| 段名称 | 文件内偏移 | 段大小 |
| ELF头部 | 0x00000000 | 0x00001000 |
| oatdata | 0x00001000 | 0x027b8000 |
| oatexec | 0x027b9000 | 0x01ed69ec |
| ELF尾部 | 0x04690000 | 0x00001000 |
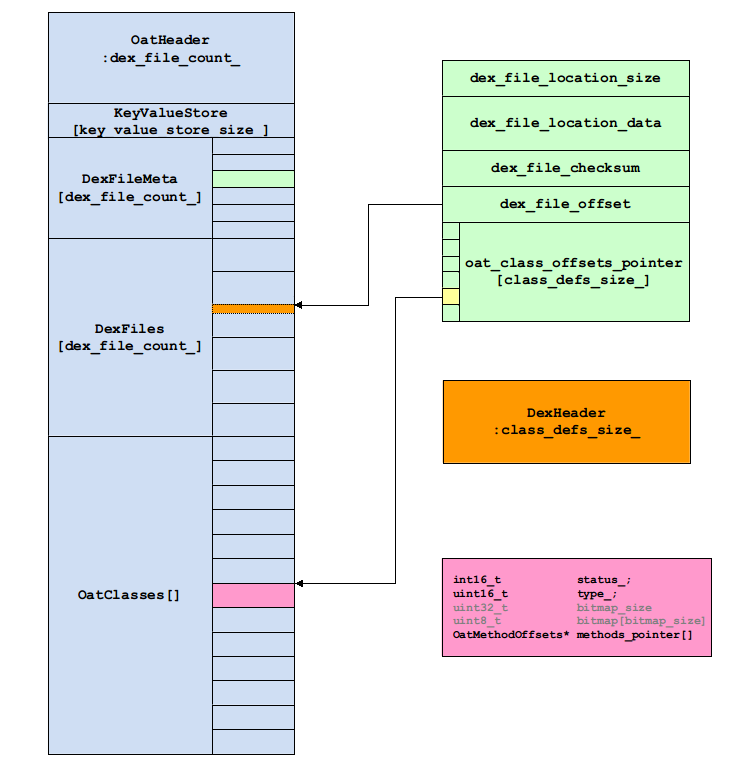
OatHeader:
0x00001000 | 6F 61 74 0A 30 33 39 00 77 40 00 B1 03 00 00 00 | 0x00001010 | 01 00 00 00 19 00 00 00 00 80 7B 02 01 80 7B 02 | 0x00001020 | 09 80 7B 02 11 80 7B 02 21 80 7B 02 29 80 7B 02 | 0x00001030 | 31 80 7B 02 39 80 7B 02 41 80 7B 02 49 80 7B 02 | 0x00001040 | 51 80 7B 02 00 00 00 00 00 00 00 00 00 00 00 00 | 0x00001050 | 93 05 00 00 |
| type | name | vallue |
|---|---|---|
uint8_t[4] |
magic_ |
'o', 'a', 't', ' ' |
uint8_t[4] |
version_ |
'0', '3', '9', '�' |
uint32_t |
adler32_checksum_ |
0xb1004077 |
InstructionSet |
instruction_set_ |
0x00000003 |
InstructionSetFeatures |
instruction_set_features_ |
0x00000001 |
uint32_t |
dex_file_count_ |
0x00000019 |
uint32_t |
executable_offset_ |
0x027b8000 |
uint32_t |
interpreter_to_interpreter_bridge_offset_ |
0x027b8001 |
uint32_t |
interpreter_to_compiled_code_bridge_offset_ |
0x027b8009 |
uint32_t |
jni_dlsym_lookup_offset_ |
0x027b8011 |
uint32_t |
portable_imt_conflict_trampoline_offset_ |
0x027b8021 |
uint32_t |
portable_resolution_trampoline_offset_ |
0x027b8029 |
uint32_t |
portable_to_interpreter_bridge_offset_ |
0x027b8031 |
uint32_t |
quick_generic_jni_trampoline_offset_ |
0x027b8039 |
uint32_t |
quick_imt_conflict_trampoline_offset_ |
0x027b8041 |
uint32_t |
quick_resolution_trampoline_offset_ |
0x027b8049 |
uint32_t |
quick_to_interpreter_bridge_offset_ |
0x027b8051 |
int32_t |
image_patch_delta_ |
0x00000000 |
| uint32_t |
image_file_location_oat_checksum_ |
0x00000000 |
| uint32_t | image_file_location_oat_data_begin_ | 0x00000000 |
| uint32_t | key_value_store_size_ | 0x00000593 |
| uint8_t[0] | key_value_store_ |
key_value_store:
0x00001050 | 64 65 78 32 6F 61 74 2D 63 6D 64 6C | dex2oat-cmdl 0x00001060 | 69 6E 65 00 2D 2D 69 6D 61 67 65 3D 2F 64 61 74 | ine.--image=/dat 0x00001070 | 61 2F 64 61 6C 76 69 6B 2D 63 61 63 68 65 2F 61 | a/dalvik-cache/a 0x00001080 | 72 6D 2F 73 79 73 74 65 6D 40 66 72 61 6D 65 77 | rm/system@framew 0x00001090 | 6F 72 6B 40 62 6F 6F 74 2E 61 72 74 20 2D 2D 64 | ork@boot.art --d 0x000010a0 | 65 78 2D 66 69 6C 65 3D 2F 73 79 73 74 65 6D 2F | ex-file=/system/ 0x000010b0 | 66 72 61 6D 65 77 6F 72 6B 2F 63 6F 72 65 2D 6C | framework/core-l ... 0x00001580 | 2D 2D 69 6D 61 67 65 2D 63 6C 61 73 73 65 73 2D | --image-classes- 0x00001590 | 7A 69 70 3D 2F 73 79 73 74 65 6D 2F 66 72 61 6D | zip=/system/fram 0x000015a0 | 65 77 6F 72 6B 2F 66 72 61 6D 65 77 6F 72 6B 2E | ework/framework. 0x000015b0 | 6A 61 72 20 2D 2D 69 6D 61 67 65 2D 63 6C 61 73 | jar --image-clas 0x000015c0 | 73 65 73 3D 70 72 65 6C 6F 61 64 65 64 2D 63 6C | ses=preloaded-cl 0x000015d0 | 61 73 73 65 73 00 64 65 78 32 6F 61 74 2D 68 6F | asses.dex2oat-ho 0x000015e0 | 73 74 00 41 72 6D 00 | st.Arm.
