kali是黑客的强大武器,还有一个也是哦——Metasploit
postgreSQL数据库是Metasploit的默认数据库哦!
启动postgresql:
service postgresql start
既然postgresql是配合Metasploit框架的,那么也要启动Metasploit:
kali > msfconsole

root@kali:~# service postgresql start root@kali:~# msfconsole [-] ***rting the Metasploit Framework console...| [-] * WARNING: No database support: No database YAML file [-] *** Unable to handle kernel NULL pointer dereference at virtual address 0xd34db33f EFLAGS: 00010046 eax: 00000001 ebx: f77c8c00 ecx: 00000000 edx: f77f0001 esi: 803bf014 edi: 8023c755 ebp: 80237f84 esp: 80237f60 ds: 0018 es: 0018 ss: 0018 Process Swapper (Pid: 0, process nr: 0, stackpage=80377000) Stack: 90909090990909090990909090 90909090990909090990909090 90909090.90909090.90909090 90909090.90909090.90909090 90909090.90909090.09090900 90909090.90909090.09090900 .......................... cccccccccccccccccccccccccc cccccccccccccccccccccccccc ccccccccc................. cccccccccccccccccccccccccc cccccccccccccccccccccccccc .................ccccccccc cccccccccccccccccccccccccc cccccccccccccccccccccccccc .......................... ffffffffffffffffffffffffff ffffffff.................. ffffffffffffffffffffffffff ffffffff.................. ffffffff.................. ffffffff.................. Code: 00 00 00 00 M3 T4 SP L0 1T FR 4M 3W OR K! V3 R5 I0 N4 00 00 00 00 Aiee, Killing Interrupt handler Kernel panic: Attempted to kill the idle task! In swapper task - not syncing =[ metasploit v5.0.2-dev ] + -- --=[ 1852 exploits - 1046 auxiliary - 325 post ] + -- --=[ 541 payloads - 44 encoders - 10 nops ] + -- --=[ 2 evasion ] + -- --=[ ** This is Metasploit 5 development branch ** ] msf5 >
启动metasploit成功后则会进入:
msf >
命令行环境下
下一步,将建立metasploit将其信息存储在其中的数据库中:
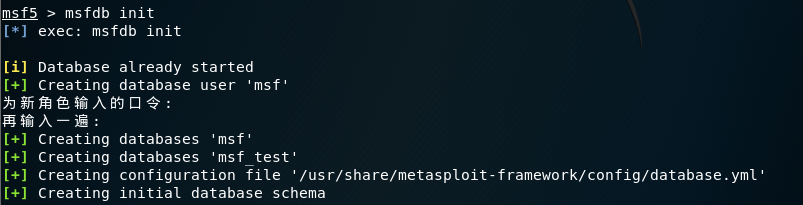
需要以root权限身份登录postgres :(su:“switch user”命令)
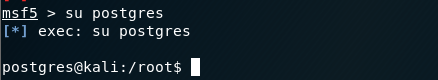
提示:postgres@kali:/root$ 【表示程序 - 主机名 - 用户】
下一步,创建用户和密码:
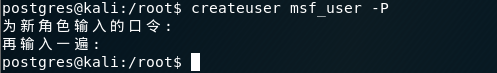
使用 createuser 命令的-P选项创建用户名msf_user,并提示输入密码。
下一步,授予用户一定的权限并创建一个数据库:
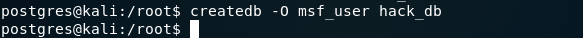
使用 createdb 命令的-O为msf_user用户创建了 hack_db 数据库。
初步配置结束,exit退出!
接下来,则是连接msf和数据库了!参考数据库连接的博文
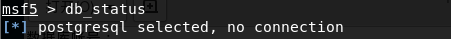
检查数据库是否连接?结果显示未连接!
使用 db_connect 命令连接数据库:

msf5 > db_connect [-] A URL or saved data service name is required. USAGE: * Postgres Data Service: db_connect <user:[pass]>@<host:[port]>/<database> Examples: db_connect user@metasploit3 db_connect user:pass@192.168.0.2/metasploit3 db_connect user:pass@192.168.0.2:1500/metasploit3 db_connect -y [path/to/database.yml] * HTTP Data Service: db_connect [options] <http|https>://<host:[port]> Examples: db_connect http://localhost:8080 db_connect http://my-super-msf-data.service.com db_connect -c ~/cert.pem -t 6a7a74c1a5003802c955ead1bbddd4ab1b05a7f2940b4732d34bfc555bc6e1c5d7611a497b29e8f0 https://localhost:8080 NOTE: You must be connected to a Postgres data service in order to successfully connect to a HTTP data service. Persisting Connections: db_connect --name <name to save connection as> [options] <address> Examples: Saving: db_connect --name LA-server http://123.123.123.45:1234 Connecting: db_connect LA-server OPTIONS: -l,--list-services List the available data services that have been previously saved. -y,--yaml Connect to the data service specified in the provided database.yml file. -n,--name Name used to store the connection. Providing an existing name will overwrite the settings for that connection. -c,--cert Certificate file matching the remote data server's certificate. Needed when using self-signed SSL cert. -t,--token The API token used to authenticate to the remote data service. --skip-verify Skip validating authenticity of server's certificate (NOT RECOMMENDED).
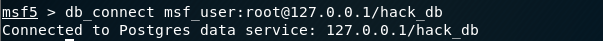
如上图显示: Connected to Postgres data service: 127.0.0.1/hack_db 【连接到hack_db数据库】
检查是否连接:
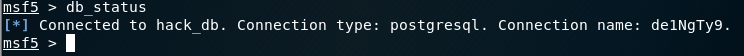
------------------------------------
至此,msf和postgreSQL数据库已经连接并可以使用,使用Metasploit进行的工作,结果将存到PostgreSQL数据库中。
更多了解,待它日研究后更新!!!
