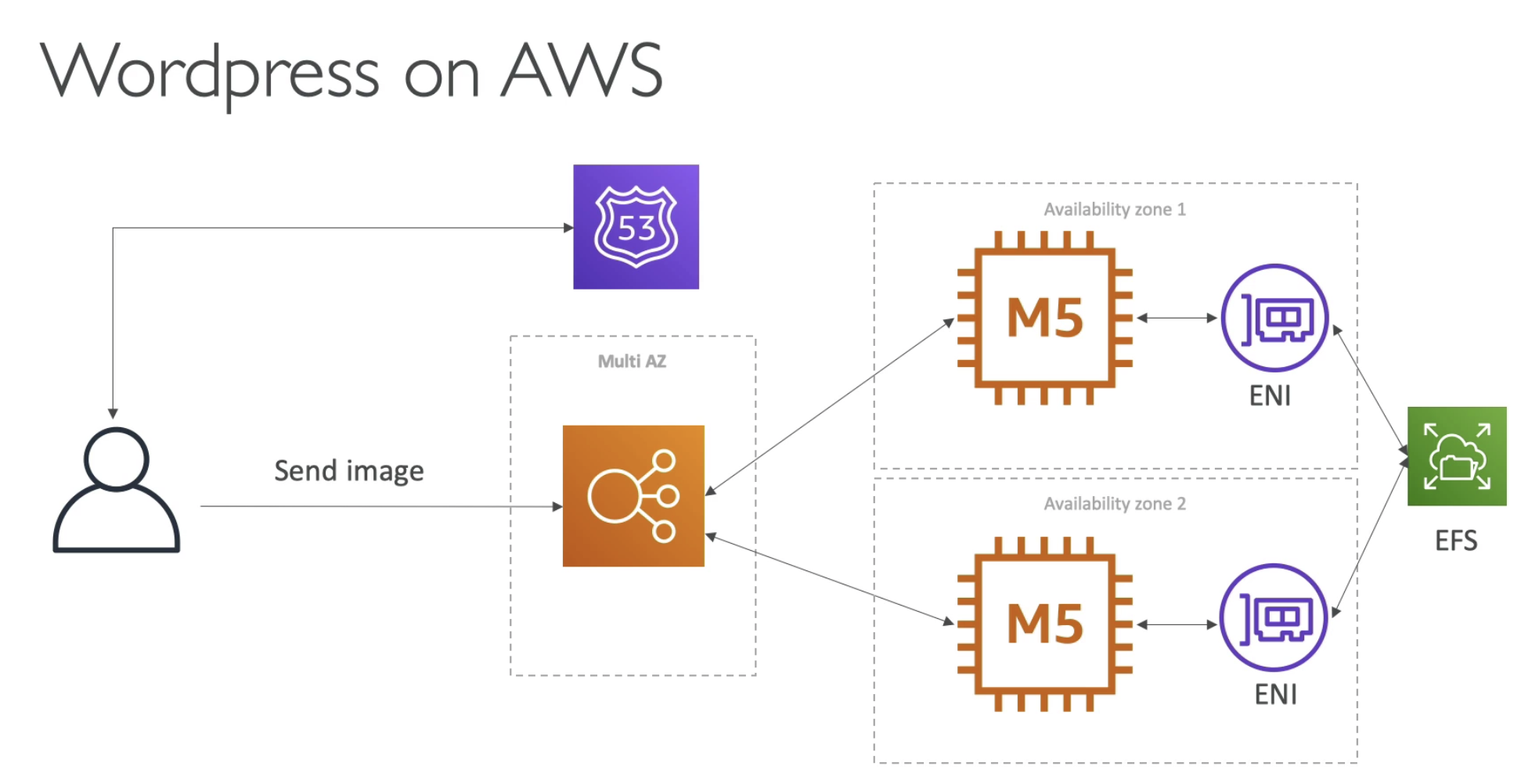
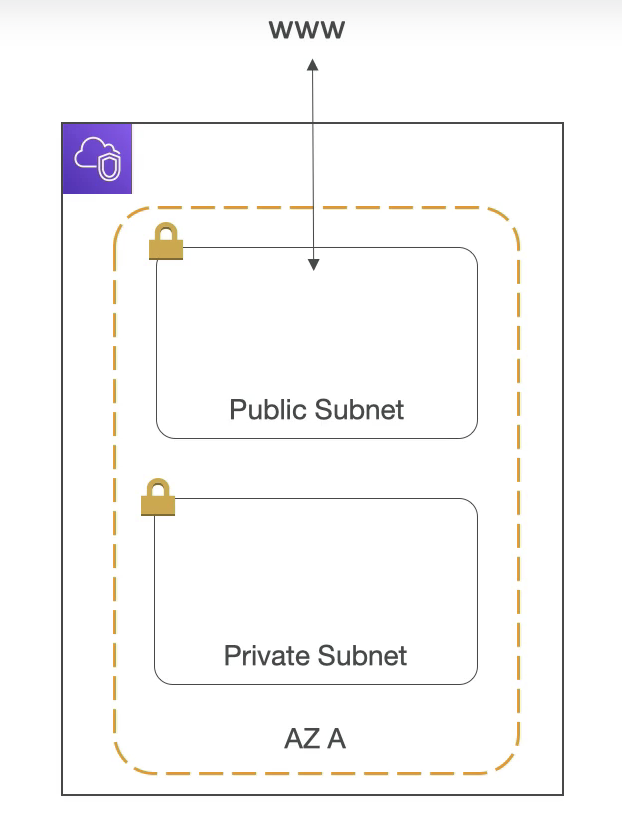
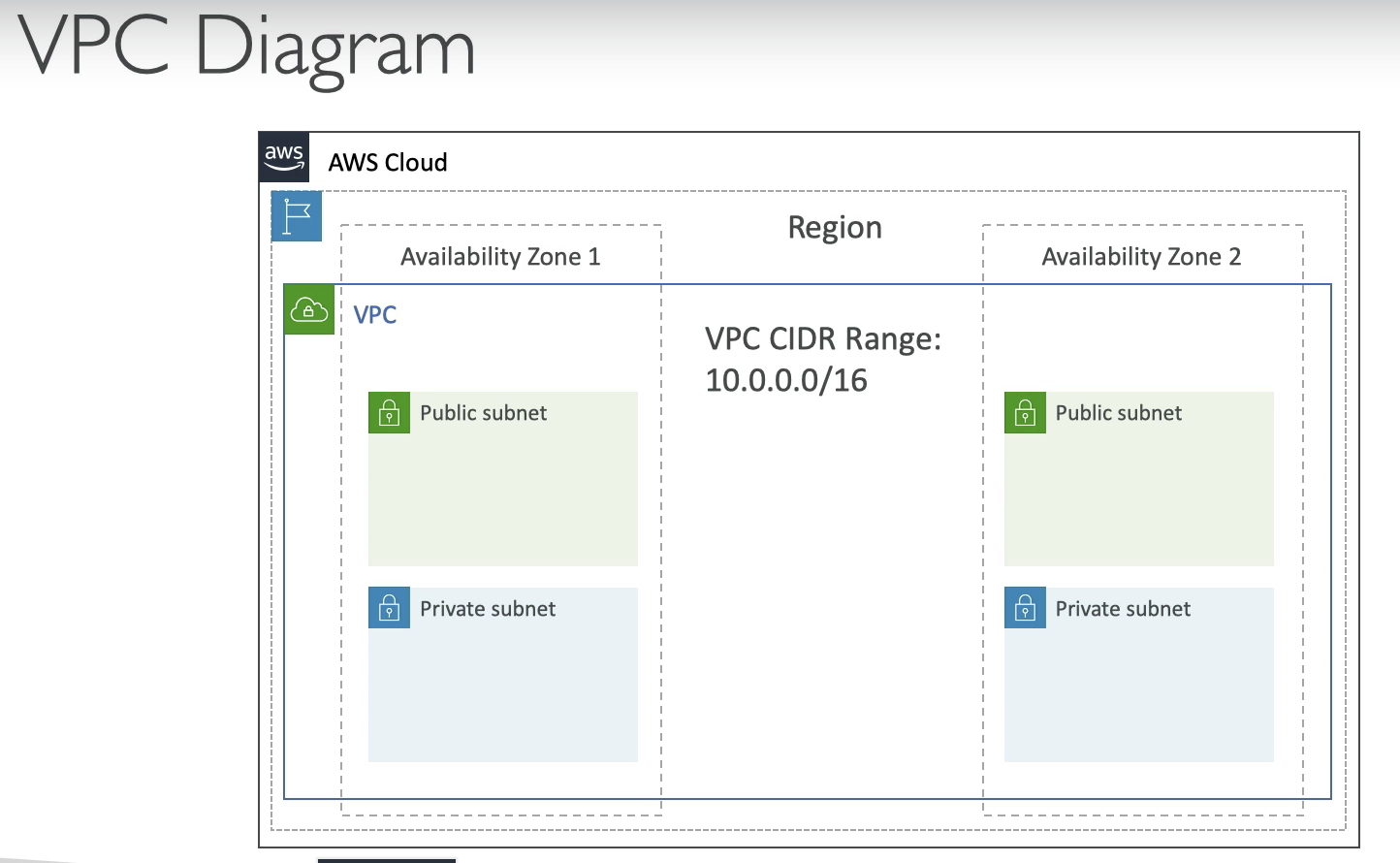
VPC & Subnets
VPC: private network to deploy your resources (regional resource)
Subnets: partition your network inside your VPC (AZ resource)
Public subnet: able to access internet
Private subnet: not able to access internet
To define access to the internet and between subnets, we use Route Tables
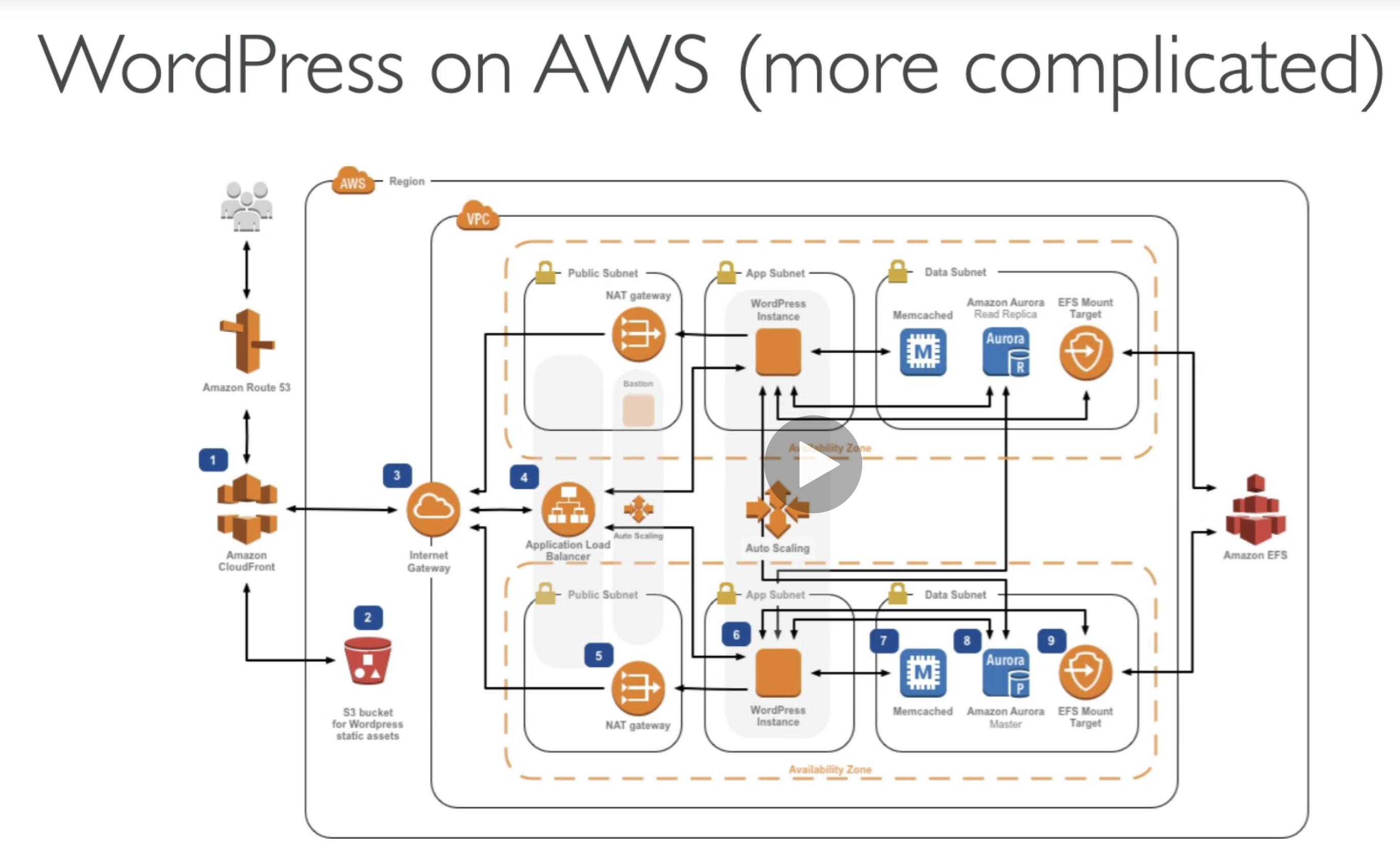
Internet Gateway & NAT Gateways
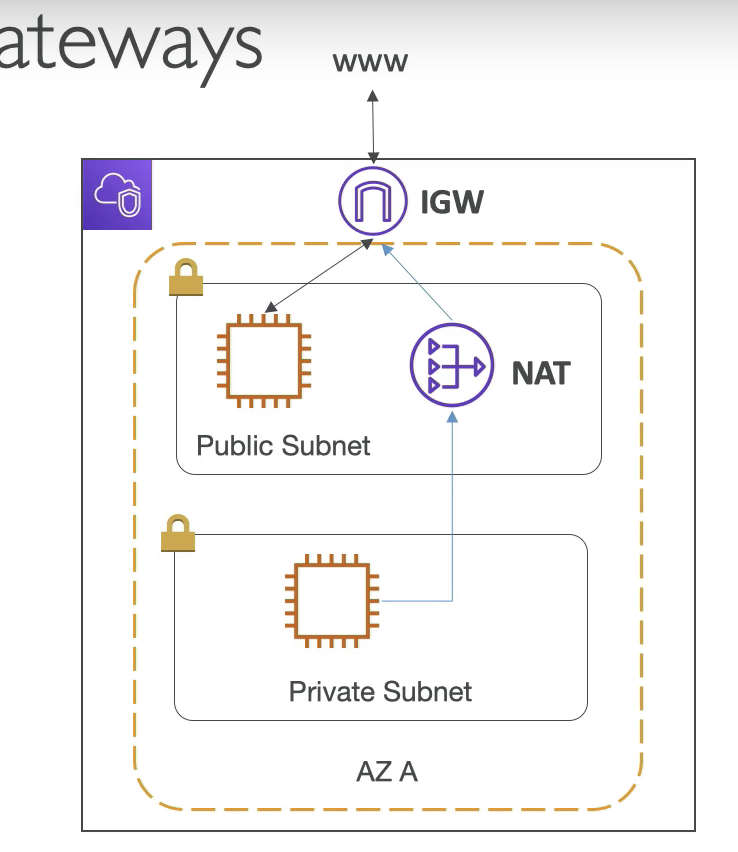
Internet Gateways
Public subnets ables to access internet is because of internet gateways.