DexFileMetas:
0x000015e0 | 21 00 00 00 2F 73 79 73 74 <-------- 0x000015f0 | 65 6D 2F 66 72 61 6D 65 77 6F 72 6B 2F 63 6F 72 0x00001600 | 65 2D 6C 69 62 61 72 74 2E 6A 61 72 FC 04 E8 B5 0x00001610 | 8C 2F 01 00 78 2C F1 01 E4 2C F1 01 E8 2C F1 01 0x00001620 | B4 2D F1 01 D8 2D F1 01 04 2E F1 01 28 2E F1 01 0x00001630 | 54 2E F1 01 F0 31 F1 01 94 32 F1 01 A8 32 F1 01 0x00001640 | BC 32 F1 01 D0 32 F1 01 E4 32 F1 01 00 33 F1 01 DexFileMeta_0 ... 0x00003740 | B8 7C F3 01 2C 7D F3 01 28 7E F3 01 44 7E F3 01 0x00003750 | 68 7F F3 01 AC 7F F3 01 60 80 F3 01 84 80 F3 01 0x00003760 | B8 80 F3 01 2C 81 F3 01 40 82 F3 01 1F 00 00 00 -----------><--- 0x00003770 | 2F 73 79 73 74 65 6D 2F 66 72 61 6D 65 77 6F 72 0x00003780 | 6B 2F 63 6F 6E 73 63 72 79 70 74 2E 6A 61 72 76 DexFileMeta_1 0x00003790 | 62 33 B4 64 5C 2D 00 2C 83 F3 01 40 83 F3 01 64 0x000037a0 | 83 F3 01 E0 83 F3 01 FC 83 F3 01 58 84 F3 01 8C ... ... 0x00013430 | B1 04 02 84 B1 04 02 B0 B1 04 02 EC B1 04 02 00 0x00013440 | B2 04 02 24 B2 04 02 00 B3 04 02 04 B3 04 02 18 DexFileMeta_23 0x00013450 | B3 04 02 2C B3 04 02 40 B3 04 02 54 B3 04 02 68 0x00013460 | B3 04 02 94 B3 04 02 D8 B3 04 02 D4 B4 04 02 20 -------------->< 0x00013470 | 00 00 00 2F 73 79 73 74 65 6D 2F 66 72 61 6D 65 0x00013480 | 77 6F 72 6B 2F 6D 69 75 69 73 79 73 74 65 6D 2E 0x00013490 | 6A 61 72 4F 52 20 05 78 DD E4 01 10 B5 04 02 AC ... DexFileMeta_24 0x00013f60 | 2E 05 02 6C 2E 05 02 80 2E 05 02 94 2E 05 02 A8 0x00013f70 | 2E 05 02 BC 2E 05 02 D0 2E 05 02 E4 2E 05 02 E8 0x00013f80 | 2E 05 02 2C 2F 05 02 88 2F 05 02 --------->
DexFileMeta_0:
| tyoe | name | value |
|---|---|---|
| uint32_t | dex_file_location_size | 0x00000021 |
| char* | dex_file_location_data | "/system/framework/core-libart.jar" |
| uint32_t | dex_file_checksum | 0xb5e804fc |
| uint32_t | dex_file_offset | 0x00012f8c |
| uint32_t[] | oat_class_offsets_pointer |
0x01f12c78 |
DexFiles:
0x00013f80 | 64 65 78 0A <--- 0x00013f90 | 30 33 35 00 EE 46 38 DD 46 FF 89 0D BE CA CD BD 0x00013fa0 | 63 CB 13 87 01 1C DC 87 53 DB 34 35 D8 2C 2C 00 0x00013fb0 | 70 00 00 00 78 56 34 12 00 00 00 00 00 00 00 00 0x00013fc0 | 08 2C 2C 00 5F 5C 00 00 70 00 00 00 E9 08 00 00 0x00013fd0 | EC 71 01 00 16 11 00 00 90 95 01 00 6E 1F 00 00 0x00013fe0 | 98 62 02 00 26 55 00 00 08 5E 03 00 56 08 00 00 DexFile_0 0x00013ff0 | 38 07 06 00 E0 1A 25 00 F8 11 07 00 AE 80 1C 00 ... 0x002d6c30 | 58 3E 23 00 04 20 00 00 55 0A 00 00 87 28 29 00 0x002d6c40 | 05 20 00 00 7C 02 00 00 08 E4 29 00 00 20 00 00 0x002d6c50 | 15 08 00 00 1F 0A 2A 00 00 10 00 00 01 00 00 00 0x002d6c60 | 08 2C 2C 00 64 65 78 0A 30 33 35 00 11 E1 2D 3F ---><----------- 0x002d6c70 | 23 F7 28 15 B0 A3 2C A4 34 0F 06 39 E4 5C D1 13 0x002d6c80 | 4E 66 79 6A 90 1E 04 00 70 00 00 00 78 56 34 12 DexFile_1 0x002d6c90 | 00 00 00 00 00 00 00 00 C0 1D 04 00 DD 0C 00 00 0x002d6ca0 | 70 00 00 00 BF 01 00 00 E4 33 00 00 3B 02 00 00 ... ... 