openssl源码下载
github官网:GitHub - openssl/openssl at OpenSSL_1_1_0-stable
下载对应版本,我下的 1.1.0stable .
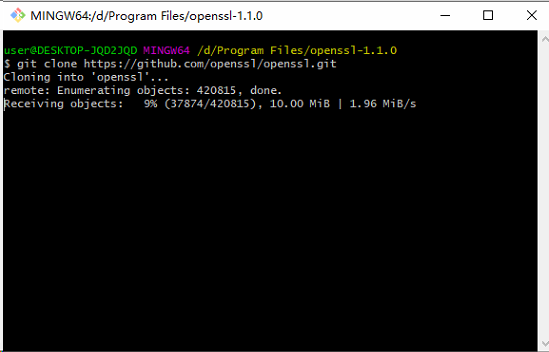
不要放到c:根目录下,否则权限问题会引发各种问题
perl下载
下载简化版本:Strawberry Perl for Windows
NASM下载
官网:NASM
安装VS2019
没什么好说的
开始编译openssl
注意,不同的编译目标要选择不同的编译环境,否则可能会提示连接错误,x86 x64目标机不符等。
此外每次编译,建议你重新解压源代码得到一个全新的目录进行编译,否则可能有后遗症.
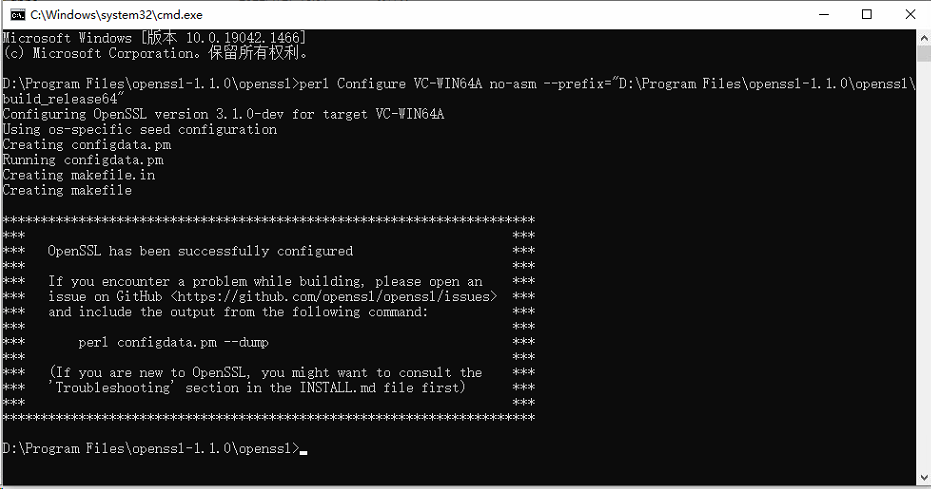
第一步:在openssl目录下打开cmd,根据你的机器,敲以下命令(标黄的部分是想build在哪里的路径,我选择的是 D:\Program Files\openssl-1.1.0\openssl\build_release64 )
32位:
perl Configure VC-WIN32 no-asm --prefix="...\opensslh110\build_release32"
64位:
perl Configure VC-WIN64A no-asm --prefix="...\opensslh110\build_release64"
perl Configure VC-WIN64A no-asm --prefix="D:\Program Files\openssl-1.1.0\openssl\build_release64"
得到以下结果:
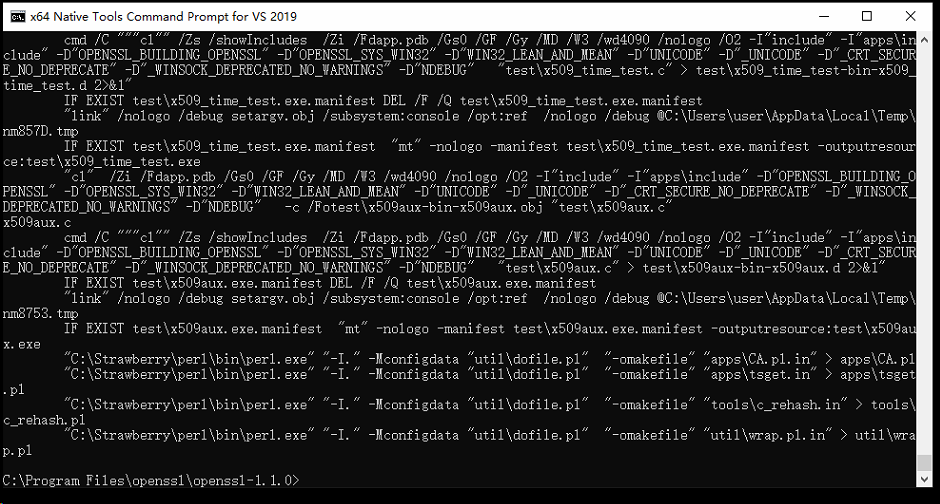
第二步:在openssl目录下面敲以下命令
nmake
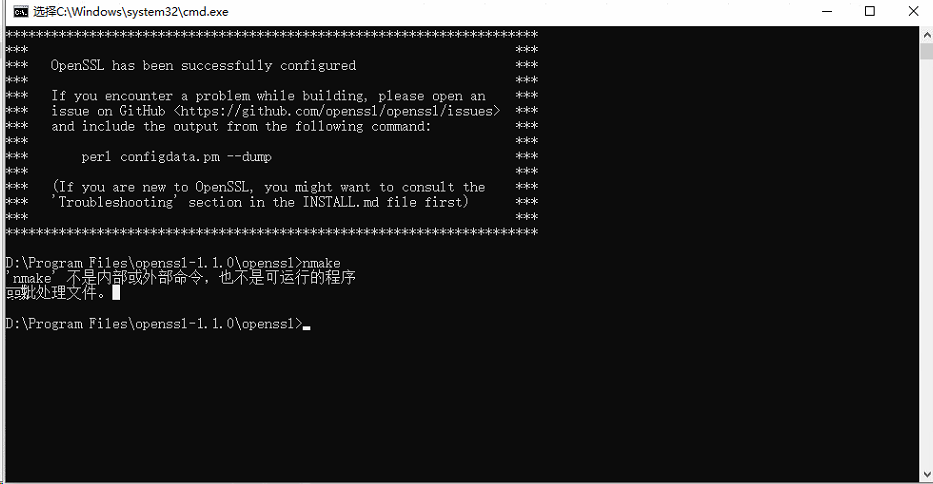
wtf? 使用vs2019自带的命令行,
进入到openssl目录下面,敲入 nmake 命令,上面错误解决!
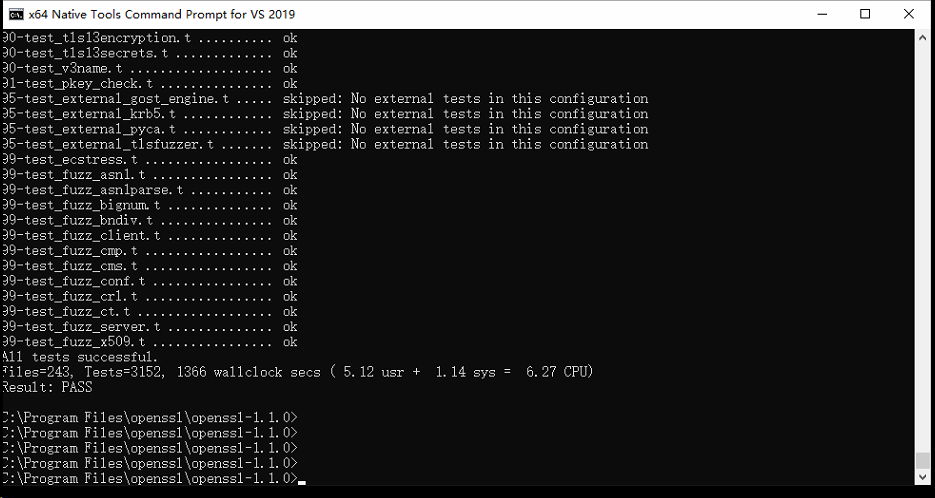
第三步:测试make是否成功
在同样的目录下敲击以下命令:
nmake test
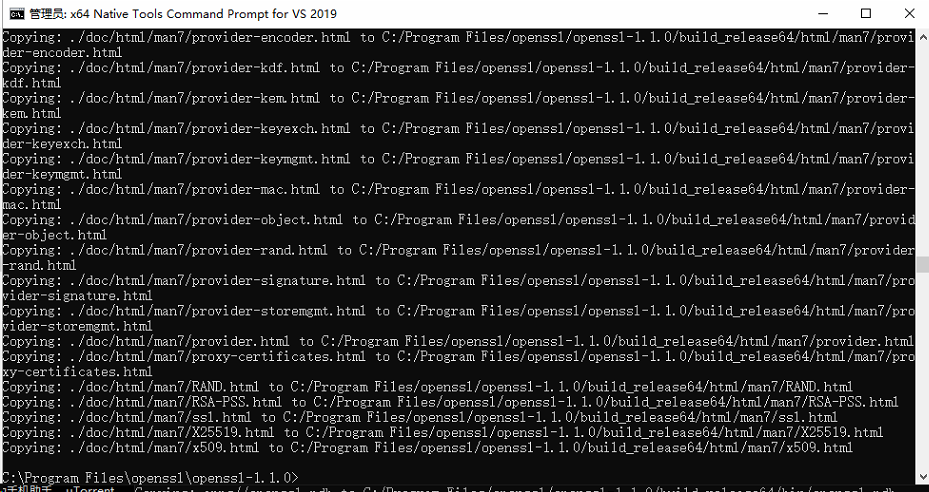
第四步:完成安装,敲以下命令
nmake install
第五步:vs2019项目里面添加依赖
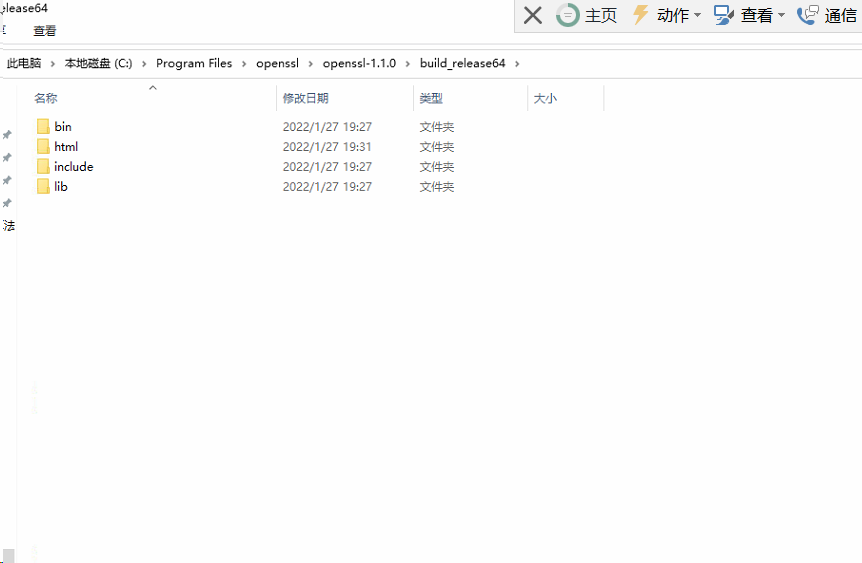
可以看到编译完成后有如下内容,需要将对应的依赖加到工程里面。
- 添加头文件目录 ...\include
- 添加
library目录 ...\lib - 添加附加依赖项
使用例子:
AES+SSE2+AVX2+openssl

/* * Copyright 2021 Florent Bondoux * * Licensed under the Apache License, Version 2.0 (the "License"); * you may not use this file except in compliance with the License. * You may obtain a copy of the License at * * http://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License. */ #pragma once #include <cstdint> #include <stdio.h> #include <stdlib.h> namespace AESNI { struct AES_KEY_128 { uint32_t rd_key[4 * (10 + 1)];//44 > 256 if attribute aligned(16) }; struct AES_KEY_192 { uint32_t rd_key[4 * (12 + 1)];//52 > 256 }; struct AES_KEY_256 { uint32_t rd_key[4 * (14 + 1)];//60 > 256 }; struct AES_KEY { uint32_t rd_key[4 * (14 + 1)];//60 = 64*4 = 256 int rounds;//1 }; //密钥编排肯定要做,事实上这个操作复杂了,没有密钥编排最好了 //AES128 10轮 int AES128_set_encrypt_key(const unsigned char *userKey, AES_KEY_128 *key);//userKey?是干什么用的 int AES128_set_decrypt_key(const unsigned char *userKey, AES_KEY_128 *key); void AES128_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY_128 *key); void AES128_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY_128 *key); //AES192 12轮 int AES192_set_encrypt_key(const unsigned char *userKey, AES_KEY_192 *key); int AES192_set_decrypt_key(const unsigned char *userKey, AES_KEY_192 *key); void AES192_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY_192 *key); void AES192_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY_192 *key); //AES256 14轮 int AES256_set_encrypt_key(const unsigned char *userKey, AES_KEY_256 *key); int AES256_set_decrypt_key(const unsigned char *userKey, AES_KEY_256 *key); void AES256_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY_256 *key); void AES256_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY_256 *key); //pick不同的版本调用上面的函数 int AES_set_encrypt_key(const unsigned char *userKey, const int bits, AES_KEY *key); int AES_set_decrypt_key(const unsigned char *userKey, const int bits, AES_KEY *key); void AES_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY *key); void AES_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY *key); }

/* * Copyright 2021 Florent Bondoux * * Licensed under the Apache License, Version 2.0 (the "License"); * you may not use this file except in compliance with the License. * You may obtain a copy of the License at * * http://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License. */ #include "aesni.h" #include <cstring> #include <emmintrin.h> // SSE2 #include <immintrin.h> // AVX2 #include <wmmintrin.h> // AESNI // not sure if this one is standard #ifndef _MM_SHUFFLE # define _MM_SHUFFLE(z, y, x, w) (((z) << 6) | ((y) << 4) | ((x) << 2) | (w)) #endif #if defined(__clang__) # pragma clang attribute push (__attribute__((target("avx2,aes"))), apply_to=function) # define INLINE static inline __attribute((always_inline)) #elif defined(__GNUC__) # pragma GCC target ("avx2", "aes") # define INLINE static inline __attribute((always_inline)) #endif #ifndef INLINE # define INLINE static inline //内联函数定义,函数被调用时,需要出栈入栈,inline 解决频繁的内存消耗 #endif namespace AESNI { namespace P { /* * AES-128 * Create the next round key (k1), using the previous round key (k0) */ template<const int rcon> INLINE void AES_128_key_exp(__m128i k0, __m128i &k1) { __m128i core = _mm_shuffle_epi32(_mm_aeskeygenassist_si128(k0, rcon), _MM_SHUFFLE(3,3,3,3)); k1 = _mm_xor_si128(k0, _mm_slli_si128(k0, 4)); k1 = _mm_xor_si128(k1, _mm_slli_si128(k1, 8)); k1 = _mm_xor_si128(k1, core); } /* * AES-192 * Create the next 192 bits of round keys data (k1[64:128] + k2[0:64]) using the previous round keys (k0[0:128] + k1[0:64]) * AES_192_key_exp_1 and AES_192_key_exp_2 are used alternatively depending on data alignment * * k0 [ Prev | Prev | Prev | Prev ] * k1 [ Prev | Prev | Next | Next ] * k2 [ Next | Next | Next | Next ] */ template<const int rcon> INLINE void AES_192_key_exp_1(__m128i k0, __m128i &k1, __m128i &k2) { __m128i core = _mm_shuffle_epi32(_mm_aeskeygenassist_si128(k1, rcon), _MM_SHUFFLE(1,1,1,1)); k2 = _mm_xor_si128(k0, _mm_slli_si128(k0, 4)); k2 = _mm_xor_si128(k2, _mm_slli_si128(k2, 8)); __m128i tmp = _mm_slli_si128(k1, 8); tmp = _mm_xor_si128(tmp, _mm_slli_si128(tmp, 4)); k2 = _mm_xor_si128(k2, core); k2 = _mm_shuffle_epi32(k2, _MM_SHUFFLE(1, 0, 3, 2)); // rotate, bits[64:128] are in position k1 = _mm_blend_epi32(k1, k2, 0+0+4+8); // write bits[0:64] tmp = _mm_xor_si128(tmp, _mm_shuffle_epi32(k2, _MM_SHUFFLE(1,1,1,1))); k2 = _mm_blend_epi32(k2, tmp, 0+0+4+8); // blend bits[128:192] } /* * AES-192 * Create the next 192 bits of round keys data (k2[0:128] + k3[0:64]) using the previous round keys (k0[64:128] + k1[0:128]) * AES_192_key_exp_1 and AES_192_key_exp_2 are used alternatively depending on data alignment * * k0 [ XXXX | XXXX | Prev | Prev ] * k1 [ Prev | Prev | Prev | Prev ] * k2 [ Next | Next | Next | Next ] * k3 [ Next | Next | Dirt | Dirt ] */ template<const int rcon> INLINE void AES_192_key_exp_2(__m128i k0, __m128i k1, __m128i &k2, __m128i &k3) { __m128i core = _mm_shuffle_epi32(_mm_aeskeygenassist_si128(k1, rcon), _MM_SHUFFLE(3,3,3,3)); k2 = _mm_blend_epi32(k0, k1, 1+2+0+0); k2 = _mm_shuffle_epi32(k2, _MM_SHUFFLE(1,0,3,2)); // rotate k2 = _mm_xor_si128(k2, _mm_slli_si128(k2, 4)); k2 = _mm_xor_si128(k2, _mm_slli_si128(k2, 8)); k3 = _mm_srli_si128(k1, 8); k3 = _mm_xor_si128(k3, _mm_slli_si128(k3, 4)); k2 = _mm_xor_si128(k2, core); // write bits[0:128] k3 = _mm_xor_si128(k3, _mm_shuffle_epi32(k2, _MM_SHUFFLE(3,3,3,3))); // this also override k3[64:128] with dirty data } /* * AES-192 * Create the last 128 bits of round keys data * Same as AES_192_key_exp_2 but generate 128 bits * * k0 [ XXXX | XXXX | Prev | Prev ] * k1 [ Prev | Prev | Prev | Prev ] * k2 [ Next | Next | Next | Next ] */ template<const int rcon> INLINE void AES_192_key_exp_3(__m128i k0, __m128i k1, __m128i &k2) { __m128i core = _mm_shuffle_epi32(_mm_aeskeygenassist_si128(k1, rcon), _MM_SHUFFLE(3,3,3,3)); k2 = _mm_blend_epi32(k0, k1, 1+2+0+0); k2 = _mm_shuffle_epi32(k2, _MM_SHUFFLE(1,0,3,2)); // rotate k2 = _mm_xor_si128(k2, _mm_slli_si128(k2, 4)); k2 = _mm_xor_si128(k2, _mm_slli_si128(k2, 8)); k2 = _mm_xor_si128(k2, core); } /* * AES-256 * Generate the 1st part of the next 256 bits of round keys data using the previous 256 bits * Called alternating with AES_256_key_exp_2 */ template<const int rcon> INLINE void AES_256_key_exp_1(__m128i k0, __m128i k1, __m128i &k2) { __m128i core = _mm_shuffle_epi32(_mm_aeskeygenassist_si128(k1, rcon), _MM_SHUFFLE(3,3,3,3)); k2 = _mm_xor_si128(k0, _mm_slli_si128(k0, 4)); k2 = _mm_xor_si128(k2, _mm_slli_si128(k2, 8)); k2 = _mm_xor_si128(k2, core); } /* * AES-256 * Generate the 2nd part of next 256 bits of round keys data using the previous 256 bits * Called alternating with AES_256_key_exp_1 */ INLINE void AES_256_key_exp_2(__m128i k0, __m128i k1, __m128i &k2) { __m128i sboxed = _mm_shuffle_epi32(_mm_aeskeygenassist_si128(k1, 0), _MM_SHUFFLE(2,2,2,2)); k2 = _mm_xor_si128(k0, _mm_slli_si128(k0, 4)); k2 = _mm_xor_si128(k2, _mm_slli_si128(k2, 8)); k2 = _mm_xor_si128(k2, sboxed); } } int AES128_set_encrypt_key(const unsigned char *userKey, AES_KEY_128 *key) { if (!userKey || !key) { return -1; } __m128i *rk128 = reinterpret_cast<__m128i *>(key->rd_key); ::memcpy(rk128, userKey, 16); P::AES_128_key_exp<0x01>(rk128[ 0], rk128[ 1]); P::AES_128_key_exp<0x02>(rk128[ 1], rk128[ 2]); P::AES_128_key_exp<0x04>(rk128[ 2], rk128[ 3]); P::AES_128_key_exp<0x08>(rk128[ 3], rk128[ 4]); P::AES_128_key_exp<0x10>(rk128[ 4], rk128[ 5]); P::AES_128_key_exp<0x20>(rk128[ 5], rk128[ 6]); P::AES_128_key_exp<0x40>(rk128[ 6], rk128[ 7]); P::AES_128_key_exp<0x80>(rk128[ 7], rk128[ 8]); P::AES_128_key_exp<0x1B>(rk128[ 8], rk128[ 9]); P::AES_128_key_exp<0x36>(rk128[ 9], rk128[10]); return 0; } int AES128_set_decrypt_key(const unsigned char *userKey, AES_KEY_128 *key) { if (!userKey || !key) { return -1; } __m128i *rk128 = reinterpret_cast<__m128i *>(key->rd_key); ::memcpy(&(rk128[10]), userKey, 16); P::AES_128_key_exp<0x01>(rk128[10], rk128[ 9]); P::AES_128_key_exp<0x02>(rk128[ 9], rk128[ 8]); rk128[ 9] = _mm_aesimc_si128(rk128[9]); P::AES_128_key_exp<0x04>(rk128[ 8], rk128[ 7]); rk128[ 