2
00457DB3 |. 71 05 jno short 00457DBA ; 无溢出则跳转
00457DB5 |. E8 D2ADFAFF call 00402B8C
00457DBA |> 03F0 add esi, eax ; 运算结果累加存入esi
00457DBC |. 71 05 jno short 00457DC3 ; 无溢出则跳转
00457DBE |. E8 C9ADFAFF call 00402B8C
00457DC3 |> 8935 40B84500 mov dword ptr [45B840], esi ; 将结果存入内存
00457DC9 |> A1 44B84500 mov eax, dword ptr [45B844]
00457DCE |. E8 FDFBFAFF call 004079D0
00457DD3 |. 6BC0 02 imul eax, eax, 2 ; eax = 用户名长度*2
00457DD6 |. 73 05 jnb short 00457DDD ; 若eax无进位,则跳转
00457DD8 |. E8 AFADFAFF call 00402B8C
00457DDD |> 33D2 xor edx, edx
00457DDF |. 52 push edx
00457DE0 |. 50 push eax
00457DE1 |. A1 40B84500 mov eax, dword ptr [45B840] ; 取结果
00457DE6 |. 99 cdq ; 把原来的 EAX 扩展成 EDX:EAX (带正负值)
00457DE7 |. 030424 add eax, dword ptr [esp] ; 结果加上用户名长度*2
00457DEA |. 135424 04 adc edx, dword ptr [esp+4] ; 带进位加法指令
00457DEE |. 71 05 jno short 00457DF5 ; 无溢出则跳转
00457DF0 |. E8 97ADFAFF call 00402B8C
00457DF5 |> 83C4 08 add esp, 8 ; 清除局部变量内存
00457DF8 |. 50 push eax ; 结果入栈
00457DF9 |. C1F8 1F sar eax, 1F ; 算术右移1F(最高位不变)
00457DFC |. 3BC2 cmp eax, edx
00457DFE |. 58 pop eax ; 还原eax
00457DFF |. 74 05 je short 00457E06
00457E01 |. E8 7EADFAFF call 00402B84
00457E06 |> A3 40B84500 mov dword ptr [45B840], eax ; 保存结果
00457E0B |. 8D55 E4 lea edx, dword ptr [ebp-1C] ; 取内存地址
00457E0E |. A1 40B84500 mov eax, dword ptr [45B840]
00457E13 |. E8 2CF9FAFF call 00407744 ; 根据用户名得出的结果算出一个字串
00457E18 |. 8B45 E4 mov eax, dword ptr [ebp-1C] ; 取计算结果
00457E1B |. 50 push eax
00457E1C |. 8D55 FC lea edx, dword ptr [ebp-4] ; 取用户名
00457E1F |. 8B83 DC020000 mov eax, dword ptr [ebx+2DC]
00457E25 |. E8 B6C0FCFF call 00423EE0
00457E2A |. 8B55 FC mov edx, dword ptr [ebp-4] ; 取序列号
00457E2D |. 58 pop eax ; 还原第一次的运算结果
00457E2E |. E8 51BDFAFF call 00403B84 ; 比较两次的运算结果,不相同则序列号无效
00457E33 |. 75 1A jnz short 00457E4F
00457E35 |. 6A 00 push 0
00457E37 |. B9 387F4500 mov ecx, 00457F38 ; ASCII "Congratz !"
00457E3C |. BA 447F4500 mov edx, 00457F44 ; ASCII "You cracked the CFF CrackMe #4 ! Please send your solution to acidbytes@gmx.net !"
00457E41 |. A1 98A54500 mov eax, dword ptr [45A598]
00457E46 |. 8B00 mov eax, dword ptr [eax]
00457E48 |. E8 E382FEFF call 00440130
00457E4D |. EB 18 jmp short 00457E67
00457E4F |> 6A 00 push 0
00457E51 |. B9 987F4500 mov ecx, 00457F98 ; ASCII "Serial not valid"
00457E56 |. BA AC7F4500 mov edx, 00457FAC ; ASCII "The Serial you entered is in any case not valid !"