0x01e4ed30 | 02 20 00 00 C5 40 00 00 A0 65 0E 00 03 20 00 00 0x01e4ed40 | 49 1E 00 00 AA D9 13 00 04 20 00 00 1C 05 00 00 0x01e4ed50 | 96 17 16 00 05 20 00 00 C7 00 00 00 78 69 16 00 DexFile_23 0x01e4ed60 | 00 20 00 00 2F 04 00 00 B7 77 16 00 00 10 00 00 0x01e4ed70 | 01 00 00 00 5C 74 17 00 64 65 78 0A 30 33 35 00 -------><------- 0x01e4ed80 | CE F8 BA FC 2E B8 5B 1A 70 4D 47 12 5C 10 61 40 0x01e4ed90 | 24 04 85 DE 8B EA 68 85 00 4F 0C 00 70 00 00 00 0x01e4eda0 | 78 56 34 12 00 00 00 00 00 00 00 00 30 4E 0C 00 0x01e4edb0 | 31 28 00 00 70 00 00 00 9B 04 00 00 34 A1 00 00 DexFile_24 ... 0x01f13c60 | 00 20 00 00 B4 02 00 00 DA C9 0B 00 00 10 00 00 0x01f13c70 | 01 00 00 00 30 4E 0C 00 ------->
DexFile_0:
| type | name | value |
|---|---|---|
| uint8_t[8] | magic_ | "dex.035" |
| uint32_t | checksum_ |
0xdd3846ee |
| uint8_t[20] | signature_ |
46 FF 89 0D BE CA CD BD |
| uint32_t | file_size_ |
0x002c2cd8 |
| uint32_t | header_size_ |
0x00000070 |
| uint32_t | endian_tag_ |
0x12345678 |
| uint32_t | link_size_ |
0x00000000 |
| uint32_t | link_off_ |
0x00000000 |
| uint32_t | map_off_ |
0x002c2c08 |
| uint32_t | string_ids_size_ |
0x00005c5f |
| uint32_t | string_ids_off_ |
0x00000070 |
| uint32_t | type_ids_size_ |
0x000008e9 |
| uint32_t | type_ids_off_ |
0x000171ec |
| uint32_t | proto_ids_size_ |
0x00001116 |
| uint32_t | proto_ids_off_ |
0x00019590 |
| uint32_t | field_ids_size_ |
0x00001f6e |
| uint32_t | field_ids_off_ |
0x00026298 |
| uint32_t | method_ids_size_ |
0x00005526 |
| uint32_t | method_ids_off_ |
0x00035e08 |
| uint32_t | class_defs_size_ |
0x00000856 |
| uint32_t | class_defs_off_ |
0x00060738 |
| uint32_t | data_size_ |
0x00251ae0 |
| uint32_t | data_off_ |
0x000711f8 |
|
StringId[] uint32_t string_data_off_; |
string_ids |
0x001c80ae |
|
TypeId[] uint32_t descriptor_idx_; |
type_ids |
0x0000062c |
|
ProtoId[] uint32_t shorty_idx_; |
proto_ids |
{
|
|
FieldId[] uint16_t class_idx_; |
field_ids |
{
|
|
MethodId[] uint16_t class_idx_; |
method_ids |
{
|
|
ClassDef[] uint16_t class_idx_; |
class_defs |
{
|
| uint32_t[] | data |
0x00000001, |
OatClasses:
0x01f13c70 | 0A 00 00 00 71 80 7B 02 <------- 0x01f13c80 | C0 30 05 02 91 80 7B 02 00 00 00 00 29 81 7B 02 0x01f13c90 | C4 30 05 02 81 82 7B 02 FB 30 05 02 71 80 7B 02 0x01f13ca0 | C0 30 05 02 D9 82 7B 02 C0 30 05 02 F9 82 7B 02 0x01f13cb0 | 03 31 05 02 81 83 7B 02 00 00 00 00 81 83 7B 02 DexFile_0_Class_0 0x01f13cc0 | 00 00 00 00 19 84 7B 02 0D 31 05 02 81 83 7B 02 0x01f13cd0 | 00 00 00 00 29 85 7B 02 2F 31 05 02 91 85 7B 02 0x01f13ce0 | 00 00 00 00 0A 00 02 00 0A 00 00 00 41 86 7B 02 ---><--><------- DexFile_0_Class_1 0x01f13cf0 | 39 31 05 02 E1 86 7B 02 45 31 05 02 91 87 7B 02 DexFile_0_Class_2 0x01f13d00 | 51 31 05 02 59 88 7B 02 5D 31 05 02 39 89 7B 02 ... ... 