查壳
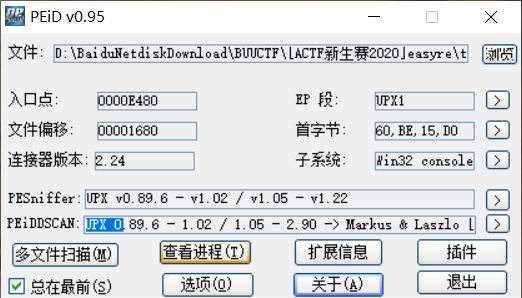
UPX壳
工具脱壳
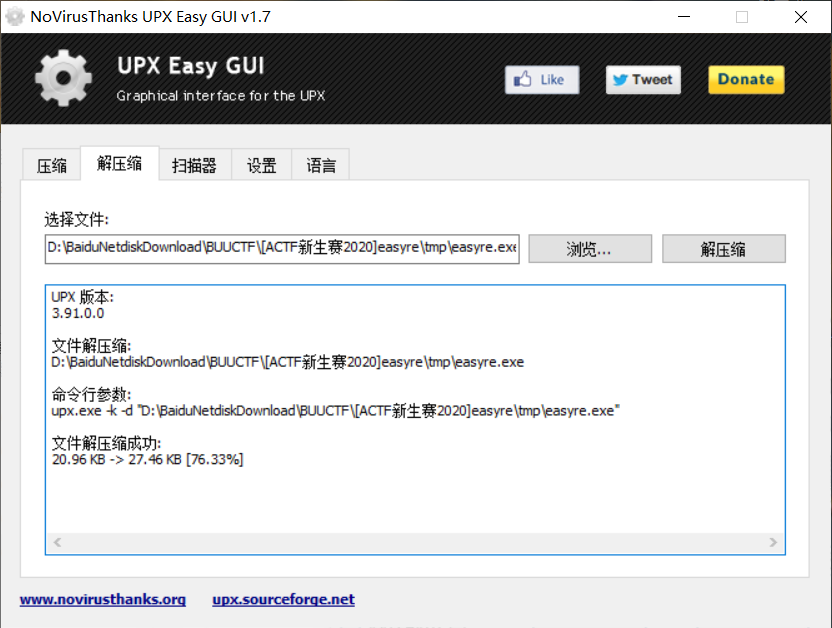
脱完壳扔IDA里分析 这一题很明显
分析
int __cdecl main(int argc, const char **argv, const char **envp)
{
char v4; // [esp+12h] [ebp-2Eh]
char v5; // [esp+13h] [ebp-2Dh]
char v6; // [esp+14h] [ebp-2Ch]
char v7; // [esp+15h] [ebp-2Bh]
char v8; // [esp+16h] [ebp-2Ah]
char v9; // [esp+17h] [ebp-29h]
char v10; // [esp+18h] [ebp-28h]
char v11; // [esp+19h] [ebp-27h]
char v12; // [esp+1Ah] [ebp-26h]
char v13; // [esp+1Bh] [ebp-25h]
char v14; // [esp+1Ch] [ebp-24h]
char v15; // [esp+1Dh] [ebp-23h]
int v16; // [esp+1Eh] [ebp-22h]
int v17; // [esp+22h] [ebp-1Eh]
int v18; // [esp+26h] [ebp-1Ah]
__int16 v19; // [esp+2Ah] [ebp-16h]
char v20; // [esp+2Ch] [ebp-14h]
char v21; // [esp+2Dh] [ebp-13h]
char v22; // [esp+2Eh] [ebp-12h]
int v23; // [esp+2Fh] [ebp-11h]
int v24; // [esp+33h] [ebp-Dh]
int v25; // [esp+37h] [ebp-9h]
char v26; // [esp+3Bh] [ebp-5h]
int i; // [esp+3Ch] [ebp-4h]
__main();
v4 = 42;
v5 = 70;
v6 = 39;
v7 = 34;
v8 = 78;
v9 = 44;
v10 = 34;
v11 = 40;
v12 = 73;
v13 = 63;
v14 = 43;
v15 = 64;
printf("Please input:");
scanf("%s", &v19);
if ( (_BYTE)v19 != 'A' || HIBYTE(v19) != 'C' || v20 != 'T' || v21 != 'F' || v22 != '{' || v26 != '}' )
return 0;
v16 = v23;
v17 = v24;
v18 = v25;
for ( i = 0; i <= 11; ++i )
{
if ( *(&v4 + i) != _data_start__[*((char *)&v16 + i) - 1] )
return 0;
}
printf("You are correct!");
return 0;
}
v4[i]!=data_start[flag[i]-1]
v4与data_start数组中的字符串比较,data_start数组中的下表进行减法得到flag的ascii值
解题脚本
v4 = [42,70,39,34,78,44,34,40,73,63,43,64]
model = r"}|{zyxwvutsrqponmlkjihgfedcba`_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)(" + chr(0x27) + r'&%$# !"'
pos = []
for i in v4:
pos.append(model.find(chr(i))+1)#find()方法检测字符串中是否包含子字符串 str
s = [chr(x + 1) for x in pos]
flag = ''.join(s)
print ('ACTF{'+flag+'}')
脚本参考:https://www.cnblogs.com/Mayfly-nymph/p/12664201.html#Wbh6Hw7p
flag{U9X_1S_W6@T?}