00457E5B |. A1 98A54500 mov eax, dword ptr [45A598]
00457E60 |. 8B00 mov eax, dword ptr [eax]
00457E62 |. E8 C982FEFF call 00440130
在457E13中调用了子程序407744,在这个函数里对入栈的运算结果进行了操作,我们F7跟进:
00407744 /$ 83C4 F8 add esp, -8 ; 开辟8个字节的内存单元
00407747 |. 6A 00 push 0
00407749 |. 894424 04 mov dword ptr [esp+4], eax ; 存入运算结果
0040774D |. C64424 08 00 mov byte ptr [esp+8], 0
00407752 |. 8D4C24 04 lea ecx, dword ptr [esp+4]
00407756 |. 8BC2 mov eax, edx
00407758 |. BA 70774000 mov edx, 00407770 ; ASCII "%d"
0040775D |. E8 CA090000 call 0040812C ; 进入有关键call的子程序
00407762 |. 59 pop ecx
00407763 |. 5A pop edx
00407764 . C3 retn
继续跟进40812C:
0040812C /$ 55 push ebp
0040812D |. 8BEC mov ebp, esp
0040812F |. 81C4 04F0FFFF add esp, -0FFC ; 猜测是开辟1023个4个字节的内存
00408135 |. 50 push eax
00408136 |. 83C4 F4 add esp, -0C ; 三个局部变量
00408139 |. 53 push ebx
0040813A |. 56 push esi
0040813B |. 894D F8 mov dword ptr [ebp-8], ecx
0040813E |. 8955 FC mov dword ptr [ebp-4], edx
00408141 |. 8BF0 mov esi, eax
00408143 |. BB 02100000 mov ebx, 1002
00408148 |. 8B45 FC mov eax, dword ptr [ebp-4]
0040814B |. E8 24B9FFFF call 00403A74
00408150 |. 8BD3 mov edx, ebx
00408152 |. 85D2 test edx, edx
00408154 |. 79 03 jns short 00408159
00408156 |. 83C2 03 add edx, 3
00408159 |> C1FA 02 sar edx, 2
0040815C |. 8BCB mov ecx, ebx
0040815E |. 2BCA sub ecx, edx
00408160 |. 3BC1 cmp eax, ecx
00408162 |. 7D 24 jge short 00408188
00408164 |. 8B45 FC mov eax, dword ptr [ebp-4]
00408167 |. E8 08B9FFFF call 00403A74 ; 如果eax不为空则将他前一个变量的值赋给它
0040816C |. 50 push eax
0040816D |. 8B45 F8 mov eax, dword ptr [ebp-8]
00408170 |. 50 push eax
00408171 |. 8B45 08 mov eax, dword ptr [ebp+8]
00408174 |. 50 push eax
00408175 |. 8B4D FC mov ecx, dword ptr [ebp-4]
00408178 |. 8BD3 mov edx, ebx
0040817A |. 4A dec edx
0040817B |. 8D85 F6EFFFFF lea eax, dword ptr [ebp-100A]
00408181 |. E8 32FBFFFF call 00407CB8 ; 关键call
00408186 |. EB 0C jmp short 00408194
00408188 |> 8B45 FC mov eax, dword ptr [ebp-4]
0040818B |. E8 E4B8FFFF call 00403A74
00408190 |. 8BD8 mov ebx, eax
00408192 |. 8BC3 mov eax, ebx
00408194 |> 8BD3 mov edx, ebx
00408196 |. 4A dec edx
00408197 |. 3BC2 cmp eax, edx
00408199 |. 7C 43 jl short 004081DE
0040819B |. EB 30 jmp short 004081CD
0040819D |> 03DB /add ebx, ebx
0040819F |. 8BC6 |mov eax, esi
004081A1 |. E8 52B6FFFF |call 004037F8
004081A6 |. 8BC6 |mov eax, esi
004081A8 |. 8BD3 |mov edx, ebx
004081AA |. E8 99BBFFFF |call 00403D48
004081AF |. 8B45 FC |mov eax, dword ptr [ebp-4]
004081B2 |. E8 BDB8FFFF |call 00403A74
004081B7 |. 50 |push eax
004081B8 |. 8B45 F8 |mov eax, dword ptr [ebp-8]