0x01f39230 | F1 CE A9 02 12 CD 0A 02 81 D1 A9 02 91 CD 0A 02 ---------------> 0x01f39240 | 0A 00 01 00 04 00 00 00 FE FF FF 1F F1 A3 7B 02 <--------------- 0x01f39250 | 19 34 05 02 81 F6 7C 02 00 00 00 00 81 F6 7C 02 0x01f39260 | 00 00 00 00 E9 D1 A9 02 9D CD 0A 02 F9 89 A2 02 0x01f39270 | 00 00 00 00 A9 D2 A9 02 AF CD 0A 02 C1 D3 A9 02 0x01f39280 | AF CD 0A 02 D9 D4 A9 02 00 00 00 00 B1 D5 A9 02 0x01f39290 | 00 00 00 00 99 D6 A9 02 00 00 00 00 91 D7 A9 02 0x01f392a0 | 00 00 00 00 91 D7 A9 02 00 00 00 00 59 D8 A9 02 0x01f392b0 | 00 00 00 00 59 D8 A9 02 00 00 00 00 21 D9 A9 02 DexFile_0_Class_2133 0x01f392c0 | 00 00 00 00 21 D9 A9 02 00 00 00 00 E1 D9 A9 02 0x01f392d0 | CF CD 0A 02 B1 DA A9 02 E5 CD 0A 02 A1 00 85 02 0x01f392e0 | 00 00 00 00 A1 00 85 02 00 00 00 00 E1 96 A2 02 0x01f392f0 | 00 00 00 00 E1 96 A2 02 00 00 00 00 31 DB A9 02 0x01f39300 | 00 00 00 00 31 DB A9 02 00 00 00 00 A1 00 85 02 0x01f39310 | 00 00 00 00 E1 96 A2 02 00 00 00 00 31 DB A9 02 0x01f39320 | 00 00 00 00 11 DC A9 02 F5 CD 0A 02 0A 00 00 00 -----------><--- 0x01f39330 | C1 DC A9 02 66 3C 05 02 29 DD A9 02 07 CE 0A 02 ---------------> DexFile_1_Class_0 0x01f39340 | 0A 00 00 00 21 DE A9 02 09 48 05 02 81 DE A9 02 0x01f39350 | 25 CE 0A 02 C1 EE 7C 02 91 32 05 02 71 DF A9 02 DexFile_1_Class_1 0x01f39360 | 3F CE 0A 02 0A 00 01 00 04 00 00 00 FF 7D 00 00 ---><----------- 0x01f39370 | 11 E0 A9 02 53 CE 0A 02 B9 E0 A9 02 61 CE 0A 02 DexFile_1_Class_2 ... ... ... ... 0x02053f70 | 61 A8 68 04 8B B8 4F 02 91 A9 68 04 A9 B8 4F 02 0x02053f80 | 21 AA 68 04 B7 B8 4F 02 08 00 01 00 08 00 00 00 -------><------- 0x02053f90 | FE FF FF FF 3F 00 00 00 F1 A3 7B 02 19 34 05 02 0x02053fa0 | D1 AA 68 04 CA B8 4F 02 A9 AB 68 04 DE B8 4F 02 0x02053fb0 | B9 AD 68 04 37 B9 4F 02 39 B0 68 04 EA B9 4F 02 0x02053fc0 | 21 B3 68 04 66 BA 4F 02 C1 B3 68 04 19 27 06 02 0x02053fd0 | 21 B4 68 04 74 BA 4F 02 19 B7 68 04 F8 BA 4F 02 0x02053fe0 | 91 B8 68 04 40 BB 4F 02 59 BC 68 04 04 BC 4F 02 0x02053ff0 | C1 BD 68 04 3E BC 4F 02 89 C0 68 04 BE BC 4F 02 0x02054000 | 39 C2 68 04 0E BD 4F 02 39 C6 68 04 CA BD 4F 02 0x02054010 | 41 CB 68 04 8E 65 33 02 A9 CB 68 04 22 BF 4F 02 DexFile_24_Class_x 0x02054020 | C1 CD 68 04 8A BF 4F 02 91 CE 68 04 9C BF 4F 02 0x02054030 | 71 D3 68 04 88 C0 4F 02 49 D5 68 04 E0 C0 4F 02 0x02054040 | 89 D8 68 04 BB C1 4F 02 49 D9 68 04 CF C1 4F 02 0x02054050 | D9 D9 68 04 DF C1 4F 02 A1 DA 68 04 F1 C1 4F 02 0x02054060 | 99 DC 68 04 A6 9C 0F 02 01 DD 68 04 55 C2 4F 02 0x02054070 | 01 E0 68 04 F5 C2 4F 02 C9 E1 68 04 A6 9C 0F 02 0x02054080 | 31 E2 68 04 A6 9C 0F 02 99 E2 68 04 49 C3 4F 02 0x02054090 | 09 E4 68 04 62 6C 0E 02 91 E4 68 04 77 C3 4F 02 0x020540a0 | D9 E5 68 04 91 C3 4F 02 D9 E7 68 04 03 C4 4F 02 0x020540b0 | A1 E8 68 04 17 C4 4F 02 69 E9 68 04 29 C4 4F 02 <---------------
