菜鸡想要走出菜狗设计的迷宫
(这个也不会了......
下载得到64位ELF文件
进入ida
__int64 __fastcall main(__int64 a1, char **a2, char **a3) { const char *v3; // rsi signed __int64 v4; // rbx signed int v5; // eax char v6; // bp char v7; // al const char *v8; // rdi __int64 v10; // [rsp+0h] [rbp-28h] v10 = 0LL; puts("Input flag:"); scanf("%s", &s1, 0LL); if ( strlen(&s1) != 24 || (v3 = "nctf{", strncmp(&s1, "nctf{", 5uLL)) || *(&byte_6010BF + 24) != 125 ) { LABEL_22: puts("Wrong flag!"); exit(-1); } v4 = 5LL; if ( strlen(&s1) - 1 > 5 ) { while ( 1 ) { v5 = *(&s1 + v4); v6 = 0; if ( v5 > 'N' ) { v5 = (unsigned __int8)v5; if ( (unsigned __int8)v5 == 'O' ) { v7 = sub_400650((char *)&v10 + 4, v3); goto LABEL_14; } if ( v5 == 'o' ) { v7 = sub_400660((char *)&v10 + 4, v3); goto LABEL_14; } } else { v5 = (unsigned __int8)v5; if ( (unsigned __int8)v5 == '.' ) { v7 = sub_400670(&v10, v3); goto LABEL_14; } if ( v5 == '0' ) { v7 = sub_400680(&v10, v3); LABEL_14: v6 = v7; goto LABEL_15; } } LABEL_15: v3 = (const char *)HIDWORD(v10); if ( !(unsigned __int8)sub_400690(asc_601060, HIDWORD(v10), (unsigned int)v10) ) goto LABEL_22; if ( ++v4 >= strlen(&s1) - 1 ) { if ( v6 ) break; LABEL_20: v8 = "Wrong flag!"; goto LABEL_21; } } } if ( asc_601060[8 * (signed int)v10 + SHIDWORD(v10)] != 35 ) goto LABEL_20; v8 = "Congratulations!"; LABEL_21: puts(v8); return 0LL; }
回到ida view-a
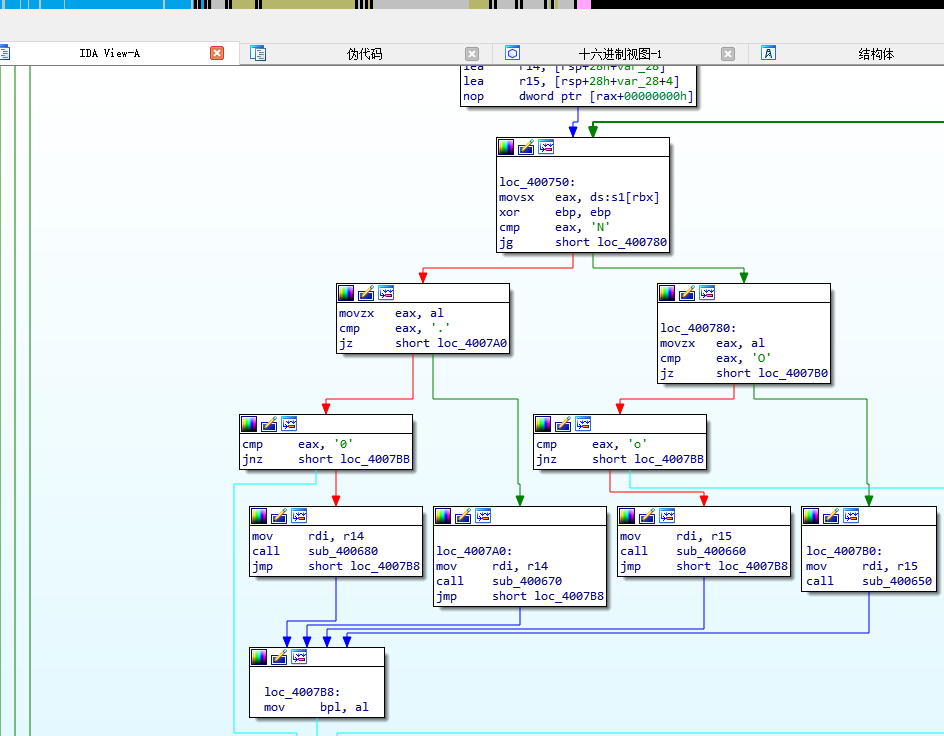
对相关位置按r,发现.o0O,大概是利用这四个字符进行不同的位置的迷宫操作
再看一下下面的400690
发现是与asc_601060有关
400822输出"wrong flag"
601060跳转的新的16进制窗口
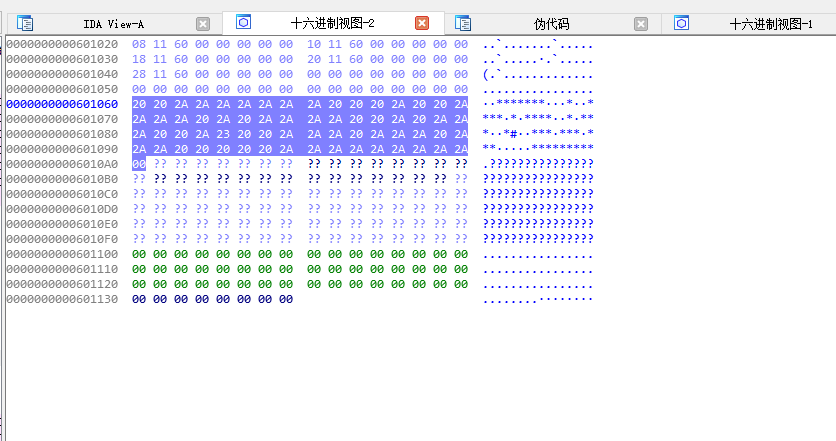
拼接一下得到下图

20是路径 2A是墙壁
得到
flag nctf{o0oo00O000oooo..OO}
//卡巴斯基又把我程序删了!!!!!!