004081BB |. 50 |push eax
004081BC |. 8B45 08 |mov eax, dword ptr [ebp+8]
004081BF |. 50 |push eax
004081C0 |. 8B4D FC |mov ecx, dword ptr [ebp-4]
004081C3 |. 8BD3 |mov edx, ebx
004081C5 |. 4A |dec edx
004081C6 |. 8B06 |mov eax, dword ptr [esi]
004081C8 |. E8 EBFAFFFF |call 00407CB8
004081CD |> 8BD3 mov edx, ebx
004081CF |. 4A |dec edx
004081D0 |. 3BC2 |cmp eax, edx
004081D2 |.^ 7D C9 jge short 0040819D
004081D4 |. 8BD6 mov edx, esi
004081D6 |. 92 xchg eax, edx
004081D7 |. E8 6CBBFFFF call 00403D48
004081DC |. EB 0E jmp short 004081EC
004081DE |> 8D95 F6EFFFFF lea edx, dword ptr [ebp-100A]
004081E4 |. 8BCE mov ecx, esi
004081E6 |. 91 xchg eax, ecx
004081E7 |. E8 F0B6FFFF call 004038DC
004081EC |> 5E pop esi
004081ED |. 5B pop ebx
004081EE |. 8BE5 mov esp, ebp
004081F0 |. 5D pop ebp
004081F1 . C2 0400 retn 4
跟进关键call:
00407CB8 $ 55 push ebp ; ↓关键算法
00407CB9 . 8BEC mov ebp, esp
00407CBB . 83C4 8C add esp, -74
00407CBE . 53 push ebx
00407CBF . 33DB xor ebx, ebx
00407CC1 . 895D F0 mov dword ptr [ebp-10], ebx
00407CC4 . 53 push ebx
00407CC5 . 56 push esi
00407CC6 . 57 push edi
00407CC7 . 89C7 mov edi, eax
00407CC9 . 89CE mov esi, ecx
00407CCB . 034D 10 add ecx, dword ptr [ebp+10]
00407CCE . 897D FC mov dword ptr [ebp-4], edi
00407CD1 . 31C0 xor eax, eax
00407CD3 . 8945 F8 mov dword ptr [ebp-8], eax
00407CD6 . 8945 F4 mov dword ptr [ebp-C], eax
00407CD9 . 8945 F0 mov dword ptr [ebp-10], eax
00407CDC > 09D2 or edx, edx
00407CDE . 74 0E je short 00407CEE
00407CE0 > 39CE cmp esi, ecx
00407CE2 . 74 0A je short 00407CEE
00407CE4 . AC lods byte ptr [esi]
00407CE5 . 80F8 25 cmp al, 25
00407CE8 . 74 0E je short 00407CF8
00407CEA > AA stos byte ptr es:[edi]
00407CEB . 4A dec edx
00407CEC .^ 75 F2 jnz short 00407CE0
00407CEE > 89F8 mov eax, edi
00407CF0 . 2B45 FC sub eax, dword ptr [ebp-4]
00407CF3 . E9 A8030000 jmp 004080A0
00407CF8 > 39CE cmp esi, ecx
00407CFA .^ 74 F2 je short 00407CEE
00407CFC . AC lods byte ptr [esi]
00407CFD . 80F8 25 cmp al, 25
00407D00 .^ 74 E8 je short 00407CEA
00407D02 . 8D5E FE lea ebx, dword ptr [esi-2]
00407D05 . 895D EC mov dword ptr [ebp-14], ebx
00407D08 > 8845 EB mov byte ptr [ebp-15], al
00407D0B . 80F8 2D cmp al, 2D
00407D0E . 75 05 jnz short 00407D15
00407D10 . 39CE cmp esi, ecx
00407D12 .^ 74 DA je short 00407CEE
00407D14 . AC lods byte ptr [esi]
00407D15 > E8 80000000 call 00407D9A
00407D1A . 80F8 3A cmp al, 3A
00407D1D . 75 0A jnz short 00407D29
00407D1F . 895D F8 mov dword ptr [ebp-8], ebx
00407D22 . 39CE cmp esi, ecx
00407D24 .^ 74 C8 je short 00407CEE
00407D26 . AC lods byte ptr [esi]