DexFile_0_Class_2133:
| type | name | value |
|---|---|---|
| uint16_t enum Status { |
status |
0x000a |
|
uint16_t enum OatClassType { |
type | 0x0001 |
| uint32_t | bitmap_size(only type == 1) | 0x0004 |
| uint32_t[] | bintmap(only type == 1) |
0x1ffffffe |
|
OatMethodOffsets[] uint32_t code_offset_ |
methods |
0x027cf681,0x00000000 |
gc_map:
0x020540c0 | 00 00 00 00 0A 00 11 00 70 00 0F D6 00 0F EA 00 0x020540d0 | 08 B4 00 0F 00 01 01 84 00 0F DE 00 0F 86 00 0F 0x020540e0 | 08 00 08 58 00 0B 4A 00 09 98 00 0F 3C 00 08 9A ... 0x024fd410 | 7C 8C 7D 98 00 52 7F 09 00 07 00 A0 00 08 18 62 0x024fd420 | 1B 46 19 54 19 98 18 82 1B 09 00 05 00 70 00 48 0x024fd430 | 0F 22 0C 08 0C 5E 0F
mapping_table:
0x024fd430 | 00 00 11 11 08 00 34 04 0E 0x024fd440 | 02 0E 02 18 05 14 08 02 00 12 04 02 00 18 06 02 0x024fd450 | 00 10 04 02 00 10 04 08 03 0C 01 16 04 02 02 32 ... 0x0278c650 | 0A 14 05 0A 00 1C 04 02 00 0A 7B 07 07 08 00 3E 0x0278c660 | 03 0E 04 0E 02 20 03 16 75 08 0E 05 05 08 00 1A 0x0278c670 | 00 26 0A 16 03 12 03
vmap_table:
0x0278c670 | 00 06 00 03 02 04 05 01 04 0x0278c680 | 02 03 04 01 05 05 02 07 00 01 05 00 02 03 04 01 0x0278c690 | 05 03 04 05 00 01 04 03 00 02 01 05 03 00 02 04 ... 0x027b80b0 | 02 09 03 08 04 01 07 0E 00 02 03 08 0C 01 07 00 0x027b80c0 | 08 02 04 05 0A 01 07 00 03 02 05 0B 06 01 07 00 0x027b80d0 | 02 09 08 03 0A 01 07 00 02 08 03 04 0A 01 07 0E 0x027b80e0 | 00 11 0C 0D 02 01
padding:
0x027b80e0 | 00 00 00 00 00 00 00 00 00 00 0x027b80f0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x027b8100 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ... 0x027b8fd0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x027b8fe0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x027b8ff0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
oatexec:
0x027b9000 | D0 F8 00 F1 00 BE 00 00 D0 F8 04 F1 00 BE 00 00 0x027b9010 | D0 F8 04 C0 DC F8 08 F1 00 BE 00 00 00 00 00 00 0x027b9020 | D9 F8 0C F1 00 BE 00 00 D9 F8 10 F1 00 BE 00 00 0x027b9030 | D9 F8 14 F1 00 BE 00 00 D9 F8 AC F1 00 BE 00 00 ... 0x0468ffd0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0468ffe0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0468fff0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Bridge & Trampoline:
0x027b9000 | ldr.w pc, [r0, #256] ; INTERPRETER TO INTERPRETER BRIDGE OFFSET 0x027b9004 | 0x027b9008 | ldr.w pc, [r0, #260] ; INTERPRETER TO COMPILED CODE BRIDGE OFFSET 0x027b900c | 0x027b9010 | ldr.w r12, [r0, #4] ; JNI DLSYM LOOKUP OFFSET 0x027b9014 | ldr.w pc, [r12, #264] ; 0x027b9018 | 0x027b901c | 0x027b9020 | ldr.w pc, [r9, #268] ; PORTABLE IMT CONFLICT TRAMPOLINE OFFSET 0x027b9024 | 0x027b9028 | ldr.w pc, [r9, #272] ; PORTABLE RESOLUTION TRAMPOLINE OFFSET 0x027b902c | 0x027b9030 | ldr.w pc, [r9, #276] ; PORTABLE TO INTERPRETER BRIDGE OFFSET 0x027b9034 | 0x027b9038 | ldr.w pc, [r9, #428] ; QUICK GENERIC JNI TRAMPOLINE OFFSET 0x027b903c | 0x027b9040 | ldr.w pc, [r9, #528] ; QUICK IMT CONFLICT TRAMPOLINE OFFSET 0x027b9044 | 0x027b9048 | ldr.w pc, [r9, #532] ; QUICK RESOLUTION TRAMPOLINE OFFSET 0x027b904c | 0x027b9050 | ldr.w pc, [r9, #536] ; QUICK TO INTERPRETER BRIDGE OFFSET 0x027b9054 |
