测试文件:https://www.lanzous.com/ib3elba
脱壳
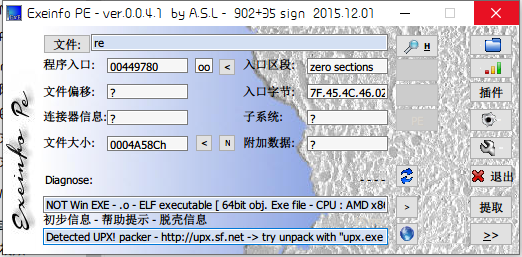
获取信息
- 64位文件
- upx加壳
代码分析
1 __int64 sub_400E28() 2 { 3 const char *v0; // rdi 4 __int64 result; // rax 5 __int64 v2; // rdx 6 unsigned __int64 v3; // rt1 7 __int64 v4; // [rsp+0h] [rbp-30h] 8 __int64 v5; // [rsp+8h] [rbp-28h] 9 __int64 v6; // [rsp+10h] [rbp-20h] 10 __int64 v7; // [rsp+18h] [rbp-18h] 11 unsigned __int64 v8; // [rsp+28h] [rbp-8h] 12 13 v8 = __readfsqword(0x28u); 14 v4 = 0LL; 15 v5 = 0LL; 16 v6 = 0LL; 17 v7 = 0LL; 18 sub_40F950((__int64)"input your flag:", 0LL, 0LL, 0LL, 0LL); 19 sub_40FA80((__int64)"%s", &v4); 20 if ( (unsigned int)sub_4009AE(&v4, &v4) ) 21 { 22 v0 = "Correct!"; 23 sub_410350("Correct!"); 24 } 25 else 26 { 27 v0 = "Wrong!"; 28 sub_410350("Wrong!"); 29 } 30 result = 0LL; 31 v3 = __readfsqword(0x28u); 32 v2 = v3 ^ v8; 33 if ( v3 != v8 ) 34 sub_443550(v0, &v4, v2); 35 return result; 36 }
打开关键函数sub_4009AE
_BOOL8 __fastcall sub_4009AE(char *a1) { if ( 1629056 * *a1 != 166163712 ) return 0LL; if ( 6771600 * a1[1] != 731332800 ) return 0LL; if ( 3682944 * a1[2] != 357245568 ) return 0LL; if ( 10431000 * a1[3] != 1074393000 ) return 0LL; if ( 3977328 * a1[4] != 489211344 ) return 0LL; if ( 5138336 * a1[5] != 518971936 ) return 0LL; if ( 7532250 * a1[7] != 406741500 ) return 0LL; if ( 5551632 * a1[8] != 294236496 ) return 0LL; if ( 3409728 * a1[9] != 177305856 ) return 0LL; if ( 13013670 * a1[10] != 650683500 ) return 0LL; if ( 6088797 * a1[11] != 298351053 ) return 0LL; if ( 7884663 * a1[12] != 386348487 ) return 0LL; if ( 8944053 * a1[13] != 438258597 ) return 0LL; if ( 5198490 * a1[14] != 249527520 ) return 0LL; if ( 4544518 * a1[15] != 445362764 ) return 0LL; if ( 3645600 * a1[17] != 174988800 ) return 0LL; if ( 10115280 * a1[16] != 981182160 ) return 0LL; if ( 9667504 * a1[18] != 493042704 ) return 0LL; if ( 5364450 * a1[19] != 257493600 ) return 0LL; if ( 13464540 * a1[20] != 767478780 ) return 0LL; if ( 5488432 * a1[21] != 312840624 ) return 0LL; if ( 14479500 * a1[22] != 1404511500 ) return 0LL; if ( 6451830 * a1[23] != 316139670 ) return 0LL; if ( 6252576 * a1[24] != 619005024 ) return 0LL; if ( 7763364 * a1[25] != 372641472 ) return 0LL; if ( 7327320 * a1[26] != 373693320 ) return 0LL; if ( 8741520 * a1[27] != 498266640 ) return 0LL; if ( 8871876 * a1[28] != 452465676 ) return 0LL; if ( 4086720 * a1[29] != 208422720 ) return 0LL; if ( 9374400 * a1[30] == 515592000 ) return 5759124 * a1[31] == 719890500; return 0LL; }
a1就是我们输入的v4,反向除就行
脚本
# -*- coding:utf-8 -*- a1 = chr(166163712 // 1629056) a2 = chr(731332800 // 6771600) a3 = chr(357245568 // 3682944) a4 = chr(1074393000 // 10431000) a5 = chr(489211344 // 3977328) a6 = chr(518971936 // 5138336) a8 = chr(406741500 // 7532250) a9 = chr(294236496 // 5551632) a10 = chr(177305856 // 3409728) a11 = chr(650683500 // 13013670) a12 = chr(298351053 // 6088797) a13 = chr(386348487 // 7884663) a14 = chr(438258597 // 8944053) a15 = chr(249527520 // 5198490) a16 = chr(445362764 // 4544518) a17 = chr(981182160 // 10115280) a18 = chr(174988800 // 3645600) a19 = chr(493042704 // 9667504) a20 = chr(257493600 // 5364450) a21 = chr(767478780 // 13464540) a22 = chr(312840624 // 5488432) a23 = chr(1404511500 // 14479500) a24 = chr(316139670 // 6451830) a25 = chr(619005024 // 6252576) a26 = chr(372641472 // 7763364) a27 = chr(373693320 // 7327320) a28 = chr(498266640 // 8741520) a29 = chr(452465676 // 8871876) a30 = chr(208422720 // 4086720) a31 = chr(515592000 // 9374400) a32 = chr(719890500 // 5759124) print (a1,a2,a3,a4,a5,a6,a8,a9,a10,a11,a12,a13,a14,a15,a16,a17,a18,a19,a20,a21,a22,a23,a24,a25,a26,a27,a28,a29,a30,a31,a32)
这上面缺了一位,只能爆破得到a7=1
get flag!
flag{e165421110ba03099a1c039337}