测试文件:https://www.lanzous.com/ib515vi
脱壳
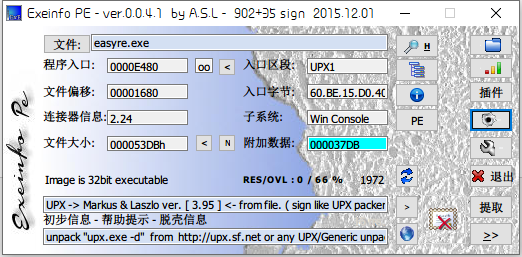
获取到信息
- 32位文件
- upx加密
代码分析
1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 char v4; // [esp+12h] [ebp-2Eh] 4 char v5; // [esp+13h] [ebp-2Dh] 5 char v6; // [esp+14h] [ebp-2Ch] 6 char v7; // [esp+15h] [ebp-2Bh] 7 char v8; // [esp+16h] [ebp-2Ah] 8 char v9; // [esp+17h] [ebp-29h] 9 char v10; // [esp+18h] [ebp-28h] 10 char v11; // [esp+19h] [ebp-27h] 11 char v12; // [esp+1Ah] [ebp-26h] 12 char v13; // [esp+1Bh] [ebp-25h] 13 char v14; // [esp+1Ch] [ebp-24h] 14 char v15; // [esp+1Dh] [ebp-23h] 15 int v16; // [esp+1Eh] [ebp-22h] 16 int v17; // [esp+22h] [ebp-1Eh] 17 int v18; // [esp+26h] [ebp-1Ah] 18 __int16 v19; // [esp+2Ah] [ebp-16h] 19 char v20; // [esp+2Ch] [ebp-14h] 20 char v21; // [esp+2Dh] [ebp-13h] 21 char v22; // [esp+2Eh] [ebp-12h] 22 int v23; // [esp+2Fh] [ebp-11h] 23 int v24; // [esp+33h] [ebp-Dh] 24 int v25; // [esp+37h] [ebp-9h] 25 char v26; // [esp+3Bh] [ebp-5h] 26 int i; // [esp+3Ch] [ebp-4h] 27 28 __main(); 29 v4 = 42; 30 v5 = 70; 31 v6 = 39; 32 v7 = 34; 33 v8 = 78; 34 v9 = 44; 35 v10 = 34; 36 v11 = 40; 37 v12 = 73; 38 v13 = 63; 39 v14 = 43; 40 v15 = 64; 41 printf("Please input:"); 42 scanf("%s", &v19); 43 if ( (_BYTE)v19 != 65 || HIBYTE(v19) != 67 || v20 != 84 || v21 != 70 || v22 != 123 || v26 != 125 ) 44 return 0; 45 v16 = v23; 46 v17 = v24; 47 v18 = v25; 48 for ( i = 0; i <= 11; ++i ) 49 { 50 if ( *(&v4 + i) != _data_start__[*((char *)&v16 + i) - 1] ) 51 return 0; 52 } 53 printf("You are correct!"); 54 return 0; 55 }
着眼观察for循环就行,从for循环了解到flag长度应该是11,将flag的ASCII值作为下标取值,与v4数组比较。很简单,只需要利用v4数组在_data_start__中找位置,就是我们flag的值
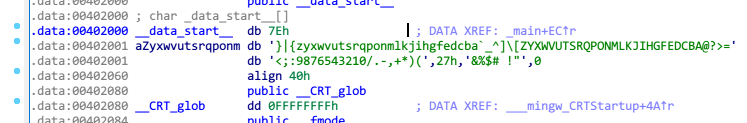
脚本
# -*- coding:utf-8 -*- v4 = [42,70,39,34,78,44,34,40,73,63,43,64] model = r"}|{zyxwvutsrqponmlkjihgfedcba`_^][ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/.-,+*)(" + chr(0x27) + r'&%$# !"' pos = [] for i in v4: pos.append(model.find(chr(i))+1) s = [chr(x + 1) for x in pos] flag = ''.join(s) print ('flag{'+flag+'}')
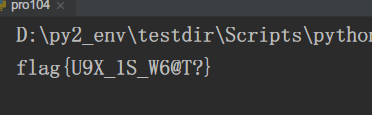
get flag!
flag{U9X_1S_W6@T?}