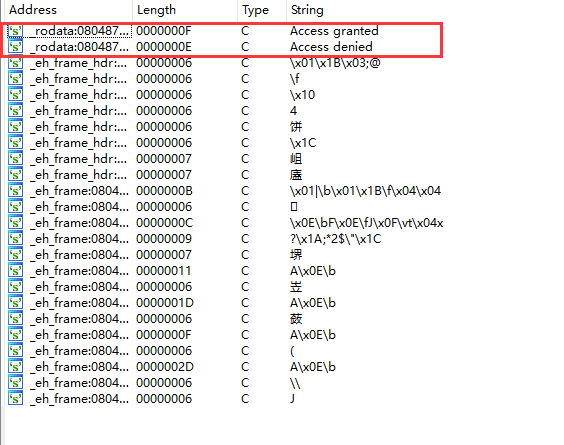
1、查询基本信息,32位程序

2、载入IDA中,查询字符串
3、进入 main 函数,发现如果要得到正确结果需要运行 function() 和 encrypt() 函数
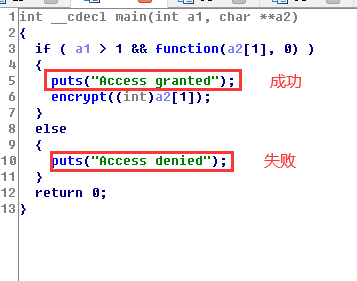
4、function() 函数正确运行需要参数在 [3, 9, 4, 1, 0, 5, 6, 7] 中
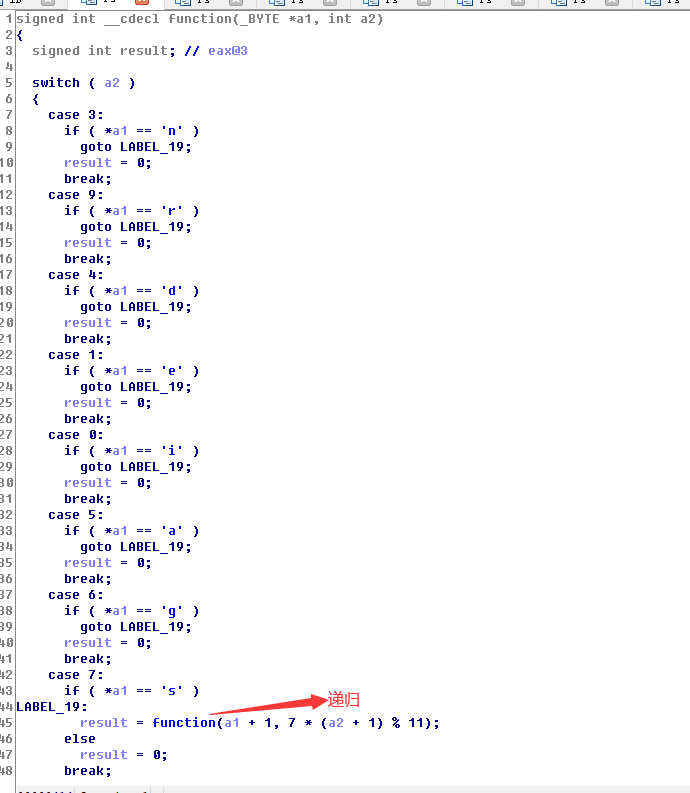

根据 main() 函数可以知道 function() 的 a2 参数的初值为 0,根据递归部分可以编写脚本
1 def func1(a2): 2 a = [] 3 a.append(a2) 4 while True: 5 a2 = 7 * (a2 + 1) % 11 6 if a2 in [3, 9, 4, 1, 0, 5, 6, 7]: 7 a.append(a2) 8 else: 9 break 10 return a
switch() 语句,即将上一步得到的列表的各个数值转换为字符
1 def func2(t): 2 result = '' 3 for i in t: 4 if i == 3: result += 'n' 5 elif i == 9: result += 'r' 6 elif i == 4: result += 'd' 7 elif i == 1: result += 'e' 8 elif i == 0: result += 'i' 9 elif i == 5: result += 'a' 10 elif i == 6: result += 'g' 11 elif i == 7: result += 's' 12 else: pass 13 return result
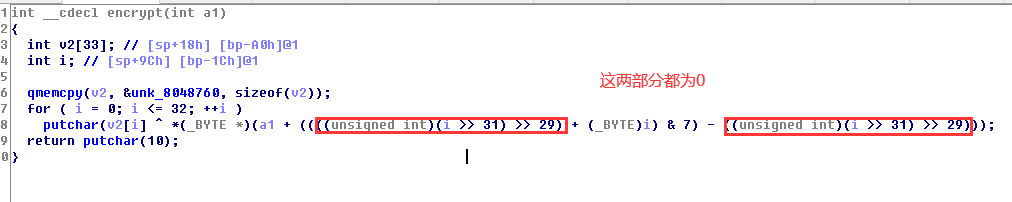
5、进入 encrypt() 中,程序仅仅是将 v2 和 a1 两个数组中的元素进行了异或运算
1 def func3(s, t): 2 result = '' 3 for i in range(33): 4 a = ord(s[i&7]) 5 b = a ^ t[i] 6 result += chr(b) 7 return result