8] = _mm_aesimc_si128(rk128[8]); P::AES_128_key_exp<0x08>(rk128[ 7], rk128[ 6]); rk128[ 7] = _mm_aesimc_si128(rk128[7]); P::AES_128_key_exp<0x10>(rk128[ 6], rk128[ 5]); rk128[ 6] = _mm_aesimc_si128(rk128[6]); P::AES_128_key_exp<0x20>(rk128[ 5], rk128[ 4]); rk128[ 5] = _mm_aesimc_si128(rk128[5]); P::AES_128_key_exp<0x40>(rk128[ 4], rk128[ 3]); rk128[ 4] = _mm_aesimc_si128(rk128[4]); P::AES_128_key_exp<0x80>(rk128[ 3], rk128[ 2]); rk128[ 3] = _mm_aesimc_si128(rk128[3]); P::AES_128_key_exp<0x1B>(rk128[ 2], rk128[ 1]); rk128[ 2] = _mm_aesimc_si128(rk128[2]); P::AES_128_key_exp<0x36>(rk128[ 1], rk128[ 0]); rk128[ 1] = _mm_aesimc_si128(rk128[1]); return 0; } int AES192_set_encrypt_key(const unsigned char *userKey, AES_KEY_192 *key) { if (!userKey || !key) { return -1; } __m128i *rk128 = reinterpret_cast<__m128i *>(key->rd_key); ::memcpy(rk128, userKey, 24); P::AES_192_key_exp_1<0x01>(rk128[ 0], rk128[ 1], rk128[ 2]); P::AES_192_key_exp_2<0x02>(rk128[ 1], rk128[ 2], rk128[ 3], rk128[ 4]); P::AES_192_key_exp_1<0x04>(rk128[ 3], rk128[ 4], rk128[ 5]); P::AES_192_key_exp_2<0x08>(rk128[ 4], rk128[ 5], rk128[ 6], rk128[ 7]); P::AES_192_key_exp_1<0x10>(rk128[ 6], rk128[ 7], rk128[ 8]); P::AES_192_key_exp_2<0x20>(rk128[ 7], rk128[ 8], rk128[ 9], rk128[10]); P::AES_192_key_exp_1<0x40>(rk128[ 9], rk128[10], rk128[11]); P::AES_192_key_exp_3<0x80>(rk128[10], rk128[11], rk128[12]); return 0; } int AES192_set_decrypt_key(const unsigned char *userKey, AES_KEY_192 *key) { if (!userKey || !key) { return -1; } __m128i *rk128 = reinterpret_cast<__m128i *>(key->rd_key); ::memcpy(&(rk128[12]), userKey, 16); ::memcpy(&(rk128[11]), userKey + 16, 8); P::AES_192_key_exp_1<0x01>(rk128[12], rk128[11], rk128[10]); P::AES_192_key_exp_2<0x02>(rk128[11], rk128[10], rk128[ 9], rk128[ 8]); rk128[11] = _mm_aesimc_si128(rk128[11]); rk128[10] = _mm_aesimc_si128(rk128[10]); P::AES_192_key_exp_1<0x04>(rk128[ 9], rk128[ 8], rk128[ 7]); rk128[ 9] = _mm_aesimc_si128(rk128[ 9]); P::AES_192_key_exp_2<0x08>(rk128[ 8], rk128[ 7], rk128[ 6], rk128[ 5]); rk128[ 8] = _mm_aesimc_si128(rk128[ 8]); rk128[ 7] = _mm_aesimc_si128(rk128[ 7]); P::AES_192_key_exp_1<0x10>(rk128[ 6], rk128[ 5], rk128[ 4]); rk128[ 6] = _mm_aesimc_si128(rk128[ 6]); P::AES_192_key_exp_2<0x20>(rk128[ 5], rk128[ 4], rk128[ 3], rk128[ 2]); rk128[ 5] = _mm_aesimc_si128(rk128[ 5]); rk128[ 4] = _mm_aesimc_si128(rk128[ 4]); P::AES_192_key_exp_1<0x40>(rk128[ 3], rk128[ 2], rk128[ 1]); rk128[ 3] = _mm_aesimc_si128(rk128[ 3]); P::AES_192_key_exp_3<0x80>(rk128[ 2], rk128[ 1], rk128[ 0]); rk128[ 2] = _mm_aesimc_si128(rk128[ 2]); rk128[ 1] = _mm_aesimc_si128(rk128[ 1]); return 0; } int AES256_set_encrypt_key(const unsigned char *userKey, AES_KEY_256 *key) { if (!userKey || !key) { return -1; } __m128i *rk128 = reinterpret_cast<__m128i *>(key->rd_key); ::memcpy(rk128, userKey, 32); P::AES_256_key_exp_1<0x01>(rk128[ 0], rk128[ 1], rk128[ 2]); P::AES_256_key_exp_2 (rk128[ 1], rk128[ 2], rk128[ 3]); P::AES_256_key_exp_1<0x02>(rk128[ 2], rk128[ 3], rk128[ 4]); P::AES_256_key_exp_2 (rk128[ 3], rk128[ 4], rk128[ 5]); P::AES_256_key_exp_1<0x04>(rk128[ 4], rk128[ 5], rk128[ 6]); P::AES_256_key_exp_2 (rk128[ 5], rk128[ 6], rk128[ 7]); P::AES_256_key_exp_1<0x08>(rk128[ 6], rk128[ 7], rk128[ 8]); P::AES_256_key_exp_2 (rk128[ 7], rk128[ 8], rk128[ 9]); P::AES_256_key_exp_1<0x10>(rk128[ 8], rk128[ 9], rk128[10]); P::AES_256_key_exp_2 (rk128[ 9], rk128[10], rk128[11]); P::AES_256_key_exp_1<0x20>(rk128[10], rk128[11], rk128[12]); P::AES_256_key_exp_2 (rk128[11], rk128[12], rk128[13]); P::AES_256_key_exp_1<0x40>(rk128[12], rk128[13], rk128[14]); return 0; } int AES256_set_decrypt_key(const unsigned char *userKey, AES_KEY_256 *key) { if (!userKey || !key) { return -1; } __m128i *rk128 = reinterpret_cast<__m128i *>(key->rd_key); ::memcpy(&(rk128[14]), userKey, 16); ::memcpy(&(rk128[13]), userKey + 16, 16); P::AES_256_key_exp_1<0x01>(rk128[14], rk128[13], rk128[12]); P::AES_256_key_exp_2 (rk128[13], rk128[12], rk128[11]); rk128[13] = _mm_aesimc_si128(rk128[13]); P::AES_256_key_exp_1<0x02>(rk128[12], rk128[11], rk128[10]); rk128[12] = _mm_aesimc_si128(rk128[12]); P::AES_256_key_exp_2 (rk128[11], rk128[10], rk128[ 9]); rk128[11] = _mm_aesimc_si128(rk128[11]); P::AES_256_key_exp_1<0x04>(rk128[10], rk128[ 