Methods:
0x027b9050 | 39 BC 2B 00 F9 C9 02 00 <------- 0x027b9060 | 00 00 00 00 00 00 00 00 00 00 00 00 04 00 00 00 Method_0 0x027b9070 | 70 47 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ---><----------- 0x027b9080 | 40 00 00 00 E0 4D 00 00 00 00 00 00 7A 00 00 00 0x027b9090 | 2D E9 E0 4D AD F2 24 0D 00 90 11 91 4F F0 01 0C 0x027b90a0 | CD F8 08 C0 D9 F8 C8 C0 CD F8 04 C0 0D F2 04 0C 0x027b90b0 | C9 F8 C8 C0 DD F8 44 C0 CD F8 0C C0 C9 F8 8C D0 Method_1 0x027b90c0 | 4F F0 00 0C C9 F8 90 C0 48 46 D0 F8 94 C1 E0 47 0x027b90d0 | 04 90 0D F2 0C 01 D9 F8 98 00 DD F8 00 C0 DC F8 0x027b90e0 | 20 C0 E0 47 04 99 4A 46 D2 F8 A4 C1 E0 47 D9 F8 0x027b90f0 | 7C C0 BC F1 00 0F 03 D1 0D F2 24 0D BD E8 E0 8D 0x027b9100 | 60 46 D9 F8 34 C2 E0 47 00 BE 00 00 00 00 00 00 ---------> 0x027b9110 | EF BC 2B 00 B0 CA 02 00 40 00 00 00 E0 85 00 00 <--------------- 0x027b9120 | 00 00 00 00 3C 01 00 00 BD F5 00 5C DC F8 00 C0 0x027b9130 | 2D E9 E0 45 8A B0 05 1C 00 90 8A 46 29 1C 0A 69 0x027b9140 | 50 46 D2 F8 44 24 20 B1 01 68 D9 F8 3C E1 10 1C 0x027b9150 | F0 47 07 1C 00 2F 56 D1 DF F8 04 01 D9 F8 2C E1 Method_2 0x027b9160 | 29 1C F0 47 D9 F8 2C E1 07 1C DF F8 F0 00 29 1C 0x027b9170 | F0 47 DF F8 CC E0 06 1C DF F8 DC 00 31 1C F0 47 ... 0x0468f8c0 | 85 53 C0 58 98 B3 82 6E 0A 2A 30 DB BF F3 5B 8F 0x0468f8d0 | D0 F8 88 60 28 1C C0 68 31 1C 52 46 D0 F8 A4 06 0x0468f8e0 | D0 F8 28 E0 F0 47 D9 F8 2C E1 06 1C DF F8 5C 00 0x0468f8f0 | 29 1C F0 47 DF F8 4C E0 07 1C DF F8 4C 00 39 1C Method_n-1 0x0468f900 | F0 47 28 1C C0 68 00 22 04 92 45 F2 2C 3C 50 F8 0x0468f910 | 0C 00 00 22 D0 F8 28 E0 05 92 41 46 32 1C 3B 1C 0x0468f920 | F0 47 01 3C 00 F0 09 80 0A B0 BD E8 E0 85 D9 F8 0x0468f930 | 44 E1 40 F2 25 40 F0 47 C8 E7 D9 F8 30 E2 F0 47 0x0468f940 | F2 E7 00 00 49 84 BB 73 30 D0 43 70 A0 CD 43 70 0x0468f950 | FD 32 F0 01 78 23 F0 01 30 00 00 00 E0 85 00 00 <--------------- 0x0468f960 | 00 00 00 00 84 00 00 00 BD F5 00 5C DC F8 00 C0 0x0468f970 | 2D E9 E0 45 86 B0 05 1C 00 90 8A 46 17 1C DF F8 0x0468f980 | 60 E0 DF F8 64 00 39 1C F0 47 06 1C DE B9 6A 69 0x0468f990 | D5 F8 14 C0 44 F2 A0 63 D6 58 DF F8 40 E0 49 F6 Method_n 0x0468f9a0 | F8 20 5C F8 00 80 DF F8 3C 00 31 1C 42 46 F0 47 0x0468f9b0 | 28 1C C0 68 51 46 3A 1C 45 F2 30 3C 50 F8 0C 00 0x0468f9c0 | D0 F8 28 E0 F0 47 01 3C 00 F0 03 80 06 B0 BD E8 0x0468f9d0 | E0 85 D9 F8 30 E2 F0 47 F8 E7 00 00 49 61 23 74 0x0468f9e0 | 31 84 1E 74 38 91 65 70 88 67 64 70 00 00 00 00 -----------><--- 0x0468f9f0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0468fa00 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0468fa10 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ... padding 0x0468ffd0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0468ffe0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0x0468fff0 | 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 --------------->
Method_0:
0x027b9058 | 0x002bbc39 OatQuickMethodHeader::mapping_table_offset_ 0x027b905c | 0x0002c9f9 OatQuickMethodHeader::vmap_table_offset_ 0x027b9060 | 0x00000000 OatQuickMethodHeader::QuickMethodFrameInfo::frame_size_in_bytes_ 0x027b9064 | 0x00000000 OatQuickMethodHeader::QuickMethodFrameInfo::core_spill_mask_ 0x027b9068 | 0x00000000 OatQuickMethodHeader::QuickMethodFrameInfo::fp_spill_mask_ 0x027b906c | 0x00000004 OatQuickMethodHeader::code_size_ 0x027b8070 | 4770 bx lr 0x027b8072 | 0000 lsls r0, r0, #0
oatdump:
0: Ljava/lang/Object; (offset=0x01f12c78) (type_idx=322) (StatusInitialized) (OatClassAllCompiled)
0: void java.lang.Object.<init>() (dex_method_idx=2877)
DEX CODE:
0x0000: return-void
OatMethodOffsets (offset=0x01f12c7c)
code_offset: 0x027b8071
gc_map: (offset=0x020530c0)
OatQuickMethodHeader (offset=0x027b8058)
mapping_table: (offset=0x024fc437)
vmap_table: (offset=0x0278b677)
QuickMethodFrameInfo
frame_size_in_bytes: 0
core_spill_mask: 0x00000000
fp_spill_mask: 0x00000000
CODE: (code_offset=0x027b8071 size_offset=0x027b806c size=4)...
0x027b8070: 4770 bx lr
0x027b8072: 0000 lsls r0, r0, #0
Method_1:
0x027b9078 | 0x00000000 OatQuickMethodHeader::mapping_table_offset_
0x027b907c | 0x00000000 OatQuickMethodHeader::vmap_table_offset_
0x027b9080 | 0x00000040 OatQuickMethodHeader::QuickMethodFrameInfo::frame_size_in_bytes_
0x027b9084 | 0x00004de0 OatQuickMethodHeader::QuickMethodFrameInfo::core_spill_mask_
0x027b9088 | 0x00000000 OatQuickMethodHeader::QuickMethodFrameInfo::fp_spill_mask_
0x027b908c | 0x0000007a OatQuickMethodHeader::code_size_
0x027b8090 | e92d4de0 push {r5, r6, r7, r8, r10, r11, lr}
0x027b8094 | f2ad0d24 subw sp, sp, #36
0x027b8098 | 9000 str r0, [sp, #0]
0x027b809a | 9111 str r1, [sp, #68]
0x027b809c | f04f0c01 mov.w r12, #1
0x027b80a0 | f8cdc008 str.w r12, [sp, #8]
0x027b80a4 | f8d9c0c8 ldr.w r12, [r9, #200] ; top_handle_scope
0x027b80a8 | f8cdc004 str.w r12, [sp, #4]
0x027b80ac | f20d0c04 addw r12, sp, #4
0x027b80b0 | f8c9c0c8 str.w r12, [r9, #200]
0x027b80b4 | f8ddc044 ldr.w r12, [sp, #68]
0x027b80b8 | f8cdc00c str.w r12, [sp, #12]
0x027b80bc | f8c9d08c str.w sp, [r9, #140]
0x027b80c0 | f04f0c00 mov.w r12, #0
0x027b80c4 | f8c9c090 str.w r12, [r9, #144]
0x027b80c8 | 4648 mov r0, r9
0x027b80ca | f8d0c194 ldr.w r12, [r0, #404]
0x027b80ce | 47e0 blx r12
0x027b80d0 | 9004 str r0, [sp, #16]
