内容:端口扫描器—脚本调用参数、多线程扫描、使用Nmap端口扫描代码
环境:python+kali,靶机:win2003
分成五步编写
###############1、脚本调用的参数

import optparse parser = optparse.OptionParser('usage %prog -H <target host> -p <target port>') parser.add_option('-H', dest='tgtHost', type='string', help='specify target host') parser.add_option('-p', dest='tgtPort', type='int', help='specify target port') (options, args) = parser.parse_args() tgtHost = options.tgtHost tgtPort = options.tgtPort if tgtHost == None | tgtPort == None: print(parser.usage) exit(0)
################2、生成connScan和portScan函数

from socket import * def connScan(tgtHost, tgtPort): try: connSkt = socket(AF_INET, SOCK_STREAM) connSkt.connect((tgtHost, tgtPort)) print('[+] %d/tcp open' % tgtPort) connSkt.close() except: print('[-] %d/tcp close' % tgtPort) def portScan(tgtHost, tgtPorts): try: tgtIP = gethostbyname(tgtHost) except: print('[-] Cannot resolve %s:Unknown host' % tgtHost) return try: tgtName = gethostbyaddr(tgtIP) print('[+] Scan Results for: ' + tgtName) except: print('[+] Scan Results for: ' + tgtIP) setdefaulttimeout(1) for tgtPort in tgtPorts: print('Scanning port:' + tgtPort) connScan(tgtHost, int(tgtPort))
#################3、抓取应用的Banner
在connScan函数里面添加新增代码,找到开放的端口后,发送一个字符串等待响应

1 import optparse 2 from socket import * 3 4 def connScan(tgtHost, tgtPort): 5 try: 6 connSkt = socket(AF_INET, SOCK_STREAM) 7 connSkt.connect((tgtHost, tgtPort)) 8 connSkt.send('ViolentPython ') 9 results = connSkt.recv(100) 10 print('[+] %d/tcp open' % tgtPort) 11 #print('[+] retult' , str(results)) 12 connSkt.close() 13 except: 14 print('[-] %d/tcp close' % tgtPort) 15 16 def portScan(tgtHost, tgtPorts): 17 try: 18 tgtIP = gethostbyname(tgtHost) 19 except: 20 print('[-] Cannot resolve %s:Unknown host' % tgtHost) 21 return 22 try: 23 tgtName = gethostbyaddr(tgtIP) 24 print('[+] Scan Results for: ' + tgtName) 25 except: 26 print('[+] Scan Results for: ' + tgtIP) 27 setdefaulttimeout(1) 28 for tgtPort in tgtPorts: 29 print('Scanning port:' + tgtPort) 30 connScan(tgtHost, int(tgtPort)) 31 32 def main(): 33 parser = optparse.OptionParser('usage %prog -H <target host> -p <target port>') 34 parser.add_option('-H', dest='tgtHost', type='string', help='specify target host') 35 parser.add_option('-p', dest='tgtPort', type='string', help='specify target port') 36 (options, args) = parser.parse_args() 37 tgtHost = options.tgtHost 38 tgtPort = options.tgtPort 39 tgtPorts = str(tgtPort).split(',') 40 if tgtHost == None or tgtPort== None: 41 print(parser.usage) 42 print('[-] you must specify a target host and port[s]') 43 exit(0) 44 portScan(tgtHost,tgtPorts) 45 46 if __name__ == '__main__': 47 main()
在这里已经可以通过调用脚本的形式执行
在终端执行的命令:root@HuaHong:~/python_hacker/chap2/端口扫描器# python port_scanner.py -H 192.168.10.142 -p 80,21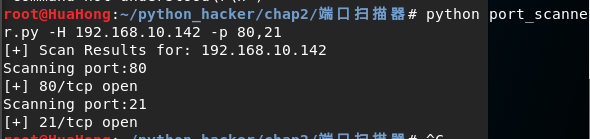
要注意的就是逗号不要是中文,很多人会注意,当然也有人没有注意
或者在python代码里面和这里保持一致,我觉得用英文的逗号就行了。
####################4、线程扫描