9], rk128[ 8]); rk128[10] = _mm_aesimc_si128(rk128[10]); P::AES_256_key_exp_2 (rk128[ 9], rk128[ 8], rk128[ 7]); rk128[ 9] = _mm_aesimc_si128(rk128[ 9]); P::AES_256_key_exp_1<0x08>(rk128[ 8], rk128[ 7], rk128[ 6]); rk128[ 8] = _mm_aesimc_si128(rk128[ 8]); P::AES_256_key_exp_2 (rk128[ 7], rk128[ 6], rk128[ 5]); rk128[ 7] = _mm_aesimc_si128(rk128[ 7]); P::AES_256_key_exp_1<0x10>(rk128[ 6], rk128[ 5], rk128[ 4]); rk128[ 6] = _mm_aesimc_si128(rk128[ 6]); P::AES_256_key_exp_2 (rk128[ 5], rk128[ 4], rk128[ 3]); rk128[ 5] = _mm_aesimc_si128(rk128[ 5]); P::AES_256_key_exp_1<0x20>(rk128[ 4], rk128[ 3], rk128[ 2]); rk128[ 4] = _mm_aesimc_si128(rk128[ 4]); P::AES_256_key_exp_2 (rk128[ 3], rk128[ 2], rk128[ 1]); rk128[ 3] = _mm_aesimc_si128(rk128[ 3]); P::AES_256_key_exp_1<0x40>(rk128[ 2], rk128[ 1], rk128[ 0]); rk128[ 2] = _mm_aesimc_si128(rk128[ 2]); rk128[ 1] = _mm_aesimc_si128(rk128[ 1]); return 0; } int AES_set_encrypt_key(const unsigned char *userKey, const int bits, AES_KEY *key) { if (bits == 128) { if (AES128_set_encrypt_key(userKey, reinterpret_cast<AES_KEY_128 *>(key)) == 0) { key->rounds = 10; return 0; } } else if (bits == 192) { if (AES192_set_encrypt_key(userKey, reinterpret_cast<AES_KEY_192 *>(key)) == 0) { key->rounds = 12; return 0; } } else if (bits == 256) { if (AES256_set_encrypt_key(userKey, reinterpret_cast<AES_KEY_256 *>(key)) == 0) { key->rounds = 14; return 0; } } return -2; } int AES_set_decrypt_key(const unsigned char *userKey, const int bits, AES_KEY *key) { if (bits == 128) { if (AES128_set_decrypt_key(userKey, reinterpret_cast<AES_KEY_128 *>(key)) == 0) { key->rounds = 10; return 0; } } else if (bits == 192) { if (AES192_set_decrypt_key(userKey, reinterpret_cast<AES_KEY_192 *>(key)) == 0) { key->rounds = 12; return 0; } } else if (bits == 256) { if (AES256_set_decrypt_key(userKey, reinterpret_cast<AES_KEY_256 *>(key)) == 0) { key->rounds = 14; return 0; } } return -2; } void AES128_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY_128 *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); //先做一次Addroundkey m = _mm_aesenc_si128(m, rk128[ 1]);//做9轮论函数加密 m = _mm_aesenc_si128(m, rk128[ 2]); m = _mm_aesenc_si128(m, rk128[ 3]); m = _mm_aesenc_si128(m, rk128[ 4]); m = _mm_aesenc_si128(m, rk128[ 5]); m = _mm_aesenc_si128(m, rk128[ 6]); m = _mm_aesenc_si128(m, rk128[ 7]); m = _mm_aesenc_si128(m, rk128[ 8]); m = _mm_aesenc_si128(m, rk128[ 9]); m = _mm_aesenclast_si128(m, rk128[10]);//最后一轮少了mixcolumns操作,另外写一个函数 _mm_storeu_si128((__m128i *) out, m); } void AES192_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY_192 *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); m = _mm_aesenc_si128(m, rk128[ 1]); m = _mm_aesenc_si128(m, rk128[ 2]); m = _mm_aesenc_si128(m, rk128[ 3]); m = _mm_aesenc_si128(m, rk128[ 4]); m = _mm_aesenc_si128(m, rk128[ 5]); m = _mm_aesenc_si128(m, rk128[ 6]); m = _mm_aesenc_si128(m, rk128[ 7]); m = _mm_aesenc_si128(m, rk128[ 8]); m = _mm_aesenc_si128(m, rk128[ 9]); m = _mm_aesenc_si128(m, rk128[10]); m = _mm_aesenc_si128(m, rk128[11]); m = _mm_aesenclast_si128(m, rk128[12]); _mm_storeu_si128((__m128i *) out, m); } void AES256_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY_256 *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); m = _mm_aesenc_si128(m, rk128[ 1]); m = _mm_aesenc_si128(m, rk128[ 2]); m = _mm_aesenc_si128(m, rk128[ 3]); m = _mm_aesenc_si128(m, rk128[ 4]); m = _mm_aesenc_si128(m, rk128[ 5]); m = _mm_aesenc_si128(m, rk128[ 6]); m = _mm_aesenc_si128(m, rk128[ 7]); m = _mm_aesenc_si128(m, rk128[ 8]); m = _mm_aesenc_si128(m, rk128[ 9]); m = _mm_aesenc_si128(m, rk128[10]); m = _mm_aesenc_si128(m, rk128[11]); m = _mm_aesenc_si128(m, rk128[12]); m = _mm_aesenc_si128(m, rk128[13]); m = _mm_aesenclast_si128(m, rk128[14]); _mm_storeu_si128((__m128i *) out, m); } void AES_encrypt(const unsigned char *in, unsigned char *out, const AES_KEY *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); m = _mm_aesenc_si128(m, rk128[ 1]); m = _mm_aesenc_si128(m, rk128[ 2]); m = _mm_aesenc_si128(m, rk128[ 3]); m = _mm_aesenc_si128(m, rk128[ 4]); m = _mm_aesenc_si128(m, rk128[ 5]); m = _mm_aesenc_si128(m, rk128[ 6]); m = _mm_aesenc_si128(m, rk128[ 