Public subnets have a route to the internet gateway.
NAT Gateways
For private gateways, to access internet, we use NAT Gateway / instance.
NAT Gateways (AWS-managed) & NAT instances (self-managed) allow your instances in your Private Subnets to access internet while remaning private.
The way it works is: NAT lives in public subnet and has route to IGW, then private subnet connet to NAT, then it able to access internet,
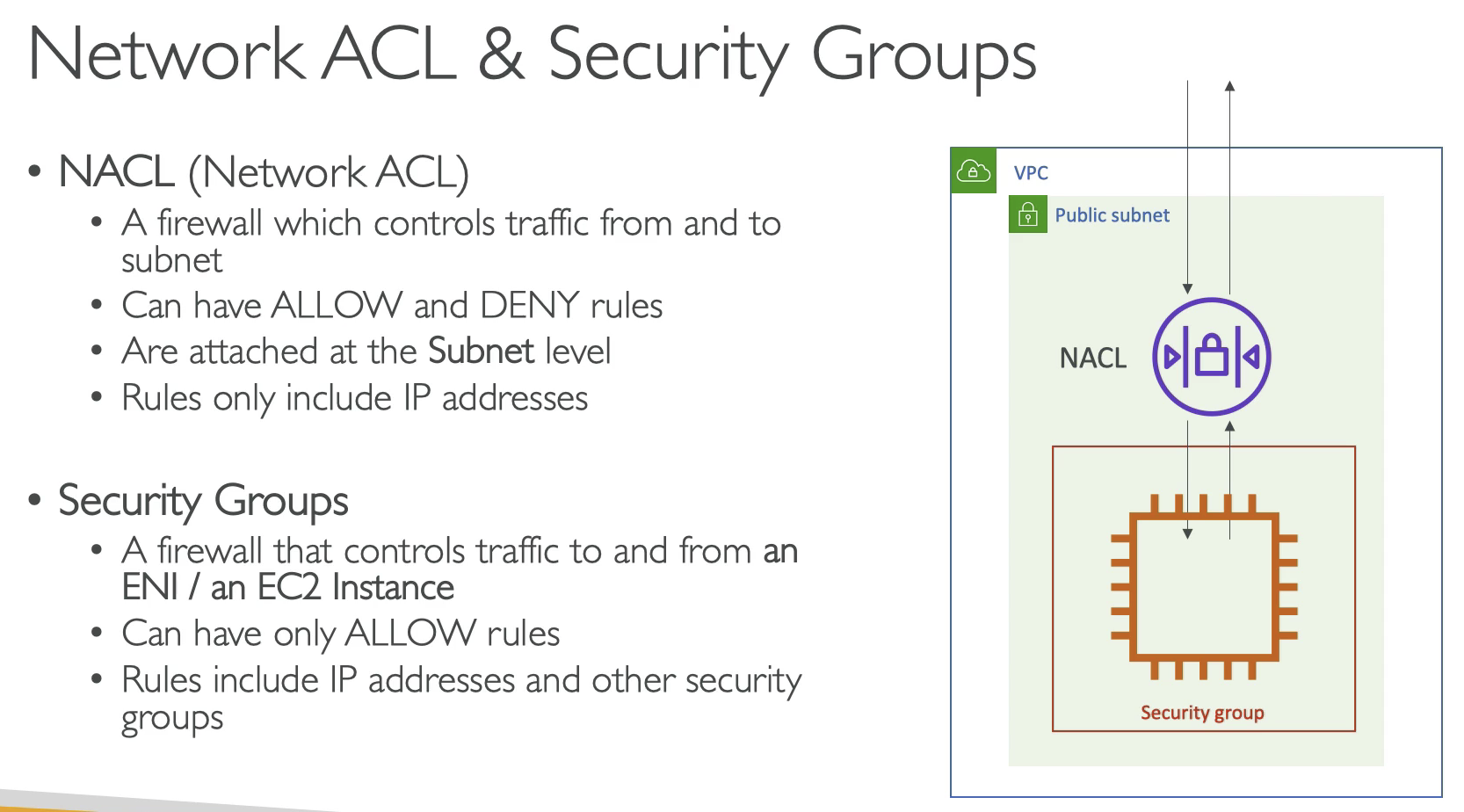
Public subnet has first firewall which is NACL, it can allow and deny traffic from and to subnet.
Security Groups is a firewall for EC2 instance, by default deny all traffic, you need to tell what you want to allow.
Security groups are stateful, you traffic can go out, then it can go back in as well.
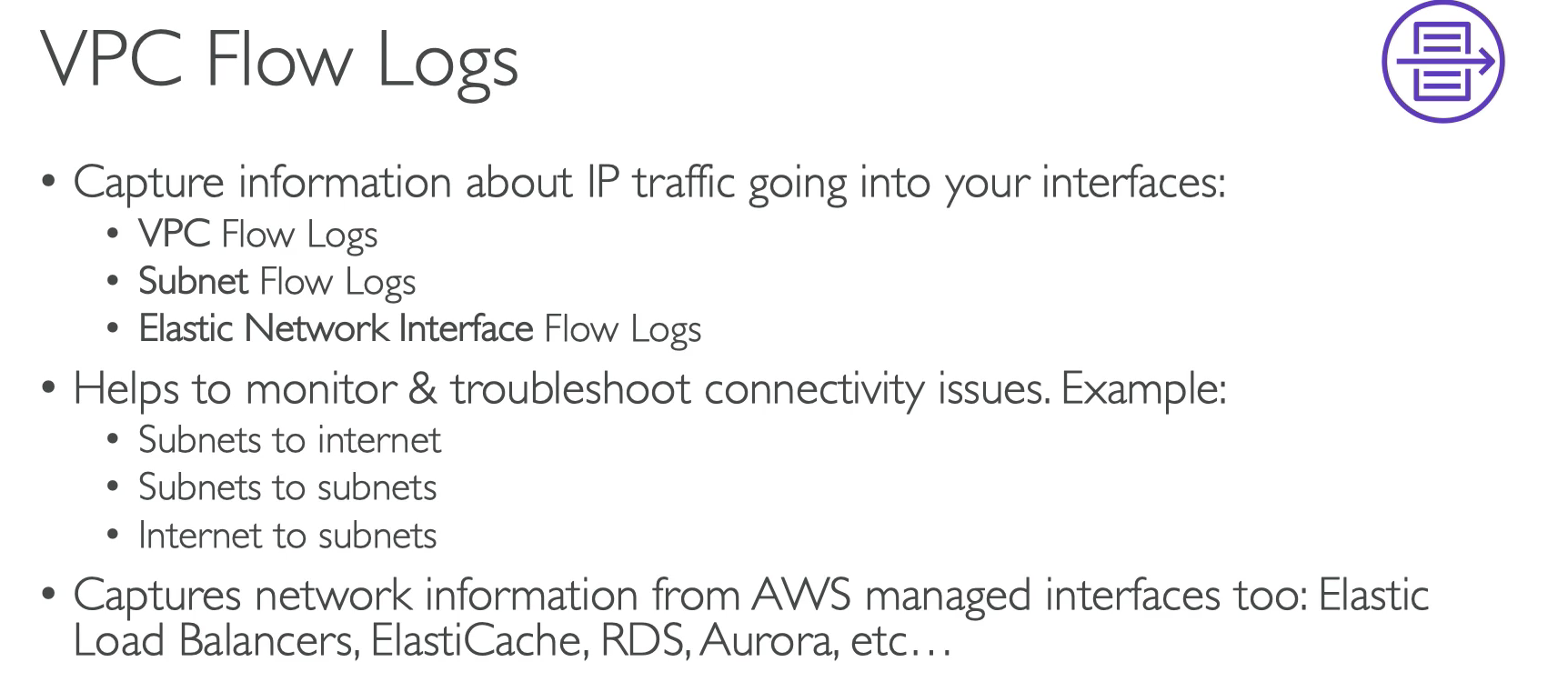
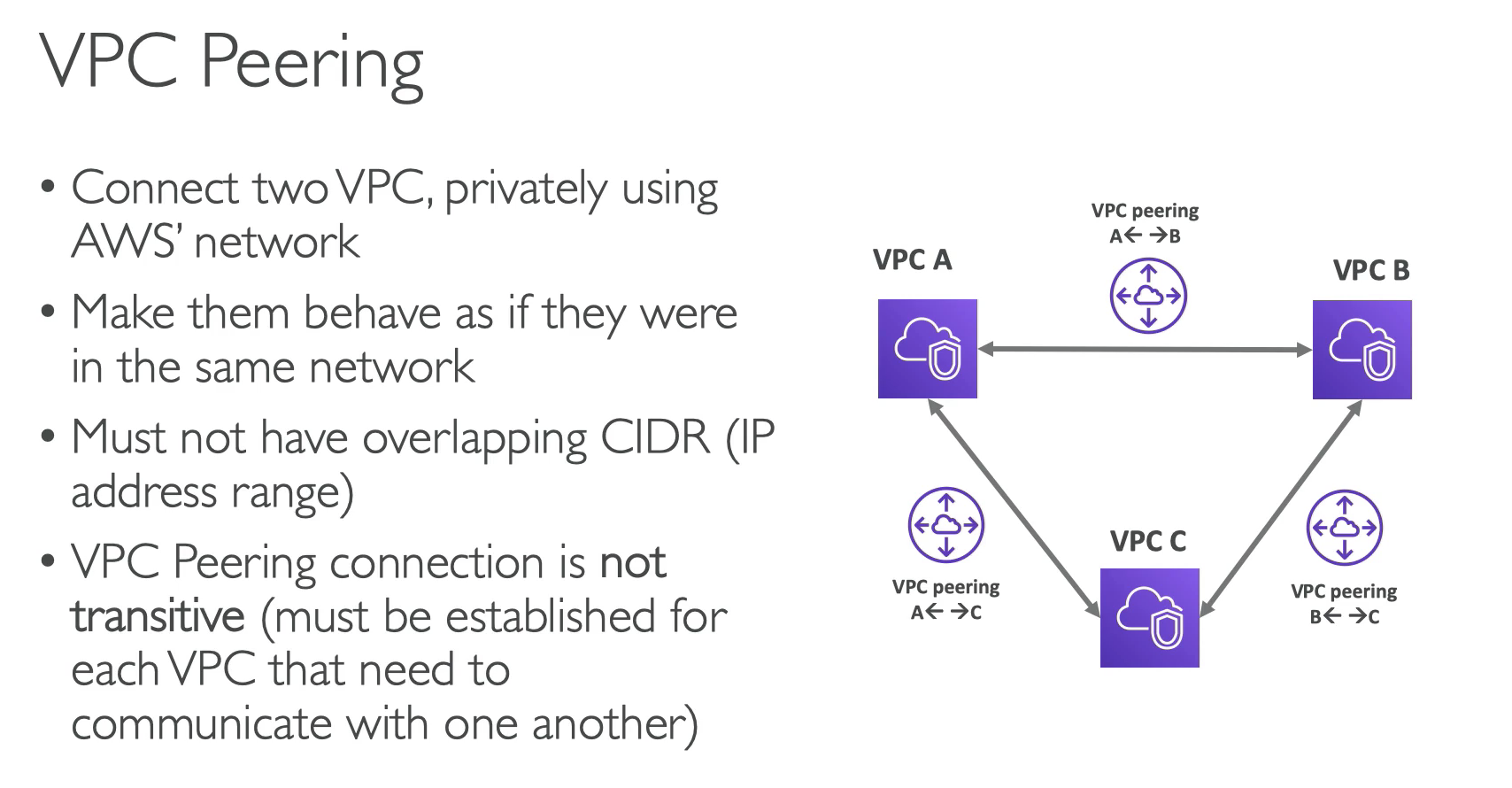
VPC Perring is used for communication between two VCP.
VPC Endpoints
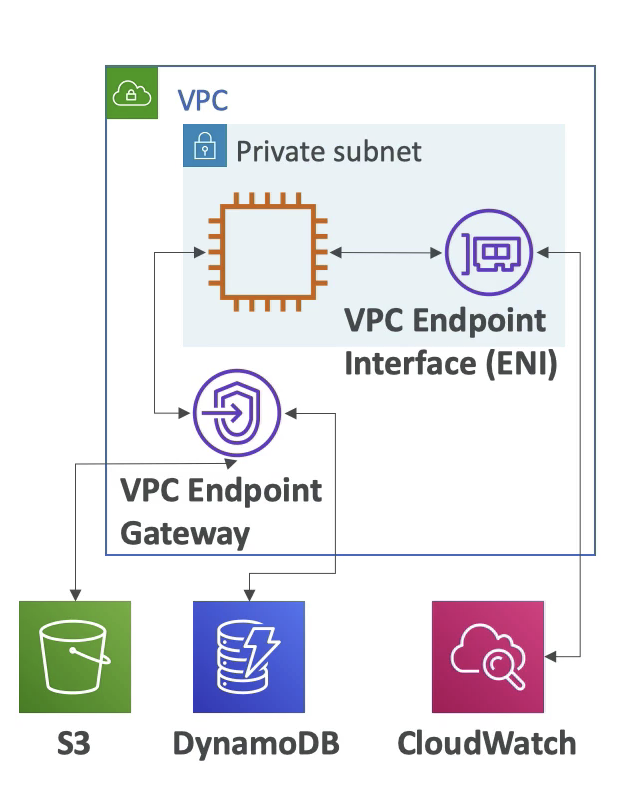
- Endpoints allow you to connect to AWS service using a private network instead of the public www network
- ALl the AWS services are public, any time you use an AWS service, EC2 talks publicly in AWS
- If you want to access S3 or DynamoDB outside VPC, you can use VPC Endpoints Gateway.