00407D27 .^ EB DF jmp short 00407D08
00407D29 > 895D E4 mov dword ptr [ebp-1C], ebx
00407D2C . BB FFFFFFFF mov ebx, -1
00407D31 . 80F8 2E cmp al, 2E
00407D34 . 75 0A jnz short 00407D40
00407D36 . 39CE cmp esi, ecx
00407D38 .^ 74 B4 je short 00407CEE
00407D3A . AC lods byte ptr [esi]
00407D3B . E8 5A000000 call 00407D9A
00407D40 > 895D E0 mov dword ptr [ebp-20], ebx
00407D43 . 8975 DC mov dword ptr [ebp-24], esi
00407D46 . 51 push ecx
00407D47 . 52 push edx
00407D48 . E8 96000000 call 00407DE3
00407D4D . 5A pop edx
00407D4E . 8B5D E4 mov ebx, dword ptr [ebp-1C]
00407D51 . 29CB sub ebx, ecx
00407D53 . 73 02 jnb short 00407D57
00407D55 . 31DB xor ebx, ebx
00407D57 > 807D EB 2D cmp byte ptr [ebp-15], 2D
00407D5B . 75 0A jnz short 00407D67
00407D5D . 29CA sub edx, ecx
00407D5F . 73 04 jnb short 00407D65
00407D61 . 01D1 add ecx, edx
00407D63 . 31D2 xor edx, edx
00407D65 > F3:A4 rep movs byte ptr es:[edi], byte ptr [esi]
00407D67 > 87CB xchg ebx, ecx
00407D69 . 29CA sub edx, ecx
00407D6B . 73 04 jnb short 00407D71
00407D6D . 01D1 add ecx, edx
00407D6F . 31D2 xor edx, edx
00407D71 > B0 20 mov al, 20
00407D73 . F3:AA rep stos byte ptr es:[edi]
00407D75 . 87CB xchg ebx, ecx
00407D77 . 29CA sub edx, ecx
00407D79 . 73 04 jnb short 00407D7F
00407D7B . 01D1 add ecx, edx
00407D7D . 31D2 xor edx, edx
00407D7F > F3:A4 rep movs byte ptr es:[edi], byte ptr [esi]
00407D81 . 837D F4 00 cmp dword ptr [ebp-C], 0
00407D85 . 74 0A je short 00407D91
00407D87 . 52 push edx
00407D88 . 8D45 F4 lea eax, dword ptr [ebp-C]
00407D8B . E8 1CFFFFFF call 00407CAC
00407D90 . 5A pop edx
00407D91 > 59 pop ecx
00407D92 . 8B75 DC mov esi, dword ptr [ebp-24]
00407D95 .^ E9 42FFFFFF jmp 00407CDC
00407D9A $ 31DB xor ebx, ebx
00407D9C . 80F8 2A cmp al, 2A
00407D9F . 74 22 je short 00407DC3
00407DA1 > 80F8 30 cmp al, 30
00407DA4 . 72 3C jb short 00407DE2
00407DA6 . 80F8 39 cmp al, 39
00407DA9 . 77 37 ja short 00407DE2
00407DAB . 6BDB 0A imul ebx, ebx, 0A
00407DAE . 80E8 30 sub al, 30
00407DB1 . 0FB6C0 movzx eax, al
00407DB4 . 01C3 add ebx, eax
00407DB6 . 39CE cmp esi, ecx
00407DB8 . 74 03 je short 00407DBD
00407DBA . AC lods byte ptr [esi]
00407DBB .^ EB E4 jmp short 00407DA1
00407DBD > 58 pop eax
00407DBE .^ E9 2BFFFFFF jmp 00407CEE
00407DC3 > 8B45 F8 mov eax, dword ptr [ebp-8]
00407DC6 . 3B45 08 cmp eax, dword ptr [ebp+8]
00407DC9 . 77 12 ja short 00407DDD
00407DCB . FF45 F8 inc dword ptr [ebp-8]
00407DCE . 8B5D 0C mov ebx, dword ptr [ebp+C]
00407DD1 . 807CC3 04 00 cmp byte ptr [ebx+eax*8+4], 0
00407DD6 . 8B1CC3 mov ebx, dword ptr [ebx+eax*8]
00407DD9 . 74 02 je short 00407DDD