7]); m = _mm_aesenc_si128(m, rk128[ 8]); m = _mm_aesenc_si128(m, rk128[ 9]); if (key->rounds == 10) { m = _mm_aesenclast_si128(m, rk128[10]); } else if (key->rounds == 12) { m = _mm_aesenc_si128(m, rk128[10]); m = _mm_aesenc_si128(m, rk128[11]); m = _mm_aesenclast_si128(m, rk128[12]); } else { m = _mm_aesenc_si128(m, rk128[10]); m = _mm_aesenc_si128(m, rk128[11]); m = _mm_aesenc_si128(m, rk128[12]); m = _mm_aesenc_si128(m, rk128[13]); m = _mm_aesenclast_si128(m, rk128[14]); } _mm_storeu_si128((__m128i *) out, m); } void AES128_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY_128 *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); m = _mm_aesdec_si128(m, rk128[ 1]); m = _mm_aesdec_si128(m, rk128[ 2]); m = _mm_aesdec_si128(m, rk128[ 3]); m = _mm_aesdec_si128(m, rk128[ 4]); m = _mm_aesdec_si128(m, rk128[ 5]); m = _mm_aesdec_si128(m, rk128[ 6]); m = _mm_aesdec_si128(m, rk128[ 7]); m = _mm_aesdec_si128(m, rk128[ 8]); m = _mm_aesdec_si128(m, rk128[ 9]); m = _mm_aesdeclast_si128(m, rk128[10]); _mm_storeu_si128((__m128i *) out, m); } void AES192_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY_192 *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); m = _mm_aesdec_si128(m, rk128[ 1]); m = _mm_aesdec_si128(m, rk128[ 2]); m = _mm_aesdec_si128(m, rk128[ 3]); m = _mm_aesdec_si128(m, rk128[ 4]); m = _mm_aesdec_si128(m, rk128[ 5]); m = _mm_aesdec_si128(m, rk128[ 6]); m = _mm_aesdec_si128(m, rk128[ 7]); m = _mm_aesdec_si128(m, rk128[ 8]); m = _mm_aesdec_si128(m, rk128[ 9]); m = _mm_aesdec_si128(m, rk128[10]); m = _mm_aesdec_si128(m, rk128[11]); m = _mm_aesdeclast_si128(m, rk128[12]); _mm_storeu_si128((__m128i *) out, m); } void AES256_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY_256 *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); m = _mm_aesdec_si128(m, rk128[ 1]); m = _mm_aesdec_si128(m, rk128[ 2]); m = _mm_aesdec_si128(m, rk128[ 3]); m = _mm_aesdec_si128(m, rk128[ 4]); m = _mm_aesdec_si128(m, rk128[ 5]); m = _mm_aesdec_si128(m, rk128[ 6]); m = _mm_aesdec_si128(m, rk128[ 7]); m = _mm_aesdec_si128(m, rk128[ 8]); m = _mm_aesdec_si128(m, rk128[ 9]); m = _mm_aesdec_si128(m, rk128[10]); m = _mm_aesdec_si128(m, rk128[11]); m = _mm_aesdec_si128(m, rk128[12]); m = _mm_aesdec_si128(m, rk128[13]); m = _mm_aesdeclast_si128(m, rk128[14]); _mm_storeu_si128((__m128i *) out, m); } void AES_decrypt(const unsigned char *in, unsigned char *out, const AES_KEY *key) { __m128i m = _mm_loadu_si128((__m128i *) in); const __m128i *rk128 = reinterpret_cast<const __m128i *>(key->rd_key); m = _mm_xor_si128(m, rk128[ 0]); m = _mm_aesdec_si128(m, rk128[ 1]); m = _mm_aesdec_si128(m, rk128[ 2]); m = _mm_aesdec_si128(m, rk128[ 3]); m = _mm_aesdec_si128(m, rk128[ 4]); m = _mm_aesdec_si128(m, rk128[ 5]); m = _mm_aesdec_si128(m, rk128[ 6]); m = _mm_aesdec_si128(m, rk128[ 7]); m = _mm_aesdec_si128(m, rk128[ 8]); m = _mm_aesdec_si128(m, rk128[ 9]); if (key->rounds == 10) { m = _mm_aesdeclast_si128(m, rk128[10]); } else if (key->rounds == 12) { m = _mm_aesdec_si128(m, rk128[10]); m = _mm_aesdec_si128(m, rk128[11]); m = _mm_aesdeclast_si128(m, rk128[12]); } else { m = _mm_aesdec_si128(m, rk128[10]); m = _mm_aesdec_si128(m, rk128[11]); m = _mm_aesdec_si128(m, rk128[12]); m = _mm_aesdec_si128(m, rk128[13]); m = _mm_aesdeclast_si128(m, rk128[14]); } _mm_storeu_si128((__m128i *) out, m); } } #if defined(__clang__) #pragma clang attribute pop #endif

/* * Copyright 2021 Florent Bondoux * * Licensed under the Apache License, Version 2.0 (the "License"); * you may not use this file except in compliance with the License. * You may obtain a copy of the License at * * http://www.apache.org/licenses/LICENSE-2.0 * * Unless required by applicable law or agreed to in writing, software * distributed under the License is distributed on an "AS IS" BASIS, * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. * See the License for the specific language governing permissions and * limitations under the License. */ #include "aesni.h" #include <cstring> #include <cstdio> #include <chrono> #include <openssl/aes.h> #include <openssl/rand.h> #include <openssl/evp.h> //Openssl 中实现了各种对称算法、摘要算法以及签名/验签算法。EVP 函数将这些具体的算法进行了封装。 //EVP系列函数主要封装了加密、摘要、编码三大类型的算法 template<const int bits, typename KEY, int set_encrypt_key(const unsigned char *, KEY *), int set_decrypt_key(const unsigned char *, KEY *), void encrypt(const unsigned char *, unsigned char *, const KEY *), void decrypt(const unsigned char *, unsigned char *, const KEY *)> bool rand_test() { uint8_t key[32]; uint8_t in[16]; uint8_t out_ref[16], out_tst[16]; RAND_bytes(key, 32); ::AES_KEY ref_enc_key; ::AES_set_encrypt_key(key, bits, &ref_enc_key); ::AES_encrypt(in, out_ref, &ref_enc_key); KEY enc_key, dec_key; set_encrypt_key(key, &enc_key); set_decrypt_key(key, &dec_key); encrypt(in, out_tst, &enc_key); if (::memcmp(out_ref, out_tst, 16) != 0) { printf("error: AESNI::AES%d_encrypt\n", bits); return false; } decrypt(out_tst, out_tst, &dec_key); if (::memcmp(in, out_tst, 16) != 0) { printf("error: AESNI::AES%d_decrypt\n", bits); return false; } AESNI::AES_KEY enc_key_gen, dec_key_gen; AESNI::AES_set_encrypt_key(key, bits, &enc_key_gen); AESNI::AES_set_decrypt_key(key, bits, &dec_key_gen); AESNI::AES_encrypt(in, out_tst, &enc_key_gen); if (::memcmp(out_ref, out_tst, 16) != 0) { printf("error: AESNI::AES_encrypt (%d)\n", bits); return false; } AESNI::AES_decrypt(out_tst, out_tst, &dec_key_gen); if (::memcmp(in, out_tst, 16) != 0) { printf("error: AESNI::AES_encrypt (%d)\n", bits); return false; } return true; } template<const int bits_, typename Key_, int set_encrypt_key_(const unsigned char *, Key_ *), int set_decrypt_key_(const unsigned char *, Key_ *), void encrypt_(const unsigned char *, unsigned char *, const Key_ *), void decrypt_(const unsigned char *, unsigned char *, const Key_ *)> struct AESNIDescriptor { typedef Key_ Key; static inline int bits() { return bits_; } static inline int set_encrypt_key(const unsigned char *userKey, Key *key) { return set_encrypt_key_(userKey, key); } static inline int set_decrypt_key(const unsigned char *userKey, Key *key) { return set_decrypt_key_(userKey, key); } static inline void encrypt(const unsigned char *in, unsigned char *out, const Key *key) { encrypt_(in, out, key); } static inline void decrypt(const unsigned char *in, unsigned char *out, const Key *key) { decrypt_(in, out, key); } }; template<const int bits_> struct OpenSSLDesc { typedef ::AES_KEY Key; static inline int bits() { return bits_; } static inline int set_encrypt_key(const unsigned char *userKey, Key *key) { return ::AES_set_encrypt_key(userKey, bits_, key); } static inline int set_decrypt_key(const unsigned char *userKey, Key *key) { return ::AES_set_decrypt_key(userKey, bits_, key); } static inline void encrypt(const unsigned char *in, unsigned char *out, const Key *key) { ::AES_encrypt(in, out, key); } static inline void decrypt(const unsigned char *in, unsigned char *out, const Key *key) { ::AES_decrypt(in, out, key); } }; typedef AESNIDescriptor<128, AESNI::AES_KEY_128, AESNI::AES128_set_encrypt_key, AESNI::AES128_set_decrypt_key, AESNI::AES128_encrypt, AESNI::AES128_decrypt> AESNIDesc128; typedef AESNIDescriptor<192, AESNI::AES_KEY_192, AESNI::AES192_set_encrypt_key, AESNI::AES192_set_decrypt_key, AESNI::AES192_encrypt, AESNI::AES192_decrypt> AESNIDesc192; typedef AESNIDescriptor<256, AESNI::AES_KEY_256, AESNI::AES256_set_encrypt_key, AESNI::AES256_set_decrypt_key, AESNI::AES256_encrypt, AESNI::AES256_decrypt> AESNIDesc256; typedef OpenSSLDesc<128> OpenSSLDesc128; typedef OpenSSLDesc<192> OpenSSLDesc192; typedef OpenSSLDesc<256> OpenSSLDesc256; template<typename Desc, const unsigned int n_keys = 256, const unsigned long n_runs = 100000> class SpeedTest { unsigned char m_userKeys[n_keys * 32]; typename Desc::Key m_keys[n_keys]; public: SpeedTest() : m_userKeys(), m_keys() { RAND_bytes(m_userKeys, sizeof(m_userKeys)); } void run_set_encrypt_key() { auto begin = std::chrono::high_resolution_clock::now(); for (int r = 0; r < n_runs; r++) { for (int n = 0; n < n_keys; n++) { Desc::set_encrypt_key(m_userKeys + n * 32, m_keys + n); } } auto end = std::chrono::high_resolution_clock::now(); std::chrono::duration<double, std::milli> d = end - begin; printf(" %0.3f key setup / ms\n", (n_keys * n_runs) / d.count()); } void run_set_decrypt_key() { auto begin = std::chrono::high_resolution_clock::now(); for (int r = 0; r < n_runs; r++) { for (int n = 0; n < n_keys; n++) { Desc::set_decrypt_key(m_userKeys + n * 32, m_keys + n); } } auto end = std::chrono::high_resolution_clock::now(); std::chrono::duration<double, std::milli> d = end - begin; printf(" %0.3f key setup / ms\n", (n_keys * n_runs) / d.count()); } }; template<const int bits, const unsigned int n_keys = 256, const unsigned long n_runs = 100000> class SpeedTestEVP { unsigned char m_userKeys[n_keys * 32]; EVP_CIPHER_CTX *m_ctx[n_keys]; const EVP_CIPHER *m_cipher; public: SpeedTestEVP() : m_userKeys(), m_ctx(), m_cipher(NULL) { RAND_bytes(m_userKeys, sizeof(m_userKeys)); for (int i = 0; i < n_keys; i++) { m_ctx[i] = EVP_CIPHER_CTX_new(); } if (bits == 128) { m_cipher = EVP_aes_128_ecb(); } else if (bits == 192) { m_cipher = EVP_aes_192_ecb(); } else { m_cipher = EVP_aes_256_ecb(); } } ~SpeedTestEVP() { for (int i = 0; i < n_keys; i++) { EVP_CIPHER_CTX_free(m_ctx[i]); } } void run_set_encrypt_key() { auto begin = std::chrono::high_resolution_clock::now(); for (int r = 0; r < n_runs; r++) { for (int n = 0; n < n_keys; n++) { EVP_EncryptInit_ex(m_ctx[n], m_cipher, NULL, m_userKeys + n * 32, NULL); } } auto end = std::chrono::high_resolution_clock::now(); std::chrono::duration<double, std::milli> d = end - begin; printf(" %0.3f key setup / ms\n", (n_keys * n_runs) / d.count()); } void run_set_decrypt_key() { auto begin = std::chrono::high_resolution_clock::now(); for (int r = 0; r < n_runs; r++) { for (int n = 0; n < n_keys; n++) { EVP_DecryptInit_ex(m_ctx[n], m_cipher, NULL, m_userKeys + n * 32, NULL); } } auto end = std::chrono::high_resolution_clock::now(); std::chrono::duration<double, std::milli> d = end - begin; printf(" %0.3f key setup / ms\n", (n_keys * n_runs) / d.count()); } }; int main() { const int n_tests = 200000; puts("AES-128..."); for (int i = 0; i < n_tests; i++) { if (!rand_test<128, AESNI::AES_KEY_128, AESNI::AES128_set_encrypt_key, AESNI::AES128_set_decrypt_key, AESNI::AES128_encrypt, AESNI::AES128_decrypt>()) { break; } } puts("AES-192..."); for (int i = 0; i < n_tests; i++) { if (!rand_test<192, AESNI::AES_KEY_192, AESNI::AES192_set_encrypt_key, AESNI::AES192_set_decrypt_key, AESNI::AES192_encrypt, AESNI::AES192_decrypt>()) { break; } } puts("AES-256..."); for (int i = 0; i < n_tests; i++) { if (!rand_test<256, AESNI::AES_KEY_256, AESNI::AES256_set_encrypt_key, AESNI::AES256_set_decrypt_key, AESNI::AES256_encrypt, AESNI::AES256_decrypt>()) { break; } } puts("AESNI set_encrypt_key 128"); SpeedTest<AESNIDesc128>().run_set_encrypt_key(); puts("AESNI set_decrypt_key 128"); SpeedTest<AESNIDesc128>().run_set_decrypt_key(); puts("AESNI set_encrypt_key 192"); SpeedTest<AESNIDesc192>().run_set_encrypt_key(); puts("AESNI set_decrypt_key 192"); SpeedTest<AESNIDesc192>().run_set_decrypt_key(); puts("AESNI set_encrypt_key 256"); SpeedTest<AESNIDesc256>().run_set_encrypt_key(); puts("AESNI set_decrypt_key 256"); SpeedTest<AESNIDesc256>().run_set_decrypt_key(); puts("OpenSSL set_encrypt_key 128"); SpeedTest<OpenSSLDesc128>().run_set_encrypt_key(); puts("OpenSSL set_decrypt_key 128"); SpeedTest<OpenSSLDesc128>().run_set_decrypt_key(); puts("OpenSSL set_encrypt_key 192"); SpeedTest<OpenSSLDesc192>().run_set_encrypt_key(); puts("OpenSSL set_decrypt_key 192"); SpeedTest<OpenSSLDesc192>().run_set_decrypt_key(); puts("OpenSSL set_encrypt_key 256"); SpeedTest<OpenSSLDesc256>().run_set_encrypt_key(); puts("OpenSSL set_decrypt_key 256"); SpeedTest<OpenSSLDesc256>().run_set_decrypt_key(); puts("OpenSSL EVP_EncryptInit_ex 128"); SpeedTestEVP<128>().run_set_encrypt_key(); puts("OpenSSL EVP_DecryptInit_ex 128"); SpeedTestEVP<128>().run_set_decrypt_key(); puts("OpenSSL EVP_EncryptInit_ex 192"); SpeedTestEVP<192>().run_set_encrypt_key(); puts("OpenSSL EVP_DecryptInit_ex 192"); SpeedTestEVP<192>().run_set_decrypt_key(); puts("OpenSSL EVP_EncryptInit_ex 256"); SpeedTestEVP<256>().run_set_encrypt_key(); puts("OpenSSL EVP_DecryptInit_ex 256"); SpeedTestEVP<256>().run_set_decrypt_key(); return 0; }
错误解决
1、ml64不是内部命令或者外部命令:我加装了NASM和把openssl目录移到C下面的子目录就好了???啊
2、权限不够:管理员身份打开vs2016 x64 自带命令行工具就好了。
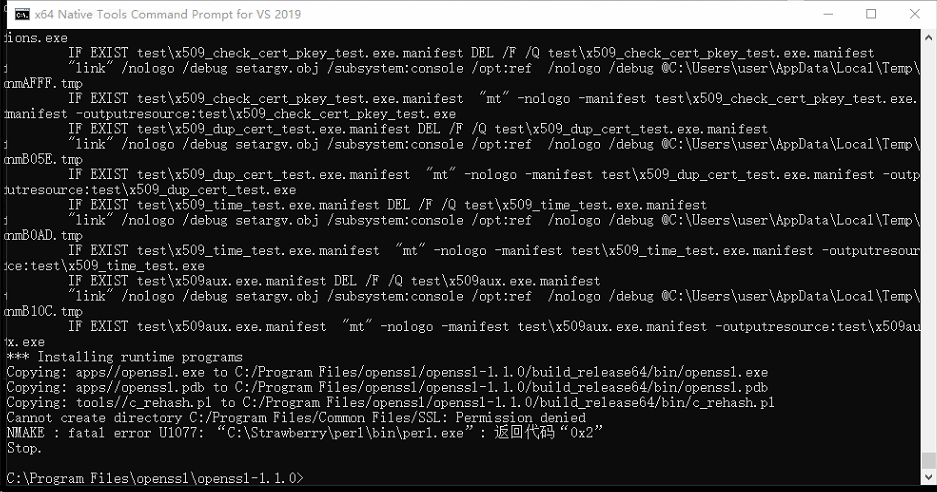
参考
(22条消息) OpenSSL 在windows系统下的编译全解_danscort2000的专栏-CSDN博客_openssl windows 编译
