一、添加历史命令记录
1.首先在/etc/profile中添加
export HISTORY_FILE=/var/log/Command/Command.log
export PROMPT_COMMAND='{ date "+%Y-%m-%d %T # $(who am i |awk "{print $1,$2,$5}") $(whoami):[$PWD]# $(history 1 | { read x cmd; echo "$cmd"; })"; } >>$HISTORY_FILE'
2.定期备份移动历史命令,把如下脚本写到任务计划里。每隔一周执行一次
30 10 * * 6 /bin/bash /var/log/Command/history.sh > /dev/null 2>&1
Time=`date +%Y%m%d%H`
logs_path="/var/log/Command/"
logs_name="Command.log"
new_file="$logs_path$logs_name-$Time"
old_file=`find $logs_path -mtime +30 -type f -name "Command.*"`
chattr -a $logs_path$logs_name
mv $logs_path$logs_name $new_file
chattr +a $new_file
touch $logs_path$logs_name
chown -R nobody:nobody $logs_path$logs_name
chmod -R 002 $logs_path$logs_name
chattr +a $logs_path$logs_name
if [ ! -z $old_file ]
then
echo "delet $old_file $Time" >> /var/log/messages
chattr -a $old_file
rm -rf $old_file
fi
3.检查/var/log/Command/Command.log的中的日志
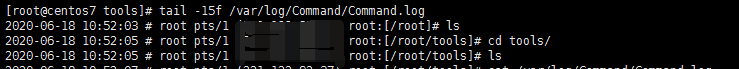
二、使用审计工具,splunk或者eak。
完成步骤一基本就完成了审计功能,如果想要图形化的搜索界面。可以使用步骤二。
方法1.使用splunk
(1).下载splunkforwarder
splunkforwarder类似于zabbix_agent,logstash,filebeat之类的client端。
splunk类似于zabbix_server之类的server端。
splunkforwarder不好找,去splunk官网下载时候。注意右下角有一个old release。选择自己有lincense的版本。
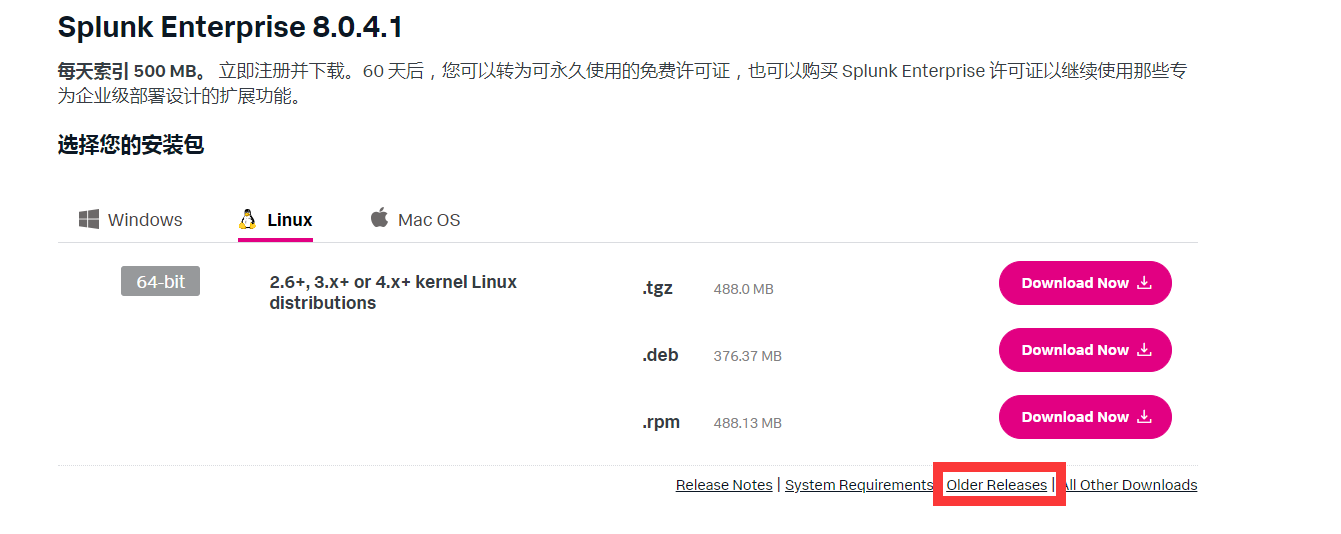
(2)安装splunkforwarder
rpm -ivh splunkforwarder-版本号.rpm cd /opt/splunkforwarder/bin ./splunk start ./splunk add forward-server 192.168.103.31:9997 ./splunk set deploy-poll 192.168.103.31:8089 ./splunk add monitor /var/log/lastlog -index secure ./splunk add monitor /var/log/lastlog -index secure #添加索引位置和目录 ./splunk add monitor /var/log/lastlog -index secure ./splunk add monitor /tmp/wtmp -index secure ./splunk add monitor /var/log/Command/Command.log -index history ./splunk restart
(3)安装splunk
方法同上,适当变通一下包名。启动web功能。
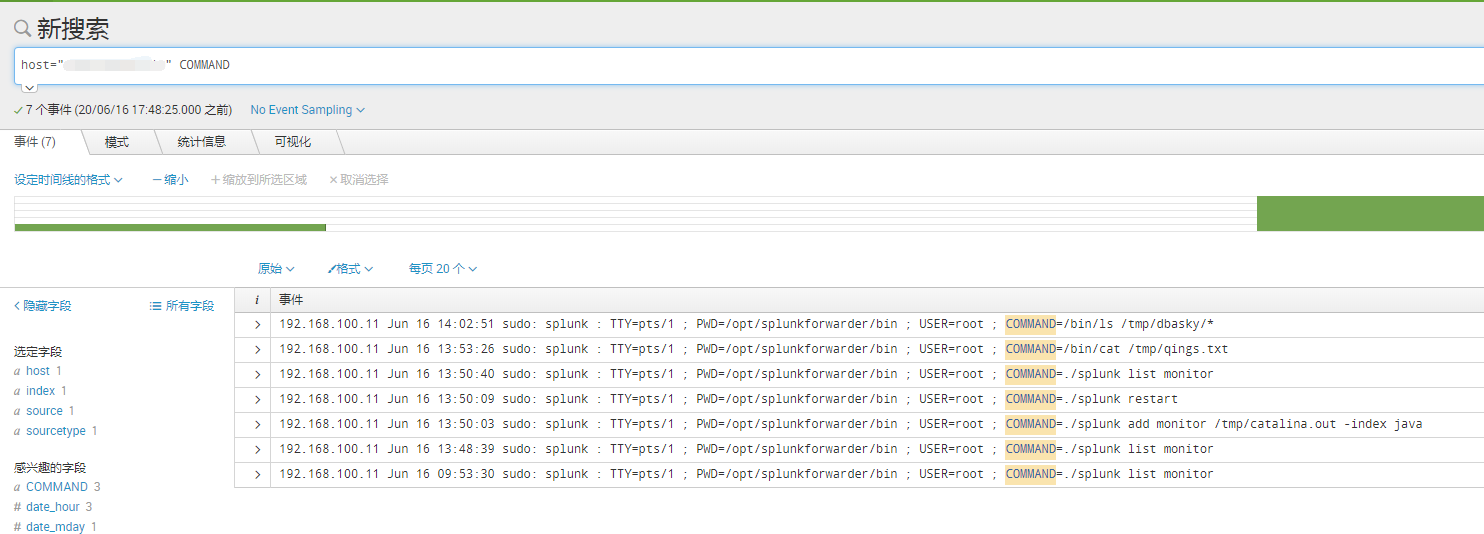
(4)查看图形
命令审计
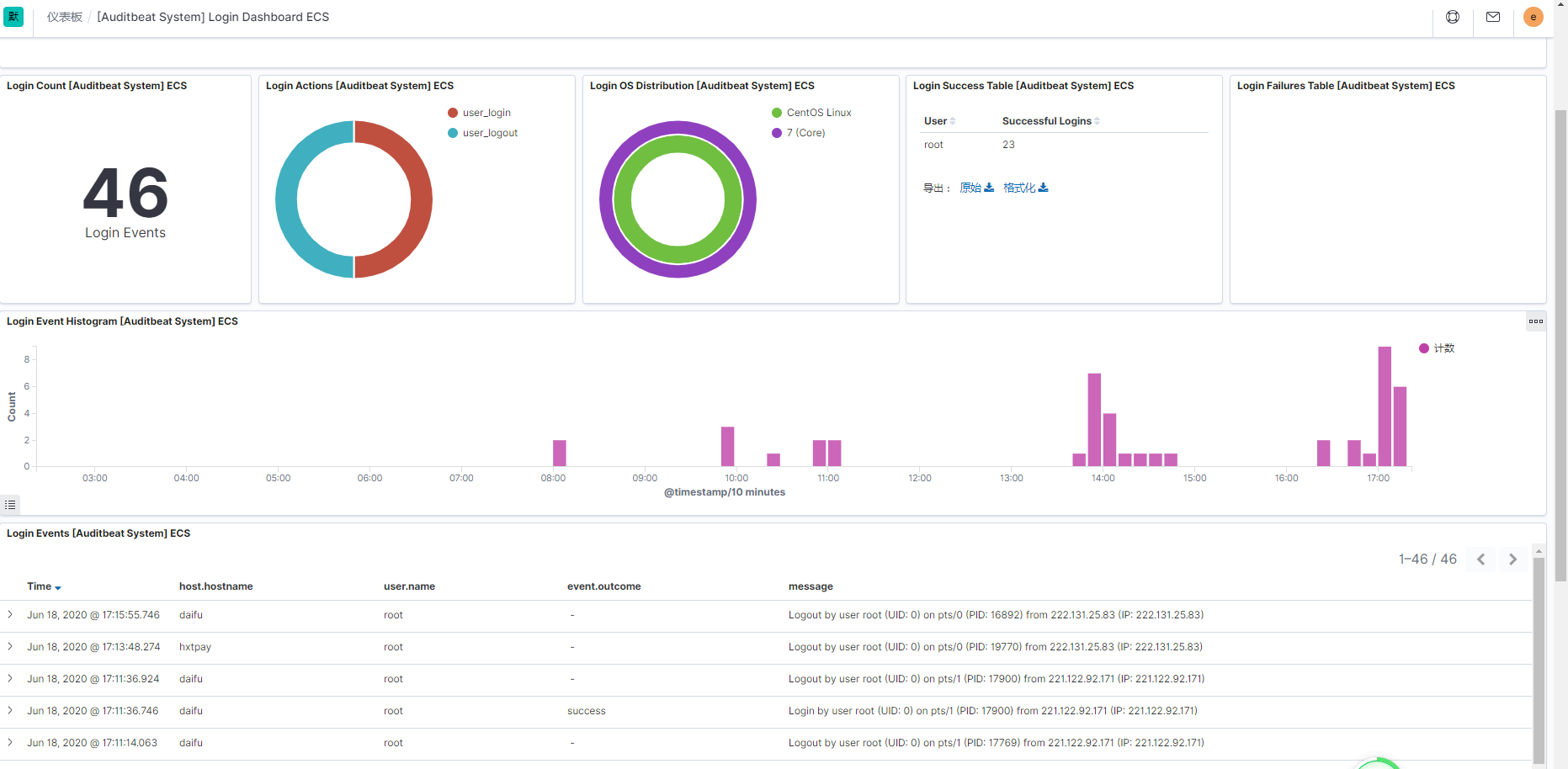
登录审计(里面的路径和上面写的/var/log/Command/Command.log位置不一致,图片截图比较早。以前的图片)

方法2.使用eak,elasticsearch,auditbeat,kibana套装
(1)安装过程不想写了,百度能搜一堆。大致过程是搜索elk官网,进去下载,选择rpm包。下载完rpm安装。或者直接yum install auditbeat
(2)修改配置文件,添加审计目录
auditbeat.modules:
- module: auditd
audit_rule_files: [ '${path.config}/audit.rules.d/*.conf' ]
audit_rules: |
-a always,exit -F arch=b64 -S execve,execveat -k exec
-w /etc/group -p wa -k identity