- VPC endpoint Gateway: S3 & DyanmoDB Only
- VPC endpoint interface: the rest
- Only used within VPC
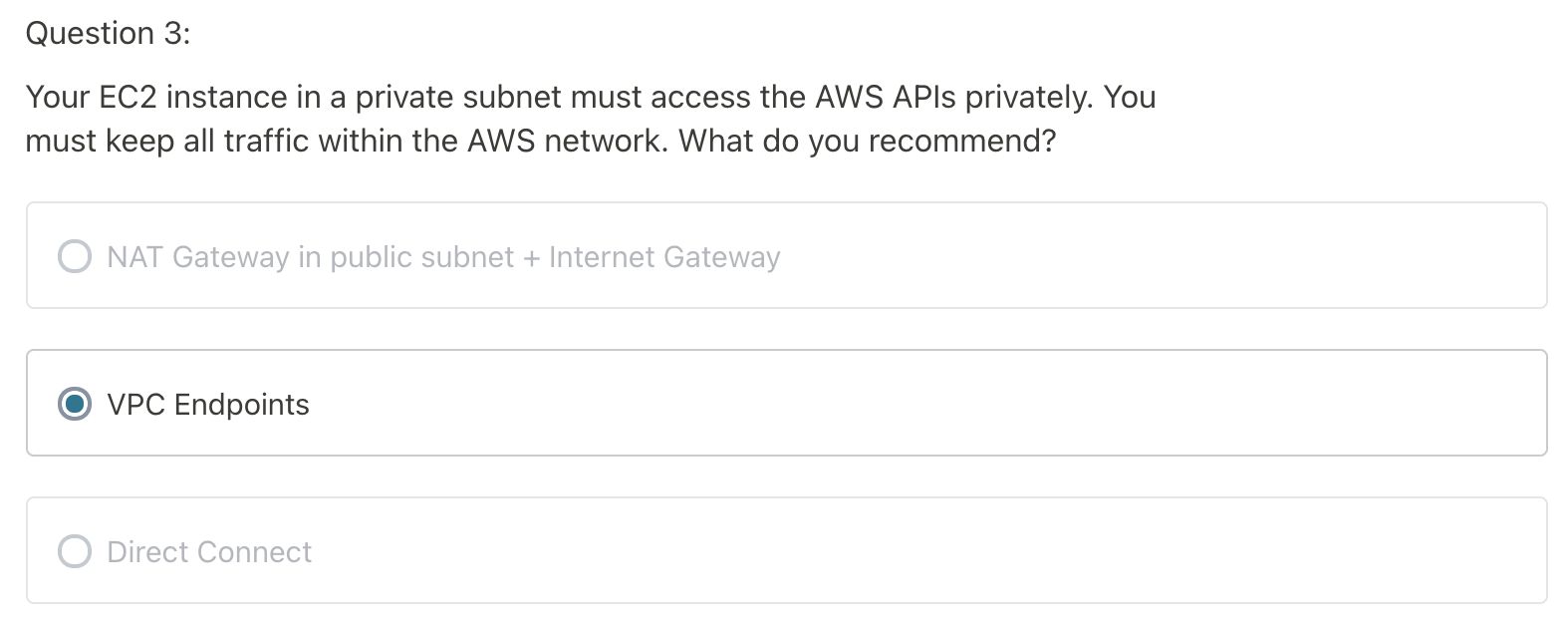
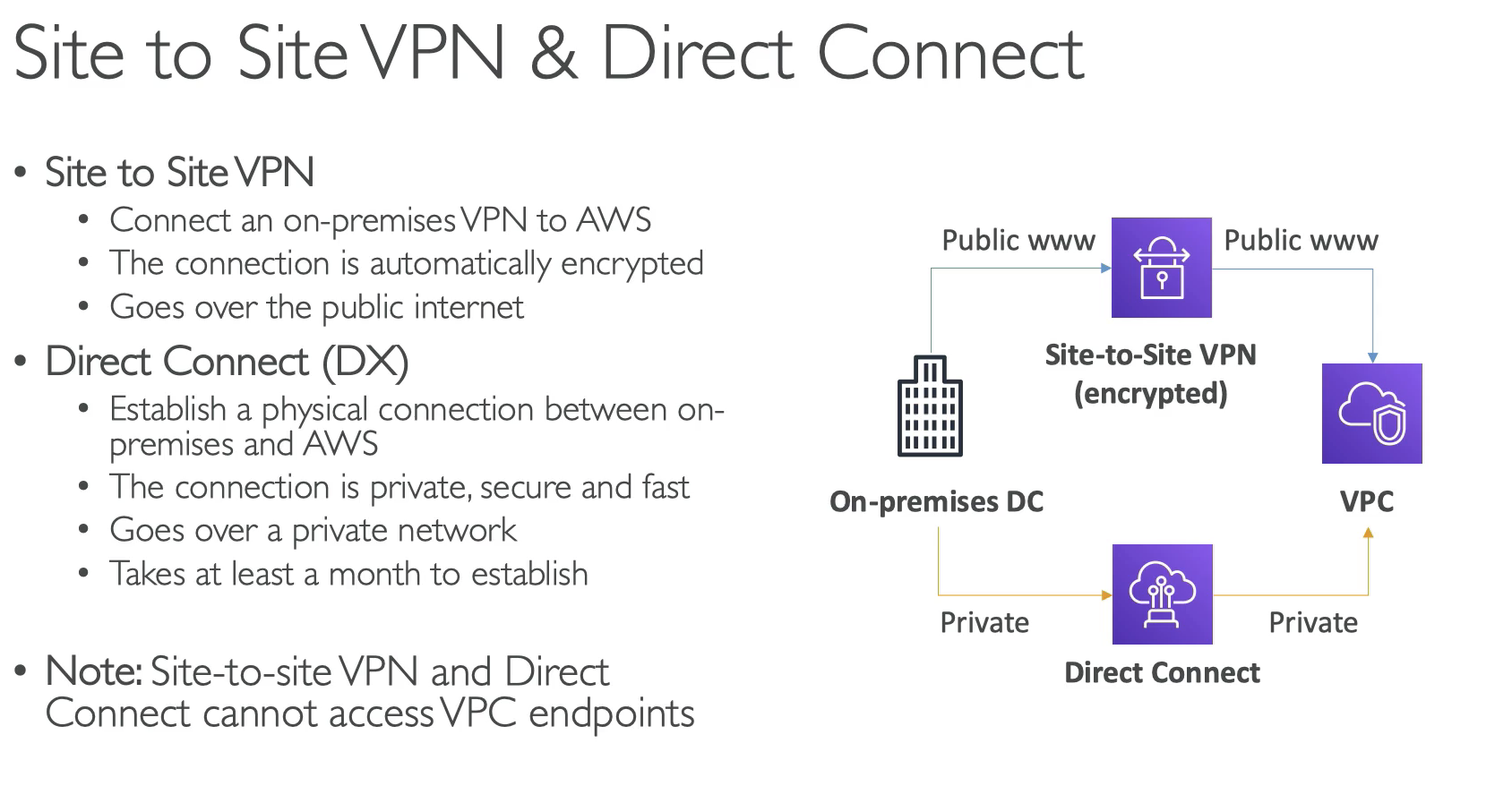
