SignIn 2019_SUCTF
__int64 __fastcall main(__int64 a1, char **a2, char **a3) { char mod; // [rsp+0h] [rbp-4A0h] char exp; // [rsp+10h] [rbp-490h] char base; // [rsp+20h] [rbp-480h] char goal; // [rsp+30h] [rbp-470h] char myinput; // [rsp+40h] [rbp-460h] char str; // [rsp+B0h] [rbp-3F0h] unsigned __int64 v10; // [rsp+498h] [rbp-8h] v10 = __readfsqword(0x28u); puts("[sign in]"); printf("[input your flag]: ", a2); __isoc99_scanf("%99s", &myinput); sub_96A(&myinput, (__int64)&str); // 转为16进制字符串表示 __gmpz_init_set_str(&goal, "ad939ff59f6e70bcbfad406f2494993757eee98b91bc244184a377520d06fc35", 16LL); __gmpz_init_set_str(&base, &str, 16LL); __gmpz_init_set_str(&mod, "103461035900816914121390101299049044413950405173712170434161686539878160984549", 10LL); __gmpz_init_set_str(&exp, "65537", 10LL); __gmpz_powm(&base, &base, &exp, &mod); // void mpz_powm (mpz_t rop, const mpz_t base, const mpz_t exp, const mpz_t mod) [Function] // Set rop to base^exp mod mod. if ( (unsigned int)__gmpz_cmp(&base, &goal) ) puts("GG!"); else puts("TTTTTTTTTTql!"); return 0LL; }
很明显的rsa加密
第一步分解大数N 103461035900816914121390101299049044413950405173712170434161686539878160984549
在线查询http://www.factordb.com/index.php?id=1100000001344853721
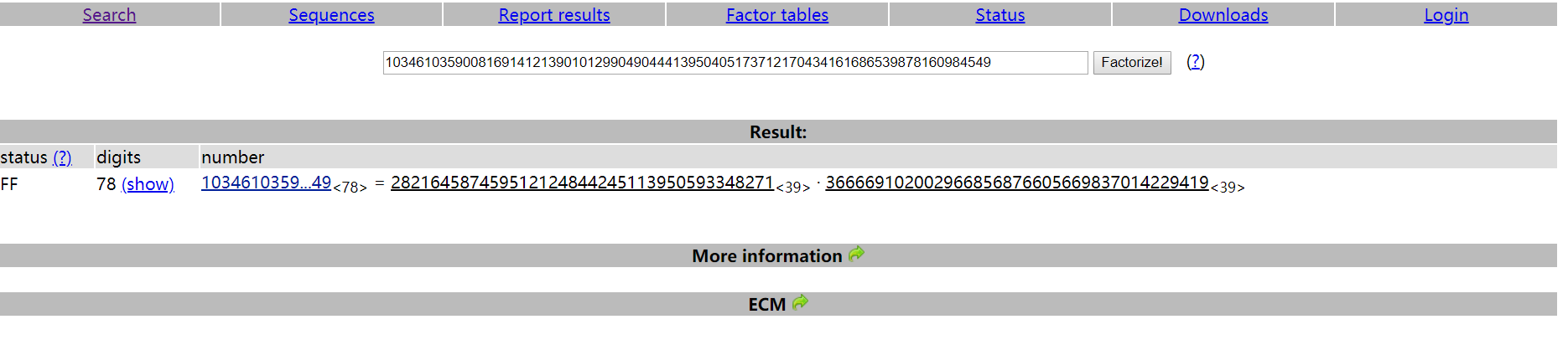
也可以使用yafu工具进行分解

下面求出d,进行解密便可
p = 366669102002966856876605669837014229419 q = 282164587459512124844245113950593348271 N = 103461035900816914121390101299049044413950405173712170434161686539878160984549 c = 0xad939ff59f6e70bcbfad406f2494993757eee98b91bc244184a377520d06fc35 e = 65537 def ext_euclid(a, b): old_s,s=1,0 old_t,t=0,1 old_r,r=a,b if b == 0: return 1, 0, a else: while(r!=0): q=old_r//r old_r,r=r,old_r-q*r old_s,s=s,old_s-q*s old_t,t=t,old_t-q*t return old_s, old_t, old_r ol=(p-1)*(q-1) d=ext_euclid(ol,e)[1] while d<0: d+=ol m = pow(c, d, N) print(bytes.fromhex(hex(m)[2:]))
suctf{Pwn_@_hundred_years}