Could not transfer artifact org.springframework.boot:spring-boot-s
tarter-parent:pom:2.2.5.RELEASE from/to nexus-aliyun (http://maven
.aliyun.com/nexus/content/groups/public): sun.security.validator.V
alidatorException: PKIX path building failed: sun.security.provider
.certpath.SunCertPathBuilderException: unable to find valid certifi
cation path to requested target.
1. 项目下新建java类
1 package org.yang.test;/* 2 * Copyright 2006 Sun Microsystems, Inc. All Rights Reserved. 3 * 4 * Redistribution and use in source and binary forms, with or without 5 * modification, are permitted provided that the following conditions 6 * are met: 7 * 8 * - Redistributions of source code must retain the above copyright 9 * notice, this list of conditions and the following disclaimer. 10 * 11 * - Redistributions in binary form must reproduce the above copyright 12 * notice, this list of conditions and the following disclaimer in the 13 * documentation and/or other materials provided with the distribution. 14 * 15 * - Neither the name of Sun Microsystems nor the names of its 16 * contributors may be used to endorse or promote products derived 17 * from this software without specific prior written permission. 18 * 19 * THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS 20 * IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, 21 * THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR 22 * PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR 23 * CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, 24 * EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, 25 * PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR 26 * PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF 27 * LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING 28 * NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS 29 * SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. 30 */ 31 32 import java.io.*; 33 34 import java.security.*; 35 import java.security.cert.*; 36 37 import javax.net.ssl.*; 38 39 public class InstallCert { 40 41 public static void main(String[] args) throws Exception { 42 String host; 43 int port; 44 char[] passphrase; 45 String[] h={"maven.aliyun.com"}; 46 if ((h.length == 1) || (h.length == 2)) { 47 String[] c = h[0].split(":"); 48 host = c[0]; 49 port = (c.length == 1) ? 443 : Integer.parseInt(c[1]); 50 String p = (h.length == 1) ? "changeit" : h[1]; 51 passphrase = p.toCharArray(); 52 } else { 53 System.out.println("Usage: java InstallCert <host>[:port] [passphrase]"); 54 return; 55 } 56 57 File file = new File("jssecacerts"); 58 if (file.isFile() == false) { 59 char SEP = File.separatorChar; 60 File dir = new File(System.getProperty("java.home") + SEP 61 + "lib" + SEP + "security"); 62 file = new File(dir, "jssecacerts"); 63 if (file.isFile() == false) { 64 file = new File(dir, "cacerts"); 65 } 66 } 67 System.out.println("Loading KeyStore " + file + "..."); 68 InputStream in = new FileInputStream(file); 69 KeyStore ks = KeyStore.getInstance(KeyStore.getDefaultType()); 70 ks.load(in, passphrase); 71 in.close(); 72 73 SSLContext context = SSLContext.getInstance("TLS"); 74 TrustManagerFactory tmf = 75 TrustManagerFactory.getInstance(TrustManagerFactory.getDefaultAlgorithm()); 76 tmf.init(ks); 77 X509TrustManager defaultTrustManager = (X509TrustManager)tmf.getTrustManagers()[0]; 78 SavingTrustManager tm = new SavingTrustManager(defaultTrustManager); 79 context.init(null, new TrustManager[] {tm}, null); 80 SSLSocketFactory factory = context.getSocketFactory(); 81 82 System.out.println("Opening connection to " + host + ":" + port + "..."); 83 SSLSocket socket = (SSLSocket)factory.createSocket(host, port); 84 socket.setSoTimeout(10000); 85 try { 86 System.out.println("Starting SSL handshake..."); 87 socket.startHandshake(); 88 socket.close(); 89 System.out.println(); 90 System.out.println("No errors, certificate is already trusted"); 91 } catch (SSLException e) { 92 System.out.println(); 93 e.printStackTrace(System.out); 94 } 95 96 X509Certificate[] chain = tm.chain; 97 if (chain == null) { 98 System.out.println("Could not obtain server certificate chain"); 99 return; 100 } 101 102 BufferedReader reader = 103 new BufferedReader(new InputStreamReader(System.in)); 104 105 System.out.println(); 106 System.out.println("Server sent " + chain.length + " certificate(s):"); 107 System.out.println(); 108 MessageDigest sha1 = MessageDigest.getInstance("SHA1"); 109 MessageDigest md5 = MessageDigest.getInstance("MD5"); 110 for (int i = 0; i < chain.length; i++) { 111 X509Certificate cert = chain[i]; 112 System.out.println 113 (" " + (i + 1) + " Subject " + cert.getSubjectDN()); 114 System.out.println(" Issuer " + cert.getIssuerDN()); 115 sha1.update(cert.getEncoded()); 116 System.out.println(" sha1 " + toHexString(sha1.digest())); 117 md5.update(cert.getEncoded()); 118 System.out.println(" md5 " + toHexString(md5.digest())); 119 System.out.println(); 120 } 121 122 System.out.println("Enter certificate to add to trusted keystore or 'q' to quit: [1]"); 123 String line = reader.readLine().trim(); 124 int k; 125 try { 126 k = (line.length() == 0) ? 0 : Integer.parseInt(line) - 1; 127 } catch (NumberFormatException e) { 128 System.out.println("KeyStore not changed"); 129 return; 130 } 131 132 X509Certificate cert = chain[k]; 133 String alias = host + "-" + (k + 1); 134 ks.setCertificateEntry(alias, cert); 135 136 OutputStream out = new FileOutputStream("jssecacerts"); 137 ks.store(out, passphrase); 138 out.close(); 139 140 System.out.println(); 141 System.out.println(cert); 142 System.out.println(); 143 System.out.println 144 ("Added certificate to keystore 'jssecacerts' using alias '" 145 + alias + "'"); 146 } 147 148 private static final char[] HEXDIGITS = "0123456789abcdef".toCharArray(); 149 150 private static String toHexString(byte[] bytes) { 151 StringBuilder sb = new StringBuilder(bytes.length * 3); 152 for (int b : bytes) { 153 b &= 0xff; 154 sb.append(HEXDIGITS[b >> 4]); 155 sb.append(HEXDIGITS[b & 15]); 156 sb.append(' '); 157 } 158 return sb.toString(); 159 } 160 161 private static class SavingTrustManager implements X509TrustManager { 162 163 private final X509TrustManager tm; 164 private X509Certificate[] chain; 165 166 SavingTrustManager(X509TrustManager tm) { 167 this.tm = tm; 168 } 169 170 public X509Certificate[] getAcceptedIssuers() { 171 throw new UnsupportedOperationException(); 172 } 173 174 public void checkClientTrusted(X509Certificate[] chain, String authType) 175 throws CertificateException { 176 throw new UnsupportedOperationException(); 177 } 178 179 public void checkServerTrusted(X509Certificate[] chain, String authType) 180 throws CertificateException { 181 this.chain = chain; 182 tm.checkServerTrusted(chain, authType); 183 } 184 } 185 186 }
2. 编译
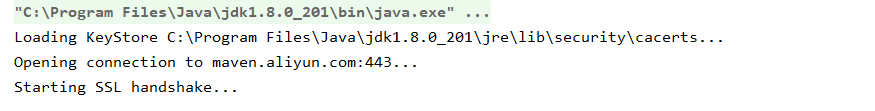
3. 运行
4. 输入1

5.生成需要的文件
6. 将此文件放入
C:Program FilesJavajre1.8.0_221libsecurity
Done