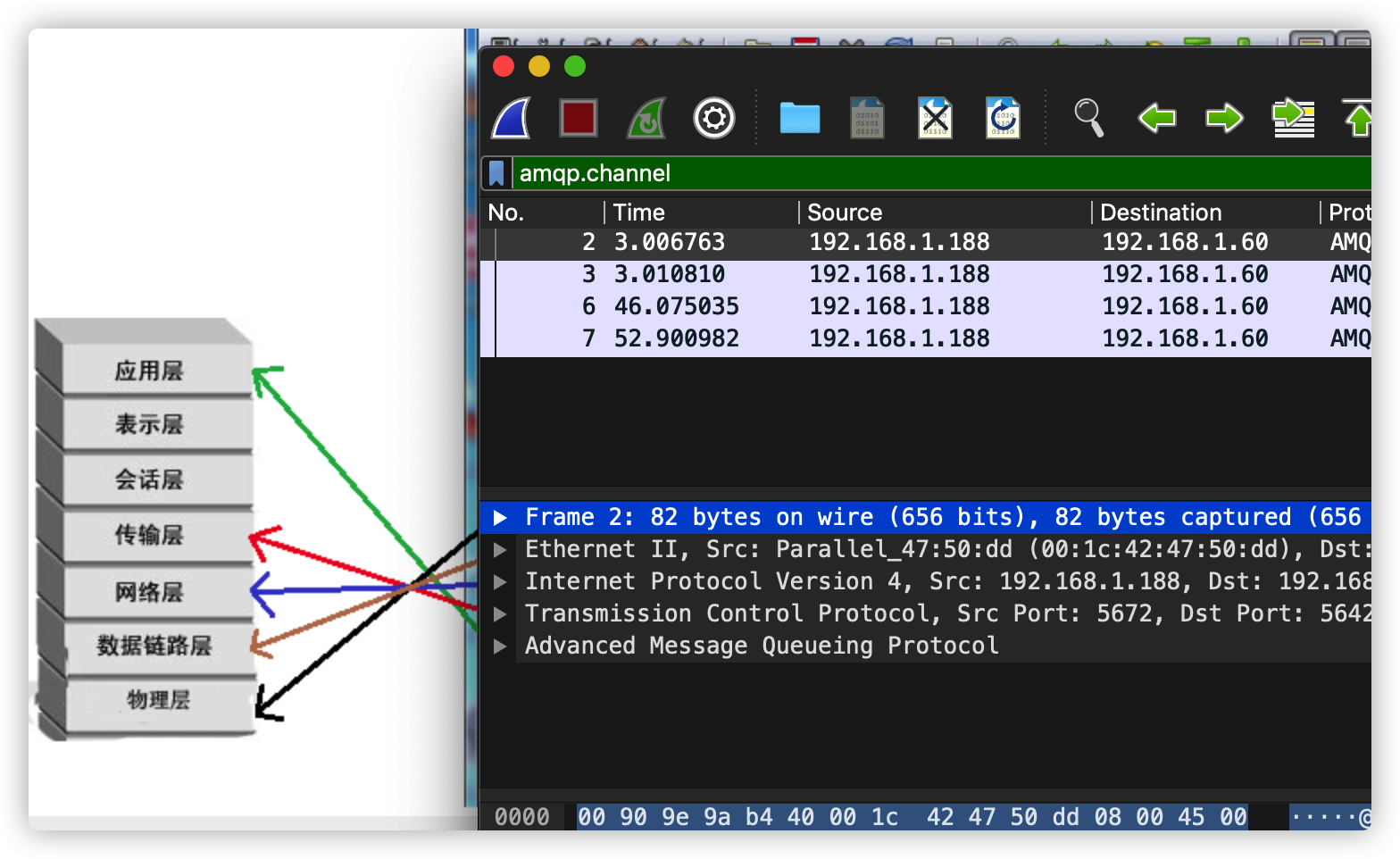
抓包分析
- 启动项目会提示,开启本地一个端口,通过该端口将数据发到 MQ (5672)
2021-08-29 21:03:33.592 INFO 67718 --- [ main] o.s.a.r.c.CachingConnectionFactory : Created new connection: rabbitConnectionFactory#4417af13:0/SimpleConnection@44e93c1f [delegate=amqp://rabbit@192.168.1.188:5672/, localPort= 60934]
Provider: helloSun Aug 29 21:03:58 CST 2021
Consumer: helloSun Aug 29 21:03:58 CST 202
- 使用 tcpdump 抓包分析
seth:~ seth$ sudo tcpdump port 60934
tcpdump: data link type PKTAP
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on pktap, link-type PKTAP (Apple DLT_PKTAP), capture size 262144 bytes
21:03:58.060237 IP 192.168.1.188.amqp > 192.168.1.60.60934: Flags [P.], seq 1561319276:1561319292, ack 371193347, win 506, options [nop,nop,TS val 1505813439 ecr 729215406], length 16
21:03:58.064623 IP 192.168.1.188.amqp > 192.168.1.60.60934: Flags [P.], seq 16:168, ack 115, win 506, options [nop,nop,TS val 1505813443 ecr 729215409], length 152
21:03:58.119393 IP 192.168.1.188.amqp > 192.168.1.60.60934: Flags [.], ack 136, win 506, options [nop,nop,TS val 1505813498 ecr 729215421], length 0
21:04:03.591917 IP 192.168.1.188.amqp > 192.168.1.60.60934: Flags [P.], seq 168:176, ack 136, win 506, options [nop,nop,TS val 1505818970 ecr 729215421], length 8
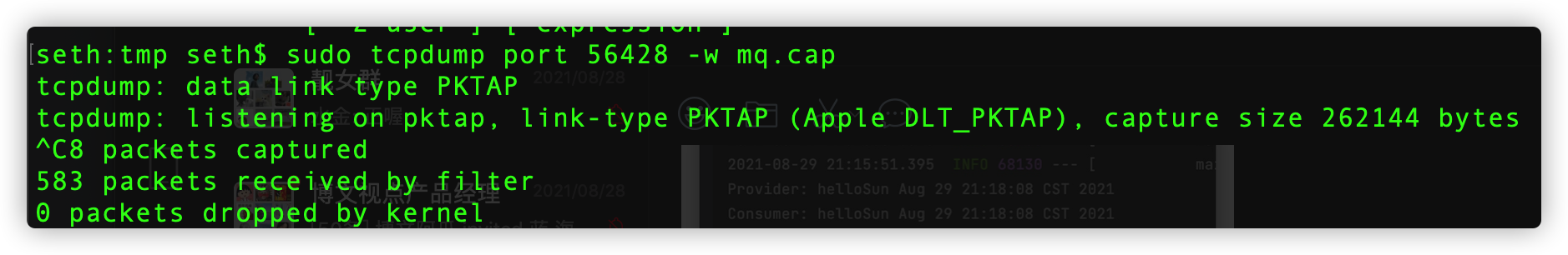
tcpdump + wireshark
提示:-w参数可将抓包数据保存到文件(.cap)中,再用 wireshark 打开,这样分析会更方便快捷
seth:tmp seth$ sudo tcpdump port 56428 -w mq.cap
tcpdump: data link type PKTAP
tcpdump: listening on pktap, link-type PKTAP (Apple DLT_PKTAP), capture size 262144 bytes
^C8 packets captured
583 packets received by filter
0 packets dropped by kernel
完整图片
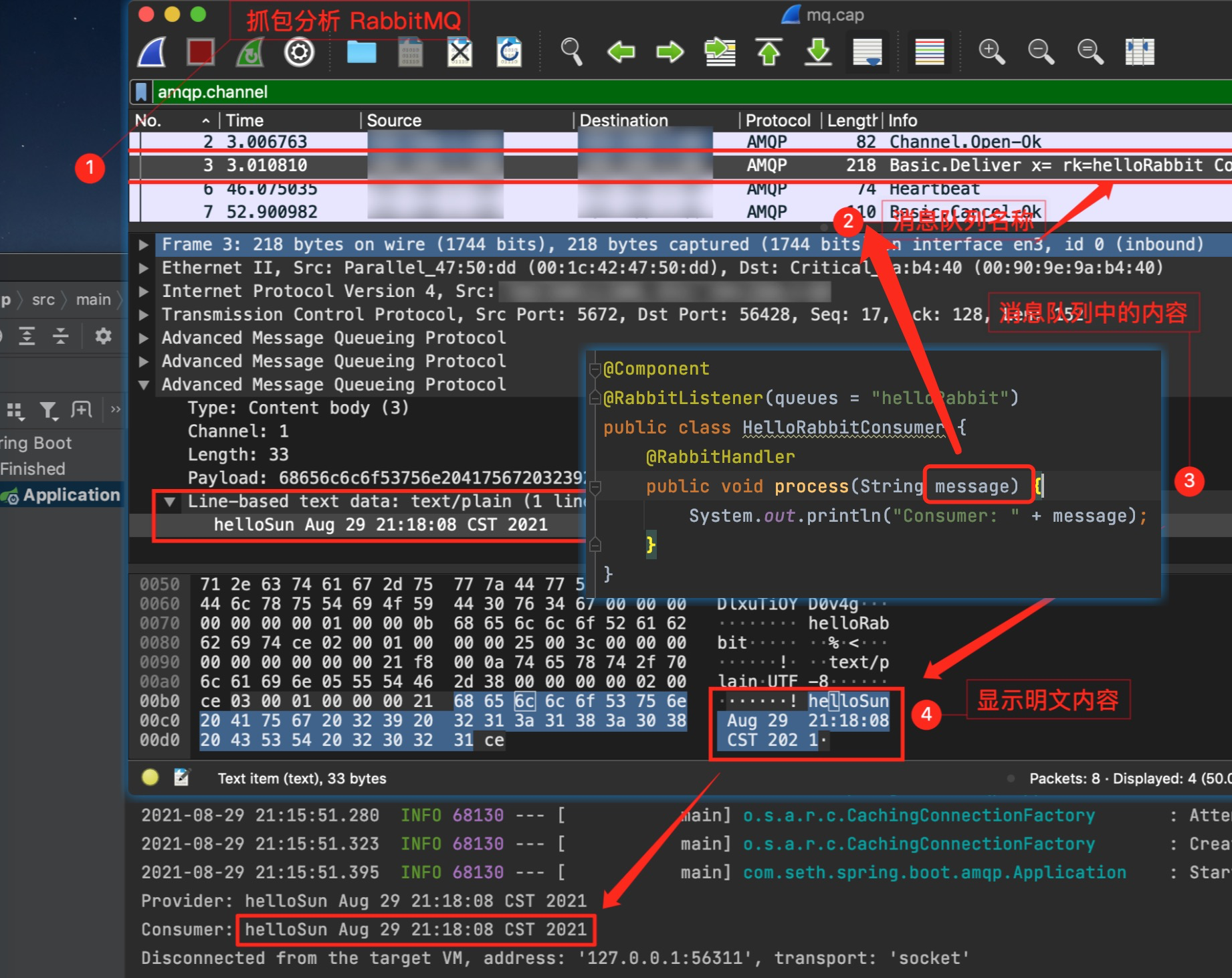
案例
当启动了客户端之后,抓包的窗口中就已经显示了抓到的报文,如下:
17:48:20.202499 IP 127.0.0.1.59466 > 127.0.0.1.8888: Flags [S], seq 3257142365, win 65495, options [mss 65495,sackOK,TS val 1604396091 ecr 0,nop,wscale 7], length 0
17:48:20.202511 IP 127.0.0.1.8888 > 127.0.0.1.59466: Flags [S.], seq 2103221418, ack 3257142366, win 65483, options [mss 65495,sackOK,TS val 1604396091 ecr 1604396091,nop,wscale 7], length 0
17:48:20.202520 IP 127.0.0.1.59466 > 127.0.0.1.8888: Flags [.], ack 1, win 512, options [nop,nop,TS val 1604396091 ecr 1604396091], length 0
说明
- 21:03:58.060237 该数据报文被抓取的系统本地时间戳
IP网络层协议类型,这里是 IPv4,如果是 IPv6 协议,该字段值是 IP6127.0.0.1.59466 > 127.0.0.1.8888源IP:端口和目标IP:端口Flags [S]这是报文的标志位,下文会用表格列出Flag与报文标志位的对应关系seq 3257142365报文的序列号,可以看到这是一个随机数win 65495发送方的窗口大小,窗口大小参考《计算机网络》这门课options [...]这些是选项length 0这是报文中数据部分的长度
Flag与报文标志位的对应关系
| Flag | 标志位 |
|---|---|
| S | SYN |
| . | ACK |
| F | FIN |
| P | PSH |
| R | RST |