解决有关VIVO的2018-04-01安全补丁导致的APP闪退问题
事件:最近几天收到几个反馈说,原本能用的APP现在启动直接闪退.
时间:2018年5月8日 10:45:22
[√]问题原因猜测4:
虽然终于知道哪里出问题了,但是该代码是必须要保留的,否则本地数据库就完全无法使用了.那么该如何解决不能读取的问题? 还是通过打点,排除法,一步步的发现可疑代码.
Log.e("--------------", "" + R.string.sql_db_version);
Log.e("--------------", "" + R.string.sql_CreateDB);
Log.e("--------------", "" + R.string.sql_UpgradeDB);
Log.e("--------------", getString(R.string.sql_db_version));
Log.e("--------------", getString(R.string.sql_CreateDB));
Log.e("--------------", getString(R.string.sql_UpgradeDB));
最终的确发现日志的输出有可疑的地方:仅在getString(R.string.sql_CreateDB)时出现曾经的问题了.
05-08 17:28:12.125 E/--------------(24311): 2131362643
05-08 17:28:12.125 E/--------------(24311): 2131362571
05-08 17:28:12.125 E/--------------(24311): 2131362576
05-08 17:28:12.125 E/--------------(24311): 74
05-08 17:28:12.125 W/ResourceType(24311): Bad string block: string #14 is not null-terminated
在看了三个字符串实际内容时,发现 sql_CreateDB 的字符串刚好是长度最长的! 那么理论上无论在哪里调用 getString(R.string.sql_CreateDB) 都将会触发崩溃.
实际测试后,将该代码放入Activity里再调用,的确是崩溃了.而且Java层应用的
UncaughtExceptionHandler也捕获不了此类底层错误.
经过手工边界值测试,发现当XML里的string里存储的字符长度最大值为:
- [√正常]<= 10922 个中文字符
一 - [×崩溃]>= 10923 个中文字符
一 - [√正常]<= 10922 个中文字符
一+ 1个英文字符A - [×奔溃]>= 10922 个中文字符
一+ 2个英文字符A - [×奔溃]>= 10922*3=32766 个英文字符
A+ 2个英文字符A - [×奔溃]>= 34000 个英文字符
A - [√正常]<= 10922*2=21844 个英文字符
A+ 1个英文字符A - [√正常]>= 10922*3=32766 个英文字符
A+ 1个英文字符A
short 占用内存空间2个字节,也就是16个二进制位。 表示负数时,最高位为符号位(负数的符号位为1),最高位为符号位(正数的符号位为0),最大的正数为0111 1111 1111 1111 即2^15 - 1 = 32767
看到这个数字于是一个大胆的猜测浮现脑中:
- VIVO为了解决Android的某个类似堆栈溢出的安全问题,在
2018-04-01打了一个对应的安全补丁 - 影响的代码因为是在
libandroidfw.so文件里 - 影响的范围应该就是
nativeGetString时的允许的最大字符串长度
个人猜测:原本未修复前,这个最大字符串长度应该是没有设置的,所以才出现类似
堆栈溢出的漏洞.
最大字符串长度类型被有意或者无意改为了short类型?? 为什么呢?? 为了节约内存?? 节约内存也不应该在"安全补丁"里处理吧?- 现在修复之后,将其设置成了某个值,字符串长度大于这个值时就返回null
- 于是APP从最底层就崩溃了.
参考资料
Maximum length of string allowed as a value (8192 characters).
最终解决方案
既然是字符串长度超标导致的,那么可以
- 将其拆分成多个不同的 XML String 里.
- 将单张表的建表SQL放入 XML 的 String 数组里
- (最终采用的方案)将其放入 assets 目录里单独读取
- TODO:会减少内存占用否??
- TODO:会增加读取时间否??
- 会减少
resources.arsc大小
- resources.arsc: 原压缩后大小:505.15 现压缩后大小:398.73 减少大小: 106.42KB
- 总压缩比有所提升(总大小减少)
- assets: 原压缩后大小:24.88 现压缩后大小:38.58 增加大小: 13.7KB
- 总减少大小: 106.42KB - 13.7KB = 92.72KB
- 总的压缩比提升了,猜测原因是打包后的APK文件里 resources.arsc 文件默认是不压缩的,而 assets文件夹默认则是使用Deflate压缩算法压缩了.所以总的来说减少APK文件大小了.
参考资料:
[√]问题原因猜测3:
主要通过分析LogCat里的整个崩溃堆栈backtrace,从几个Android函数猜测可能在Application里初始化SQLiteOpenHelper导致的问题.