-w /etc/passwd -p wa -k identity
-w /etc/gshadow -p wa -k identity
-a always,exit -F arch=b64 -S open,creat,truncate,ftruncate,openat,open_by_handle_at -F exit=-EACCES -k access
-a always,exit -F arch=b64 -S open,creat,truncate,ftruncate,openat,open_by_handle_at -F exit=-EPERM -k access
- module: file_integrity
paths:
- /bin
- /usr/bin
- /sbin
- /usr/sbin
- /etc
exclude_files:
- '(?i).sw[nop]$'
- '~$'
- '/.git($|/)'
scan_rate_per_sec: 50 MiB
max_file_size: 100 MiB
recursive: false
- module: system
datasets:
- module: system
datasets:
period: 30m #多久上报一次数据
state.period: 12h
process.hash.scan_rate_per_sec: 50 MiB
process.hash.max_file_size: 100 MiB
user.detect_password_changes: true
login.wtmp_file_pattern: /var/log/wtmp*
login.btmp_file_pattern: /var/log/btmp*
setup.template.settings:
index.number_of_shards: 1
setup.template.name: "auditbeat-hxtpay"
setup.template.pattern: "auditbeat-hxtpay-*"
setup.template.enabled: true
setup.ilm.rollover_alias: "auditbeat-hxtpay"
setup.dashboards.directory: /usr/share/auditbeat/kibana/ #导入模板
setup.dashboards.index: auditbeat-* #默认索引
setup.kibana:
output.elasticsearch:
hosts: ["你的elasticsearch服务器ip:9200"]
username: "elastic"
password: "你的密码,没设置账号密码的直接注释这两行"
processors:
- add_host_metadata: ~
- add_cloud_metadata: ~
- add_docker_metadata: ~
(3)添加auditeat审计模板到kibana里
/usr/share/auditbeat/bin/auditbeat -c /etc/auditbeat/auditbeat.yml setup --dashboards
(4)查看kibana的dashboard
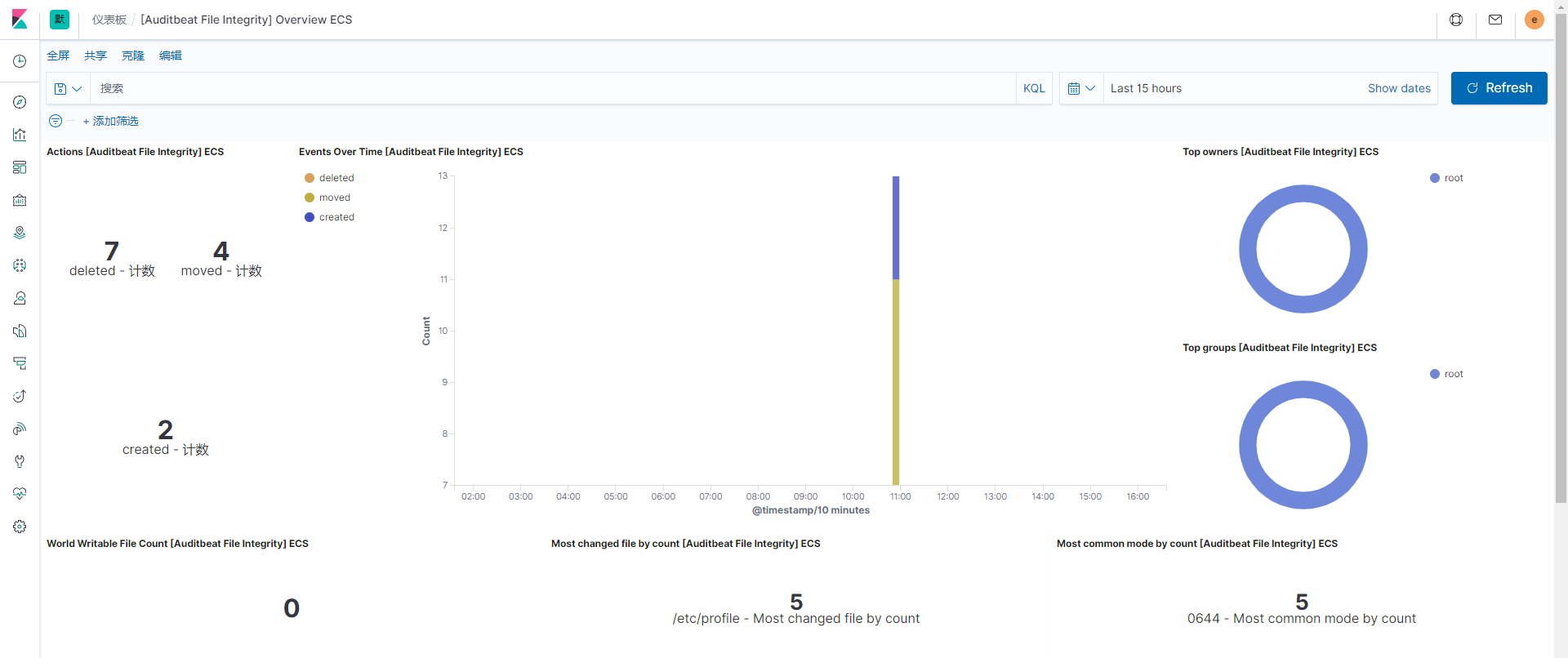
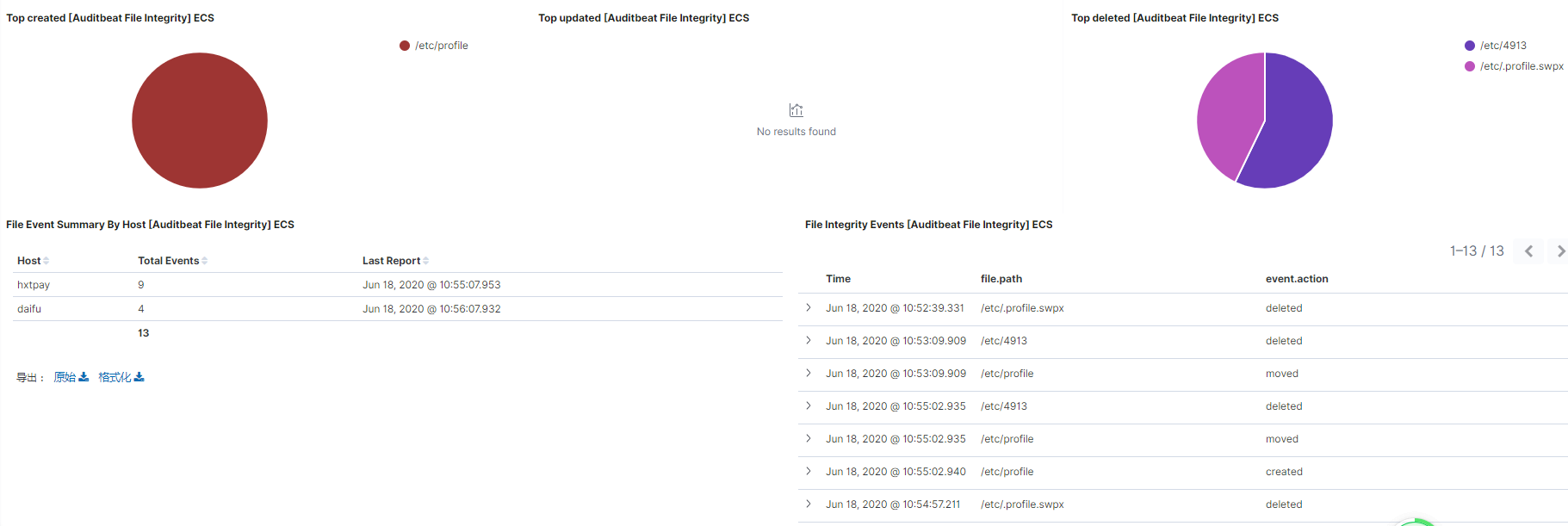
文件审计
登录审计