00407DDB . 31DB xor ebx, ebx
00407DDD > 39CE cmp esi, ecx
00407DDF .^ 74 DC je short 00407DBD
00407DE1 . AC lods byte ptr [esi]
00407DE2 > C3 retn
00407DE3 /$ 24 DF and al, 0DF
00407DE5 |. 88C1 mov cl, al
00407DE7 |. B8 01000000 mov eax, 1
00407DEC |. 8B5D F8 mov ebx, dword ptr [ebp-8]
00407DEF |. 3B5D 08 cmp ebx, dword ptr [ebp+8]
00407DF2 |. 77 5C ja short 00407E50
00407DF4 |. FF45 F8 inc dword ptr [ebp-8]
00407DF7 |. 8B75 0C mov esi, dword ptr [ebp+C]
00407DFA |. 8D34DE lea esi, dword ptr [esi+ebx*8]
00407DFD |. 8B06 mov eax, dword ptr [esi]
00407DFF |. 0FB65E 04 movzx ebx, byte ptr [esi+4]
00407E03 |. FF249D 0A7E40>jmp dword ptr [ebx*4+407E0A]
00407E0A |. FE7E4000 dd CrackMe#.00407EFE ; Switch table used at 00407E03
00407E0E |. 4E7E4000 dd CrackMe#.00407E4E
00407E12 |. 657F4000 dd CrackMe#.00407F65
00407E16 |. 23804000 dd CrackMe#.00408023
00407E1A |. 957F4000 dd CrackMe#.00407F95
00407E1E |. 05804000 dd CrackMe#.00408005
00407E22 |. E57F4000 dd CrackMe#.00407FE5
00407E26 |. 4E7E4000 dd CrackMe#.00407E4E
00407E2A |. 4E7E4000 dd CrackMe#.00407E4E
00407E2E |. 4E7E4000 dd CrackMe#.00407E4E
00407E32 |. A67F4000 dd CrackMe#.00407FA6
00407E36 |. C97F4000 dd CrackMe#.00407FC9
00407E3A |. 1F804000 dd CrackMe#.0040801F
00407E3E |. 747F4000 dd CrackMe#.00407F74
00407E42 |. 4E7E4000 dd CrackMe#.00407E4E
00407E46 |. AD7F4000 dd CrackMe#.00407FAD
00407E4A |. 627E4000 dd CrackMe#.00407E62
00407E4E |> 31C0 xor eax, eax ; Default case of switch 00408029
00407E50 |> E8 40020000 call 00408095
00407E55 |. 8B55 EC mov edx, dword ptr [ebp-14]
00407E58 |. 8B4D DC mov ecx, dword ptr [ebp-24]
00407E5B |. 29D1 sub ecx, edx
00407E5D |. E8 DEFDFFFF call 00407C40
00407E62 |> 8D5D D0 lea ebx, dword ptr [ebp-30]
00407E65 |. 8B10 mov edx, dword ptr [eax]
00407E67 |. 8913 mov dword ptr [ebx], edx
00407E69 |. 8B50 04 mov edx, dword ptr [eax+4]
00407E6C |. 8953 04 mov dword ptr [ebx+4], edx
00407E6F |. 80F9 44 cmp cl, 44 ; Switch (cases 44..58)
00407E72 |. 74 11 je short 00407E85
00407E74 |. 80F9 55 cmp cl, 55
00407E77 |. 74 2A je short 00407EA3
00407E79 |. 80F9 58 cmp cl, 58
00407E7C |.^ 75 D0 jnz short 00407E4E
00407E7E |. B9 10000000 mov ecx, 10 ; Case 58 ('X') of switch 00407E6F
00407E83 |. EB 23 jmp short 00407EA8
00407E85 |> F743 04 00000>test dword ptr [ebx+4], 80000000 ; Case 44 ('D') of switch 00407E6F
00407E8C |. 74 15 je short 00407EA3
00407E8E |. F71B neg dword ptr [ebx]
00407E90 |. 8353 04 00 adc dword ptr [ebx+4], 0
00407E94 |. F75B 04 neg dword ptr [ebx+4]
00407E97 |. E8 07000000 call 00407EA3
00407E9C |. B0 2D mov al, 2D
00407E9E |. 41 inc ecx
