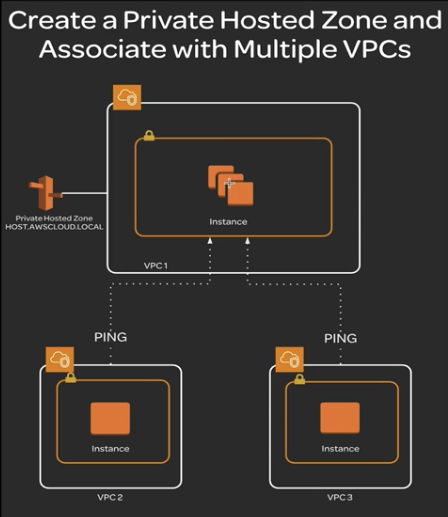
We are going to create a A private host zone and test this private host zone with VPC1 and VPC2... for VPC3, you can follow the VPC2 as example.
- Create a private host zone in VPC1, VPC2, VPC3
- Then create an A record in Route 53 point to instance in VPC 1
- Then perring VPC1 and VPC2
- Edit route tables for the subnets in VPC1 and VPC2, point to each other
- Edit Security Group to point to each other
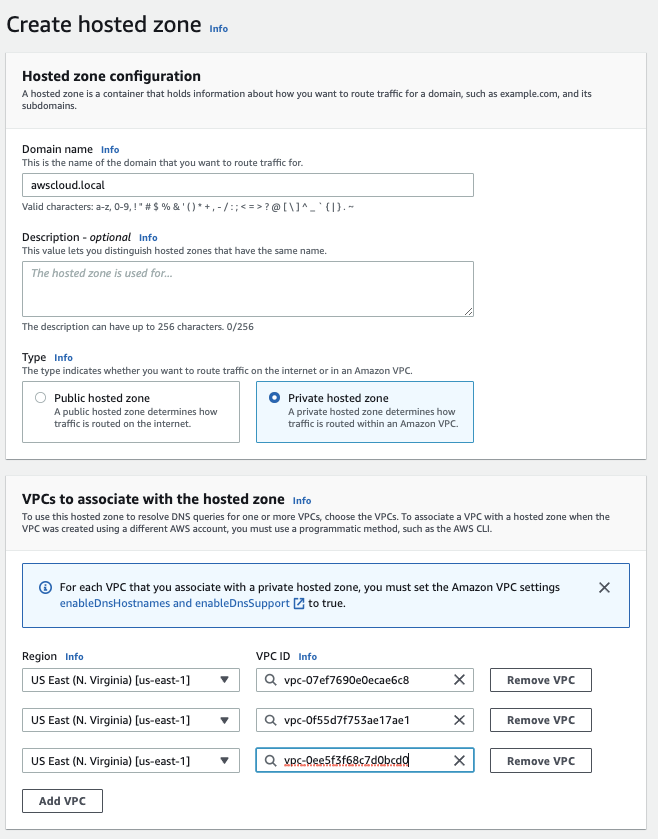
Create a private host zone
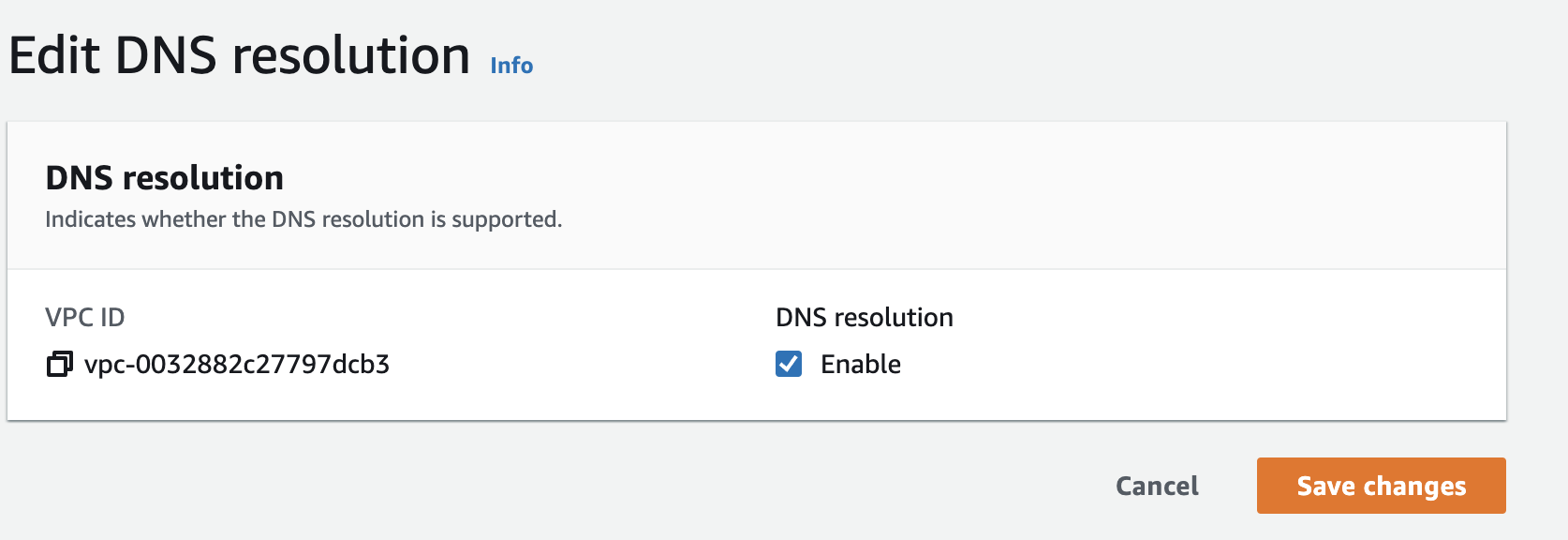
Because we have created private host zone, we need to make sure for VPC1,2,3 they all have enabled DNS hostname and DNS record.

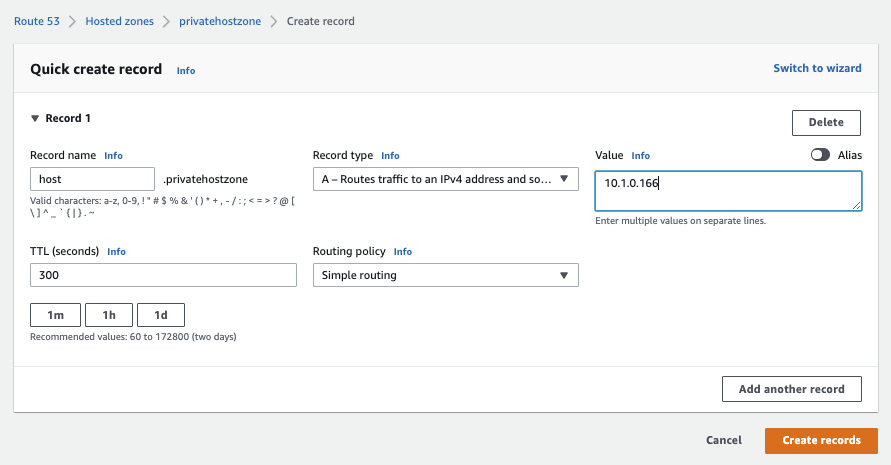
Create an A Record
The Record name should point to the private IP address of instance 1 in VPC 1