1 import optparse 2 3 from socket import * 4 from threading import Thread,Semaphore 5 6 screenLock = Semaphore(1) 7 def connScan(tgtHost, tgtPort): 8 try: 9 connSkt = socket(AF_INET, SOCK_STREAM) 10 connSkt.connect((tgtHost, tgtPort)) 11 connSkt.send('ViolentPython ') 12 results = connSkt.recv(100) 13 screenLock.acquire() 14 print('[+] %d/tcp open' % tgtPort) 15 print('[+] retult' , str(results)) 16 connSkt.close() 17 except: 18 screenLock.acquire() 19 print('[-] %d/tcp close' % tgtPort) 20 finally: 21 screenLock.release() 22 connSkt.close() 23 24 def portScan(tgtHost, tgtPorts): 25 try: 26 tgtIP = gethostbyname(tgtHost) 27 except: 28 print('[-] Cannot resolve %s:Unknown host' % tgtHost) 29 return 30 try: 31 tgtName = gethostbyaddr(tgtIP) 32 print('[+] Scan Results for: ' + tgtName) 33 except: 34 print('[+] Scan Results for: ' + tgtIP) 35 setdefaulttimeout(1) 36 for tgtPort in tgtPorts: 37 # print('Scanning port:' + tgtPort) 38 # connScan(tgtHost, int(tgtPort)) 39 t = Thread(target=connScan, args=(tgtHost,int(tgtPort))) 40 t.start() 41 42 def main(): 43 parser = optparse.OptionParser('usage %prog -H <target host> -p <target port>') 44 parser.add_option('-H', dest='tgtHost', type='string', help='specify target host') 45 parser.add_option('-p', dest='tgtPort', type='string', help='specify target port') 46 (options, args) = parser.parse_args() 47 tgtHost = options.tgtHost 48 tgtPort = options.tgtPort 49 tgtPorts = str(tgtPort).split(',') 50 if tgtHost == None or tgtPorts[0] == None: 51 print(parser.usage) 52 print('[-] you must specify a target host and port[s]') 53 exit(0) 54 portScan(tgtHost,tgtPorts) 55 56 if __name__ == '__main__': 57 main()
这里使用多线程扫描提高了速率,并且加入了信号量。
在使用信号量前要导入
测试结果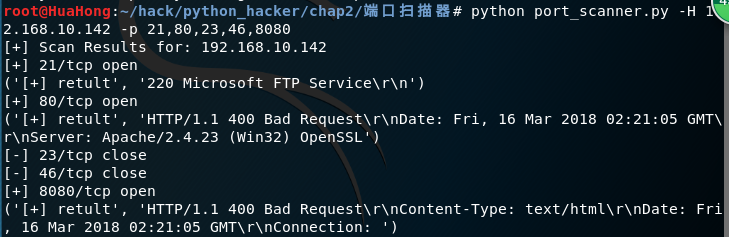
########################5使用Nmap端口扫描代码
在使用Nmap之前要安装python-nmap
我电脑kali默认就有

1 # __author: _nbloser 2 # date: 18-3-16 3 4 import nmap 5 import optparse 6 7 8 def nmapScan(tgtHost, tgtPort): 9 nmScan = nmap.PortScanner() 10 nmScan.scan(tgtHost, tgtPort) 11 state = nmScan[tgtHost]['tcp'][int(tgtPort)]['state'] 12 print("[*]" + tgtHost + " tcp/" + tgtPort + ' ' + state) 13 14 def main(): 15 parser = optparse.OptionParser('usage %prog -H <target host> -p <target port>') 16 parser.add_option('-H', dest='tgtHost', type='string', help='specify target host') 17 parser.add_option('-p', dest='tgtPort', type='string', help='specify target port') 18 (options, args) = parser.parse_args() 19 tgtHost = options.tgtHost 20 tgtPort = options.tgtPort 21 tgtPorts = str(tgtPort).split(',') 22 if tgtHost == None or tgtPorts[0] == None: 23 print(parser.usage) 24 print('[-] you must specify a target host and port[s]') 25 exit(0) 26 for tgtPort in tgtPorts: 27 nmapScan(tgtHost, tgtPort) 28 29 30 if __name__ == '__main__': 31 main()
执行结果,执行会比较慢点

nmap调用核心代码:
def nmapScan(tgtHost, tgtPort): nmScan = nmap.PortScanner() nmScan.scan(tgtHost, tgtPort) state = nmScan[tgtHost]['tcp'][int(tgtPort)]['state'] print("[*]" + tgtHost + " tcp/" + tgtPort + ' ' + state)
步骤:1)获取相应扫描对象
2)扫描
3)获取结果