00407E9F |. 4E dec esi
00407EA0 |. 8806 mov byte ptr [esi], al
00407EA2 |. C3 retn
00407EA3 |$ B9 0A000000 mov ecx, 0A ; Case 55 ('U') of switch 00407E6F
00407EA8 |> 8D75 AF lea esi, dword ptr [ebp-51]
00407EAB |> 51 /push ecx
00407EAC |. 6A 00 |push 0
00407EAE |. 51 |push ecx
00407EAF |. 8B03 |mov eax, dword ptr [ebx]
00407EB1 |. 8B53 04 |mov edx, dword ptr [ebx+4]
00407EB4 |. E8 20DAFFFF |call 004058D9
00407EB9 |. 59 |pop ecx
00407EBA |. 92 |xchg eax, edx
00407EBB |. 80C2 30 |add dl, 30
00407EBE |. 80FA 3A |cmp dl, 3A
00407EC1 |. 72 03 |jb short 00407EC6
00407EC3 |. 80C2 07 |add dl, 7
00407EC6 |> 4E |dec esi
00407EC7 |. 8816 |mov byte ptr [esi], dl
00407EC9 |. 51 |push ecx
00407ECA |. 6A 00 |push 0
00407ECC |. 51 |push ecx
00407ECD |. 8B03 |mov eax, dword ptr [ebx]
00407ECF |. 8B53 04 |mov edx, dword ptr [ebx+4]
00407ED2 |. E8 0DD9FFFF |call 004057E4
00407ED7 |. 59 |pop ecx
00407ED8 |. 8903 |mov dword ptr [ebx], eax
00407EDA |. 8953 04 |mov dword ptr [ebx+4], edx
00407EDD |. 09D0 |or eax, edx
00407EDF |.^ 75 CA jnz short 00407EAB
00407EE1 |. 8D4D AF lea ecx, dword ptr [ebp-51]
00407EE4 |. 29F1 sub ecx, esi
00407EE6 |. 8B55 E0 mov edx, dword ptr [ebp-20]
00407EE9 |. 83FA 10 cmp edx, 10
00407EEC |. 72 01 jb short 00407EEF
00407EEE |. C3 retn
00407EEF |> 29CA sub edx, ecx
00407EF1 |. 76 0A jbe short 00407EFD
00407EF3 |. 01D1 add ecx, edx
00407EF5 |. B0 30 mov al, 30
00407EF7 |> 4E /dec esi
00407EF8 |. 8806 |mov byte ptr [esi], al
00407EFA |. 4A |dec edx
00407EFB |.^ 75 FA jnz short 00407EF7
00407EFD |> C3 retn
00407EFE |> 80F9 44 cmp cl, 44 ; Switch (cases 44..58)
00407F01 |. 74 15 je short 00407F18
00407F03 |. 80F9 55 cmp cl, 55
00407F06 |. 74 22 je short 00407F2A
00407F08 |. 80F9 58 cmp cl, 58
00407F0B |.^ 0F85 3DFFFFFF jnz 00407E4E
00407F11 |. B9 10000000 mov ecx, 10 ; Case 58 ('X') of switch 00407EFE
00407F16 |. EB 17 jmp short 00407F2F
00407F18 |> 09C0 or eax, eax ; Case 44 ('D') of switch 00407EFE
00407F1A |. 79 0E jns short 00407F2A
00407F1C |. F7D8 neg eax
00407F1E |. E8 07000000 call 00407F2A
00407F23 |. B0 2D mov al, 2D
00407F25 |. 41 inc ecx
00407F26 |. 4E dec esi
00407F27 |. 8806 mov byte ptr [esi], al
00407F29 |. C3 retn
00407F2A |$ B9 0A000000 mov ecx, 0A ; Case 55 ('U') of switch 00407EFE
00407F2F |> 8D75 9F lea esi, dword ptr [ebp-61] ; 此时,eax存放着之前的运算结果
00407F32 |> 31D2 /xor edx, edx ; 这个循环把十六进制数转化成对应的十进制字串
00407F34 |. F7F1 |div ecx ; 除以10
00407F36 |. 80C2 30 |add dl, 30
00407F39 |. 80FA 3A |cmp dl, 3A
00407F3C |. 72 03 |jb short 00407F41
00407F3E |. 80C2 07 |add dl, 7
00407F41 |> 4E |dec esi