: backtrace:
: #00 pc 00018480 /system/lib/libandroidfw.so (_ZNK7android13ResStringPool9string8AtEjPj+147)
: #01 pc 0009d6f7 /system/lib/libandroid_runtime.so
: #02 pc 019d6287 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.StringBlock.nativeGetString+98)
: #03 pc 019d6609 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.StringBlock.get+324)
: #04 pc 019bca3b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.AssetManager.getResourceValue+126)
: #05 pc 019bc75b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.AssetManager.getResourceText+70)
: #06 pc 019d1adf /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.ResourcesImpl.getText+90)
: #07 pc 019cc583 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.Resources.getText+46)
: #08 pc 019cc34b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.Resources.getString+38)
: #09 pc 01735ff5 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.Context.getString+56)
:
: ……
:
: #20 pc 000ae413 /system/lib/libart.so (art_quick_to_interpreter_bridge+34)
: #21 pc 0194fc85 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.database.sqlite.SQLiteOpenHelper.getDatabaseLocked+760)
: #22 pc 0195029d /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.database.sqlite.SQLiteOpenHelper.getWritableDatabase+56)
: #23 pc 000a99c1 /system/lib/libart.so (art_quick_invoke_stub_internal+64)
:
: ……
:
: #55 pc 017b6e0b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread.handleCreateService+662)
: #56 pc 017b01ed /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread.-wrap5+48)
: #57 pc 017aceab /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread$H.handleMessage+4126)
: #58 pc 017aa74f /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.os.Handler.dispatchMessage+114)
: #59 pc 01d7ee87 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.os.Looper.loop+714)
: #60 pc 017bbcab /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread.main+438)
参考资料:
- 无限重启-千牛app Bad string block: string #6751 is not null-terminated - CSDN博客
- android 底层log分析 内存及backtrace tombstone/crash - 鸭子船长 - 博客园
- 如何阅读Android crash log以及stack trace - CSDN博客
尝试解决 [√成功]
- 将 继承自
Application的子类的onCreate里的 所有代码都移除 - 然后打包到 远程真机 VIVO X21A 终于没有 闪退了!
继续缩小定位到真正出错的代码行
原来是因为继承自Application的子类的 onCreate 里的有使用一行SQLite初始化代码需要从 R资源文件里读取建表SQL导致的问题!
class VSfaApplication extends BaseApplication
{
@Override
public void onCreate()
{
super.onCreate();
//注释掉就不会崩溃了.
//DBHelper.init(this, "VSFA", Utils.obj2int(this.getString(R.string.sql_db_version), 0), R.string.sql_CreateDB, R.string.sql_UpgradeDB);
}
}
[×]问题原因猜测2:
主要通过分析LogCat里的崩溃堆栈backtrace,猜测可能是某些特殊字符串导致的问题?
ResourceType: Bad string block: string #14 is not null-terminated
: backtrace:
: #00 pc 00018480 /system/lib/libandroidfw.so (_ZNK7android13ResStringPool9string8AtEjPj+147)
: #01 pc 0009d6f7 /system/lib/libandroid_runtime.so
: #02 pc 019d6287 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.StringBlock.nativeGetString+98)
: #03 pc 019d6609 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.StringBlock.get+324)
: #04 pc 019bca3b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.AssetManager.getResourceValue+126)
: #05 pc 019bc75b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.AssetManager.getResourceText+70)
: #06 pc 019d1adf /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.ResourcesImpl.getText+90)
: #07 pc 019cc583 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.Resources.getText+46)
: #08 pc 019cc34b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.Resources.getString+38)
: #09 pc 01735ff5 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.Context.getString+56)
尝试解决 [×失败]
- 将
AndroidManifest.xml删除所有只保留一个非常单纯的Activity作为android.intent.category.LAUNCHER - 在测试机测试时保证能正常启动到空白界面.
- 然后打包到 远程真机 VIVO X21A 还是 闪退了!
[×]问题原因猜测1:
主要通过分析LogCat猜测可能是 native 层出现未知异常
ResourceType: Bad string block: string #14 is not null-terminated
signal 11 (SIGSEGV), code 2 (SEGV_ACCERR), fault addr 0xe858eaf7
ActivityManager: net.azyk.sfa crash because Native crash
貌似还是跟权限相关的异常:
SEGV_ACCERRmeans you tried to access an address that you don’t have permission to access
Android -- SEGV_MAPERR,SEGV_ACCERR - CSDN博客
项目使用的.SO类库有:
1. libZBarDecoder.so
条码,二维码扫描组件
2. liblocSDK6a.so
百度定位组件
3. libbdpush_V2_7.so
百度推送组件
因为系统尚未渲染任何界面即闪退,那么很大可能是在Application里的初始化代码触发了.SO类库的初始化
尝试解决 [×失败]
- 重新打包APK将所有JNI类库都删除掉.