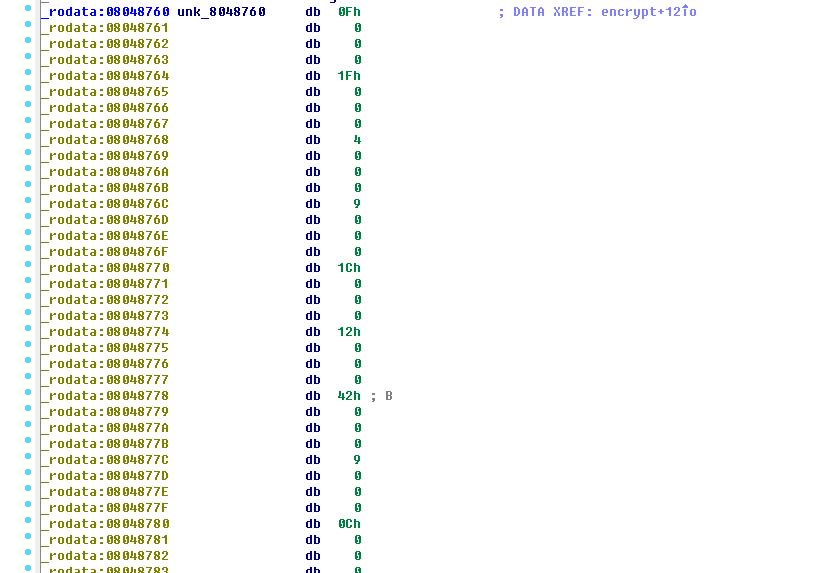
当我们查看 unk_8048760 即能得到 v2 的值,需要注意的是其中有一个值为 0
6、编写 EXP,运行得到 flag
1 def main(): 2 v2 = [0x0F, 0x1F, 0x4, 0x9, 0x1C, 0x12, 0x42, 0x9, 0x0C, 0x44, 0x0D, 0x7, 0x9, 0x6, 0x2D, 0x37, 0x59, 0x1E, 0x0, 0x59, 0x0F, 0x8, 0x1C, 0x23, 0x36, 0x7, 0x55, 0x2, 0x0C, 0x8, 0x41, 0x0A, 0x14] 3 a = func1(0) 4 print(a) 5 s = func2(a) 6 print(s) 7 flag = func3(s ,v2) 8 print(flag) 9 10 def func1(a2): 11 a = [] 12 a.append(a2) 13 while True: 14 a2 = 7 * (a2 + 1) % 11 15 if a2 in [3, 9, 4, 1, 0, 5, 6, 7]: 16 a.append(a2) 17 else: 18 break 19 return a 20 21 def func2(t): 22 result = '' 23 for i in t: 24 if i == 3: result += 'n' 25 elif i == 9: result += 'r' 26 elif i == 4: result += 'd' 27 elif i == 1: result += 'e' 28 elif i == 0: result += 'i' 29 elif i == 5: result += 'a' 30 elif i == 6: result += 'g' 31 elif i == 7: result += 's' 32 else: pass 33 return result 34 35 def func3(s, t): 36 result = '' 37 for i in range(33): 38 a = ord(s[i&7]) 39 b = a ^ t[i] 40 result += chr(b) 41 return result 42 43 main()