Perring VPC
Create a peering connection from VPC1 to VPC2
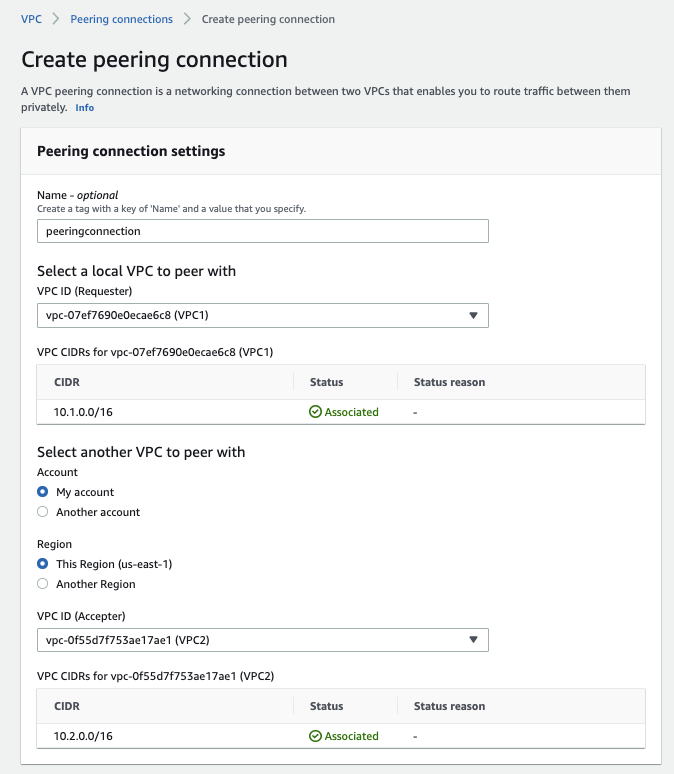
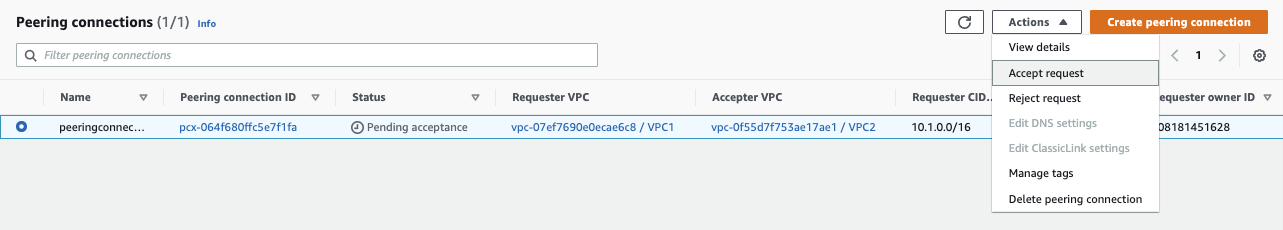
Then you need to Accpet the perring connection
Edit route tables
Edit VPC1 subnet route table to point traffic to VPC2 by going throught peering connection;

Edit VPC2 subnet route table to point traffic to VPC1 by going throught peering connection:

Edit Security Group
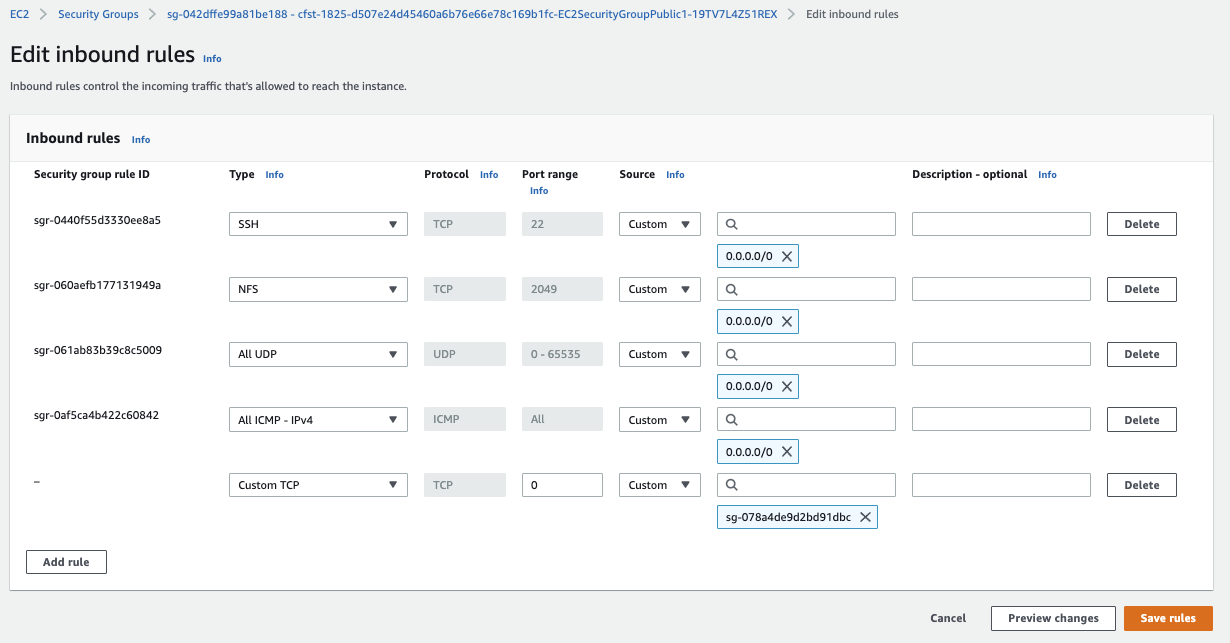
For the instance in VPC1's securty group, should accept inbound rule from VCP2's instance's Security Group
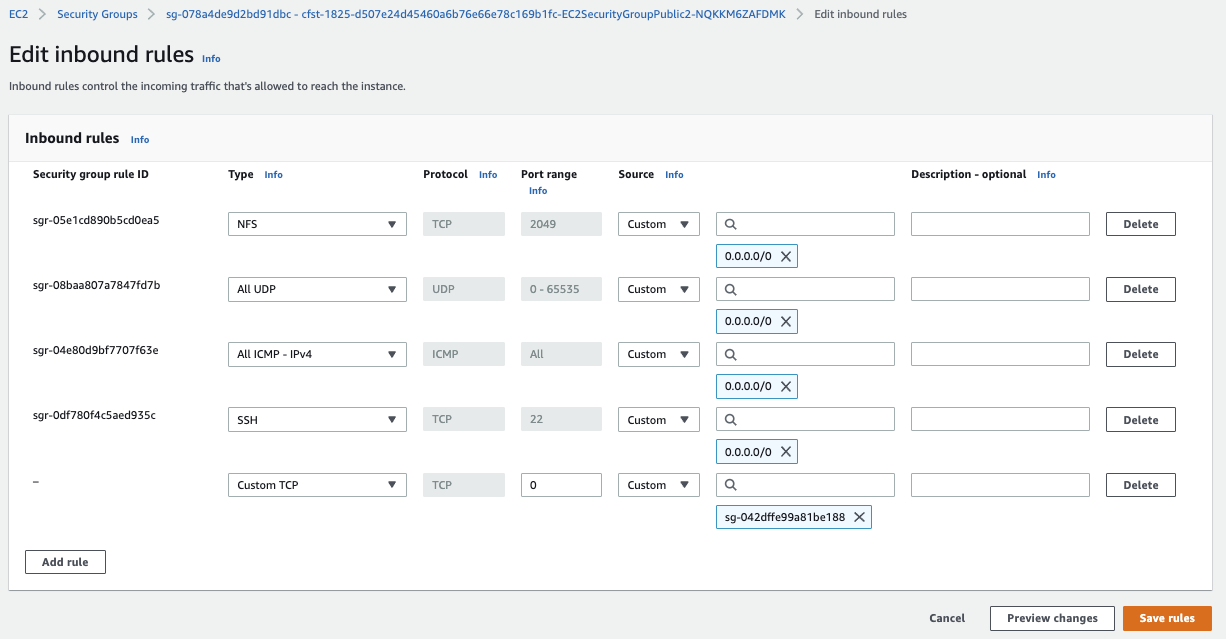
For the VPC2's instance security group should accpet VPC1's instance's security group
Last, ssh into instance 2 in VPC2, ping host.awscloud.local, from the result, you can see the private ip address of instance1