测试结果:
- 远程真机 VIVO X21A 还是闪退
- 真机ZUK Z2 7.1.2 正常打开
- 天天模拟器4.4.4版本 正常打开
根据线索尝试重现问题 [√成功]
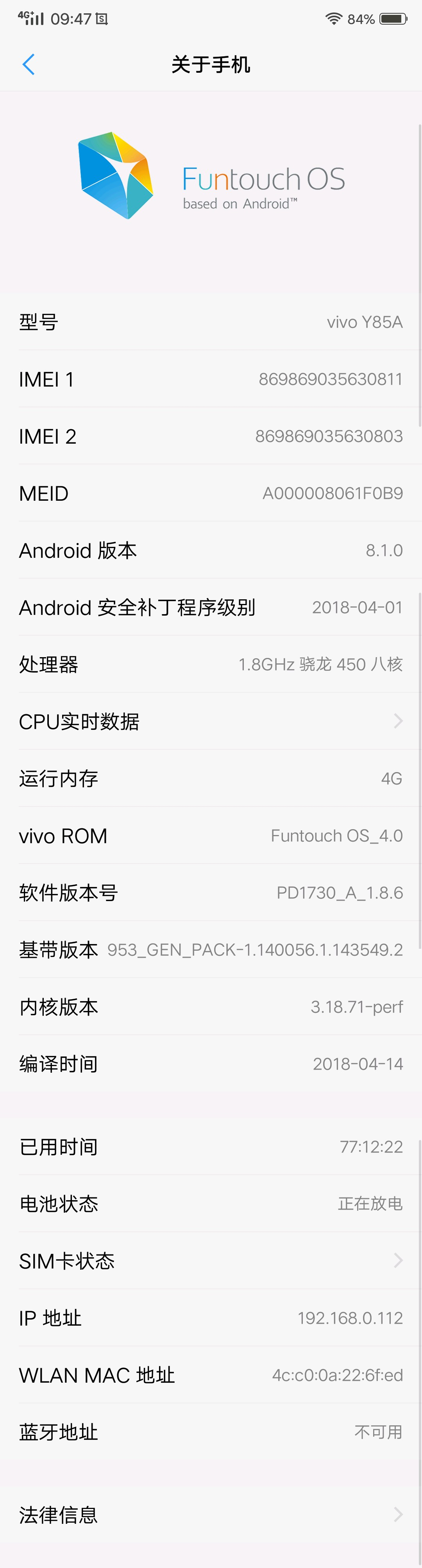
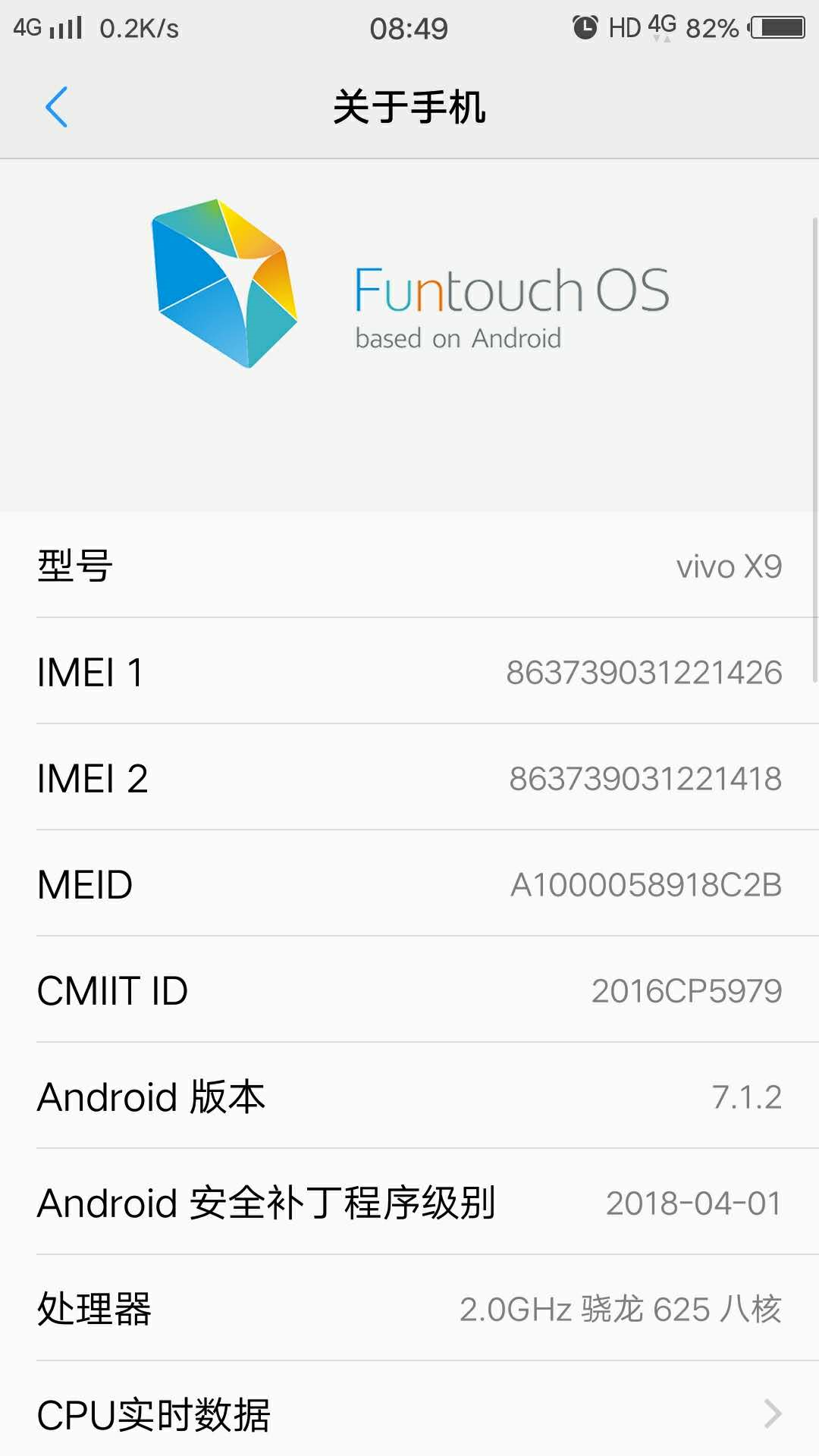
- 使用Testin远程真机服务 选择VIVO一样的8.1.0系统,安装同样的APP版本,没有出现闪退的情况. (不过 Android 安全补丁程序级别 貌似不是 2018-04-01 )
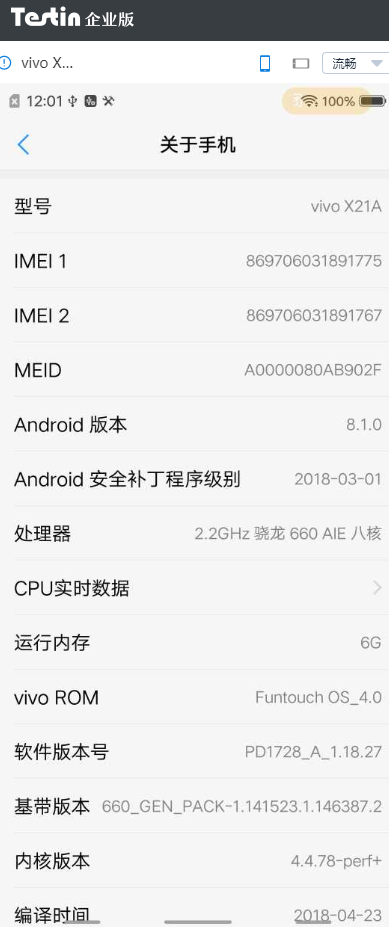
- 将远程真机检测系统升级到最新版本后, Android 安全补丁程序级别 变为 2018-04-01 后,再次尝试安装APP,完美重现闪退场景!
线索:
-
手机品牌都是VIVO
-
Android系统版本有7.1.2和8.1.0
-
Android 安全补丁程序级别 貌似都是 2018-04-01 (从几个人的反馈截图可见,Android版本不一样的情况下,补丁日期是相同的)
-
最近貌似都有过升级手机系统,或者换新手机的情况(最近新款VIVO手机内置最新版本8.1.0系统)。
-
点击APP图标直接一闪而过,没有看见任何界面被渲染出来(从微信小视频里看到的)
-
通过远程控制某位反馈人员的电脑间接控制其手机拿到了LogCat日志信息如下
05-08 10:01:01.656 3112 3112 D Launcher: click shortcut info is ShortcutInfo(title=海汇通intent=Intent { act=android.intent.action.MAIN cat=[android.intent.category.LAUNCHER] flg=0x10200000 cmp=net.azyk.sfa/net.azyk.framework.SystemLauncherFixerActivity bnds=[289,67][535,315] }id=77 type=30 container=-100 screen=2 cellX=1 cellY=0 spanX=1 spanY=1 isGesture=false dropPos=null) 05-08 10:01:01.660 1501 2392 E ActivityManager: Sending non-protected broadcast com.vivo.abe.third.lifecontrol from system uid 1000 pkg null 05-08 10:01:01.660 1501 2392 E ActivityManager: java.lang.Throwable 05-08 10:01:01.660 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.checkBroadcastFromSystem(ActivityManagerService.java:20249) 05-08 10:01:01.660 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.broadcastIntentLocked(ActivityManagerService.java:20755) 05-08 10:01:01.660 1501 2392 E ActivityManager: at com.android.server.am.ActivityStarter.startActivityLocked(ActivityStarter.java:434) 05-08 10:01:01.660 1501 2392 E ActivityManager: at com.android.server.am.ActivityStarter.startActivityMayWait(ActivityStarter.java:1239) 05-08 10:01:01.660 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.startActivityAsUser(ActivityManagerService.java:5508) 05-08 10:01:01.660 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.startActivity(ActivityManagerService.java:5442) 05-08 10:01:01.660 1501 2392 E ActivityManager: at android.app.ActivityManagerNative.onTransact(ActivityManagerNative.java:168) 05-08 10:01:01.660 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.onTransact(ActivityManagerService.java:3321) 05-08 10:01:01.660 1501 2392 E ActivityManager: at android.os.Binder.execTransact(Binder.java:565) 05-08 10:01:01.661 1501 2392 E ActivityManager: Sending non-protected broadcast com.vivo.abe.third.lifecontrol from system uid 1000 pkg null 05-08 10:01:01.661 1501 2392 E ActivityManager: java.lang.Throwable 05-08 10:01:01.661 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.checkBroadcastFromSystem(ActivityManagerService.java:20249) 05-08 10:01:01.661 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.broadcastIntentLocked(ActivityManagerService.java:20846) 05-08 10:01:01.661 1501 2392 E ActivityManager: at com.android.server.am.ActivityStarter.startActivityLocked(ActivityStarter.java:434) 05-08 10:01:01.661 1501 2392 E ActivityManager: at com.android.server.am.ActivityStarter.startActivityMayWait(ActivityStarter.java:1239) 05-08 10:01:01.661 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.startActivityAsUser(ActivityManagerService.java:5508) 05-08 10:01:01.661 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.startActivity(ActivityManagerService.java:5442) 05-08 10:01:01.661 1501 2392 E ActivityManager: at android.app.ActivityManagerNative.onTransact(ActivityManagerNative.java:168) 05-08 10:01:01.661 1501 2392 E ActivityManager: at com.android.server.am.ActivityManagerService.onTransact(ActivityManagerService.java:3321) 05-08 10:01:01.661 1501 2392 E ActivityManager: at android.os.Binder.execTransact(Binder.java:565) 05-08 10:01:01.662 1501 2392 I ActivityManager: START u0 {act=android.intent.action.MAIN cat=[android.intent.category.LAUNCHER] flg=0x10200000 cmp=net.azyk.sfa/net.azyk.framework.SystemLauncherFixerActivity bnds=[289,67][535,315]} from uid 10028 on display 0 05-08 10:01:01.670 1501 2392 D ActivityTrigger: ActivityTrigger activityPauseTrigger 05-08 10:01:01.673 3112 3112 D Launcher: startActivitySafely success ? true 05-08 10:01:01.674 3112 3112 D Launcher: onWindowFocusChanged , hasFocus = false 05-08 10:01:01.675 3112 3112 D Launcher: onPause -- mState = WORKSPACE 05-08 10:01:01.687 1501 3144 I ActivityManager: Start proc 17739:net.azyk.sfa/u0a91 for activity net.azyk.sfa/net.azyk.framework.SystemLauncherFixerActivity 05-08 10:01:01.704 1501 1515 D BBKTouchScreenService: pakage name is net.azyk.sfawith :10091 05-08 10:01:01.705 1501 1515 D BBKTouchScreenService: called and appName is [B@cb58e39 05-08 10:01:01.705 1501 1515 D touchscreenjni: chenpeng JNI called 05-08 10:01:01.705 1501 1515 E touchscreen: Open /sys/touchscreen/app_name failed 05-08 10:01:01.705 1501 1878 D UserModifyRecorder: pakage name is net.azyk.sfa with :10091 05-08 10:01:01.705 1501 1515 D VivoAppMonitor: onForegroundActivitiesChanged: pid=17739, uid=10091, foregroundActivities=true 05-08 10:01:01.706 1501 1515 D VivoAppMonitor: mForgroundAppName=net.azyk.sfa, mLastForgroundAppName = com.bbk.launcher2 05-08 10:01:01.748 17739 17739 I FtBuild : getRomVersion mRomVer=3.5 05-08 10:01:01.770 1501 2385 I ActivityManager: START u0 {flg=0x10000000 cmp=net.azyk.sfa/net.azyk.vsfa.v010v.login.LaunchScreenActivity} from uid 10091 on display 0 05-08 10:01:01.774 1501 2385 D ActivityTrigger: ActivityTrigger activityPauseTrigger 05-08 10:01:01.816 17739 17739 W ResourceType: Bad string block: string #14 is not null-terminated 05-08 10:01:01.817 474 474 W : debuggerd: handling request: pid=17739 uid=10091 gid=10091 tid=17739 05-08 10:01:01.884 17757 17757 F DEBUG : *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** 05-08 10:01:01.884 17757 17757 F DEBUG : Build fingerprint: 'vivo/PD1616/PD1616:7.1.2/N2G47H/compil04282005:user/release-keys' 05-08 10:01:01.884 17757 17757 F DEBUG : Revision: '0' 05-08 10:01:01.884 17757 17757 F DEBUG : ABI: 'arm' 05-08 10:01:01.884 17757 17757 F DEBUG : pid: 17739, tid: 17739, name: net.azyk.sfa >>> net.azyk.sfa <<< 05-08 10:01:01.884 17757 17757 F DEBUG : signal 11 (SIGSEGV), code 2 (SEGV_ACCERR), fault addr 0xe858eaf7 05-08 10:01:01.884 17757 17757 F DEBUG : r0 00000000 r1 00000000 r2 abf2adc2 r3 ec90685d 05-08 10:01:01.884 17757 17757 F DEBUG : r4 e858d0f6 r5 00001b27 r6 e858eaf7 r7 12c5a4e0 05-08 10:01:01.884 17757 17757 F DEBUG : r8 12c812b0 r9 e9b05e00 sl 7079bfac fp 12c5a4e0 05-08 10:01:01.884 17757 17757 F DEBUG : ip fffffffc sp ffb546e8 lr ec98d47f pc ec98d480 cpsr 600b0030 05-08 10:01:02.124 564 564 I SurfaceFlinger: FPS: 31 05-08 10:01:02.227 17757 17757 F DEBUG : 05-08 10:01:02.227 17757 17757 F DEBUG : backtrace: 05-08 10:01:02.227 17757 17757 F DEBUG : #00 pc 00018480 /system/lib/libandroidfw.so (_ZNK7android13ResStringPool9string8AtEjPj+147) 05-08 10:01:02.227 17757 17757 F DEBUG : #01 pc 0009d6f7 /system/lib/libandroid_runtime.so 05-08 10:01:02.227 17757 17757 F DEBUG : #02 pc 019d6287 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.StringBlock.nativeGetString+98) 05-08 10:01:02.227 17757 17757 F DEBUG : #03 pc 019d6609 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.StringBlock.get+324) 05-08 10:01:02.227 17757 17757 F DEBUG : #04 pc 019bca3b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.AssetManager.getResourceValue+126) 05-08 10:01:02.227 17757 17757 F DEBUG : #05 pc 019bc75b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.AssetManager.getResourceText+70) 05-08 10:01:02.227 17757 17757 F DEBUG : #06 pc 019d1adf /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.ResourcesImpl.getText+90) 05-08 10:01:02.227 17757 17757 F DEBUG : #07 pc 019cc583 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.Resources.getText+46) 05-08 10:01:02.227 17757 17757 F DEBUG : #08 pc 019cc34b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.res.Resources.getString+38) 05-08 10:01:02.227 17757 17757 F DEBUG : #09 pc 01735ff5 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.content.Context.getString+56) 05-08 10:01:02.227 17757 17757 F DEBUG : #10 pc 000a99c1 /system/lib/libart.so (art_quick_invoke_stub_internal+64) 05-08 10:01:02.227 17757 17757 F DEBUG : #11 pc 00405681 /system/lib/libart.so (art_quick_invoke_stub+232) 05-08 10:01:02.227 17757 17757 F DEBUG : #12 pc 000b0c55 /system/lib/libart.so (_ZN3art9ArtMethod6InvokeEPNS_6ThreadEPjjPNS_6JValueEPKc+136) 05-08 10:01:02.227 17757 17757 F DEBUG : #13 pc 001ed215 /system/lib/libart.so (_ZN3art11interpreter34ArtInterpreterToCompiledCodeBridgeEPNS_6ThreadEPNS_9ArtMethodEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameEPNS_6JValueE+200) 05-08 10:01:02.227 17757 17757 F DEBUG : #14 pc 001e77c5 /system/lib/libart.so (_ZN3art11interpreter6DoCallILb0ELb0EEEbPNS_9ArtMethodEPNS_6ThreadERNS_11ShadowFrameEPKNS_11InstructionEtPNS_6JValueE+492) 05-08 10:01:02.227 17757 17757 F DEBUG : #15 pc 003ffafb /system/lib/libart.so (MterpInvokeVirtualQuick+322) 05-08 10:01:02.227 17757 17757 F DEBUG : #16 pc 000a0594 /system/lib/libart.so (ExecuteMterpImpl+29972) 05-08 10:01:02.227 17757 17757 F DEBUG : #17 pc 001caaef /system/lib/libart.so (_ZN3art11interpreterL7ExecuteEPNS_6ThreadEPKNS_7DexFile8CodeItemERNS_11ShadowFrameENS_6JValueEb+290) 05-08 10:01:02.227 17757 17757 F DEBUG : #18 pc 001cf5c1 /system/lib/libart.so (_ZN3art11interpreter30EnterInterpreterFromEntryPointEPNS_6ThreadEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameE+92) 05-08 10:01:02.227 17757 17757 F DEBUG : #19 pc 003f4b7f /system/lib/libart.so (artQuickToInterpreterBridge+706) 05-08 10:01:02.227 17757 17757 F DEBUG : #20 pc 000ae413 /system/lib/libart.so (art_quick_to_interpreter_bridge+34) 05-08 10:01:02.227 17757 17757 F DEBUG : #21 pc 0194fc85 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.database.sqlite.SQLiteOpenHelper.getDatabaseLocked+760) 05-08 10:01:02.227 17757 17757 F DEBUG : #22 pc 0195029d /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.database.sqlite.SQLiteOpenHelper.getWritableDatabase+56) 05-08 10:01:02.227 17757 17757 F DEBUG : #23 pc 000a99c1 /system/lib/libart.so (art_quick_invoke_stub_internal+64) 05-08 10:01:02.227 17757 17757 F DEBUG : #24 pc 00405681 /system/lib/libart.so (art_quick_invoke_stub+232) 05-08 10:01:02.228 17757 17757 F DEBUG : #25 pc 000b0c55 /system/lib/libart.so (_ZN3art9ArtMethod6InvokeEPNS_6ThreadEPjjPNS_6JValueEPKc+136) 05-08 10:01:02.228 17757 17757 F DEBUG : #26 pc 001ed215 /system/lib/libart.so (_ZN3art11interpreter34ArtInterpreterToCompiledCodeBridgeEPNS_6ThreadEPNS_9ArtMethodEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameEPNS_6JValueE+200) 05-08 10:01:02.228 17757 17757 F DEBUG : #27 pc 001e77c5 /system/lib/libart.so (_ZN3art11interpreter6DoCallILb0ELb0EEEbPNS_9ArtMethodEPNS_6ThreadERNS_11ShadowFrameEPKNS_11InstructionEtPNS_6JValueE+492) 05-08 10:01:02.228 17757 17757 F DEBUG : #28 pc 003ffafb /system/lib/libart.so (MterpInvokeVirtualQuick+322) 05-08 10:01:02.228 17757 17757 F DEBUG : #29 pc 000a0594 /system/lib/libart.so (ExecuteMterpImpl+29972) 05-08 10:01:02.228 17757 17757 F DEBUG : #30 pc 001caaef /system/lib/libart.so (_ZN3art11interpreterL7ExecuteEPNS_6ThreadEPKNS_7DexFile8CodeItemERNS_11ShadowFrameENS_6JValueEb+290) 05-08 10:01:02.228 17757 17757 F DEBUG : #31 pc 001cf657 /system/lib/libart.so (_ZN3art11interpreter33ArtInterpreterToInterpreterBridgeEPNS_6ThreadEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameEPNS_6JValueE+114) 05-08 10:01:02.228 17757 17757 F DEBUG : #32 pc 001e77ab /system/lib/libart.so (_ZN3art11interpreter6DoCallILb0ELb0EEEbPNS_9ArtMethodEPNS_6ThreadERNS_11ShadowFrameEPKNS_11InstructionEtPNS_6JValueE+466) 05-08 10:01:02.228 17757 17757 F DEBUG : #33 pc 003fe299 /system/lib/libart.so (MterpInvokeStatic+236) 05-08 10:01:02.228 17757 17757 F DEBUG : #34 pc 0009c994 /system/lib/libart.so (ExecuteMterpImpl+14612) 05-08 10:01:02.228 17757 17757 F DEBUG : #35 pc 001caaef /system/lib/libart.so (_ZN3art11interpreterL7ExecuteEPNS_6ThreadEPKNS_7DexFile8CodeItemERNS_11ShadowFrameENS_6JValueEb+290) 05-08 10:01:02.228 17757 17757 F DEBUG : #36 pc 001cf657 /system/lib/libart.so (_ZN3art11interpreter33ArtInterpreterToInterpreterBridgeEPNS_6ThreadEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameEPNS_6JValueE+114) 05-08 10:01:02.228 17757 17757 F DEBUG : #37 pc 001e77ab /system/lib/libart.so (_ZN3art11interpreter6DoCallILb0ELb0EEEbPNS_9ArtMethodEPNS_6ThreadERNS_11ShadowFrameEPKNS_11InstructionEtPNS_6JValueE+466) 05-08 10:01:02.228 17757 17757 F DEBUG : #38 pc 003fe299 /system/lib/libart.so (MterpInvokeStatic+236) 05-08 10:01:02.228 17757 17757 F DEBUG : #39 pc 0009c994 /system/lib/libart.so (ExecuteMterpImpl+14612) 05-08 10:01:02.228 17757 17757 F DEBUG : #40 pc 001caaef /system/lib/libart.so (_ZN3art11interpreterL7ExecuteEPNS_6ThreadEPKNS_7DexFile8CodeItemERNS_11ShadowFrameENS_6JValueEb+290) 05-08 10:01:02.228 17757 17757 F DEBUG : #41 pc 001cf5c1 /system/lib/libart.so (_ZN3art11interpreter30EnterInterpreterFromEntryPointEPNS_6ThreadEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameE+92) 05-08 10:01:02.228 17757 17757 F DEBUG : #42 pc 003f4b7f /system/lib/libart.so (artQuickToInterpreterBridge+706) 05-08 10:01:02.228 17757 17757 F DEBUG : #43 pc 000ae413 /system/lib/libart.so (art_quick_to_interpreter_bridge+34) 05-08 10:01:02.228 17757 17757 F DEBUG : #44 pc 000a99c1 /system/lib/libart.so (art_quick_invoke_stub_internal+64) 05-08 10:01:02.228 17757 17757 F DEBUG : #45 pc 00405789 /system/lib/libart.so (art_quick_invoke_static_stub+228) 05-08 10:01:02.228 17757 17757 F DEBUG : #46 pc 000b0c7f /system/lib/libart.so (_ZN3art9ArtMethod6InvokeEPNS_6ThreadEPjjPNS_6JValueEPKc+178) 05-08 10:01:02.228 17757 17757 F DEBUG : #47 pc 001ed215 /system/lib/libart.so (_ZN3art11interpreter34ArtInterpreterToCompiledCodeBridgeEPNS_6ThreadEPNS_9ArtMethodEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameEPNS_6JValueE+200) 05-08 10:01:02.228 17757 17757 F DEBUG : #48 pc 001e77c5 /system/lib/libart.so (_ZN3art11interpreter6DoCallILb0ELb0EEEbPNS_9ArtMethodEPNS_6ThreadERNS_11ShadowFrameEPKNS_11InstructionEtPNS_6JValueE+492) 05-08 10:01:02.228 17757 17757 F DEBUG : #49 pc 003fe299 /system/lib/libart.so (MterpInvokeStatic+236) 05-08 10:01:02.228 17757 17757 F DEBUG : #50 pc 0009c994 /system/lib/libart.so (ExecuteMterpImpl+14612) 05-08 10:01:02.228 17757 17757 F DEBUG : #51 pc 001caaef /system/lib/libart.so (_ZN3art11interpreterL7ExecuteEPNS_6ThreadEPKNS_7DexFile8CodeItemERNS_11ShadowFrameENS_6JValueEb+290) 05-08 10:01:02.228 17757 17757 F DEBUG : #52 pc 001cf5c1 /system/lib/libart.so (_ZN3art11interpreter30EnterInterpreterFromEntryPointEPNS_6ThreadEPKNS_7DexFile8CodeItemEPNS_11ShadowFrameE+92) 05-08 10:01:02.228 17757 17757 F DEBUG : #53 pc 003f4b7f /system/lib/libart.so (artQuickToInterpreterBridge+706) 05-08 10:01:02.228 17757 17757 F DEBUG : #54 pc 000ae413 /system/lib/libart.so (art_quick_to_interpreter_bridge+34) 05-08 10:01:02.228 17757 17757 F DEBUG : #55 pc 017b6e0b /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread.handleCreateService+662) 05-08 10:01:02.228 17757 17757 F DEBUG : #56 pc 017b01ed /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread.-wrap5+48) 05-08 10:01:02.228 17757 17757 F DEBUG : #57 pc 017aceab /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread$H.handleMessage+4126) 05-08 10:01:02.228 17757 17757 F DEBUG : #58 pc 017aa74f /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.os.Handler.dispatchMessage+114) 05-08 10:01:02.228 17757 17757 F DEBUG : #59 pc 01d7ee87 /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.os.Looper.loop+714) 05-08 10:01:02.228 17757 17757 F DEBUG : #60 pc 017bbcab /system/framework/arm/boot-framework.oat (offset 0x1734000) (android.app.ActivityThread.main+438) 05-08 10:01:02.228 17757 17757 F DEBUG : #61 pc 000a99c1 /system/lib/libart.so (art_quick_invoke_stub_internal+64) 05-08 10:01:02.228 17757 17757 F DEBUG : #62 pc 00405789 /system/lib/libart.so (art_quick_invoke_static_stub+228) 05-08 10:01:02.228 17757 17757 F DEBUG : #63 pc 000b0c7f /system/lib/libart.so (_ZN3art9ArtMethod6InvokeEPNS_6ThreadEPjjPNS_6JValueEPKc+178) 05-08 10:01:02.275 1501 1514 W ActivityManager: Activity pause timeout for ActivityRecord{5e14494 u0 net.azyk.sfa/net.azyk.framework.SystemLauncherFixerActivity t35 f} 05-08 10:01:02.279 2124 2138 V pem : noteActivityV5 uid = 10091, cool = 1, Name = net.azyk.vsfa.v010v.login.LaunchScreenActivity 05-08 10:01:02.555 1501 17762 I ActivityManager: handleApplicationCrash callnet.azyk.sfa 05-08 10:01:02.556 1501 17762 W ContextImpl: Calling a method in the system process without a qualified user: android.app.ContextImpl.startService:1363 com.android.server.am.ActivityManagerService.handleApplicationCrashInner:15415 com.android.server.am.NativeCrashListener$NativeCrashReporter.run:86 <bottom of call stack> <bottom of call stack> 05-08 10:01:02.558 2124 2137 D SLService: ppCra : net.azyk.sfa pid : 17739 05-08 10:01:02.558 3042 3042 I UDC_LogUploadService: onCreate 05-08 10:01:02.562 474 474 W : debuggerd: resuming target 17739 05-08 10:01:02.563 1501 17762 W ActivityManager: Force finishing activity net.azyk.sfa/net.azyk.vsfa.v010v.login.LaunchScreenActivity 05-08 10:01:02.566 1501 17762 D ActivityTrigger: ActivityTrigger activityPauseTrigger 05-08 10:01:02.566 1501 17762 E JavaBinder: !!! FAILED BINDER TRANSACTION !!! (parcel size = 112) 05-08 10:01:02.566 2124 3459 V pem : noteAppPaused uid = 10091 05-08 10:01:02.567 1501 17762 W ActivityManager: Exception thrown during pause 05-08 10:01:02.567 1501 17762 W ActivityManager: android.os.DeadObjectException: Transaction failed on small parcel; remote process probably died 05-08 10:01:02.567 1501 17762 W ActivityManager: at android.os.BinderProxy.transactNative(Native Method) 05-08 10:01:02.567 1501 17762 W ActivityManager: at android.os.BinderProxy.transact(Binder.java:615) 05-08 10:01:02.567 1501 17762 W ActivityManager: at android.app.ApplicationThreadProxy.schedulePauseActivity(ApplicationThreadNative.java:804) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.ActivityStack.startPausingLocked(ActivityStack.java:1204) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.ActivityStack.finishActivityLocked(ActivityStack.java:3866) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.ActivityStack.finishTopRunningActivityLocked(ActivityStack.java:3689) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.ActivityStackSupervisor.finishTopRunningActivityLocked(ActivityStackSupervisor.java:2077) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.AppErrors.handleAppCrashLocked(AppErrors.java:687) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.AppErrors.makeAppCrashingLocked(AppErrors.java:538) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.AppErrors.crashApplicationInner(AppErrors.java:373) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.AppErrors.crashApplication(AppErrors.java:325) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.ActivityManagerService.handleApplicationCrashInner(ActivityManagerService.java:15420) 05-08 10:01:02.567 1501 17762 W ActivityManager: at com.android.server.am.NativeCrashListener$NativeCrashReporter.run(NativeCrashListener.java:86) 05-08 10:01:02.567 734 734 I Zygote : Process 17739 exited due to signal (11) 05-08 10:01:02.570 1501 17762 W ActivityManager: Failed setting process group of 17739 to 1 05-08 10:01:02.570 1501 17762 W System.err: java.lang.IllegalArgumentException: Given thread 17739 does not exist 05-08 10:01:02.571 1501 17762 W System.err: at android.os.Process.setThreadPriority(Native Method) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityManagerService.applyOomAdjLocked(ActivityManagerService.java:23039) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityManagerService.updateOomAdjLocked(ActivityManagerService.java:23583) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStack.resumeTopActivityInnerLocked(ActivityStack.java:2721) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStack.resumeTopActivityUncheckedLocked(ActivityStack.java:2311) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStackSupervisor.resumeFocusedStackTopActivityLocked(ActivityStackSupervisor.java:2050) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStackSupervisor.resumeFocusedStackTopActivityLocked(ActivityStackSupervisor.java:2004) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStack.startPausingLocked(ActivityStack.java:1259) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStack.finishActivityLocked(ActivityStack.java:3866) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStack.finishTopRunningActivityLocked(ActivityStack.java:3689) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityStackSupervisor.finishTopRunningActivityLocked(ActivityStackSupervisor.java:2077) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.AppErrors.handleAppCrashLocked(AppErrors.java:687) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.AppErrors.makeAppCrashingLocked(AppErrors.java:538) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.AppErrors.crashApplicationInner(AppErrors.java:373) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.AppErrors.crashApplication(AppErrors.java:325) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.ActivityManagerService.handleApplicationCrashInner(ActivityManagerService.java:15420) 05-08 10:01:02.571 1501 17762 W System.err: at com.android.server.am.NativeCrashListener$NativeCrashReporter.run(NativeCrashListener.java:86) 05-08 10:01:02.579 1501 17762 W ActivityManager: net.azyk.sfa crash because Native crash
反馈信息汇总
反馈的系统截图1
反馈的系统截图2
<wiz_tmp_tag id="wiz-table-range-border" contenteditable="false" style="display: none;">