00407F42 |. 8816 |mov byte ptr [esi], dl
00407F44 |. 09C0 |or eax, eax
00407F46 |.^ 75 EA jnz short 00407F32
00407F48 |. 8D4D 9F lea ecx, dword ptr [ebp-61]
00407F4B |. 29F1 sub ecx, esi
00407F4D |. 8B55 E0 mov edx, dword ptr [ebp-20]
00407F50 |. 83FA 10 cmp edx, 10
00407F53 |. 72 01 jb short 00407F56
00407F55 |. C3 retn
00407F56 |> 29CA sub edx, ecx
00407F58 |. 76 0A jbe short 00407F64
00407F5A |. 01D1 add ecx, edx
00407F5C |. B0 30 mov al, 30
00407F5E |> 4E /dec esi
00407F5F |. 8806 |mov byte ptr [esi], al
00407F61 |. 4A |dec edx
00407F62 |.^ 75 FA jnz short 00407F5E
00407F64 |> C3 retn
00407F65 |> 80F9 53 cmp cl, 53
00407F68 |.^ 0F85 E0FEFFFF jnz 00407E4E
00407F6E |. B9 01000000 mov ecx, 1
00407F73 |. C3 retn
00407F74 |> 80F9 53 cmp cl, 53
00407F77 |.^ 0F85 D1FEFFFF jnz 00407E4E
00407F7D |. 66:8338 01 cmp word ptr [eax], 1
00407F81 |. 76 0F jbe short 00407F92
00407F83 |. 89C2 mov edx, eax
00407F85 |. 8D45 F4 lea eax, dword ptr [ebp-C]
00407F88 |. E8 0BFDFFFF call 00407C98
00407F8D |. 8B75 F4 mov esi, dword ptr [ebp-C]
00407F90 |. EB 42 jmp short 00407FD4
00407F92 |> 31C9 xor ecx, ecx
00407F94 |. C3 retn
00407F95 |> 80F9 53 cmp cl, 53
00407F98 |.^ 0F85 B0FEFFFF jnz 00407E4E
00407F9E |. 89C6 mov esi, eax
00407FA0 |. AC lods byte ptr [esi]
00407FA1 |. 0FB6C8 movzx ecx, al
00407FA4 |. EB 35 jmp short 00407FDB
00407FA6 |> BE DC394000 mov esi, 004039DC
00407FAB |. EB 05 jmp short 00407FB2
00407FAD |> BE 3C3A4000 mov esi, 00403A3C
00407FB2 |> 80F9 53 cmp cl, 53
00407FB5 |.^ 0F85 93FEFFFF jnz 00407E4E
00407FBB |. 89C2 mov edx, eax
00407FBD |. 8D45 F0 lea eax, dword ptr [ebp-10]
00407FC0 |. FFD6 call esi
00407FC2 |. 8B75 F0 mov esi, dword ptr [ebp-10]
00407FC5 |. 89F0 mov eax, esi
00407FC7 |. EB 0B jmp short 00407FD4
00407FC9 |> 80F9 53 cmp cl, 53
00407FCC |.^ 0F85 7CFEFFFF jnz 00407E4E
00407FD2 |. 89C6 mov esi, eax
00407FD4 |> 09F6 or esi, esi
00407FD6 |.^ 74 BA je short 00407F92
00407FD8 |. 8B4E FC mov ecx, dword ptr [esi-4]
00407FDB |> 3B4D E0 cmp ecx, dword ptr [ebp-20]
00407FDE |. 77 01 ja short 00407FE1
00407FE0 |. C3 retn
00407FE1 |> 8B4D E0 mov ecx, dword ptr [ebp-20]
00407FE4 |. C3 retn
00407FE5 |> 80F9 53 cmp cl, 53
00407FE8 |.^ 0F85 60FEFFFF jnz 00407E4E
00407FEE |. 89C6 mov esi, eax
00407FF0 |. 57 push edi
00407FF1 |. 89C7 mov edi, eax
00407FF3 |. 30C0 xor al, al
00407FF5 |. 8B4D E0 mov ecx, dword ptr [ebp-20]
00407FF8 |. E3 05 jecxz short 00407FFF
00407FFA |. F2:AE repne scas byte ptr es:[edi]
00407FFC |. 75 01 jnz short 00407FFF
00407FFE |. 4F dec edi
00407FFF |> 89F9 mov ecx, edi
00408001 |. 29F1 sub ecx, esi
00408003 |. 5F pop edi