- VPN & DC CANNOT access VPC endpoints. Because VPC endpoint is only for AWS service inside VPC

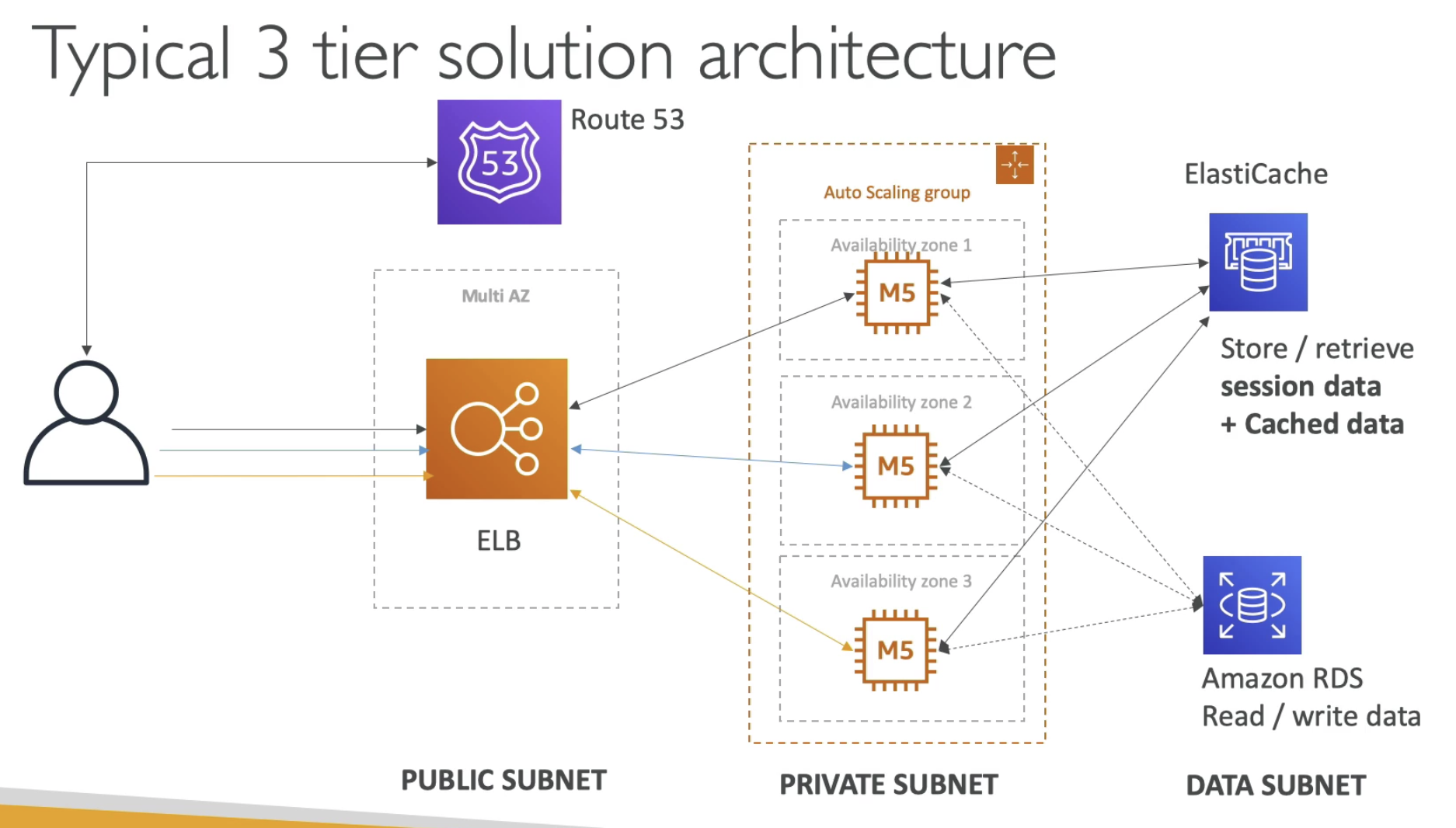
3 tiers:
- Public subnet: ELB, NAT
- Private subnet: ALB, AZ, EC2
- Data Subent: Aurora, RDS, ElastiCache