拿到题目,是64位ELF
IDA查看
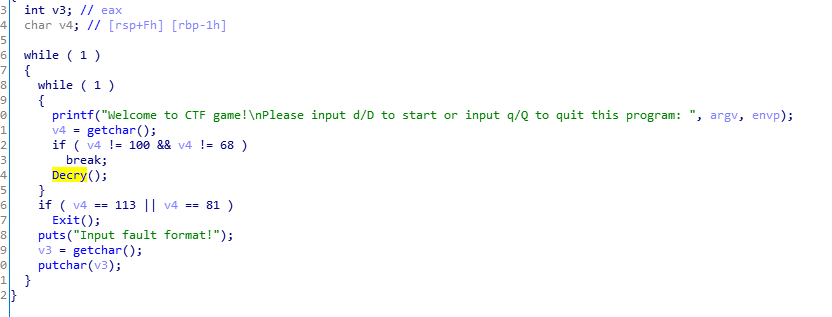
点进去
unsigned __int64 Decry() { char v1; // [rsp+Fh] [rbp-51h] int v2; // [rsp+10h] [rbp-50h] int v3; // [rsp+14h] [rbp-4Ch] int i; // [rsp+18h] [rbp-48h] int v5; // [rsp+1Ch] [rbp-44h] char src[8]; // [rsp+20h] [rbp-40h] __int64 v7; // [rsp+28h] [rbp-38h] int v8; // [rsp+30h] [rbp-30h] __int64 v9; // [rsp+40h] [rbp-20h] __int64 v10; // [rsp+48h] [rbp-18h] int v11; // [rsp+50h] [rbp-10h] unsigned __int64 v12; // [rsp+58h] [rbp-8h] v12 = __readfsqword(0x28u); *(_QWORD *)src = 'SLCDN'; v7 = 0LL; v8 = 0; v9 = 'wodah'; v10 = 0LL; v11 = 0; text = join(key3, (const char *)&v9); strcpy(key, key1); strcat(key, src); v2 = 0; v3 = 0; getchar(); v5 = strlen(key); for ( i = 0; i < v5; ++i ) { if ( key[v3 % v5] > 64 && key[v3 % v5] <= 90 ) key[i] = key[v3 % v5] + 32; ++v3; } printf("Please input your flag:", src); while ( 1 ) { v1 = getchar(); if ( v1 == ' ' ) break; if ( v1 == ' ' ) { ++v2; } else { if ( v1 <= 96 || v1 > 122 ) { if ( v1 > 64 && v1 <= 90 ) str2[v2] = (v1 - 39 - key[v3++ % v5] + 97) % 26 + 97; } else { str2[v2] = (v1 - 39 - key[v3++ % v5] + 97) % 26 + 97; } if ( !(v3 % v5) ) putchar(32); ++v2; } } if ( !strcmp(text, str2) ) puts("Congratulation! "); else puts("Try again! "); return __readfsqword(0x28u) ^ v12; }
可以看到text是最终比较的结果,经过join处理后,其结果为killshadow
join:
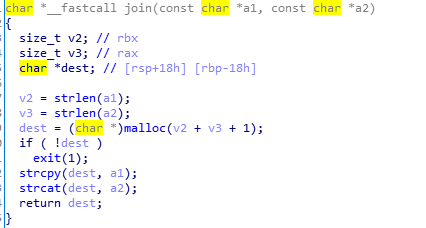
key经过拼接,为ADSFKNDCLS后经处理,变为小写
然后写脚本
text = 'killshadow' key = 'adsfkndcls' key_ = '' v3=0 for i in range(len(key)): flag = ord(key[v3%len(key)]) if flag > 64 and flag <=90: key_ += chr(ord(key[v3%len(key)])+32) v3=v3+1 ans = '' for i in range(len(key)): for j in range(0,15): tmp=chr(ord(text[i]) - 97 + 26*j - 97 + ord(key [v3%len(key)]) + 39) if ord(tmp)>64 and ord(tmp) <91: ans+=tmp break v3=v3+1 print ans
得出flag为KLDQCUDFZO