0x027b80d2 | f20d010c addw r1, sp, #12
0x027b80d6 | f8d90098 ldr.w r0, [r9, #152] ; jni_env
0x027b80da | f8ddc000 ldr.w r12, [sp, #0]
0x027b80de | f8dcc020 ldr.w r12, [r12, #32]
0x027b80e2 | 47e0 blx r12
0x027b80e4 | 9904 ldr r1, [sp, #16]
0x027b80e6 | 464a mov r2, r9
0x027b80e8 | f8d2c1a4 ldr.w r12, [r2, #420]
0x027b80ec | 47e0 blx r12
0x027b80ee | f8d9c07c ldr.w r12, [r9, #124] ; exception
0x027b80f2 | f1bc0f00 cmp.w r12, #0
0x027b80f6 | d103 bne +6 (0x027b8100)
0x027b80f8 | f20d0d24 addw sp, sp, #36
0x027b80fc | e8bd8de0 pop {r5, r6, r7, r8, r10, r11, pc}
0x027b8100 | 4660 mov r0, r12
0x027b8102 | f8d9c234 ldr.w r12, [r9, #564] ; pDeliverException
0x027b8106 | 47e0 blx r12
0x027b8108 | be00
oatdump:
1: java.lang.Object java.lang.Object.internalClone() (dex_method_idx=2883)
DEX CODE:
OatMethodOffsets (offset=0x01f12c84)
code_offset: 0x027b8091
gc_map: (offset=0x00000000)
OatQuickMethodHeader (offset=0x027b8078)
mapping_table: (offset=0x00000000)
vmap_table: (offset=0x00000000)
QuickMethodFrameInfo
frame_size_in_bytes: 64
core_spill_mask: 0x00004de0 (r5, r6, r7, r8, r10, r11, r14)
fp_spill_mask: 0x00000000
CODE: (code_offset=0x027b8091 size_offset=0x027b808c size=122)...
0x027b8090: e92d4de0 push {r5, r6, r7, r8, r10, r11, lr}
0x027b8094: f2ad0d24 subw sp, sp, #36
0x027b8098: 9000 str r0, [sp, #0]
0x027b809a: 9111 str r1, [sp, #68]
0x027b809c: f04f0c01 mov.w r12, #1
0x027b80a0: f8cdc008 str.w r12, [sp, #8]
0x027b80a4: f8d9c0c8 ldr.w r12, [r9, #200] ; top_handle_scope
0x027b80a8: f8cdc004 str.w r12, [sp, #4]
0x027b80ac: f20d0c04 addw r12, sp, #4
0x027b80b0: f8c9c0c8 str.w r12, [r9, #200]
0x027b80b4: f8ddc044 ldr.w r12, [sp, #68]
0x027b80b8: f8cdc00c str.w r12, [sp, #12]
0x027b80bc: f8c9d08c str.w sp, [r9, #140]
0x027b80c0: f04f0c00 mov.w r12, #0
0x027b80c4: f8c9c090 str.w r12, [r9, #144]
0x027b80c8: 4648 mov r0, r9
0x027b80ca: f8d0c194 ldr.w r12, [r0, #404]
0x027b80ce: 47e0 blx r12
0x027b80d0: 9004 str r0, [sp, #16]
0x027b80d2: f20d010c addw r1, sp, #12
0x027b80d6: f8d90098 ldr.w r0, [r9, #152] ; jni_env
0x027b80da: f8ddc000 ldr.w r12, [sp, #0]
0x027b80de: f8dcc020 ldr.w r12, [r12, #32]
0x027b80e2: 47e0 blx r12
0x027b80e4: 9904 ldr r1, [sp, #16]
0x027b80e6: 464a mov r2, r9
0x027b80e8: f8d2c1a4 ldr.w r12, [r2, #420]
0x027b80ec: 47e0 blx r12
0x027b80ee: f8d9c07c ldr.w r12, [r9, #124] ; exception
0x027b80f2: f1bc0f00 cmp.w r12, #0
0x027b80f6: d103 bne +6 (0x027b8100)
0x027b80f8: f20d0d24 addw sp, sp, #36
0x027b80fc: e8bd8de0 pop {r5, r6, r7, r8, r10, r11, pc}
0x027b8100: 4660 mov r0, r12
0x027b8102: f8d9c234 ldr.w r12, [r9, #564] ; pDeliverException
0x027b8106: 47e0 blx r12
0x027b8108: be00
| name | offset | size |
|---|---|---|
|
|
|
54 |
|
|
|
593 |
|
|
|
129A5 |
|
DexFiles |
13f8c | 1EFFCEC |
|
|
|
140448 |
|
|
|
4A9377 |
|
|
|
28F240 |
|
|
|
2BA6F |
|
|
|
F1A |
|
|
|
1ED7000 |