xx
程序开始验证输入长度为19位。
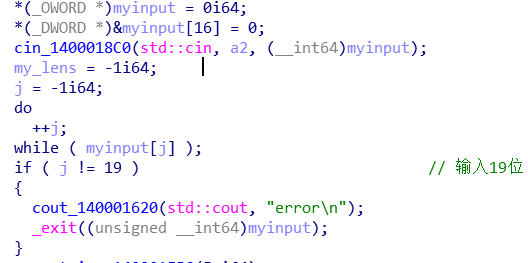
取前4位(作为后面加密的key),验证这4位都在‘qwertyuiopasdfghjklzxcvbnm1234567890‘中。

将key用0填充为16位

调用xxtea进行加密,加密结果再进行置换。
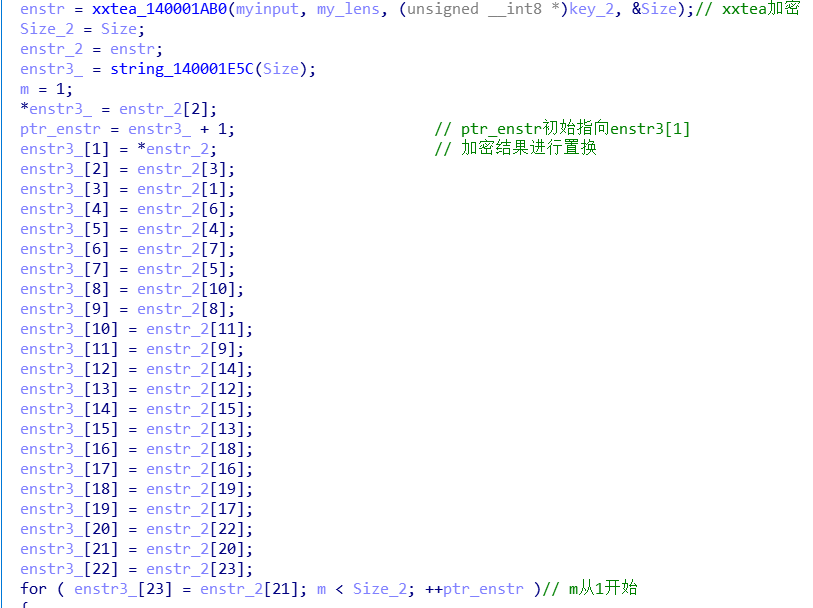
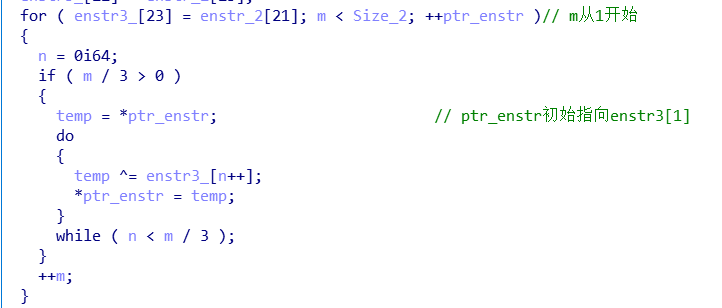
再进行异或操作
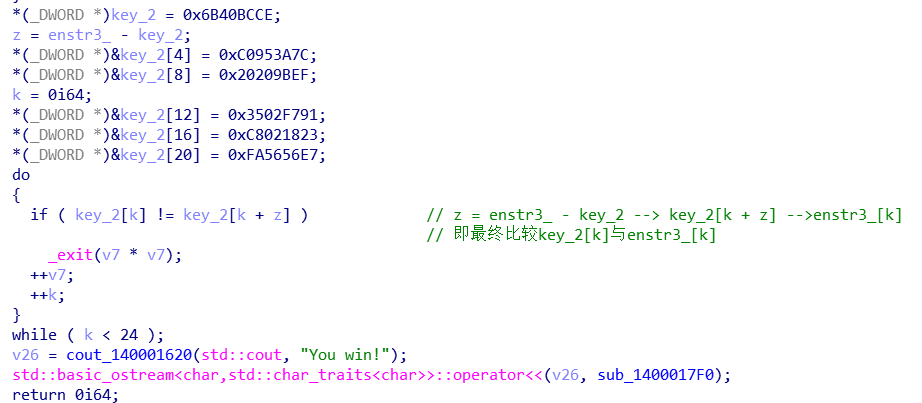
最终比较
wp
import struct _DELTA = 0x9E3779B9 def _long2str(v, w): n = (len(v) - 1) << 2 if w: m = v[-1] if (m < n - 3) or (m > n): return '' n = m s = struct.pack('<%iL' % len(v), *v) return s[0:n] if w else s def _str2long(s, w): n = len(s) m = (4 - (n & 3) & 3) + n s = s.ljust(m, b"�") v = list(struct.unpack('<%iL' % (m >> 2), s)) if w: v.append(n) return v def encrypt(str, key): if str == '': return str v = _str2long(str, True) k = _str2long(key.ljust(16, b"�"), False) n = len(v) - 1 z = v[n] y = v[0] sum = 0 q = 6 + 52 // (n + 1) while q > 0: sum = (sum + _DELTA) & 0xffffffff e = sum >> 2 & 3 for p in range(n): y = v[p + 1] v[p] = (v[p] + ((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4) ^ (sum ^ y) + (k[p & 3 ^ e] ^ z))) & 0xffffffff z = v[p] y = v[0] v[n] = (v[n] + ((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4) ^ (sum ^ y) + (k[n & 3 ^ e] ^ z))) & 0xffffffff z = v[n] q -= 1 return _long2str(v, False) def decrypt(str, key): if str == '': return str v = _str2long(str, False) k = _str2long(key.ljust(16, b"�"), False) n = len(v) - 1 z = v[n] y = v[0] q = 6 + 52 // (n + 1) sum = (q * _DELTA) & 0xffffffff while (sum != 0): e = sum >> 2 & 3 for p in range(n, 0, -1): z = v[p - 1] v[p] = (v[p] - ((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4) ^ (sum ^ y) + (k[p & 3 ^ e] ^ z))) & 0xffffffff y = v[p] z = v[n] v[0] = (v[0] - ((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4) ^ (sum ^ y) + (k[0 & 3 ^ e] ^ z))) & 0xffffffff y = v[0] sum = (sum - _DELTA) & 0xffffffff return _long2str(v, True) tg=[0xCE, 0xBC, 0x40, 0x6B, 0x7C, 0x3A, 0x95, 0xC0, 0xEF, 0x9B, 0x20, 0x20, 0x91, 0xF7, 0x02, 0x35, 0x23, 0x18, 0x02, 0xC8, 0xE7, 0x56, 0x56, 0xFA ] order=[2,0,3,1,6,4,7,5,10,8,11,9,14,12,15,13,18,16,19,17,22,20,23,21] flag=[0]*24 for i in range(23,-1,-1): for j in range(i//3): tg[i]^=tg[j] print('逆异或操作后:'+' '.join(map(hex,tg))) for i in range(24): flag[order[i]]=tg[i] print('逆加密字符串替换后:'+' '.join(map(hex,flag))) x=decrypt(bytes(flag),'flag'.encode()) print(x)
逆异或操作后:0xce 0xbc 0x40 0xa5 0xb2 0xf4 0xe7 0xb2 0x9d 0xa9 0x12 0x12 0xc8 0xae 0x5b 0x10 0x6 0x3d 0x1d 0xd7 0xf8 0xdc 0xdc 0x70
逆加密字符串替换后:0xbc 0xa5 0xce 0x40 0xf4 0xb2 0xb2 0xe7 0xa9 0x12 0x9d 0x12 0xae 0x10 0xc8 0x5b 0x3d 0xd7 0x6 0x1d 0xdc 0x70 0xf8 0xdc
b'flag{CXX_and_++tea}'
xxtea算法参考: