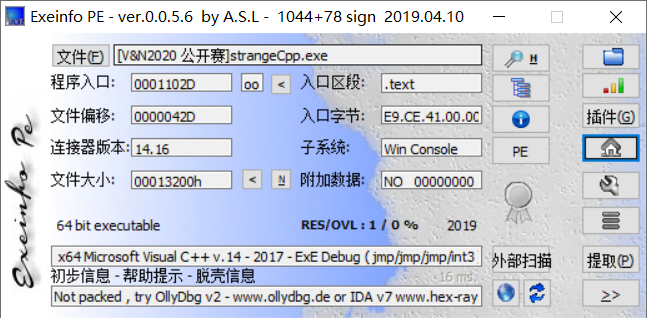
查壳
运行程序
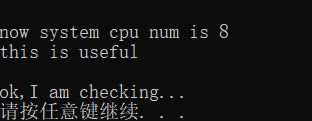
它提示说cpu num是8 这个信息是有用的
搜索字符串
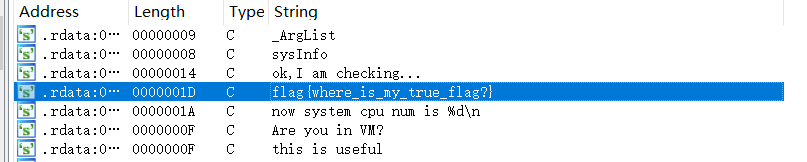
也就这一块了。
flag{where_is_my_true_flag?}肯定是假的了。
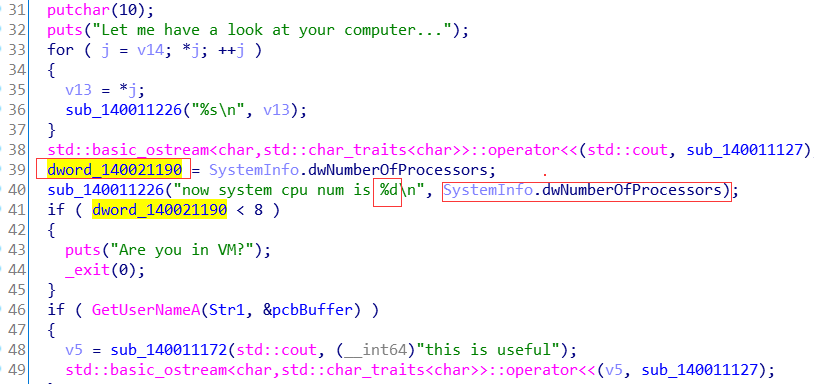
这一块就是提示cpu数值的。我们交叉引用看看。
然后我们就能找到解题的关键函数了。
__int64 sub_140013580()
{
__int64 *v0; // rdi
signed __int64 i; // rcx
__int64 result; // rax
__int64 v3; // [rsp+0h] [rbp-20h]
int v4; // [rsp+24h] [rbp+4h]
int j; // [rsp+44h] [rbp+24h]
__int64 v6; // [rsp+128h] [rbp+108h]
v0 = &v3;
for ( i = 82i64; i; --i )
{
*(_DWORD *)v0 = -858993460;
v0 = (__int64 *)((char *)v0 + 4);
}
v6 = -2i64;
sub_1400110AA((__int64)&unk_140027033);
result = sub_140011384((unsigned int)dword_140021190);
v4 = result;
if ( (_DWORD)result == 607052314 && dword_140021190 <= 14549743 )
{
for ( j = 0; j < 17; ++j )
{
putchar((unsigned __int8)(dword_140021190 ^ *((_BYTE *)&qword_140021008 + j)));
result = (unsigned int)(j + 1);
}
}
return result;
}
putchar是输出函数,我们推测可能是flag了这里。然后16个字符串也比较符合常规。那我们首先要知道dword_140021190的值,进入sub_140011384
signed __int64 __fastcall sub_140013890(int a1)
{
__int64 *v1; // rdi
signed __int64 i; // rcx
signed __int64 result; // rax
__int64 v4; // [rsp+0h] [rbp-20h]
int v5; // [rsp+24h] [rbp+4h]
int v6; // [rsp+44h] [rbp+24h]
unsigned int v7; // [rsp+64h] [rbp+44h]
int v8; // [rsp+160h] [rbp+140h]
v8 = a1;
v1 = &v4;
for ( i = 82i64; i; --i )
{
*(_DWORD *)v1 = -858993460;
v1 = (__int64 *)((char *)v1 + 4);
}
sub_1400110AA((__int64)&unk_140027033);
v5 = v8 >> 12;
v6 = v8 << 8;
v7 = (v8 << 8) ^ (v8 >> 12);
v7 *= 291;
if ( v7 )
result = v7;
else
result = 987i64;
return result;
}
结合上一个函数我们知道result == 607052314且dword_140021190 <= 14549743
经过sub_140011384操作过后的值等于607052314
我们算这个v7=607052314 我们要通过v7来推v8
然后我们写脚本把v8解出来 dword_140021190在sub_140011384里是a1也就是v8
v8解出来之后拿到外面跟qword_140021008数组做异或
注意小端
解题脚本
#include<stdio.h>
int main()
{
int m,i;
char flag[17];
char str[17] = { 0x26,0x2C,0x21,0x27,0x3B,0x0D,0x04,0x75,0x68,0x34,0x28,0x25,0x0E,0x35,0x2D,0x69,0x3D };
for (i = 0; i < 14549743; i++) {
m = (i >> 12) ^ (i << 8);
if (m * 291 == 607052314) {
printf_s("%d
",i);
break;
}
}
for (int j = 0; j < 17; j++)
putchar(str[j]^i);
return 0;
}
结果:
123456
flag{MD5(theNum)}
md5
import hashlib
print("
flag{"+hashlib.md5('123456'.encode(encoding='utf-8')).hexdigest()+'}')
flag{e10adc3949ba59abbe56e057f20f883e}