00408004 |. C3 retn
00408005 |> 80F9 50 cmp cl, 50
00408008 |.^ 0F85 40FEFFFF jnz 00407E4E
0040800E |. C745 E0 08000>mov dword ptr [ebp-20], 8
00408015 |. B9 10000000 mov ecx, 10
0040801A |.^ E9 10FFFFFF jmp 00407F2F
0040801F |> B7 01 mov bh, 1
00408021 |. EB 02 jmp short 00408025
00408023 |> B7 00 mov bh, 0
00408025 |> 89C6 mov esi, eax
00408027 |. B3 00 mov bl, 0
00408029 |. 80F9 47 cmp cl, 47 ; Switch (cases 45..4E)
0040802C |. 74 3F je short 0040806D
0040802E |. B3 01 mov bl, 1
00408030 |. 80F9 45 cmp cl, 45
00408033 |. 74 38 je short 0040806D
00408035 |. B3 02 mov bl, 2
00408037 |. 80F9 46 cmp cl, 46
0040803A |. 74 12 je short 0040804E
0040803C |. B3 03 mov bl, 3
0040803E |. 80F9 4E cmp cl, 4E
00408041 |. 74 0B je short 0040804E
00408043 |. 80F9 4D cmp cl, 4D
00408046 |.^ 0F85 02FEFFFF jnz 00407E4E
0040804C |. B3 04 mov bl, 4 ; Case 4D ('M') of switch 00408029
0040804E |> B8 12000000 mov eax, 12 ; Cases 46 ('F'),4E ('N') of switch 00408029
00408053 |. 8B55 E0 mov edx, dword ptr [ebp-20]
00408056 |. 39C2 cmp edx, eax
00408058 |. 76 25 jbe short 0040807F
0040805A |. BA 02000000 mov edx, 2
0040805F |. 80F9 4D cmp cl, 4D
00408062 |. 75 1B jnz short 0040807F
00408064 |. 0FB615 F8B445>movzx edx, byte ptr [45B4F8]
0040806B |. EB 12 jmp short 0040807F
0040806D |> 8B45 E0 mov eax, dword ptr [ebp-20] ; Cases 45 ('E'),47 ('G') of switch 00408029
00408070 |. BA 03000000 mov edx, 3
00408075 |. 83F8 12 cmp eax, 12
00408078 |. 76 05 jbe short 0040807F
0040807A |. B8 0F000000 mov eax, 0F
0040807F |> 53 push ebx
00408080 |. 50 push eax
00408081 |. 52 push edx
00408082 |. 8D45 8F lea eax, dword ptr [ebp-71]
00408085 |. 89F2 mov edx, esi
00408087 |. 0FB6CF movzx ecx, bh
0040808A |. E8 EB1C0000 call 00409D7A
0040808F |. 89C1 mov ecx, eax
00408091 |. 8D75 8F lea esi, dword ptr [ebp-71]
00408094 . C3 retn
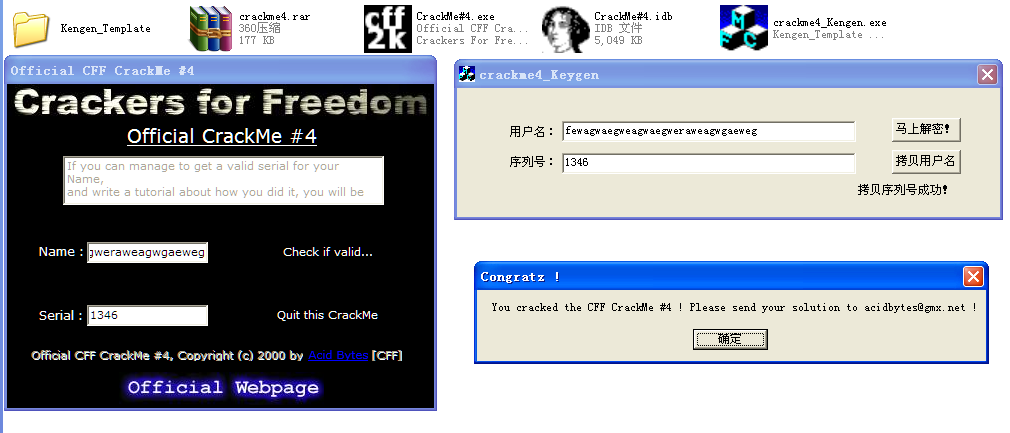
至此,我们找出了关键算法所在的位置。在无数的汇编指令中翻找出关键算法的秘诀在于,你要定位存放算出序列号的内存地址,并一步一步跟踪,发现该内存地址写入了数据。那么这时所处的汇编指令之前肯定就是对于序列号的处理算法。好了,这个crackme很简单,直接打开http://www.cnblogs.com/ZRBYYXDM/p/5115596.html中搭建的框架,并修改OnBtnDecrypt函数如下:
void CKengen_TemplateDlg::OnBtnDecrypt()
{
// TODO: Add your control notification handler code here
CString str;
GetDlgItemText( IDC_EDIT_NAME,str ); //获取用户名字串基本信息。
int len = str.GetLength();
if ( len >= 6 ){ //格式控制。
unsigned int sum = 0;
for ( int i = 0 ; i != 6 ; i++ )
sum += ( str[i] * 2 );
CString PassWord;
PassWord.Format( "%d",sum + len * 2 );
SetDlgItemText( IDC_EDIT_PASSWORD,PassWord );
}
else
MessageBox( "用户名格式错误!" );
}
再在OnInitDialog中添加此代码修改标题:SetWindowText(_T("crackme4_Keygen"));
运行效果: