Overview
- max 5 per region
- max 5 CIDR per VPC
- VPC CIDR should not overlap with your other networks

Subnet

- AWS reserves 5 IPs address (first 4 and last 1 IP address)
Internet Gateway
- Help to connect to internet
- Scales horizontally and HA and redundant
- Must be create separately from VPC
If you have created your own VPC, and you want your EC2 inside VPC to access internet, you have to add internet gateway to your VPC
- One VPC can only attached to one IGW and vice versa
- Internet Gateway is also a NAT for the instances that have a public IPv4
- Internet Gateways on their own do not allow internet access
- Route table must also be edited
If you have added IGW to your VPC, and you will find that you are still not able to connect to internet, this is because you must create a route table, route table attached in Subnet level, and its has a route to IGW.

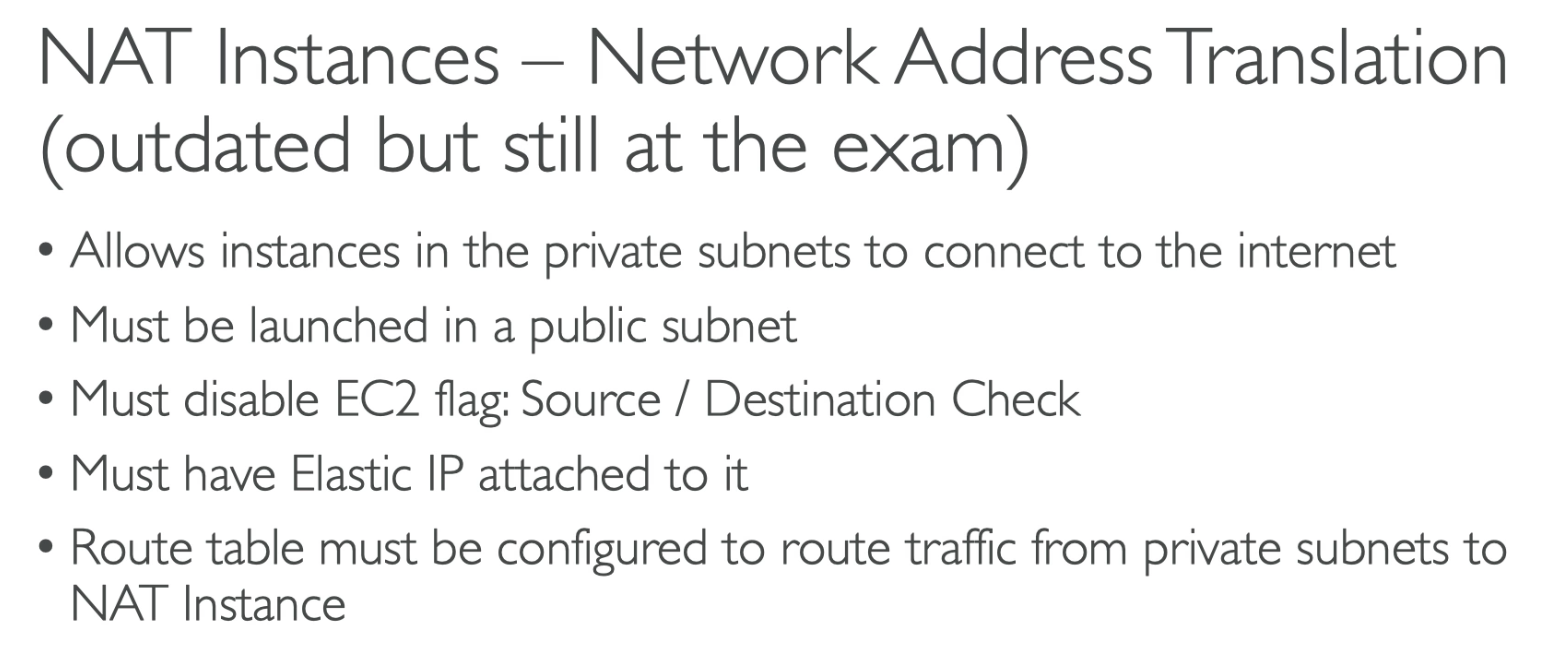
- NAT instances allow a private subnet to connect to internet
- Must have EIP attached to it
- Must disable EC2 flag: source / destination check

Private subnet should also have a Route table attach to it.

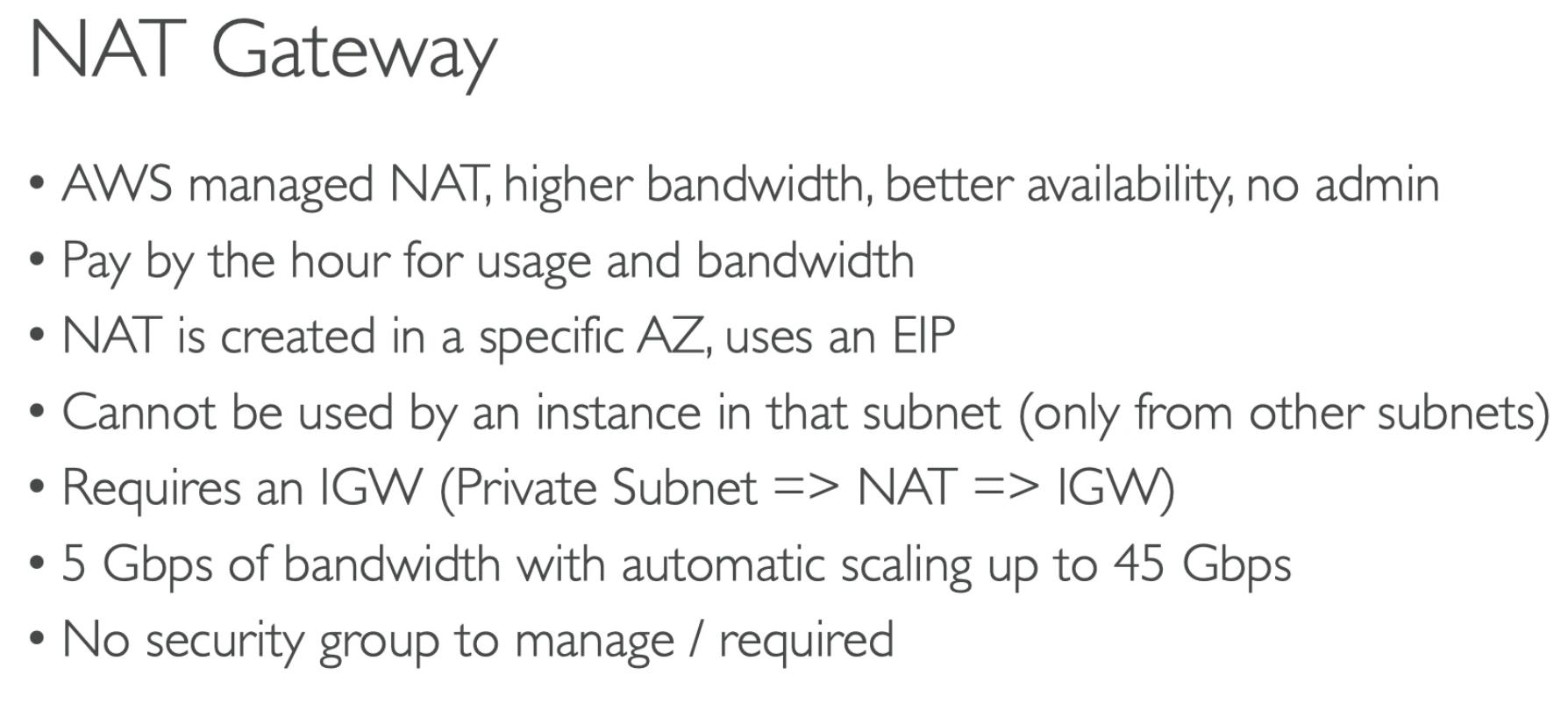
The following is a high-level summary of the differences between NAT gateways and NAT instances. We recommend that you use NAT gateways because they provide better availability and bandwidth and require less effort on your part to administer.
https://docs.aws.amazon.com/vpc/latest/userguide/vpc-nat-comparison.html
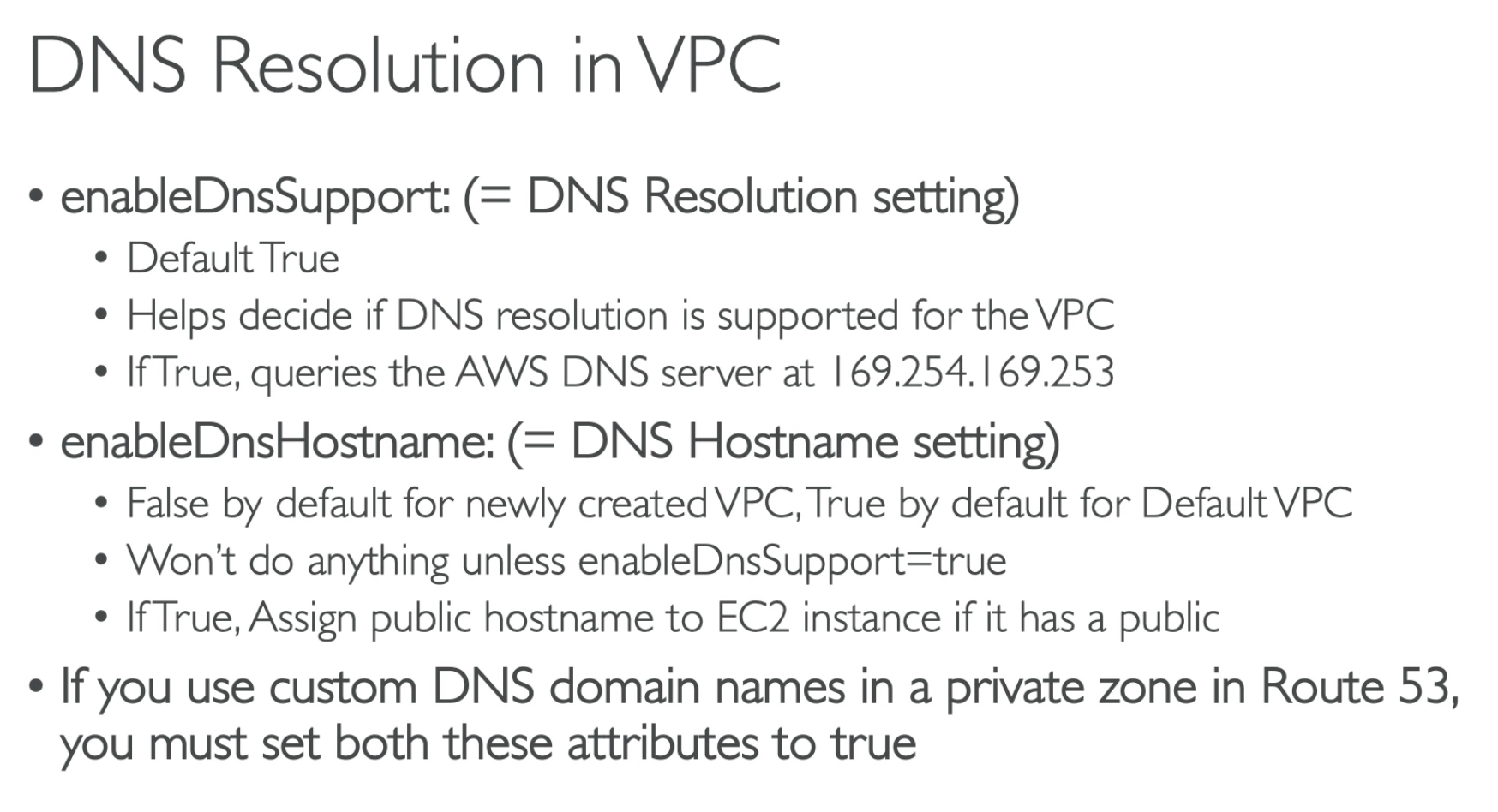
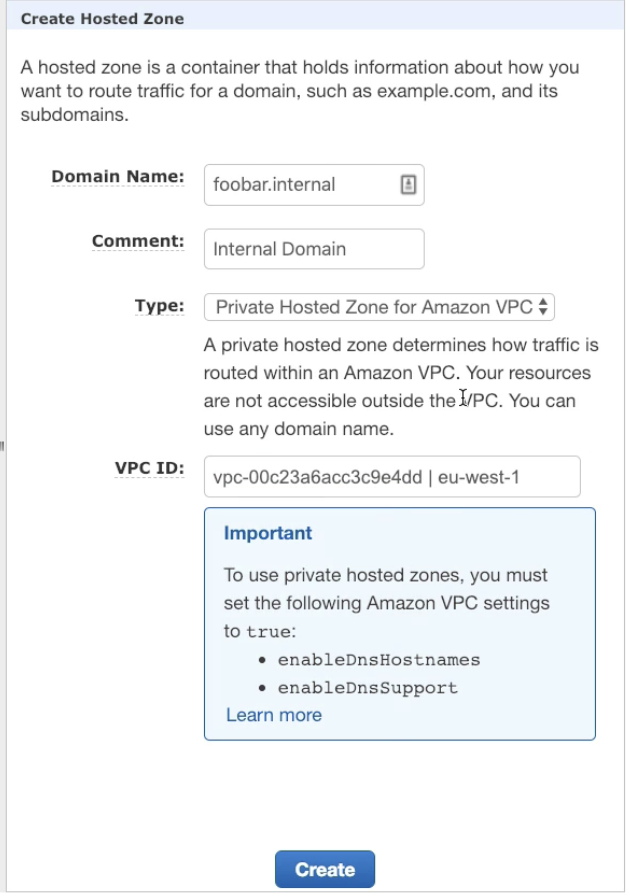
You can create lots of DNS records in your private VPC, and point those to any public IP.
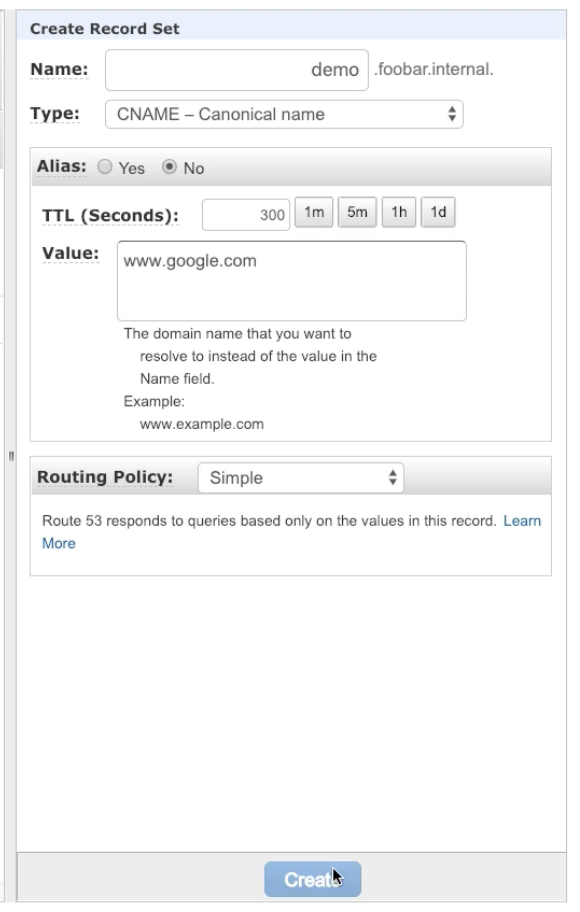
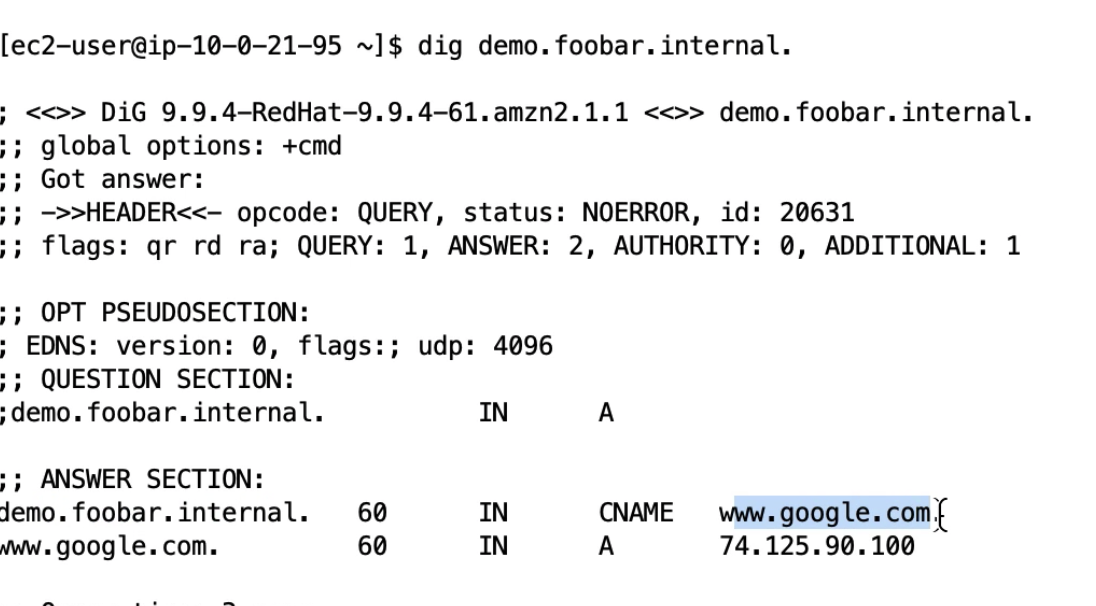

- Lowre rule number wins
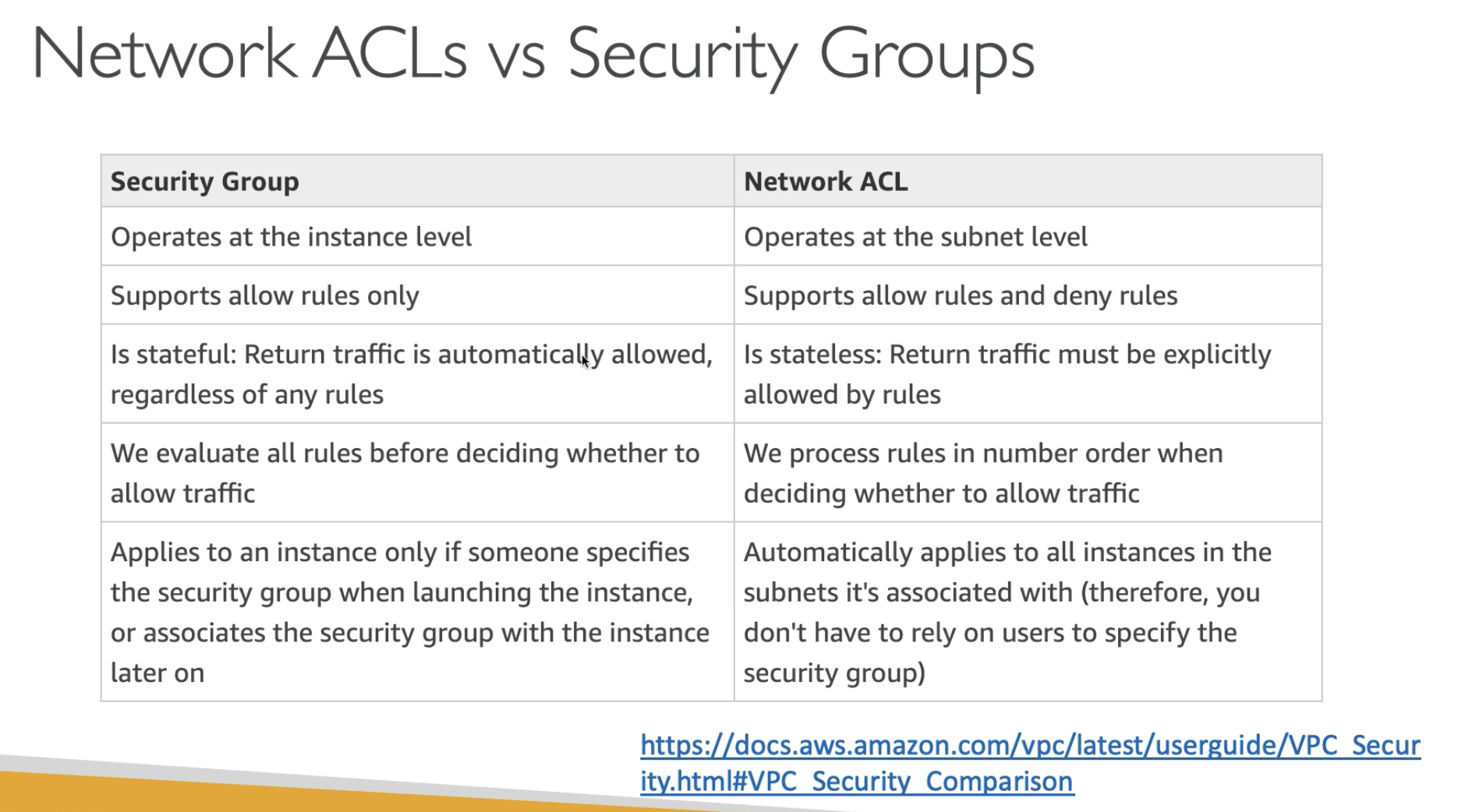
- NACL is stateless, you need to define both inbound and outbound rule
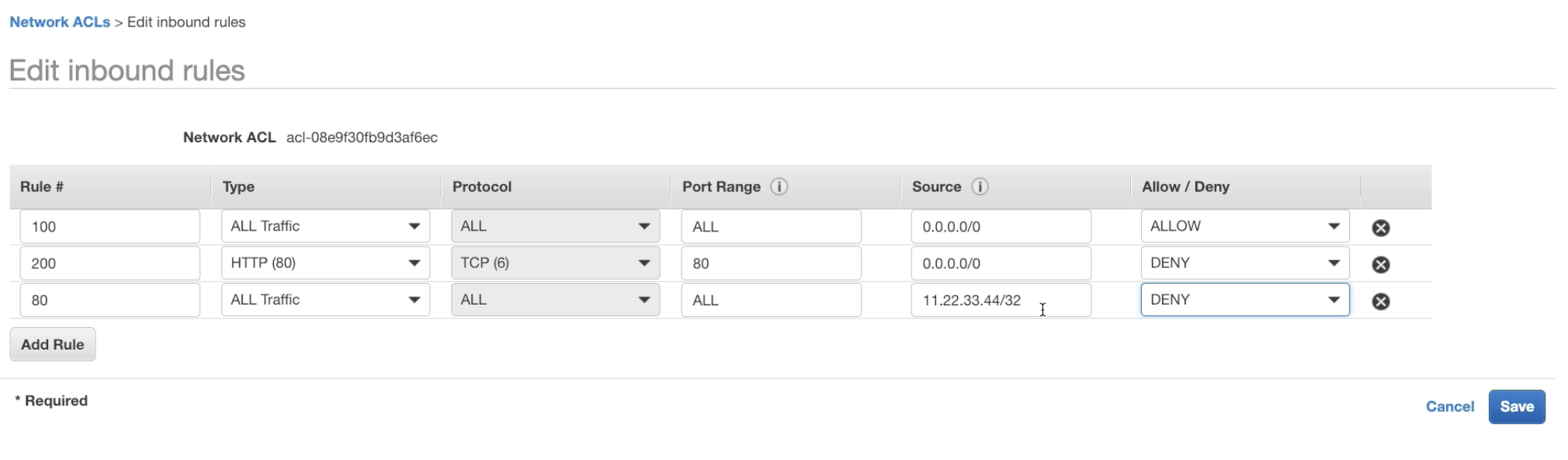
- Because there is 80, deny. so 11.22.33.44/32 range ips won't be able to access
- Even though 100 allow, all addresses.
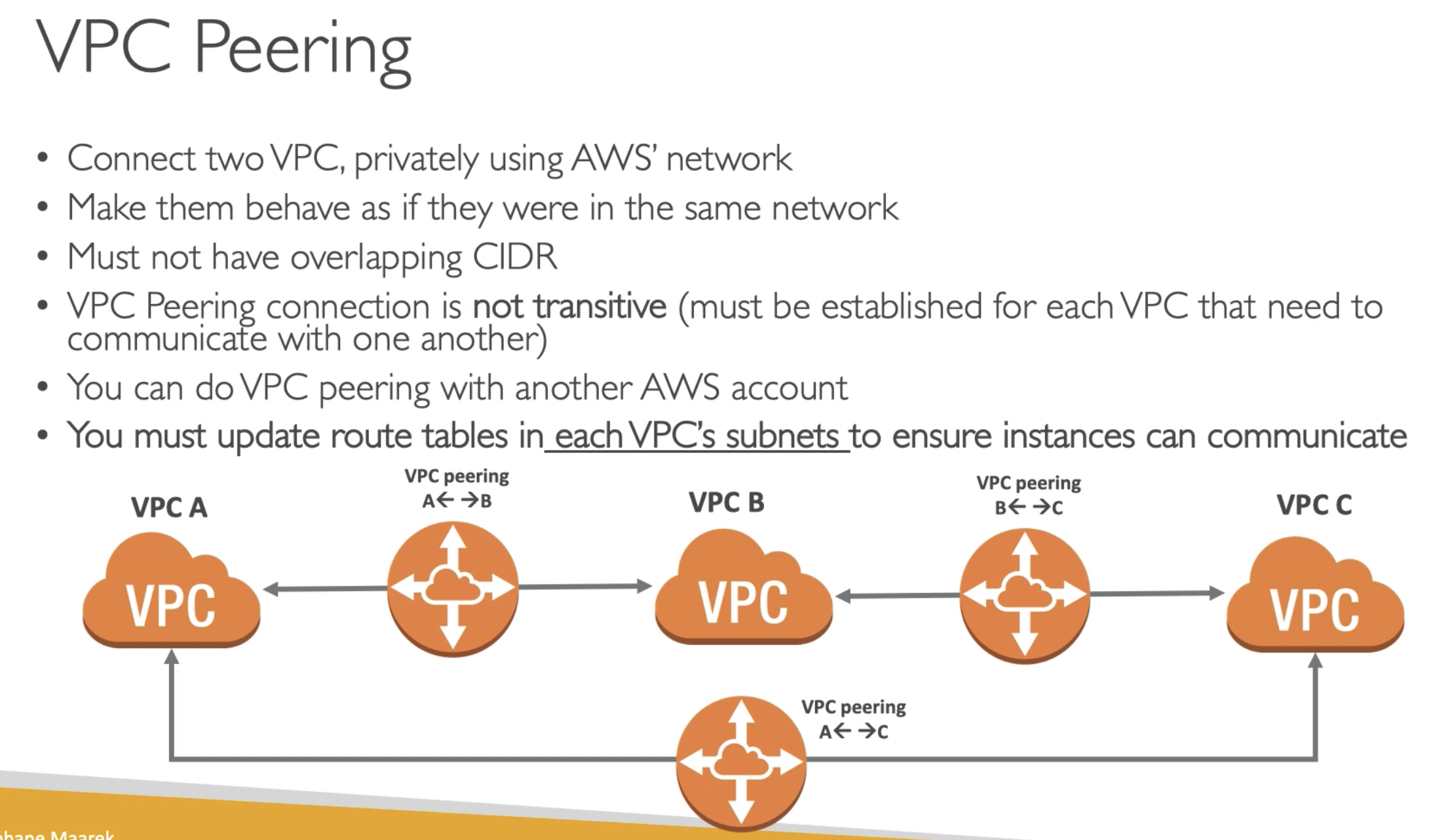
- VPC peering is not transitive, must established for each VPC that need to communicate with one another
- VPC peering with another AWS account
- Route table must be udpated in each VPC subnet
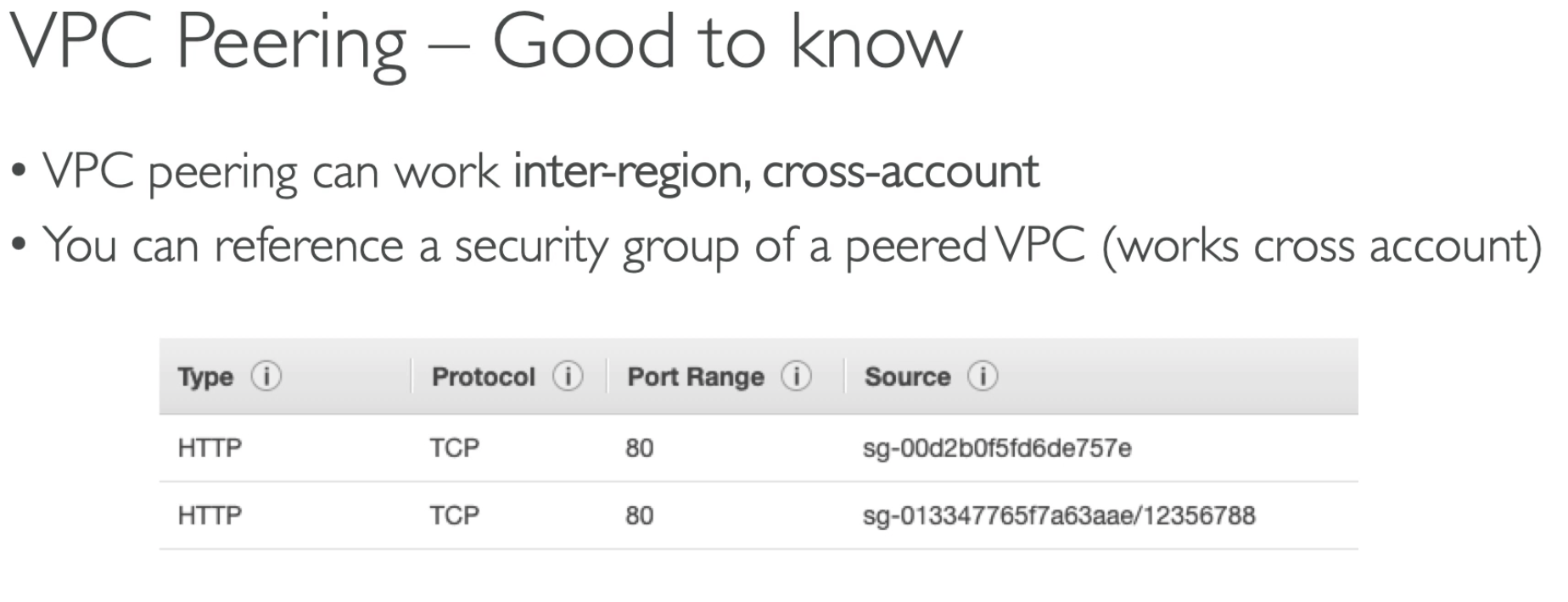
- VPC peering can refer to a Security group
VPC Endpoint
- Endpoints allow you to connect to AWS Service using a private networkinstead of the public www network
- They scale horizontally and are redundant
- They remove the need of IGW, ANT, etc... to access AWS Services
- Interface: provisions ENI (private IP address) as an entry point (must attach security group) - most AWS services
- Gateway: provisions a target and must be used in a route table - S3 and DynamoDB
- In case of issues
- Check DNS Setting Resolution in your VPC
- Check Route Tables
Gateway: for S3 and DynamoDB
Interface: ENI, private network, for most AWS services
Sometimes, if you cannot access S3 by using VPC Endpoint gateway, you need to check the region.

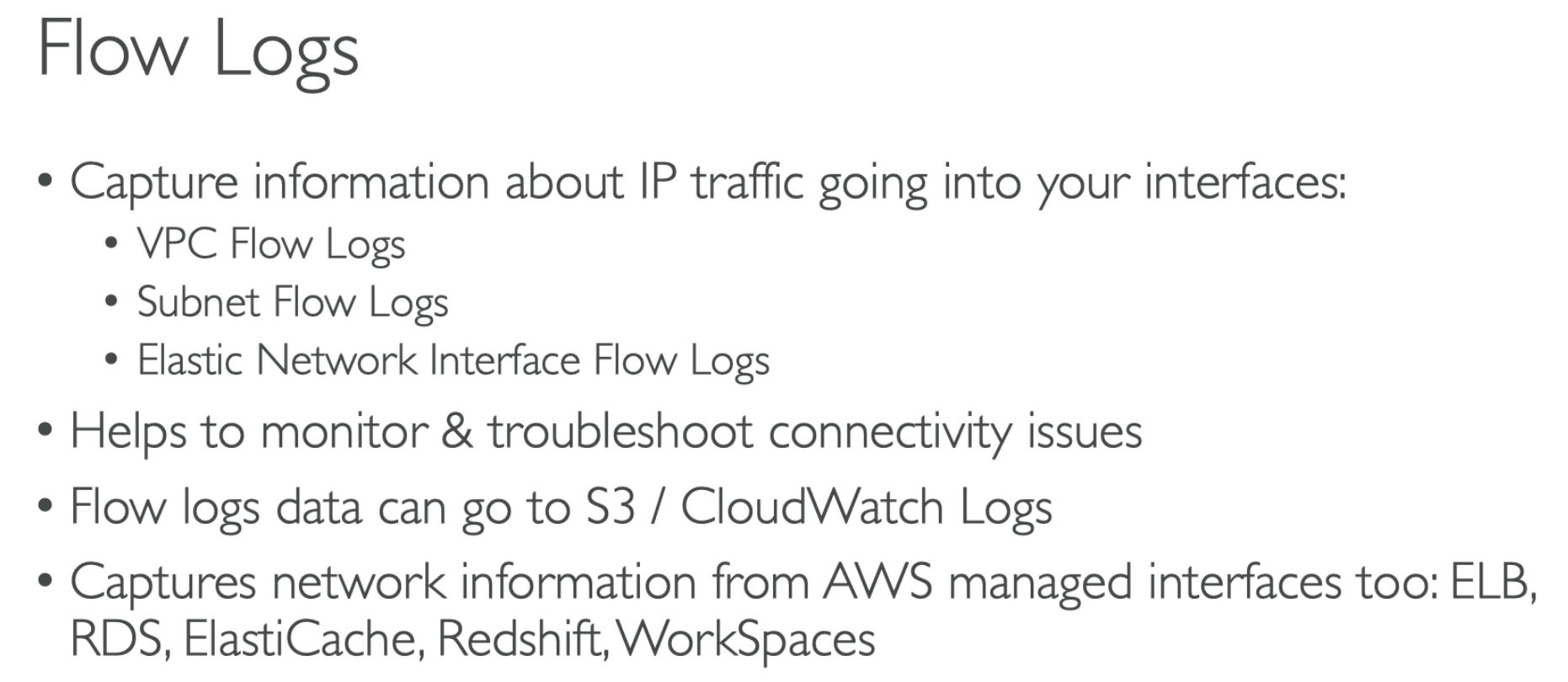
- Anlysis the VPC flow log, can use Athena.
- Logs can goes to CloudWatch and S3

Site to Site VPN, Virtual Private Gateway & Customer Gateway
- AWS Side:
- Virtual Private Gateway
- VPN concetrator on the AWS side of the VPN connection
- VPG is created and attached to the VCP from which you want to create the Site-to-Site connection
- Possibility to customize the ASN
- Virtual Private Gateway
- Customer Side:
- Customer Gateway:
- Software application or pyhsical device on customer side of the VPN connection
- IP address:
- Use static, internet-routeable IP address for your customer gateway device
- if behind a CGW behind NAT, use public IP address of the NAT
- Customer Gateway:
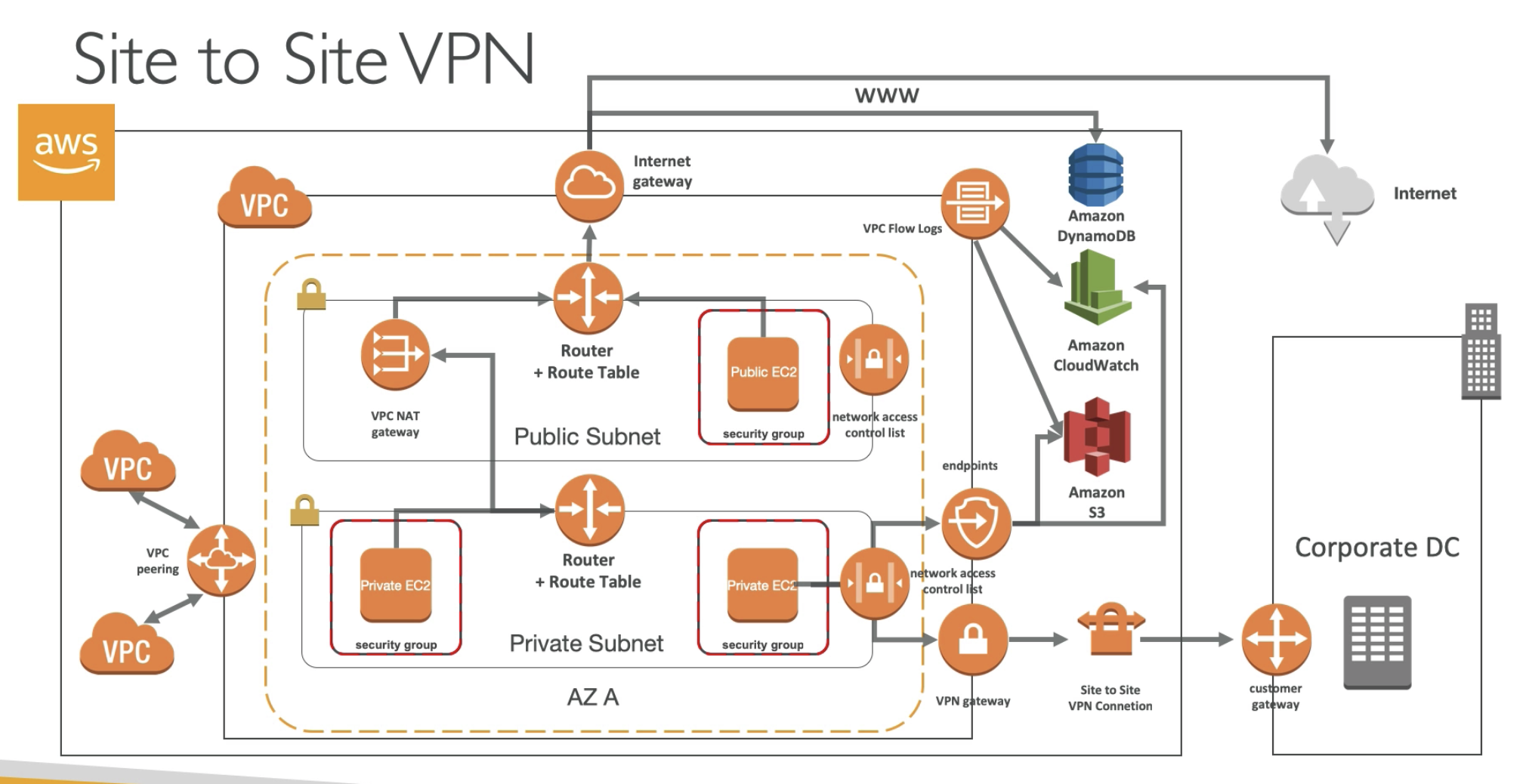
Three things need to be created:
- VPN gateway
- Customer gateway
- Site to Site VPN connection